Snapchat is an app built on sending quick-to-disappear pictures to your friends and family. Sure, this is the primary function of the app, but sometimes users want longer-lasting Memories while interacting with Snapchat. While My Story allows snaps to stick around for 24 hours, they still disappear in time. This is where Memories come in handy.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

The debate between physical and virtual navigation buttons and their respective benefits has been going on for a few years now. It looks to finally be settled, with the Samsung Galaxy S5 being the only current-generation flagship Android phone that has yet make the switch to on-screen buttons.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

Tony Stark is a smooth talking, genius billionaire playboy that occasionally saves the world... what's not to like? The Marvel films starring Robert Downey, Jr. have grossed well over a billion dollars in the U.S. alone, so it's needless to say that Iron Man is a very popular superhero.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

With Shortcuts, Apple has designed a way to create your own tools and automations right on your iPhone. And to top it off, your creations can be accessed in a variety of ways, including Siri phrases, widgets, and the Shortcuts app itself. Perhaps even more useful is adding them as custom actions to your Share Sheet and making them available to you system-wide.

By far, one of the biggest advantages to having a jailbroken iPhone is being able to apply custom themes to Apple's user interface and truly set your device apart from the rest of the crowd. And if you want to change your iPhone's app icons from rounded squares to circles for an entirely unique look, there's nothing stopping you.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

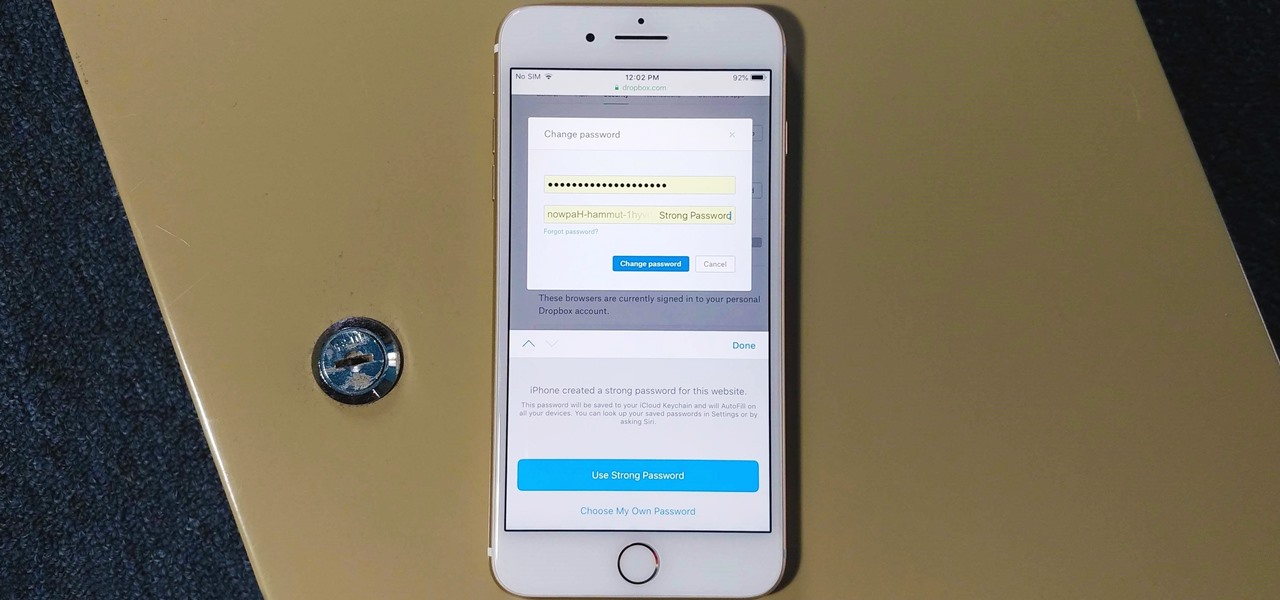
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

The Xbox One is pinning its success on the fact that is much more than just a video game console. Microsoft is looking for the Xbox One to become the centerpiece for family entertainment, which is why they included features like multitasking, TV controls, and apps.

This goes out to all of the Tweeters out there looking to get a little more creative with their Twitter accounts. My page has always been extremely basic, because I just never bothered to pretty it up. I just had one of the stock backgrounds and the good ole Sacramento Kings logo for my profile pic. So, if you want to add your own cool photos and backgrounds to your account, the folks over at Twitter made this funny cartoon video just for you. It's not the most complicated of tasks, and every...

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

With Samsung's One UI version of Android, it's easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in an overlay ribbon that can also get in the way.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Update (Fall 2020): Samsung's version of Android 11 is already in its testing phases! One UI 3.0 is expected to hit recent flagship Galaxy devices towards the end of this year, so check out the new list of features:

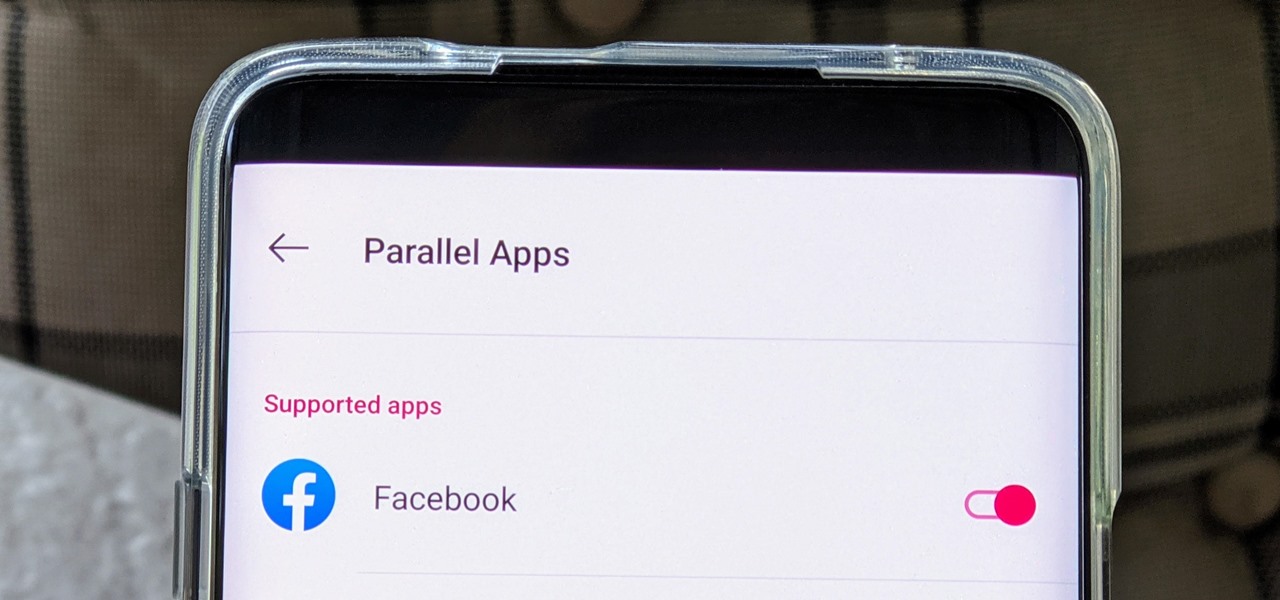
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Apple is giving iPhone owners even more options to express themselves via Animojis with a wide range of customization options for their personal Memojis.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

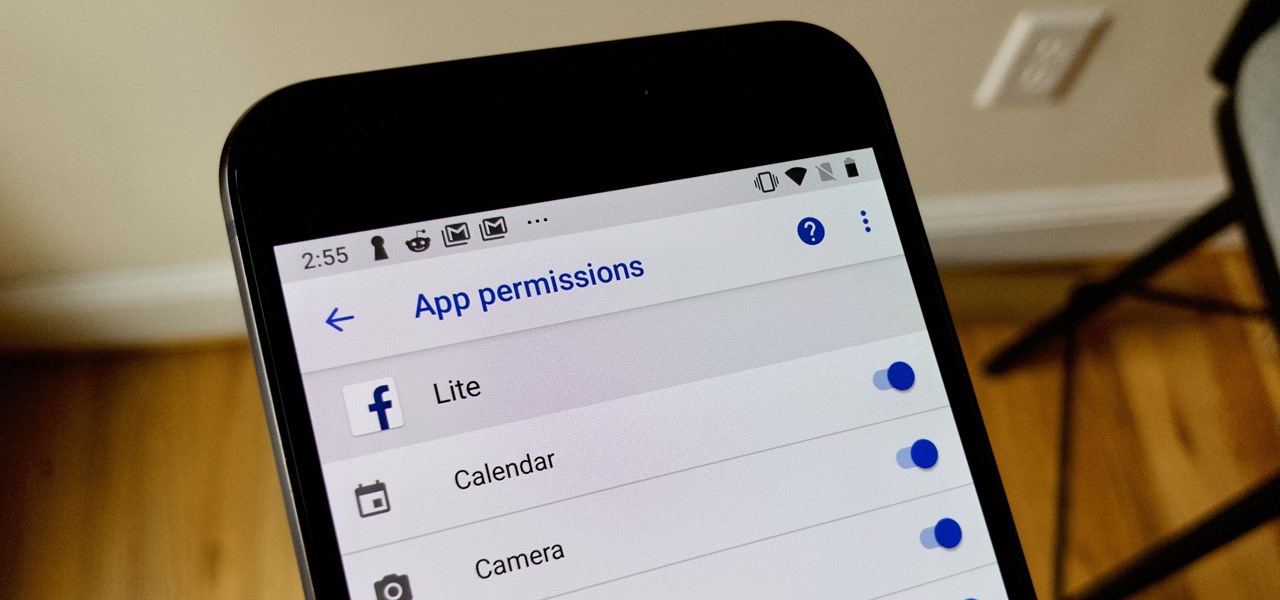
The Android world exploded when it was discovered that Facebook was logging the call and text histories of many of its users, although the company claims those users had explicitly given Facebook permission to log that data. The case remains that many users were unaware of this activity, which occurs on both Messenger and Facebook Lite. Luckily, it's very easy to disable.

AirDrop is an underrated feature that lets you to quickly transfer files like songs and photos via Bluetooth and Wi-Fi from your iPhone to Macs and other iOS devices. It's been a staple in the Control Center ever since iOS 7, prominently displayed for easy access. However, with iOS 11, that quick access to AirDrop has seemingly disappeared.

When I crack open a new book, I always make sure I have a pen and a highlighter nearby so I can mark away! Anything particularly witty, inspiring, or engaging gets highlighted, underlined, or circled. When I use the Amazon Kindle app on my phone, I do the same thing by writing notes and highlighting, but I often find it difficult to keep track of my markings.

Now you can watch your old copy of Bridget Jones's Diary anywhere, anytime, on your smartphone. It's a dream come true! (Disclaimer: This dream may oddly specific to me.)

Google just announced that it will be bringing the Google Assistant—previously an exclusive feature on Pixel phones—to many more devices in the coming days. The only requirement they're giving is that the phone must be running either Android Marshmallow or Android Nougat, so according to the most recent Android distribution numbers, that's roughly 32% of all existing phones and tablets.

While your iPhone may have a built-in time-lapse feature, it's nowhere near as smooth as Instagram's newish Hyperlapse app, and it doesn't give you any speed control like the latter does. If you haven't tested out Hyperlapse yet, check out the short promo video to see just how well its stabilization algorithm works.

By now, Samsung's Multi-Window Mode is a pretty well-known feature. With other manufacturers now recreating this functionality in their own flagships, like LG, it's safe to say the feature has been a hit with consumers.