Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.
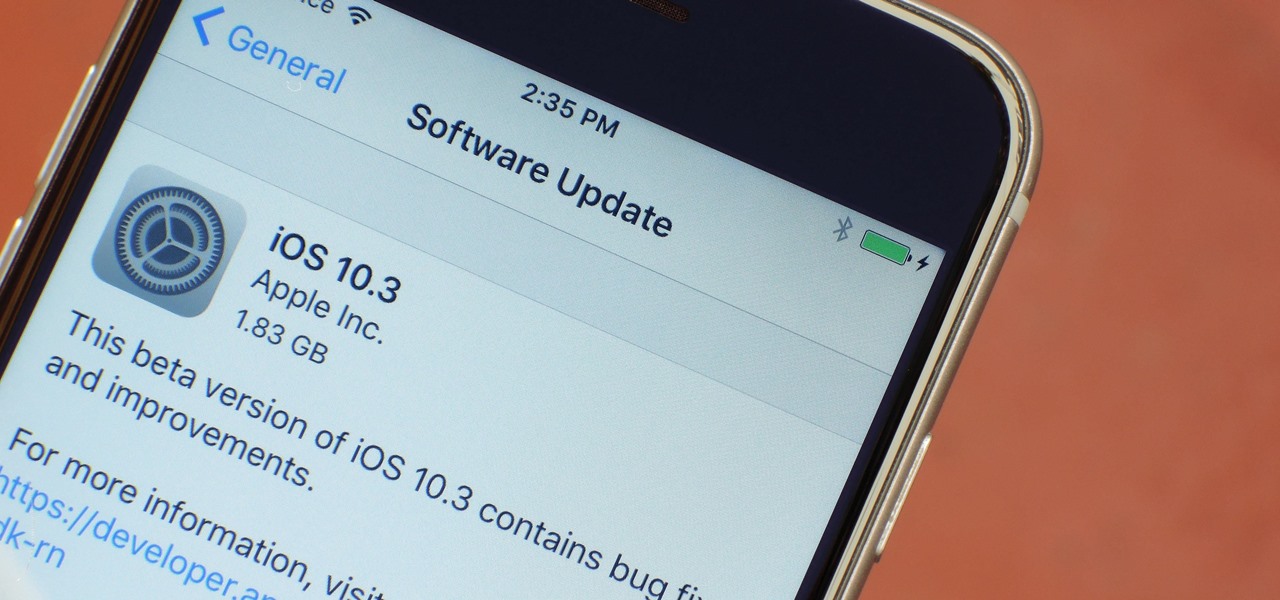
Apple just pushed out the iOS 10.3 update to everyone on March 27, so if you haven't installed it yet, make sure to do so by going to Settings -> General -> Software Update. Trust us, you'll want to.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

From Time Machine to Cartoon 3D Style, Snapchat has strung together a run of viral AR Lenses as consistently as Beyoncé drops hits songs.

Google Maps Live View is already one of the more useful examples of augmented reality on smartphones that is available to the average consumer today.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

Snapchat's face tracking has certainly come a long way. This week, we've got an example of one effect that is nearly guaranteed to freak out your friends.

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Wall studs are both critical for maintaining the structure of your home and supporting items of weight and function on the interior walls (e.g. cabinets, shelves, plasma TVs, etc.). With wall studs playing such a critical role, consistently being able to find them is important. The problem with finding them is that drywall and wallboard isn't exactly see-through.

Mimmo Rubino applies the art of brain melting to the streets with his perspective-distorting, optical illusion graffiti art. The coolest part is Mimmo includes links to Google Maps for some of the pieces, so you can go take a look for yourself (if you happen to be in the vicinity of Rome).

ISOPLETH 63 points (13 points without the bingo) Definition: a type of isogram [n]

ZERO WASTE. Yes, You read that right. This kitchen of the future aims to have zero waste. Ekokook the kitchen concept out of design company Faltazi gives us hope for a greener future. How is this possible you ask when in most homes 85 or 90 percent of a family's trash is generated in the vicinity of the kitchen? Ekokooks kitchen system is divided up into disposing and storing your waste in three mechanized sectioned systems Solid Waste, Liquid Waste and Organic Waste. Solid Waste- The solid w...

Aesthetic Houses: What are they? If you've played Minecraft for some time now, you most surely know how hard it is to build a great looking house to live in, that meets both your vision of your dream house and expectations for functionality. This brings us to the definition: in terms of Minecraft, its a structure that dosen't compromise beauty and appeal for functionality.

Tera Online is a beautiful Korean MMO with real time combat. The game is coming to the states towards the end of the year. Unlike other MMOs were combat is target specific (lock on target) and dependant on skill timers and macros, Tera Online focuses on fast area of effect action. Your blade or spell will hit whatever is in front, or miss if it's not. The closest thing to the game play of Tera is Vindictus, a free to play MMO with the same concept of game play. If you've played Vindictus, the...

Red Dead Redemption is hard to pin down in game play and story. The game offers this massive multi-layered world in which the player can roam freely, offering plenty of challenges, beautiful graphics and atmosphere for the player to experience. Yet after some point the whole world feels barren and unchangeable, and your achievements are nothing more than a trophy that does not matter in the sandbox world the player resides in. The story, told in three arcs, offers an inconsistent narrative of...

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Simple test of endurance: light off several fireworks placed in your pants pocket, belt, socks, and in close vicinity.