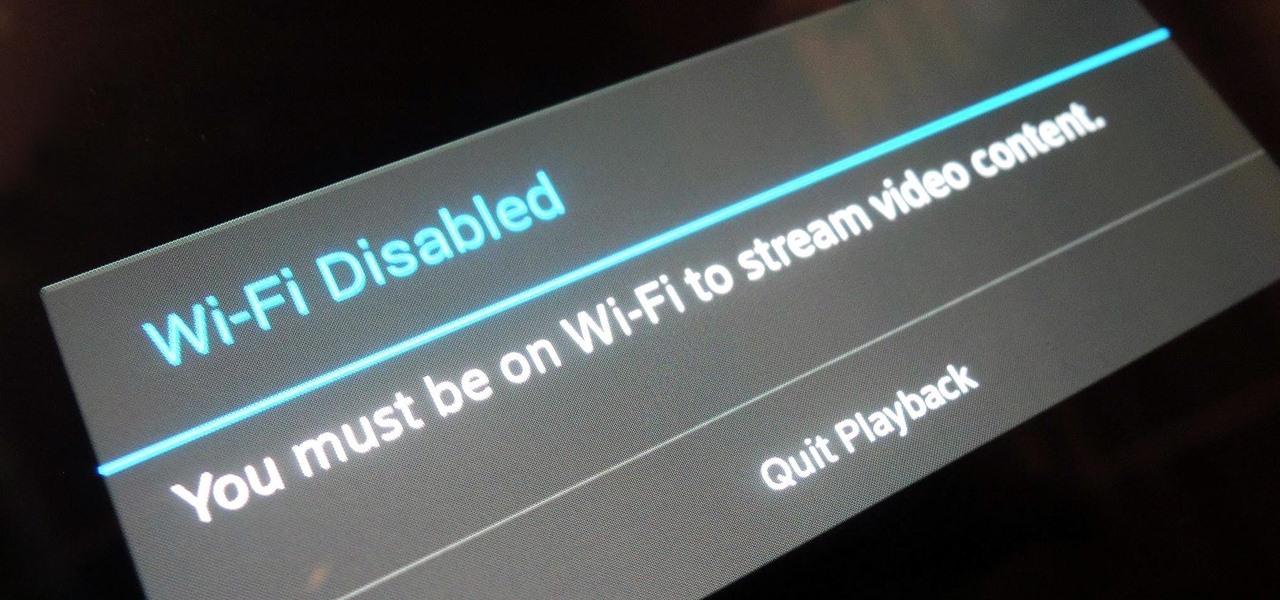
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

Even if your business is mostly online and computer related you will need paper, which in other hand will need classifier to be sorted out and easily accessed. The paperless office is as much of a myth as the paperless toilet, so accept it, if you are serious about business, you need paper. Important contracts between customers signed on papers, leaflets, reminders, advert previews, drafts for preview at the table. The paper is always used even in today highly computerized epoch.

The sovereignty that's granted when we jailbreak our iOS 7 devices can only be described with one word—liberating. With this freedom comes countless themes and apps that let us manipulate our devices to really own them and turn them into something that is truly ours.

It's fairly easy to switch between running apps on the Nexus 7 by hitting the Recent apps key in the Navigation bar at the bottom of your screen, but for me—it's just not good enough. I don't particularly like leaving the app I'm currently in to see this menu, and the menu itself is kind of clunky, and overall, not as fast as I'd like it to be.
When programming an Excel-file with links between sheets and assorted macros for whatever is needed you may want the file to behave as a program so that users can not access the ribbon even by double-clicking on the top bar. Protect the code from being accessed by pressing alt-F8 or alt-F11. Make sure you can run the macro show_sheets_and_ribbon () from the opening sheet before continuing to step 3

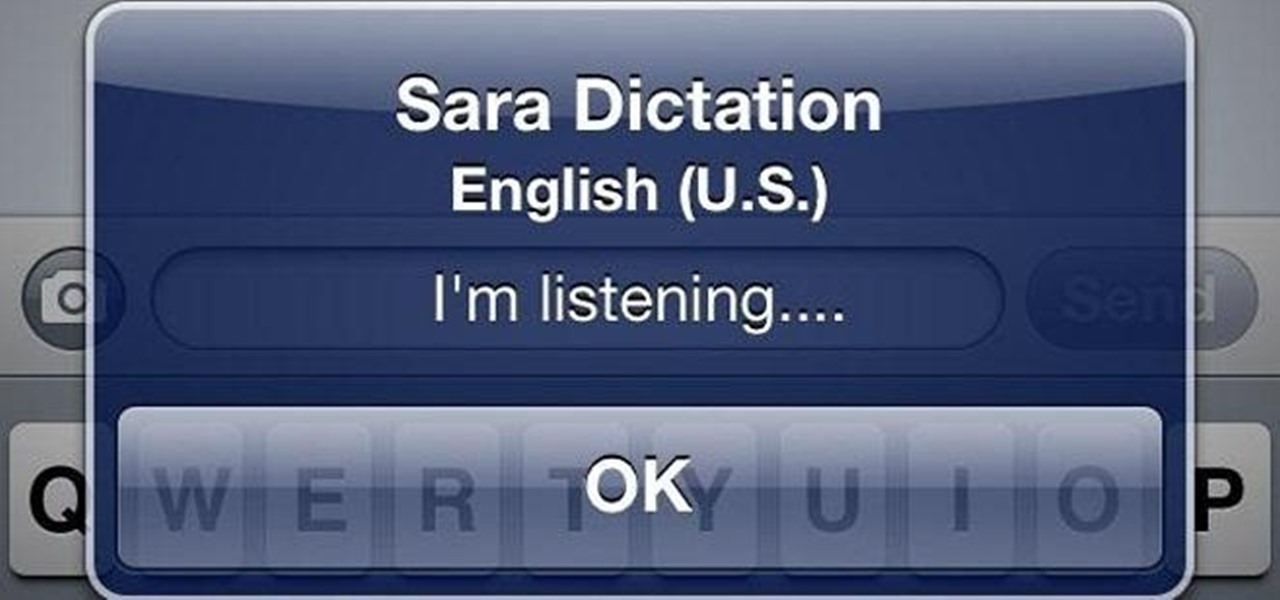
Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

My obsession with Siri is well documented, and after I jailbroke my iPhone 4 recently, I thought I would finally be able to rekindle our imaginary love. But, when I downloaded the Siri Port, I found that the app was buggy and super slow.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

Unlocking weapons skins is a great way to show off your weapon efficiency and flash some sweet gear. The diamond camouflage in Call of Duty: Black Ops 2 can be accessed by unlocking every single camouflage in a said category. So, if you want the diamond camouflage for your Assault Rifle class, you will need to unlock all of the skins for each gun in the Assault Rifle class. Once gold is unlocked, you will have access to the diamond camouflage.

One of the most played-up features of Windows 8 is that it's so much faster than previous versions. So fast, in fact, that Microsoft had to change the way that users access the BIOS because 200 milliseconds just isn't enough time to hit the right key. It may take some getting used to, but it's probably a welcome change for most people, considering that the "right" key is different depending on what type of computer you're running the OS on.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

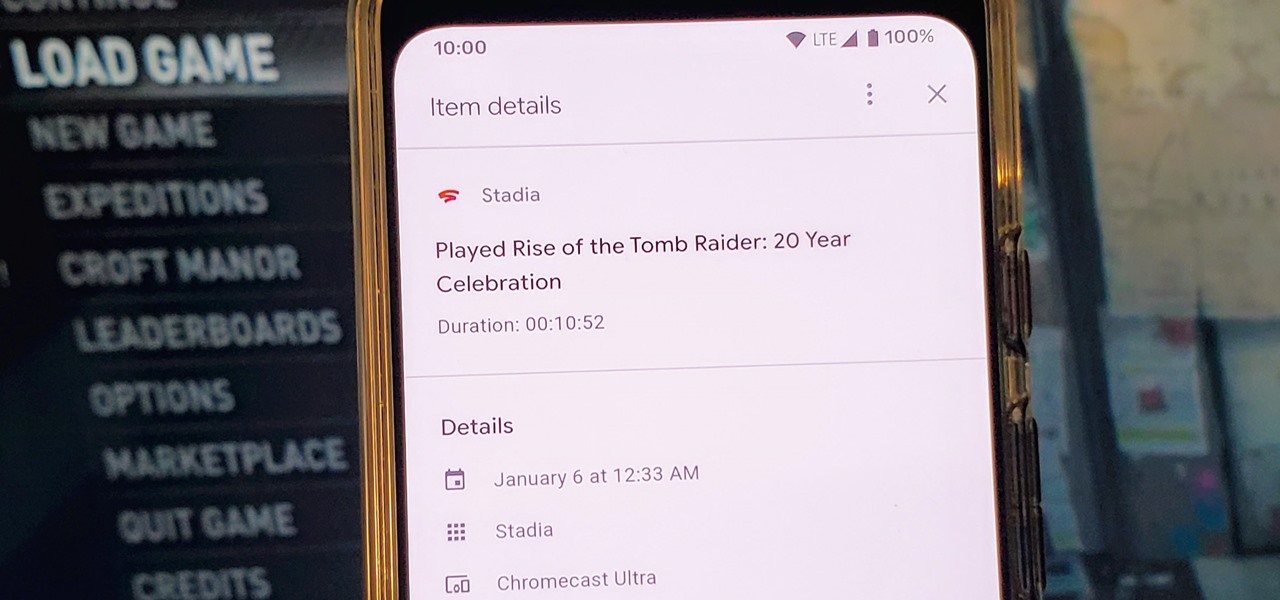
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

As first reported by Next Reality last year, game developer Preloaded, in partnership with BBC Studios, has finally launched BBC Earth - Micro Kingdoms: Senses.

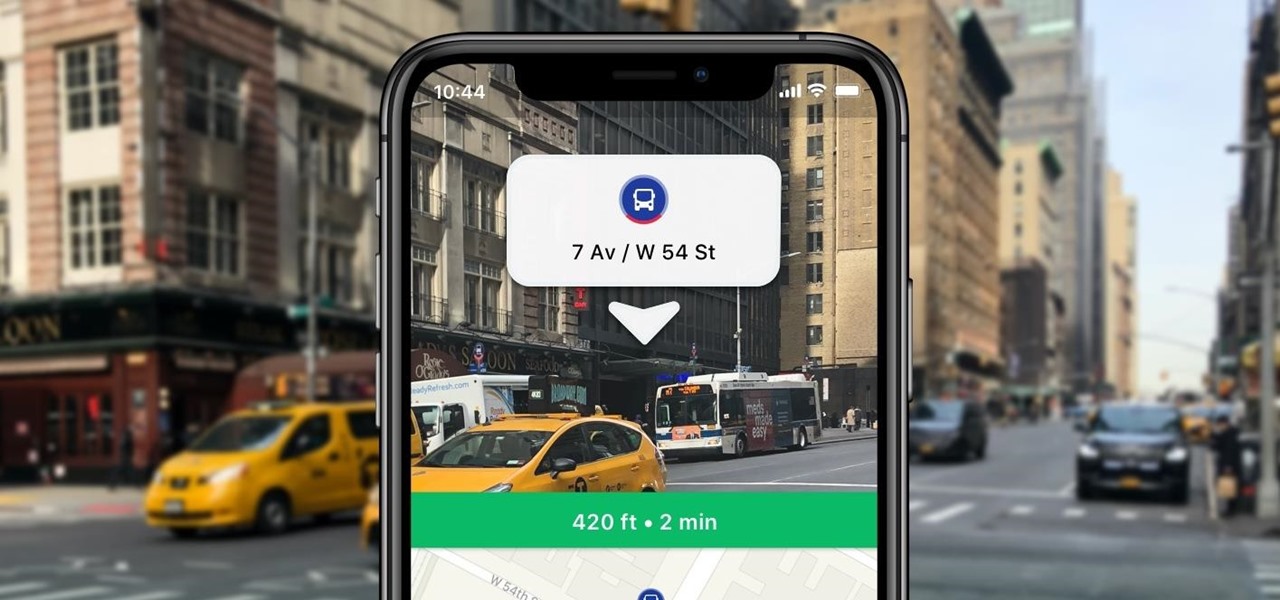
As helpful as it is, Google Maps isn't the only mapping app with augmented reality walking navigation anymore.

Starbucks is spicing things up ahead of this holiday season with a little augmented reality joy. This week the company launched its first Instagram filter, called Holijoy, delivered like an early Christmas gift and packing four seasonal lenses.

Alongside its official unveiling of the lower-cost Pixel 3a smartphone at Google I/O, Google took the opportunity to extend its early preview of AR walking navigation in Google Maps to all Pixel devices.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

Nike and Snapchat, having already reigned triumphant with its viral augmented reality ad featuring Lebron James, are teaming up with another basketball legend at NBA All-Star Weekend

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

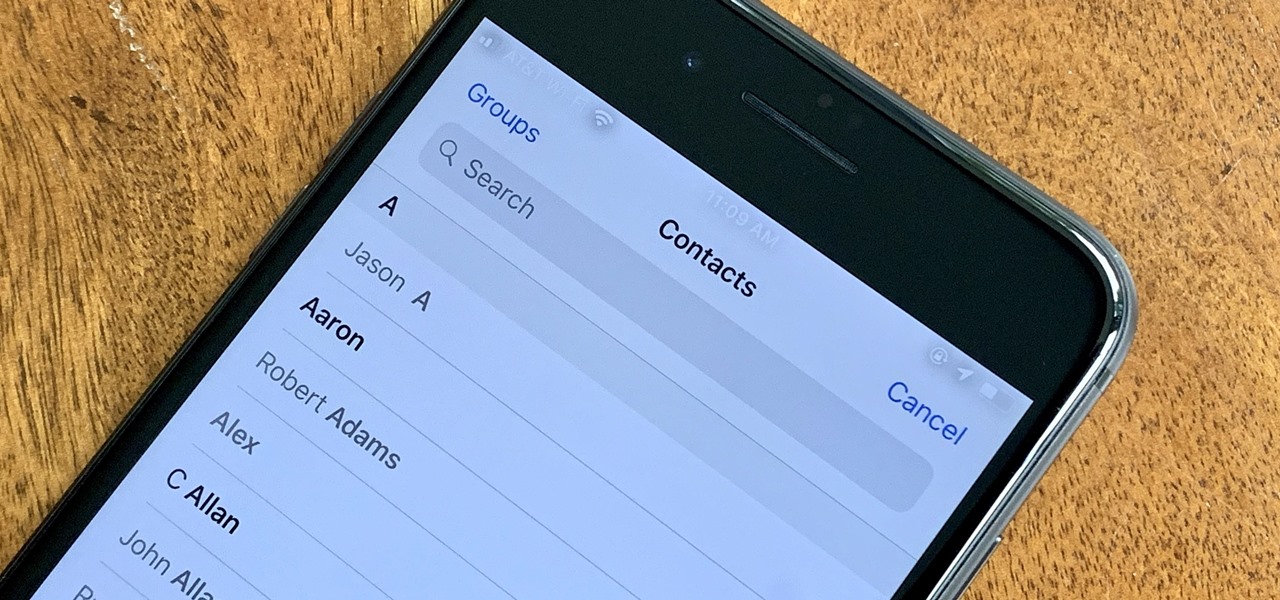
The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

Another AR cloud savior has emerged this week in Fantasmo, a startup that wants to turn anyone with a smartphone into a cartographer for spatial maps.

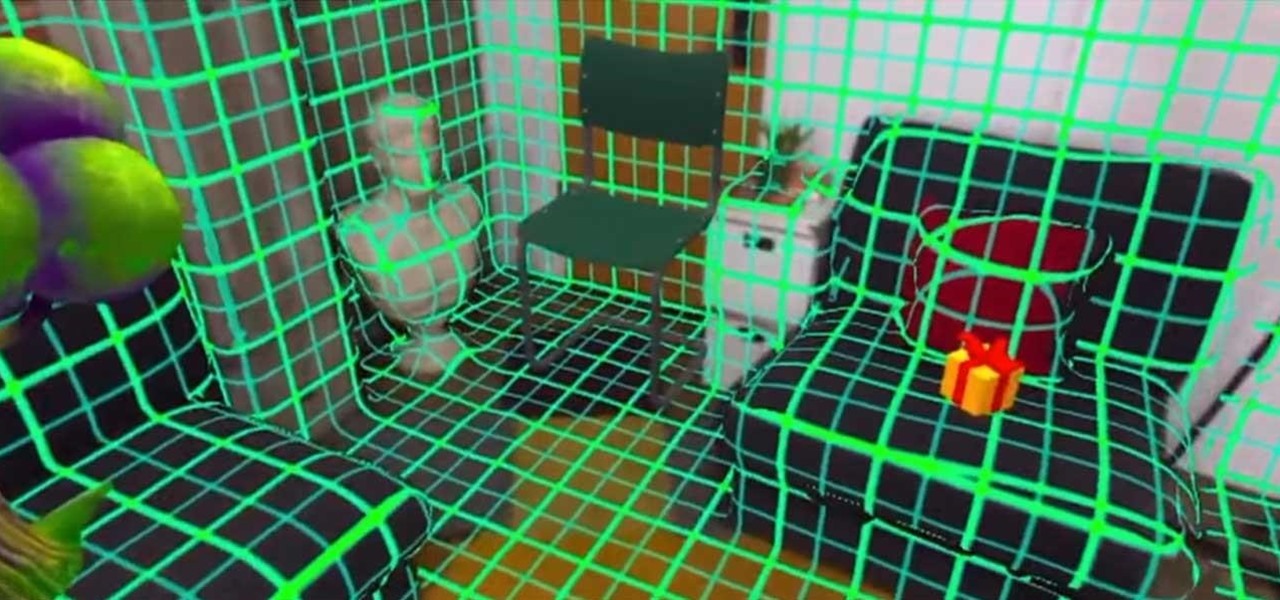
San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

One of the best things about Android is the ability to customize your phone to your liking. From changing the layout of icons to finding the perfect wallpaper to reflect your current mood, there's a wide range of tools to make your phone yours.

The Xposed Framework has an official repository for downloading modules which can be easily accessed by searching the Download section in your Xposed Installer app. But not every module is available on the Xposed repo — in fact, many unique and interesting modules are only hosted on third-party servers.

Road trips almost always include unforeseen pit stops, which can take you way off track from your destination and end up causing massive delays. But if you rely on Waze for navigation, however, this issue is totally covered.

It's fitting that students at the University of Washington can catch a glimpse of the new, 135,000 square-foot computer science building in augmented reality before construction is completed.

The beta firmware for OnePlus devices lets you record calls from the stock Oxygen OS dialer, but this feature is never included in official updates. This is likely due to legal issues with recording calls in some jurisdictions, but thankfully, there's a way to get this feature without having to run beta software.

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.

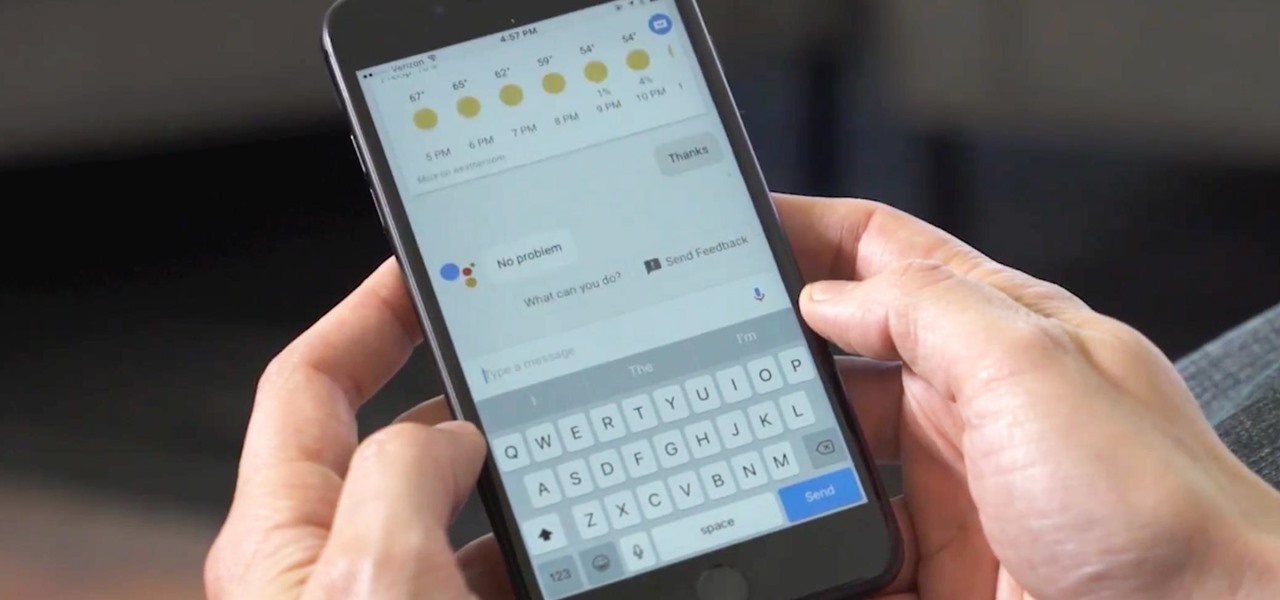
As we've said before, Siri has some major competition moving into its own playground, and Google just announced at its I/O event that Google Assistant is available on the iPhone, starting today.

It has been a long road for Uber throughout the duration of its lawsuit with Waymo, especially with a judge who seemed significantly against Uber with almost every argument made. Monday's ruling was, while not necessarily a win for Uber, less punishing than many would have thought.

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

The company that pioneered music scanning for mobile devices is moving into the augmented reality advertising arena. Included in an update of their iOS and Android apps last week, Shazam can now scan special codes to immerse users in 3D animations, 360-degree videos, mini-games, and other AR content.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.