In this lesson, learn how to use the liquify filter in Photoshop to create photographic "caricatures". See how easy and fun it is to create exaggerated, comedic images of your family, friends and adversaries using this simple but impressive technique!

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Although The Last Jedi hype has mostly passed, there are still a good number of fans out there dueling Sith lords in augmented reality via their new Lenovo Mirage headsets. Now, thanks to an update on Thursday, those aspiring Jedi have a new AR challenge to engage in the Star Wars: Jedi Challenges app.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

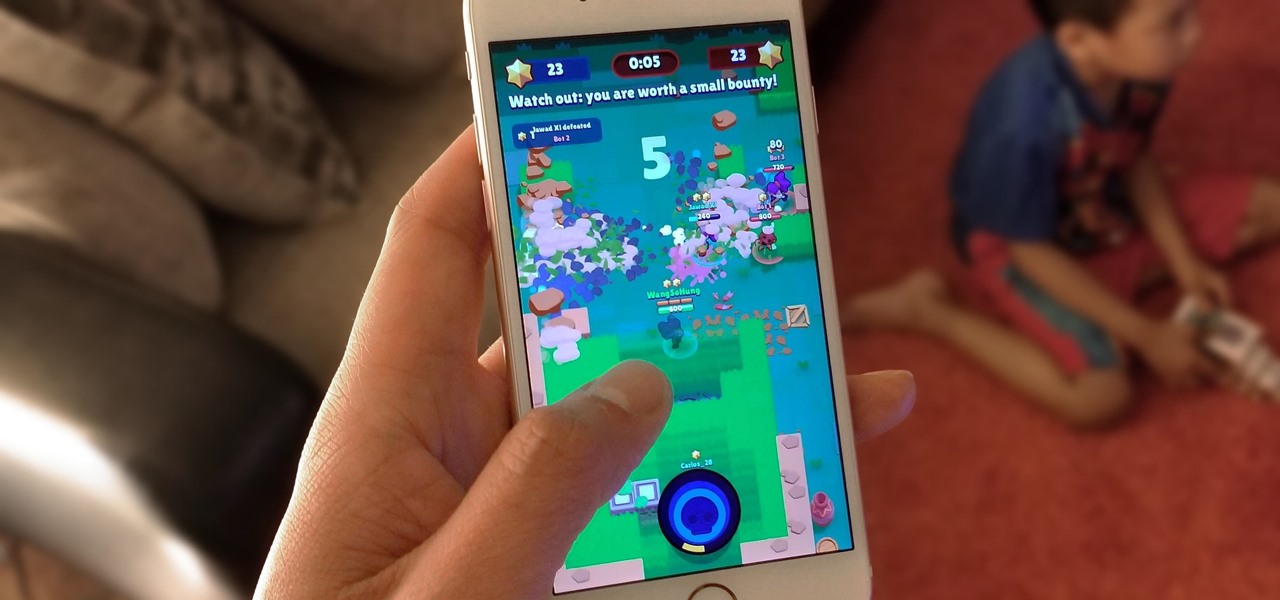
Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

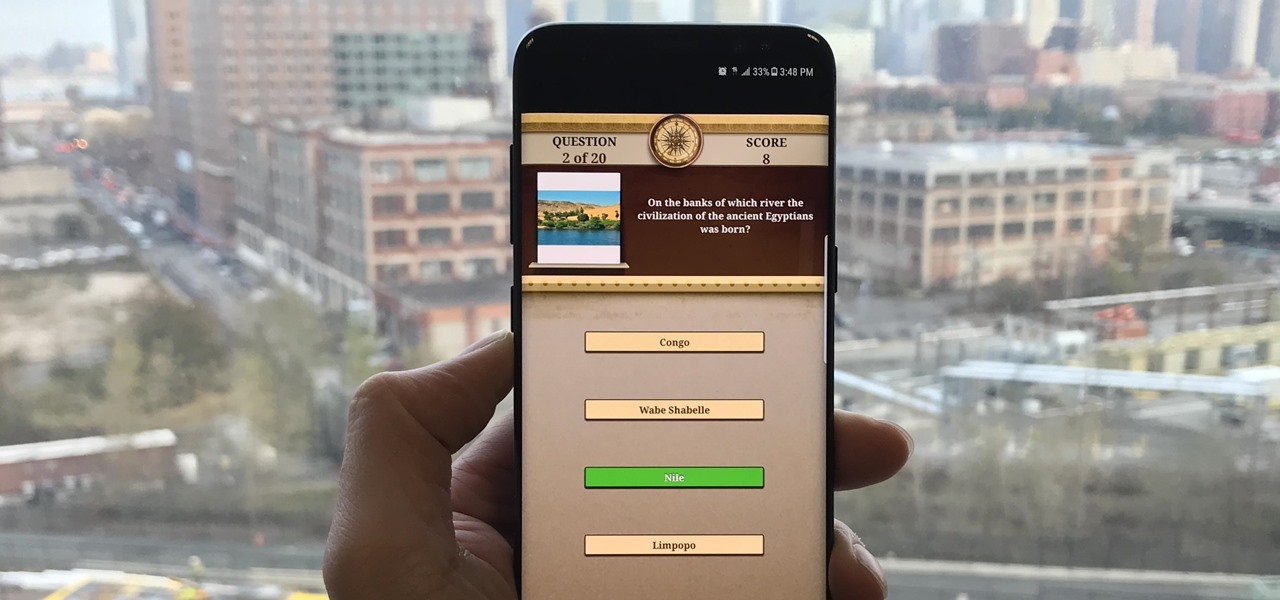
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Kizeme This Japanese word, kizeme, means "spirit of attack." It is said of Miyamoto Musashi, the famed Japanese swordsman, that as he grew older he relied more on kizeme to defeat adversaries and, as a result, emerged victorious from challenges without taking the life of his opponent.