Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.
If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

You can use MMS and Tethering on the iPhone 3GS. So first go to the settings and there you have to click on general and then go to network. there you can see Cellular data network, VPN, internet tethering etc.

If you're concerned about your data ending up where you don't want it online, then a VPN is something you'll want to consider. A VPN can prevent your bank account information from leaking, your data from being taken directly from your device, and it doesn't come at the cost of any of the convenience we've grown to expect and require from the internet.

Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

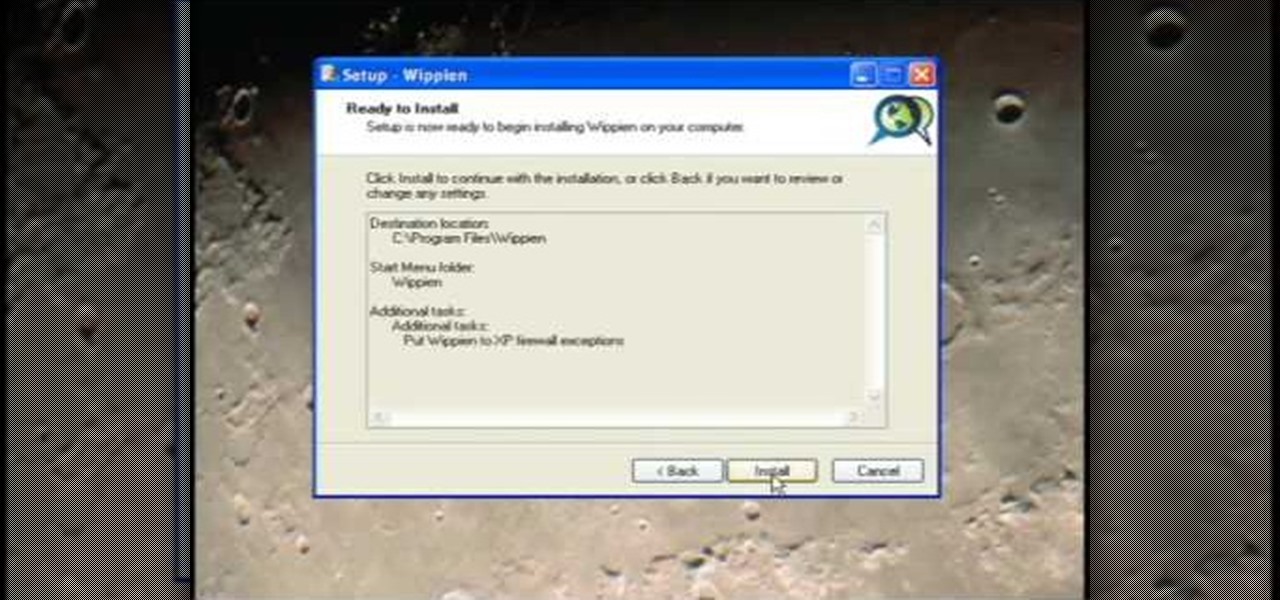
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.

The purpose of this video is to show an e-mail security flaw using telnet that allows hackers to send e-mails using anyone's e-mail address. Thankfully, many major e-mail providers have software that blocks this. My intention is to make people aware of this flaw so that other e-mail providers can protect themselves as well.

Update: HBO discontinued this service. Your best bet for transferring your data from one account to another is to save a record of your watch list. That way, you can add your titles back manually with your new account.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

So you've got a Blackberry 8830 or 9530 Storm, but you are not down for the default service provider that comes with the phone. Using this simple software hack, unlock the your Verizon phone to work with Cricket, Metro PCS, or any other CDMA provider.

Join Patrick Hynds as he demonstrates how to set up the SQL Membership Provider to add Forms authentication to your ASP.NET 2.0 Web site, in this video tutorial. There are a few tips and tricks involved, such as using the aspnet_regsql.exe utility, which are covered in the video.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

NetGuard is a well-established app known for its highly secure firewall, which blocks unwanted web activity from individual apps that can take up both precious bandwidth and battery life. Not quite as well known, however, is the fact there's a second official version of NetGuard that comes with a hidden ad-blocking feature, which can be activated with just a little tinkering in the app's settings menu.

This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information on this hack, watch this helpful video guide.

The iPhone has always been hamstrung by its alignment with AT&T, the worst of the big 4 US cell service providers. If you have an iPhone and are planning on unlocking it for use with another provider, or just want to use it without being connected to AT&T's network, this video is here to help. It will show you how to activate an iPhone instantly without a service plan using any AT&T SIM card.

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.