In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

With a few hosting tips, you will perfect your Thanksgiving season! This craft shows you how to make some elegant place cards, some easy and beautiful napkin rings, and custom-made deocrative candles. Be the perfect host or hostess this Thanksgiving season!

This clip presents a number of tips on hosting an open house at your Pilates club or studio. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.

There are several types of barrier breaker glitches in Gears of War 2. The one described in this video might be the easiest one of all. It will allow you to escape from many multiplayer maps. The only caveat is that this won't work if you are hosting the game. Simple, get one of your friends to host and glitch on!

Get ready to dance "The Ellen!" In this tutorial, you will learn all of the steps to the dance that is sweeping the..morning talk show circuit.. The Ellen! This video, hosted by Forest Thomer, will show you step by step how to follow along to this dance and bop around with TV's favorite host.

Everyone loves a party—until the host’s pooch starts giving your leg a little bit of his doggie style. Show that canine he’s not humping any old bitch.

If you have your own domain, odds are you do things from FTP from time to time. In this tutorial, you'll learn a technique for making FTP shortcuts with the Windows HOSTS file, which will allow you to simplify the process. The time you save will be your own.

How to solve some of SC's common hosting problem, this clip is using LINKSYS but it can work with all routers in about the same way.

Ever wonder who's host in Halo 3? Well now there is a way to find out with this Halo tricks video.

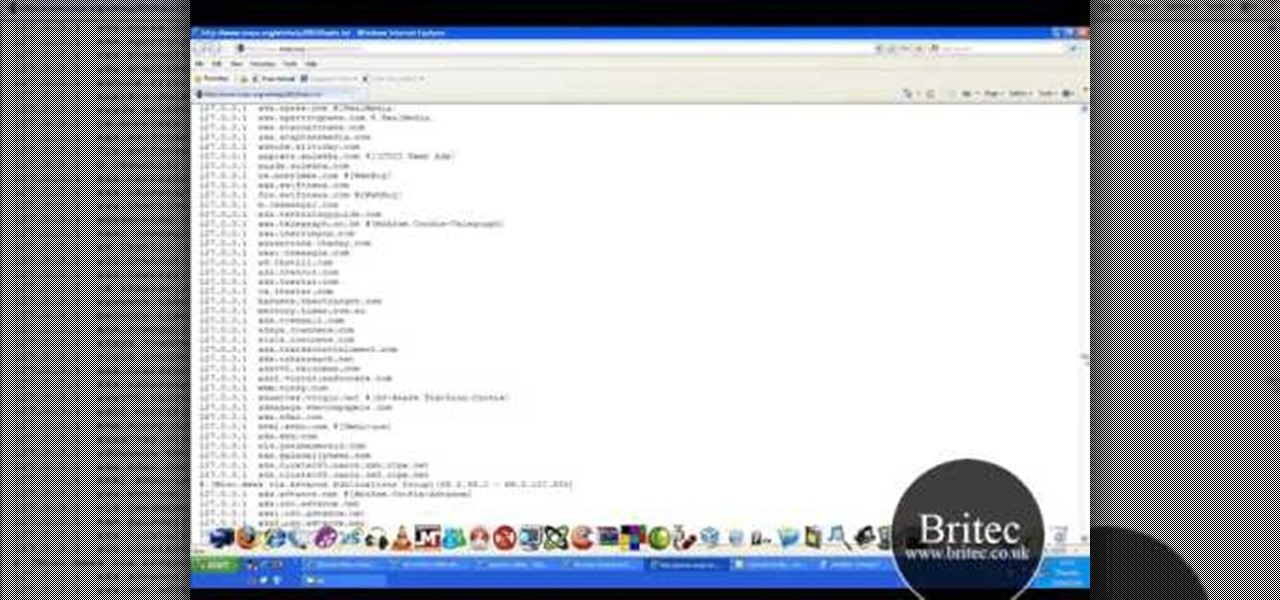
DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

Are you willing to do whatever it takes to gain host privileges in COD: Black Ops Annihilation Shangri-La Zombies? If you answered yes to that question, this is the video for you. Watch and learn how to use a lag switch to become host.

In this video tutorial, viewers learn how to create a FTP from a local computer to a website. In this video, viewers are shown (once you've chosen a web host) how to perform FTP file transfers from your local computer to your website. FTP (File Transfer Protocol) is a process that you can use to transfer files from your local computer to a remote computer (your website). Once you've set up a hosting account, your hosting company will provide you with FTP login credentials. Using an FTP softwa...

This video shows how to get more value on your GoDaddy account. You have to have a deluxe account to share domains. You have to pay an extra $2 a month to get this account. Once you sign in go to "hosting" then my "hosting account". To add another domain you move it over to a new folder then put the site files in there. To do this, click add domain then go to bulk. Then create a folder and name it what you desire. Sometimes the file folder doesn't always appear immediately, but it is there, i...

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

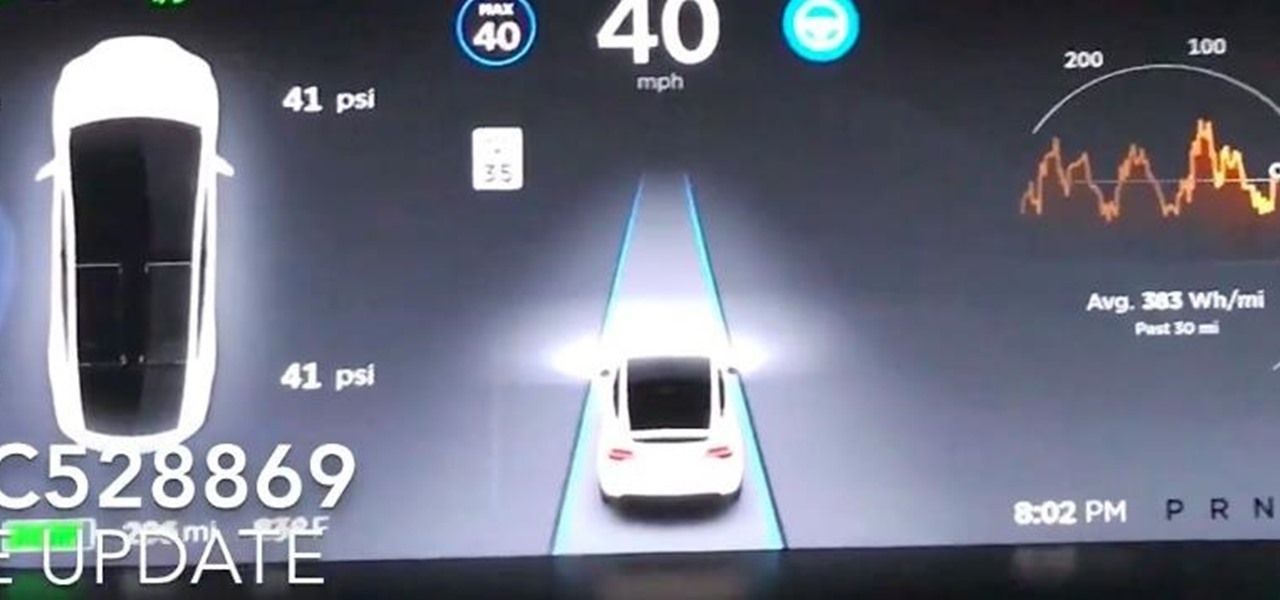
Some drivers give Tesla's Autopilot update released this week rave reviews, after version 8.1 has taken longer than expected to live up to Elon Musk's "smooth as silk" Tweet from earlier this year.

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

Cityslipper shows you how he uses the cleft grafting method to make a less appealing green apple tree produce better tasting red apples. 10-12 inches long scion wood is collected from the good apple tree while it is dormant. Care is taken not to let the twigs dry out. Selected scions should not have spurs rather they should have leaf buds that lay flat against the twig. A good host twig on a healthy-looking branch should be selected. A clean cut should be made with the fine teeth of a grafing...

Fetch is an FTP program for Macs (Smart FTP can be used if you don't have a Mac). These can be downloaded from Download.com

To make quick and easy cornbread in a truck, the host only needs jiffy corn muffin mix, egg beaters instead of whole eggs, and a little bit of milk. The ingredients are combined in a bowl, then poured into a disposable baking tin. A Crockpot is used in place of a traditional oven for baking by removing the glass interior. Place the tin with the mix directly inside, and cover until baked fully. The host usually uses a small tin that will fit easily inside the Crockpot, but if only a larger one...

AMICLUBWEAR created a tutorial on how to host a tea party based on "Alice in Wonderland". The video begins with a step by step instructional on how to make tissue paper "flowers" as decorations for your tea party. The tissue papers are layered in opposite colors, after which the tissue paper is accordion folded and tied together using a pipe cleaner. Afterwards, the tissue paper is carefully extended layer bay layer and shaped into a flower. Next, there was a tutorial for making the "EAT ME" ...

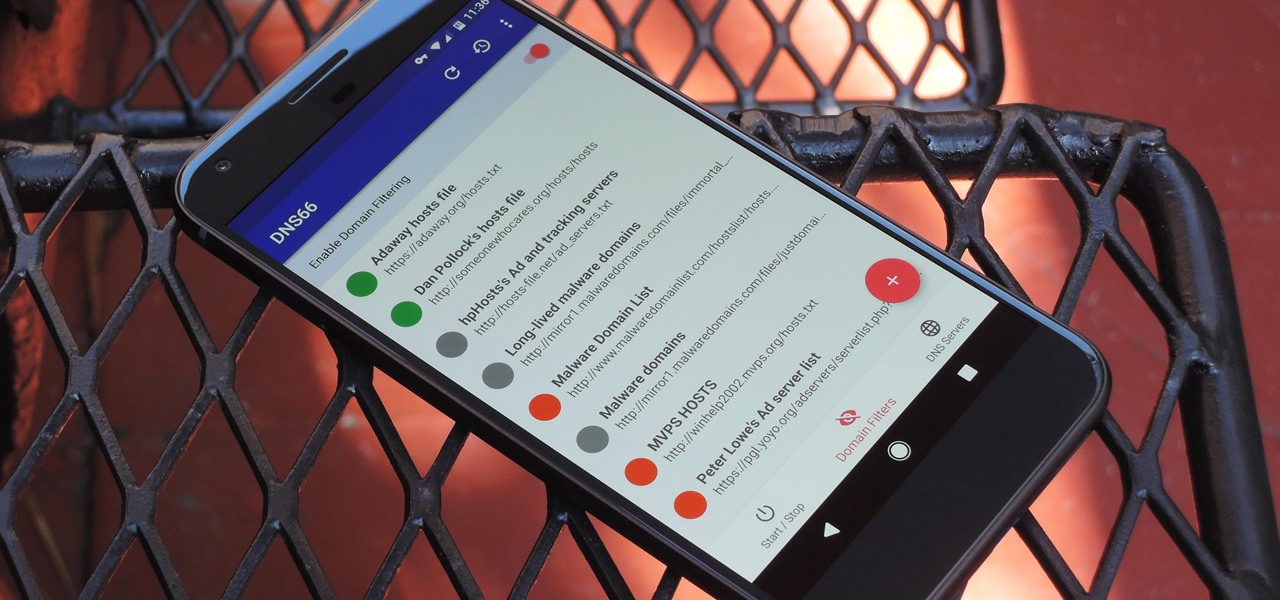
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

Want to know how to block websites on a Windows XP PC by editing the HOSTS files? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to share files between Ubuntu (Host) & XP (Guest).

LX.com's Shira Lazar visits Grace Restaurant to receive expert tips on tasting, serving, and picking out the perfect wine for your wine party. Wine tasting can be an elegant gathering, or a fun party with friends. Wines should be selected with the food serving in mind. Learn how to host a wine tasting party by watching this video tutorial.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

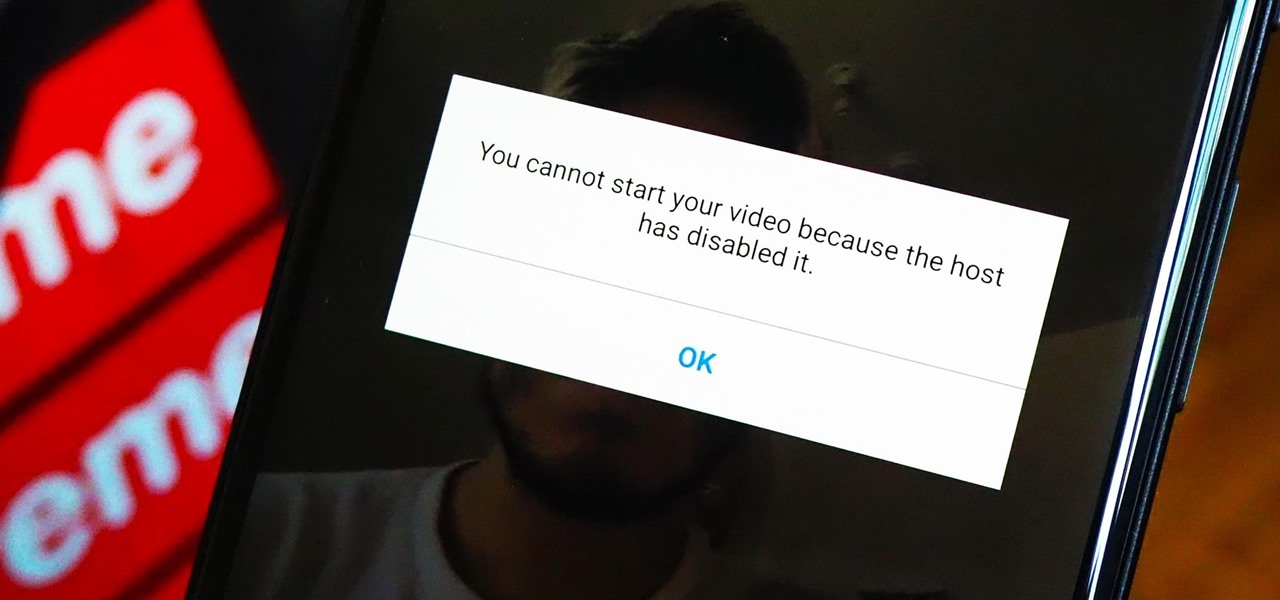
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Ramadan, the Islamic holy month of fasting and prayer, is underway, and Google has rolled out several tools to help Muslims commemorate the event, including an augmented reality app.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

If you've been debating on whether or not HTC's new virtual reality headset, the Vive, is worth the $800 price tag, then you'll be able to find out for yourself soon enough.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

Even if you decode the laundry symbols on the tags of your clothes and follow them perfectly, using the washing machine tends to change their shape and fade colors over time. And whether you spent $20 or $200 on them, there's nothing worse than having your favorite pair of jeans ruined.

In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.