How To: A Simple Virus Written...in Bash!
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.
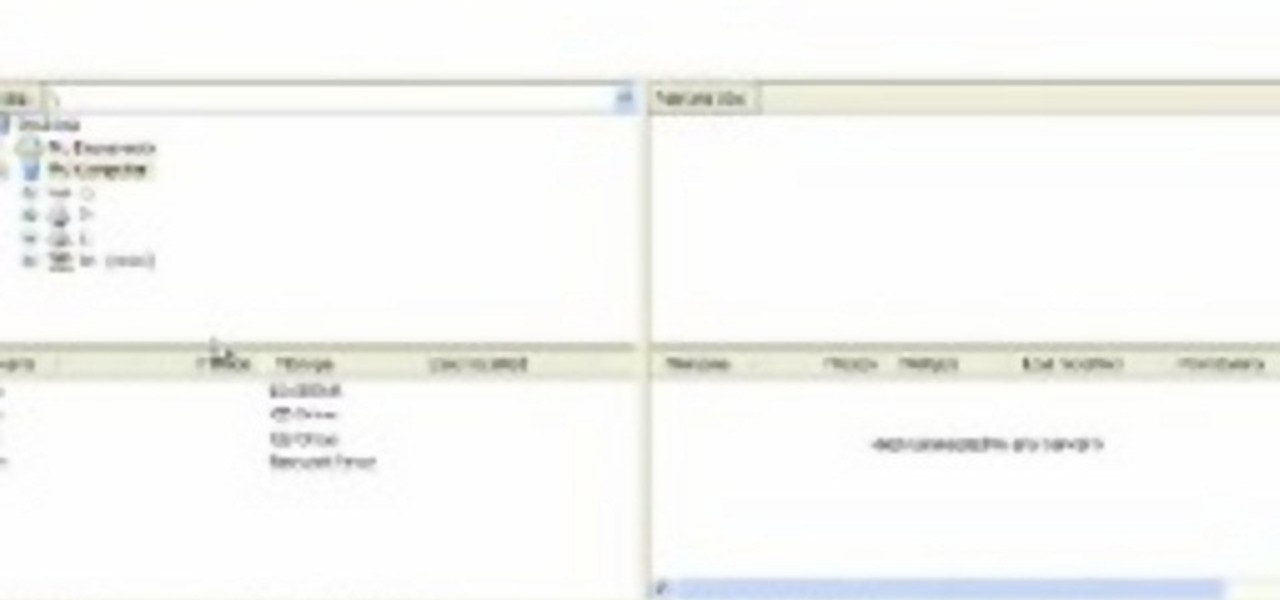
In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

In this video, our author, atomicinteractive, shows use how to use Fetch FTP to upload a temporary webpage. Please make sure your directory has the html file. Please find your email with ftplogin information. This will also show login information for the control panel and creating alternate email addresses.

Fetch is an FTP program for Macs (Smart FTP can be used if you don't have a Mac). These can be downloaded from Download.com

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.
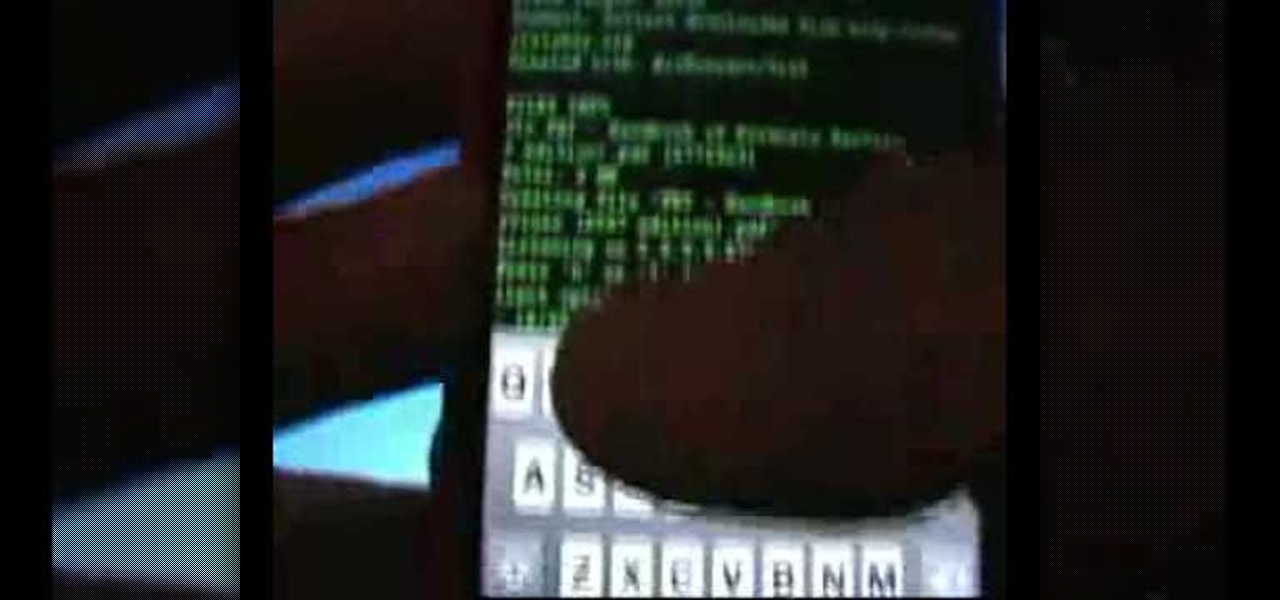
In this video, we learn how to download torrents on the iPhone 2.0 or 2.1. Before you do this, you will need: Cydia, Mobile Terminal, C Torrent, Safari Download Plug-in, and Mobile Finder. to start, you will first go to a torrent site and find the torrent that you want to download. Then, click on the download torrent button. From here, you will see a warning appear on the screen. Choose to download this and then go to your Mobile Finder. Find where you saved the torrent to. Then, hit the home...
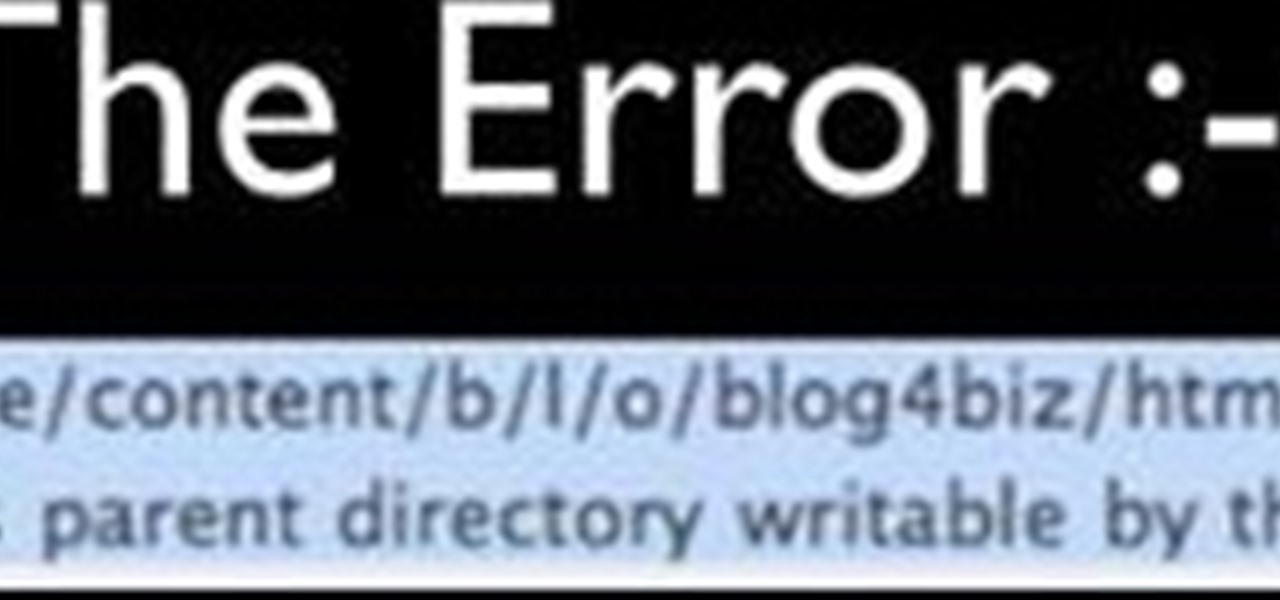
Faced with an "Unable to create directory" error when attempting to upload an image to WordPress? This clip offers instructions on how to fix it. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about its features through videos like this one. Take a look.

Internal linking is a valuable way to improve search engine optimization on your website or blog. This component of organic search engine optimization we going to focus on web copy threading.
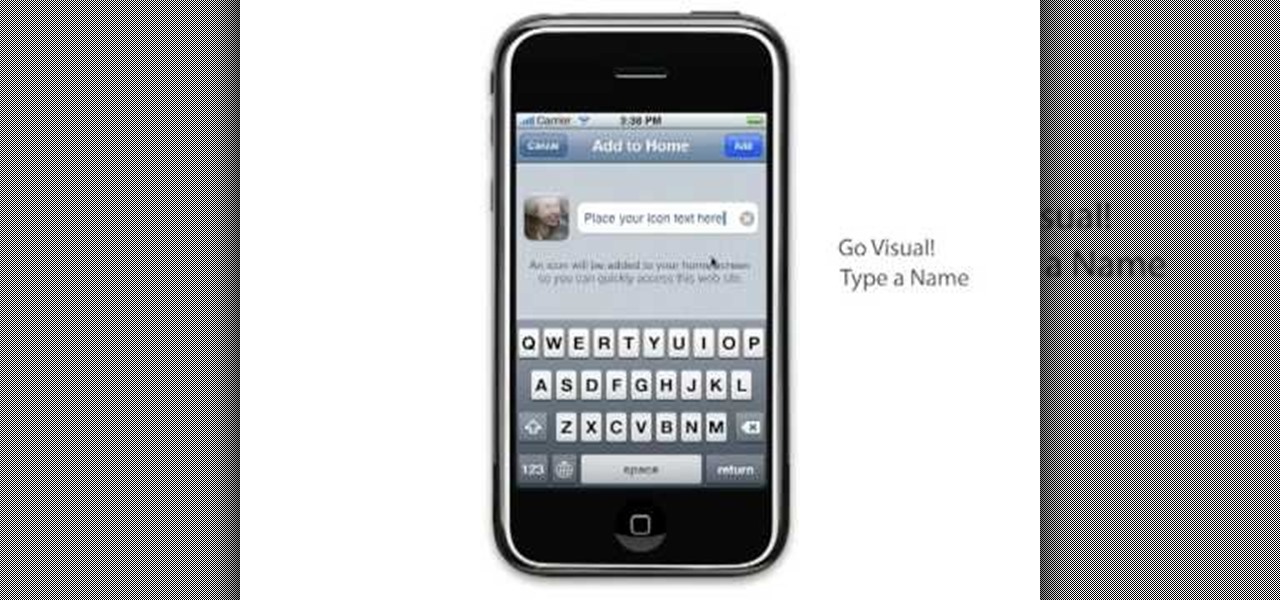
Learn to setup a visual dial icon on your iphone. This one click application allows you to call anyone in your directory by clicking on a photo of them on your phones desktop.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
In this video tutorial, viewers learn how to mount ISO files without burning DVD. This task is very fast, easy and simple to do. The first way is to simply right-click on the ISO file, go to Open With and select Open with "Archive Mounter". The second way is to open the Terminal program and type in the command line: sudo mount -o loop -t iso9660.ISO [directory]. Users will need to create a directory before using the terminal command line. Finish by pressing the Enter key. This video will bene...

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my aspiring hackers!

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.
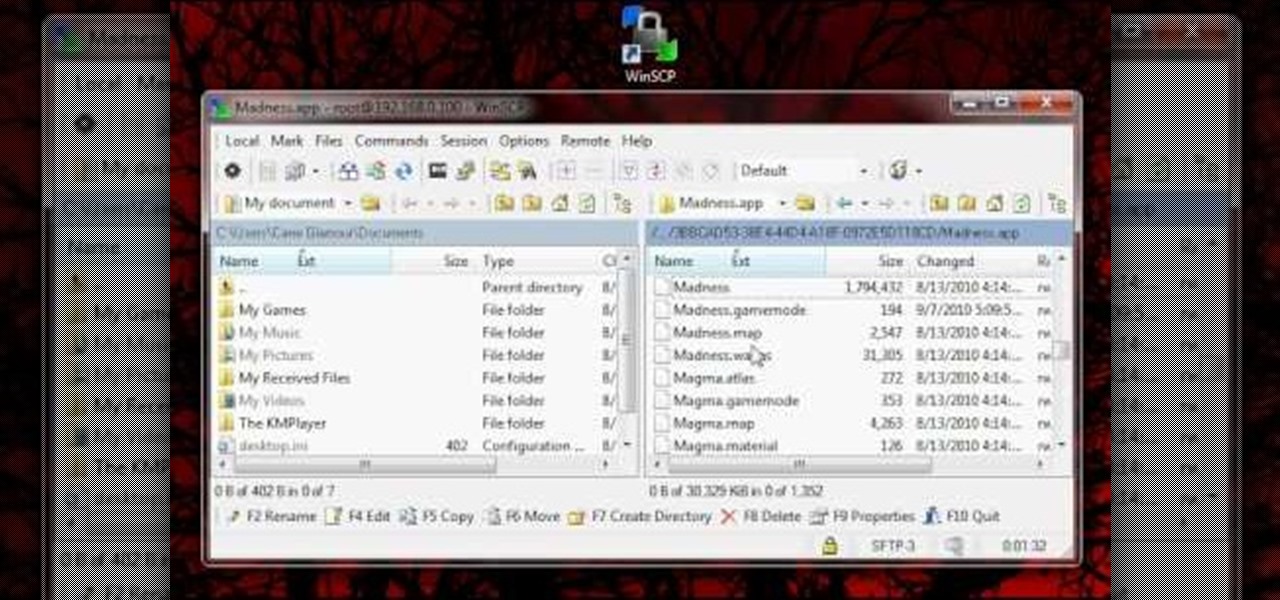
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory until you find the TowerMadness app. Once you have opened the TowerMadness app, all you need to do now is find the right file and change it around to increase the amount of money you have!

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.