Solving equations involving fractional powers of a variable are not that hard to solve as they sound. In fact, just watch this video to learn a few tips and solving these type of equations will become a little bit easier.
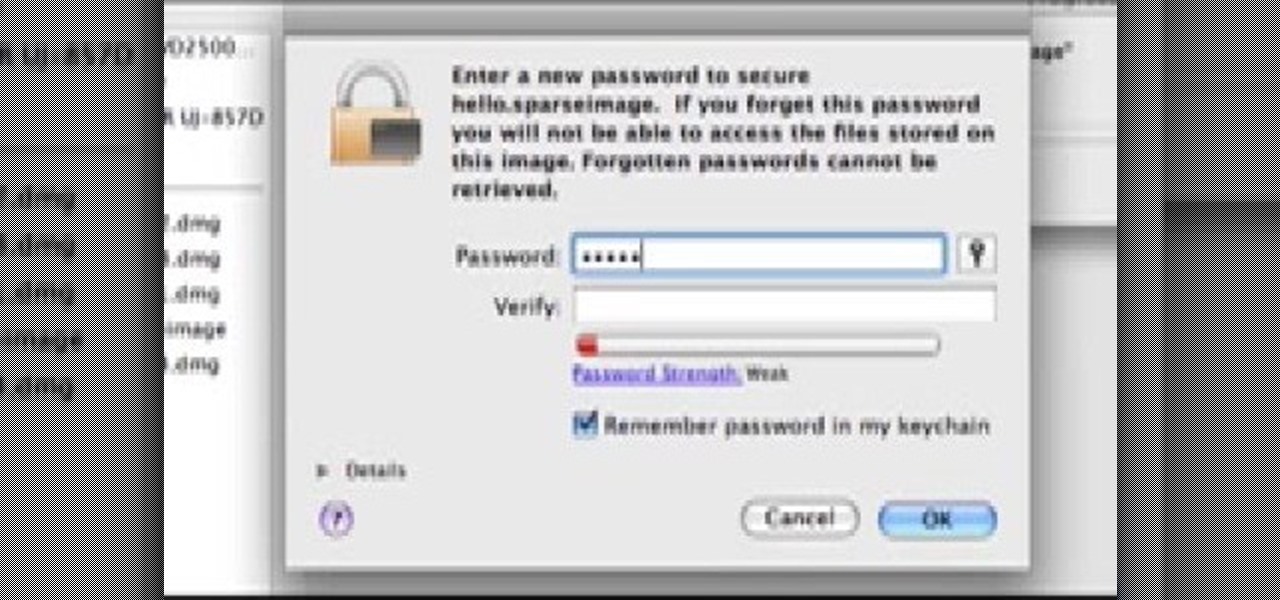
In this tutorial, we learn how to password protect your folders on a Mac computer. First, use the spotlight tool to type in "disk" and then click on disk utility on the drop down menu. From here, go to the save as menu and enter in the name for the volume. After this, change the size of the desktop and change the encryption choice. Use the one that is recommended and then click on 'ok'. Form here you will be asked for a password, then you will need to verify that password. From here, click on...
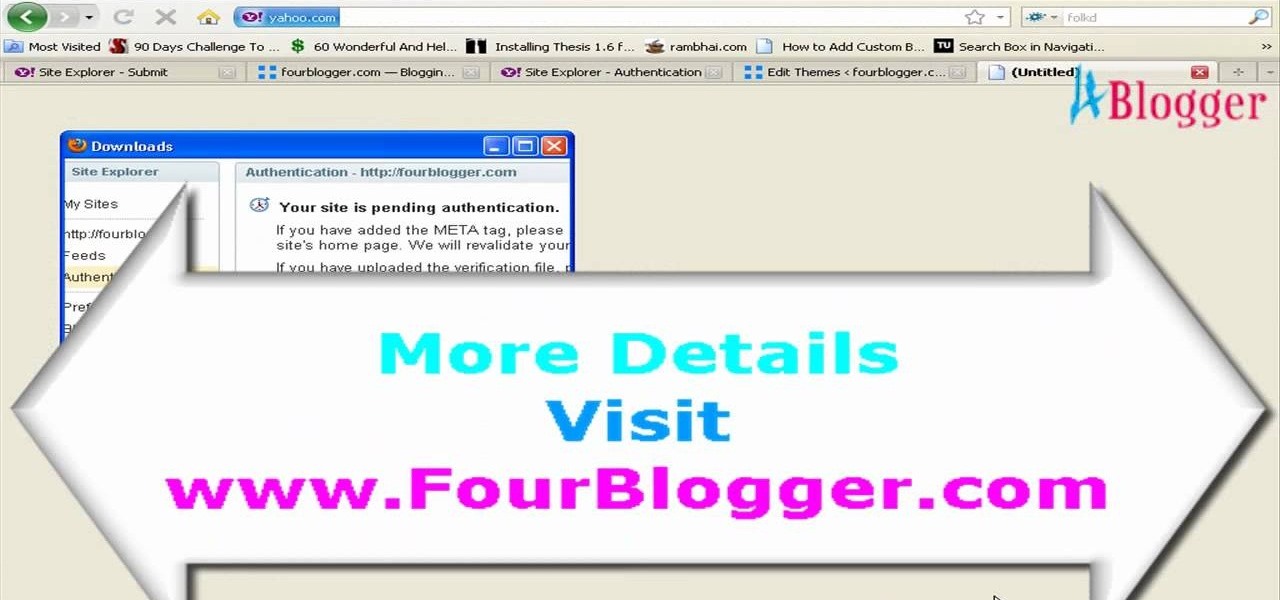
In this video, we learn how to submit your site to the Yahoo search engine. First, go to site explorer. Once here, submit your website or web page in the appropriate box. After this, enter the full URL of the site feed you want to submit. After you do this, go to the side bar and verify your site, or add a META tag, then go to your site. Now, copy the code that Yahoo gave you and paste it into your website. After you do this, your site will be submitted and you can search for it through the Y...
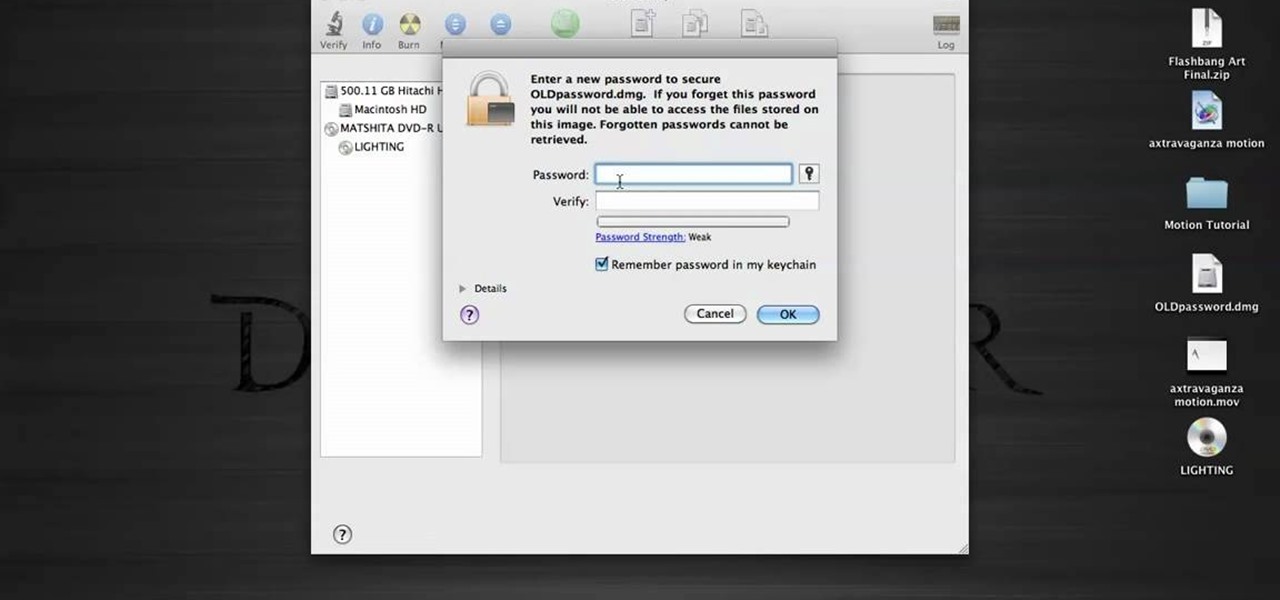
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder so you still can edit the files and enable the encryption. Save this, then it will ask you for a password. Create a password and then verify it. When finished, uncheck the "remember my password", then click on "ok". Now...

In this video, we learn how to get credit when you don't have any. Most credit agencies are now gathering information about younger people to figure out if they are allowed to get credit cards, which will help them build a credit score. There is a website, PRBC, where you can start a file and enter your information, and it can verify all the information you report. This information will be given to credit reporting agencies, and give you more of a chance to get credit. Next, you can get depar...
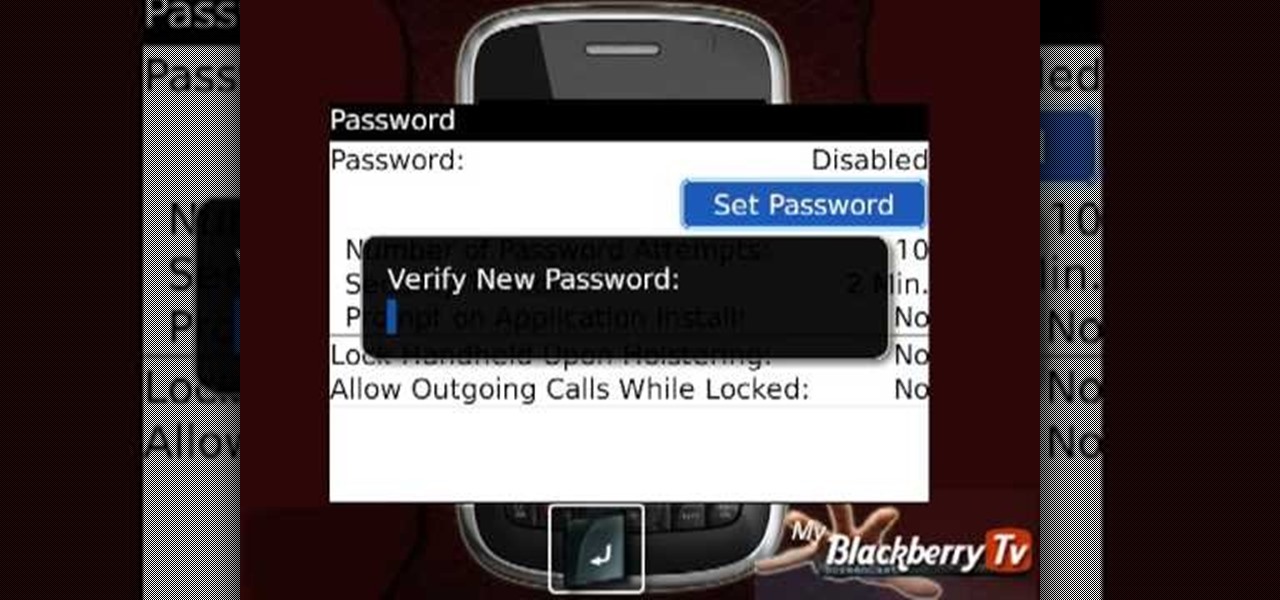
My Blackberry TV demonstrates how to protect your Blackberry device with a password. Protecting your Blackberry with a password will help to stop people from accessing your personal information on your device. From the home screen, press the Blackberry menu key. Then, select the options choice. Next, scroll down to the password choice on the options menu. Select password and then select the set password button on the password screen. Enter your desired password and then press the enter key. V...

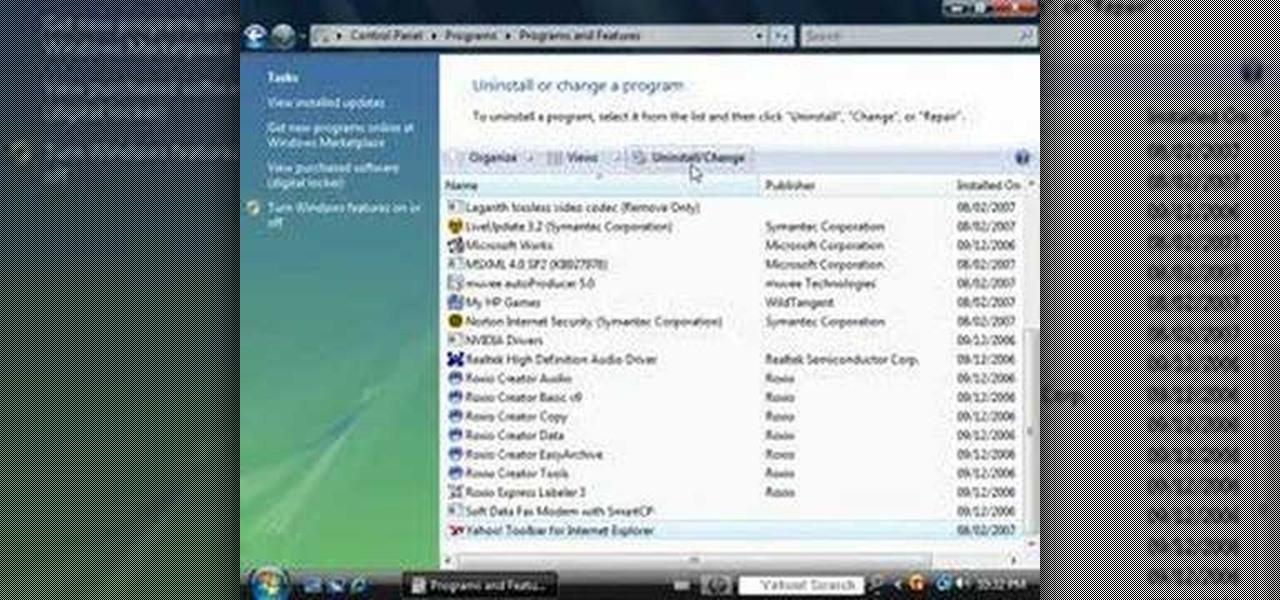
1. Go to Control Panel from the start menu and select Uninstall a program. 2. Start Menu>Control Panel>Uninstall a Program

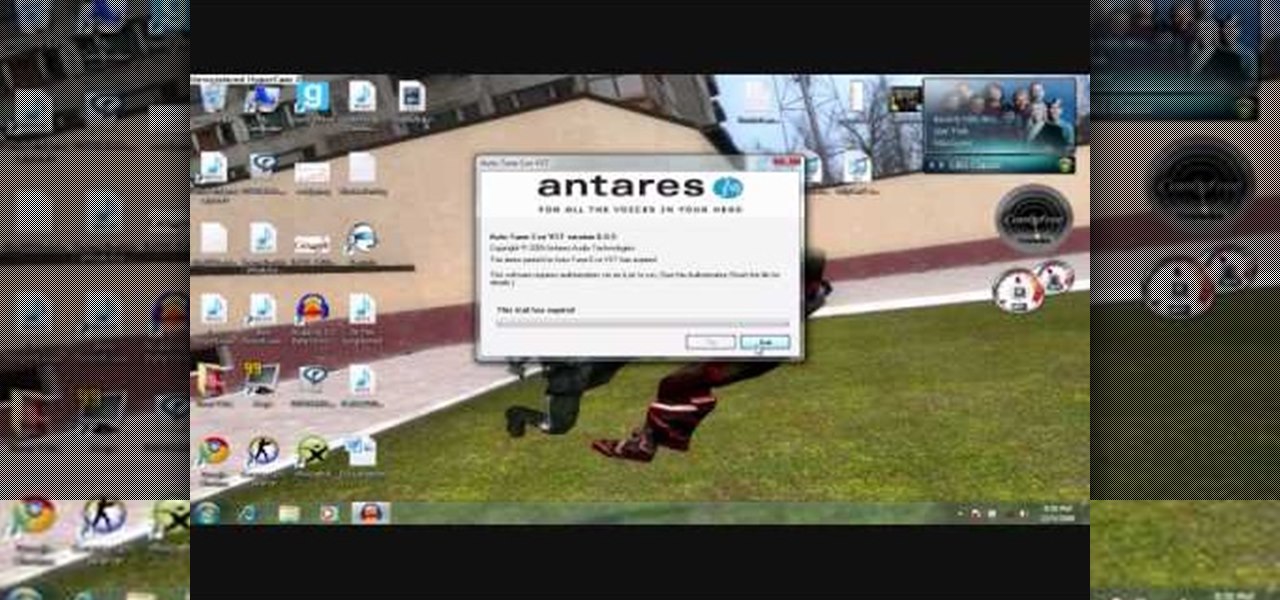
To get autotune on Audacity, you will need to have the 1.3.10 beta version from Audacity's website. Verify that you have autotune or G-snap in the plug-ins. You may need to download G-snap from the internet. First, open up Audacity. Then, go to edit and select preferences. Go to effects and click rescan BST effects next time Audacity is started. Then, click the okay button. Close out of Audacity and then reopen it. The program will then import your new files. Your new files will then show up ...

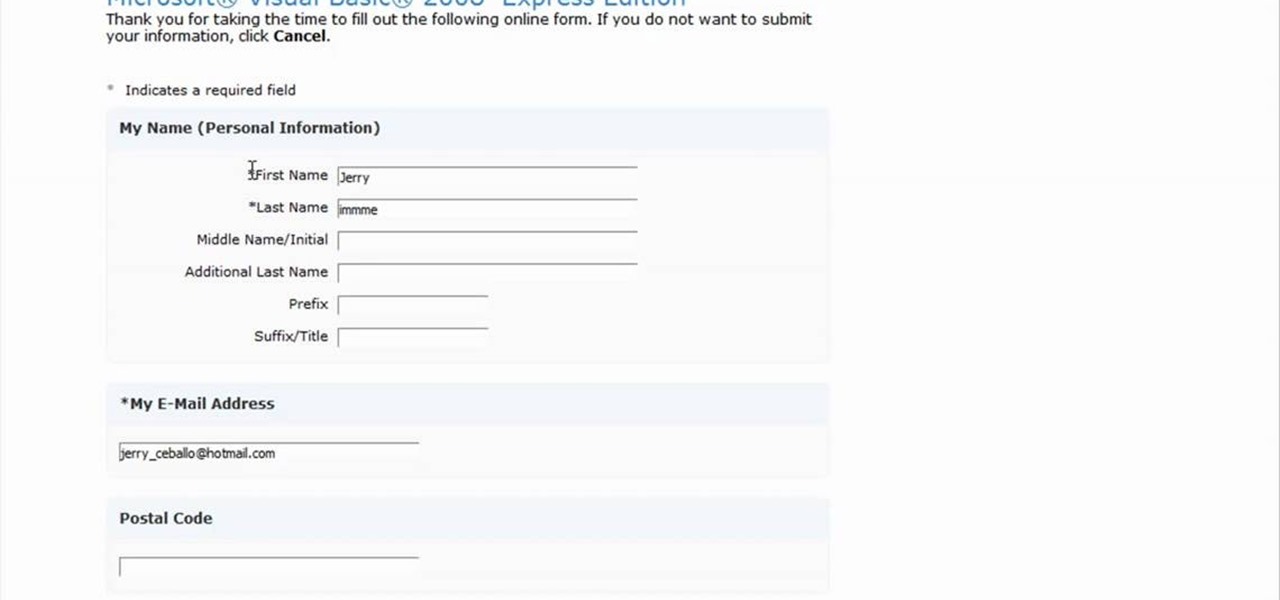
Registering Visual Basics 2008 express edition is quite simple. It is a free registration. First open visual basic then go to the help option. Register the product and click on register now. It will ask you to sign into Microsoft email using your Hotmail account or if you do not have one you can create one and use it there. Use your user name and password where it asks to verify. Fill out all the form information, it may be real or fake, it does not matter. Then you will come to a registratio...

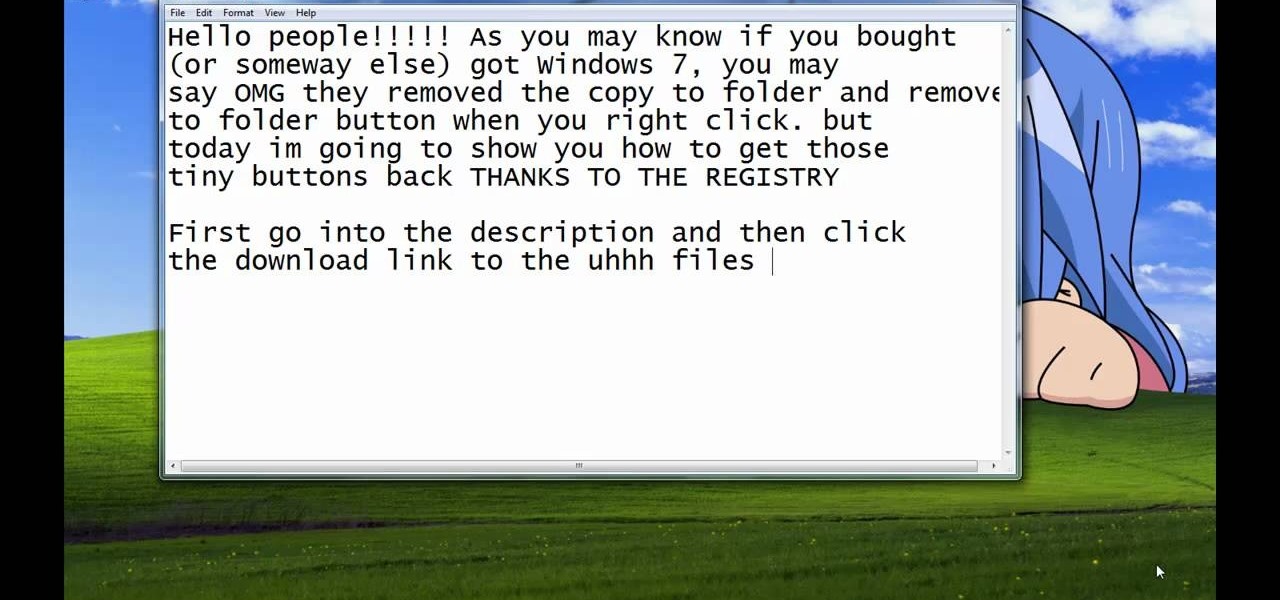
Steps taken to get the Copy to and Move to folder function in Windows 7 are:1. Go into the description and click the download link, to download the files2. After downloading the registry file you will see a zip file, which you need to extract using the software called Win Zip.3. After extracting the zip file, you will see two registry file (copy to and move to) execute both the registry file and give Yes, so that the file gets installed successfully.4. After successful installation, it is rec...

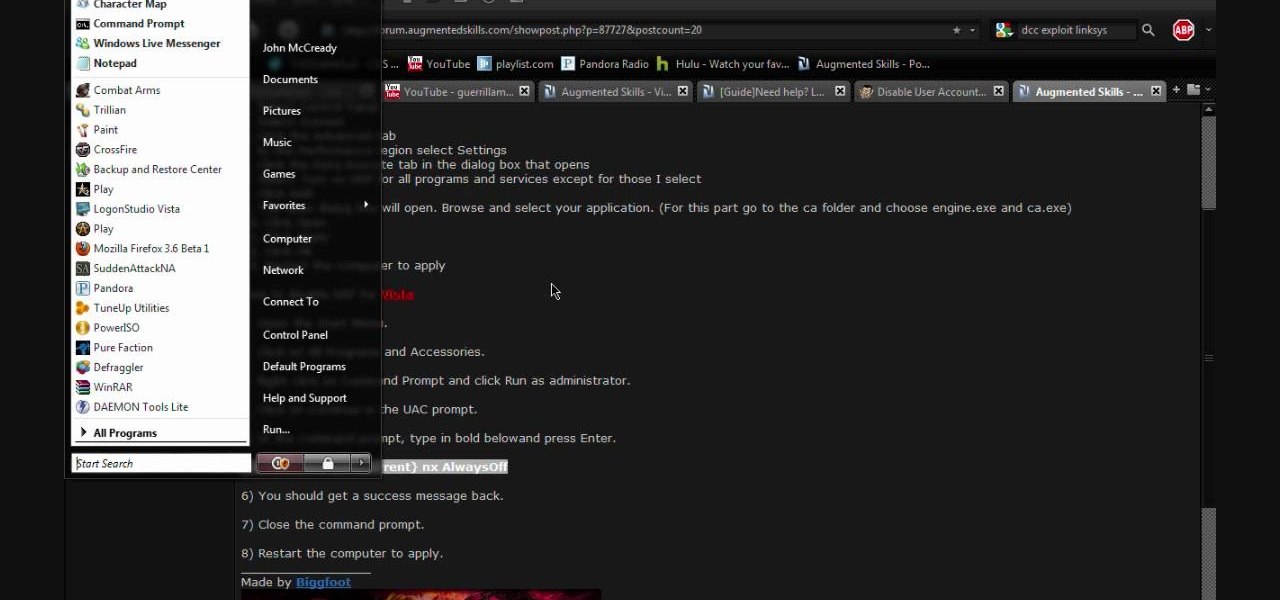
This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

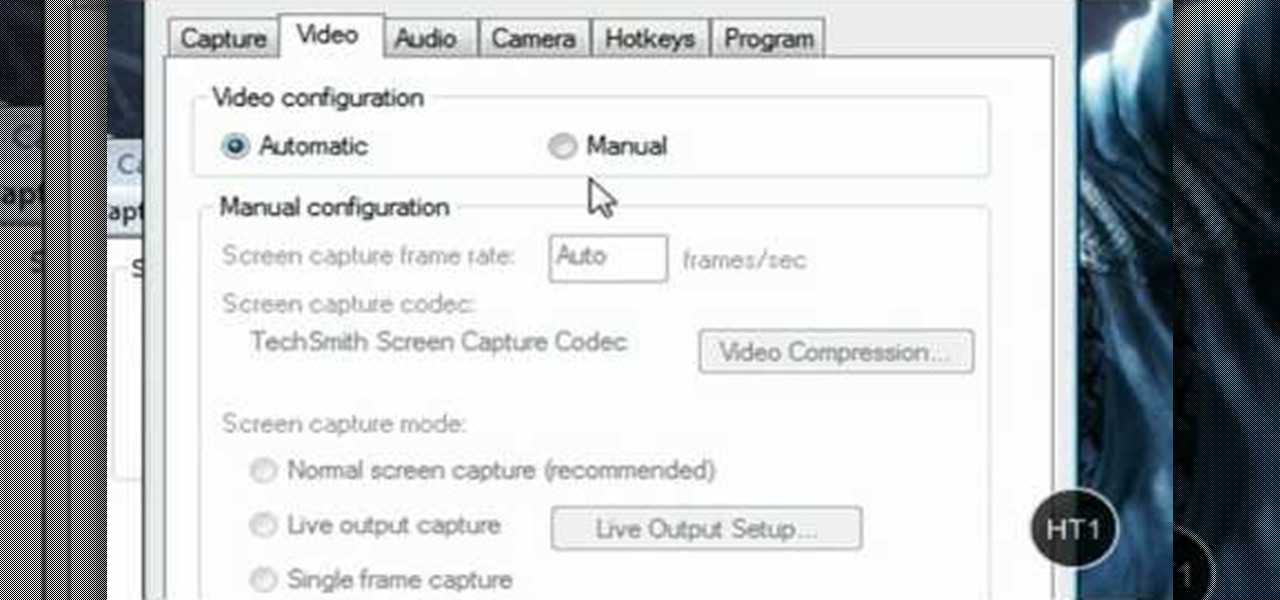
HelpTube1 teaches you how to improve video quality when recording with Camtasia. The reason some videos don't have the HD version is that it takes 30-40 minutes for YouTube to verify whether the video is in high definition or not. In Camtasia 5 there is a Tools tab at the top of the program window. Click on that and then go to Capture. Check the box that says Save as AVI. Then go to Video, change Manual and change the frame rate to 80. Then click Ok and you will get these options every time. ...

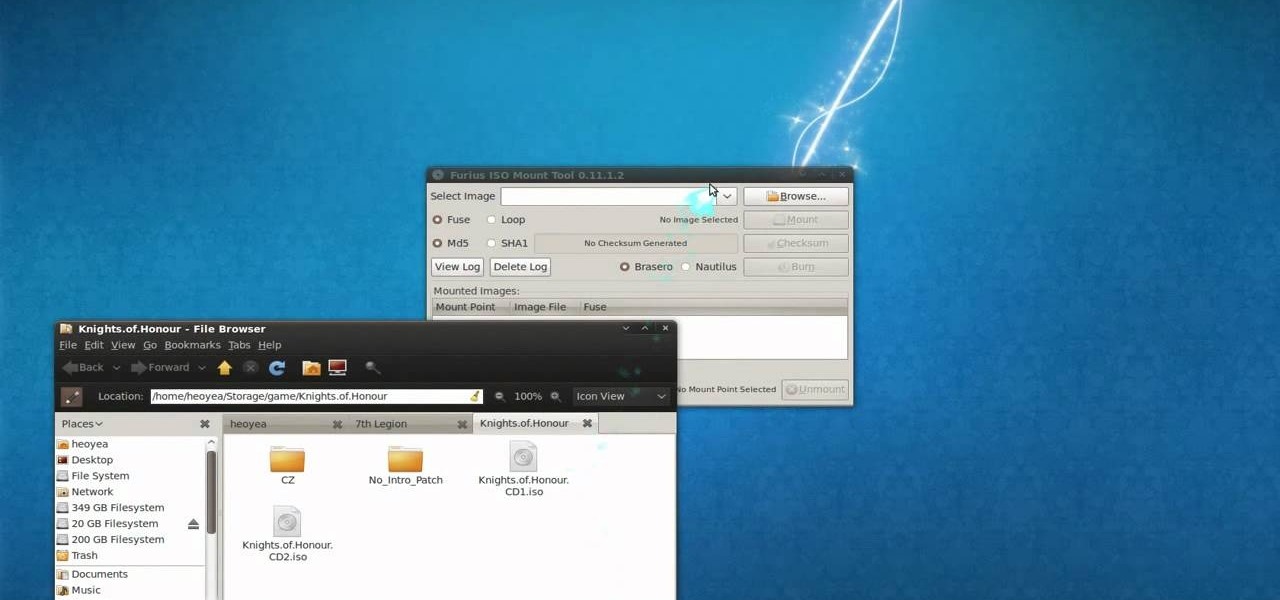
This is a tutorial video on how to use a virtual CD/DVD drive software tool called Furius ISO Mount. Furius ISO Mount is an .ISO, .IMG, .BIN, .MDF, and .NRG image management utility, that allows you to automatically mount and unmount disk image files. This utility application will allow you to mount multiple images at once, burn image files to optical disk, and create MD5 and SHA1 checksums to verify the that the image files are not corrupted. This program also automatically creates mount poi...

mybigleftnut90 teaches you how to burn Wii backup games for Mac. After you get a backup game for the Wii, you need to make sure the DVD you'll be burning it too is DVD-R as these work best. Also make sure that the size of the backup game is not larger than the blank DVD you have. Right click on the image and click on "Open with-Disk utility." In the new program window, you click your image file name and click the button "Burn" at the top. Your speed should be 2x or 4x. Unclick verify burned d...

After you've already taken your PS3's Blu-ray Disc drive apart and fixed anything necessary (or maybe nothing at all), you going to have to reassemble the drive (obviously). This video teaches you how to do just that.

Many people have complained about the lack of autofocus in video mode on the Canon 5D Mark II. Fortunately, this video demonstrates a solution by utilizing the live mode, thus enabling the still camera's autofocus features.

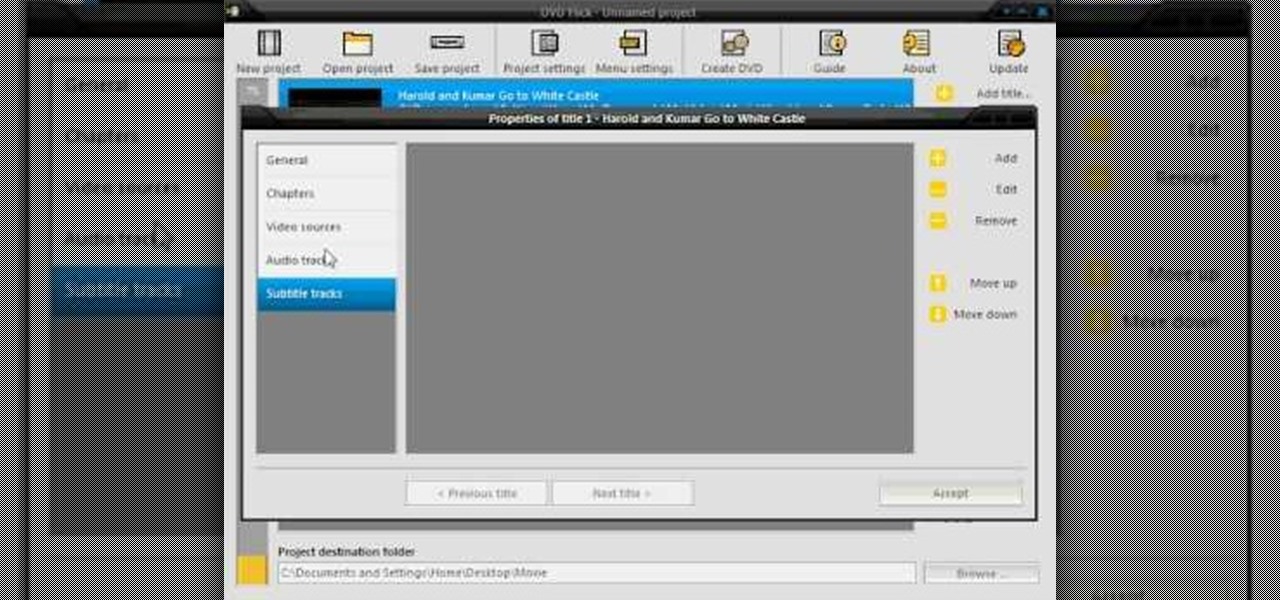
Burn downloaded movies onto a DVD. Open your browser, go to the Google website and type axxo torrents in the search bar. Then select the homepage of axxo torrents, and download the favorite video in to your computer. Then open the DVD flick, you select burn a DVD. In that you select the files to be burned on to a DVD, and then click ok. Then the general settings appear on screen, about the name of video. Then also select how to burn and writing speed, and check the box of verify the data on w...

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

In this chess video tutorial, Grandmaster Alexandra Kosteniuk, with guest star Almira Skripchenko, will show you how to checkmate in just two moves that the Fritz 10 software program doesn't even recognize. Fritz 10 just can't solve this mate in 2 chess problem.

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Snapchat has had more than its fair share of security failures and mishaps. The photo-sharing company is looking to better address some of these security gaps by adding new features, and today its most recent addition is live: the Captcha. New users will be asked to verify their "humanness" by selecting the infamous Snapchat ghost out of a selection of images. The feature is supposed to help block hacker-made bots from creating fake accounts or accessing existing ones. But rather than using t...

Samsung and Hulu have gotten together in a big way to partner the Huluplus interface with Samsung TV's and Blu-Ray players and allow Samsung users easy access to Hulu's massive library of TV shows and movies. This video will show you how the system works on a Samsung Blu-Ray player.

Are you tired of keeping all the music on your mp3 player to yourself? Share it with the world by hooking your mp3 player up to a radio and using the speakers for output. This simple radio hack of connecting a capacitor to the potensiometer will bring you endless hours of music enjoyment.

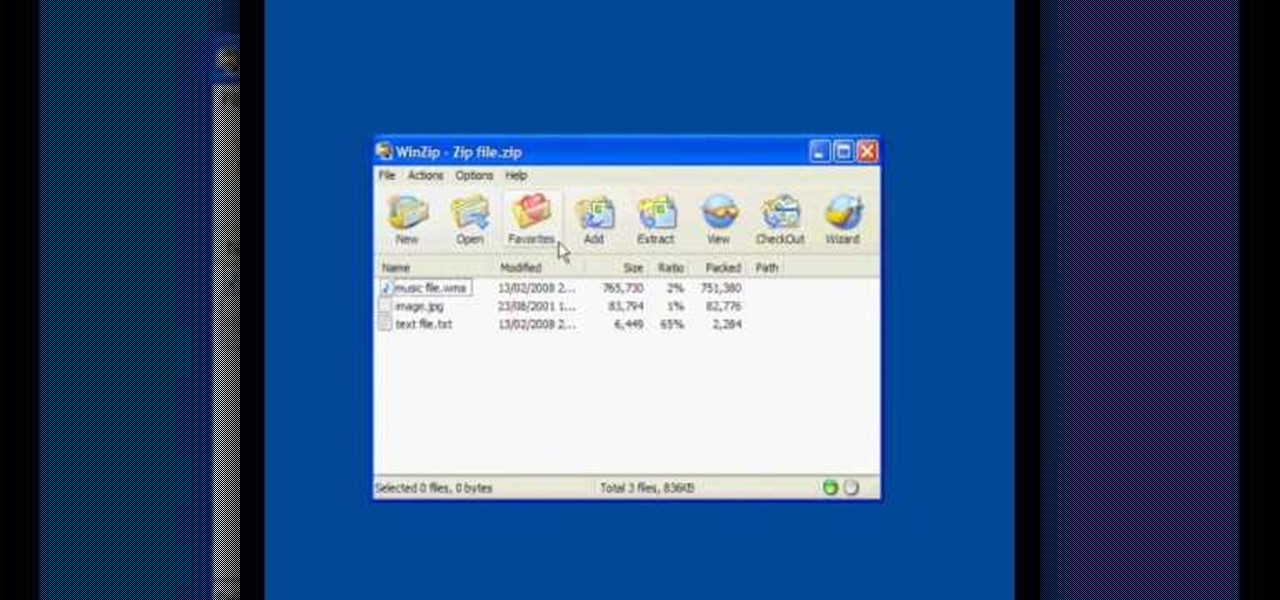
Do you have a hard time extracting/unzipping files using WinZip? If you follow along we will be shown a couple simple steps on how to unzip files using WinZip.

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Portable video players often provide an all-in-one solution for listening to MP3s, watching videos and even playing games. Find out which one is right for you.

This video demonstrates how to hook up a DVD player. The cute part is the DVD player is sponge bob.

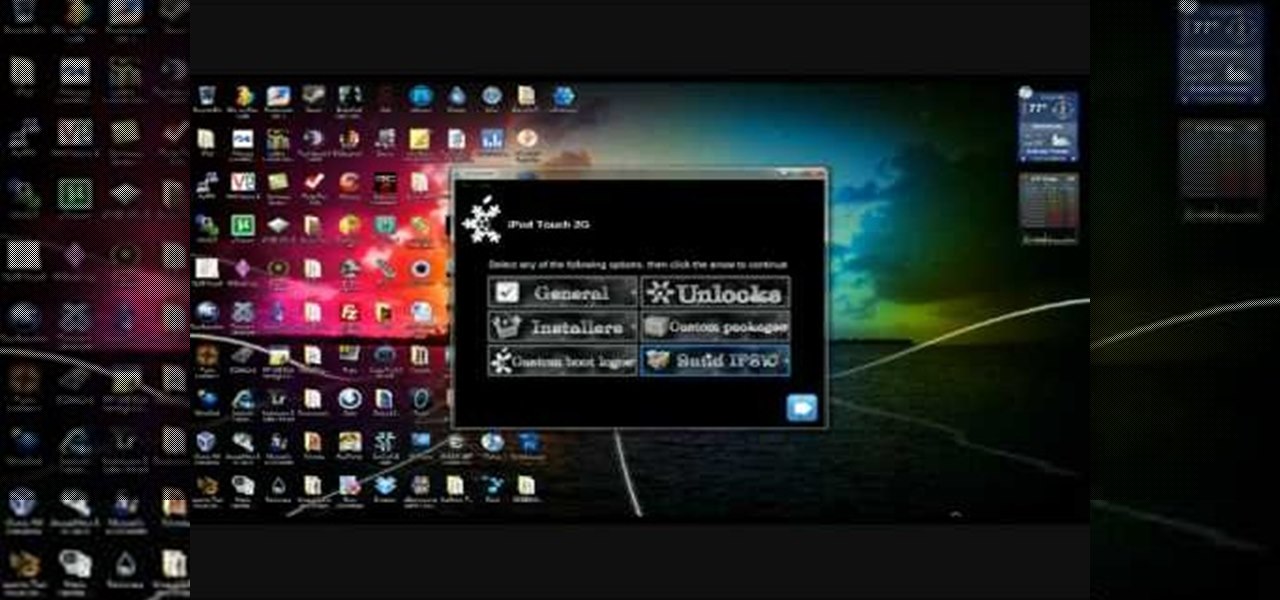
In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!

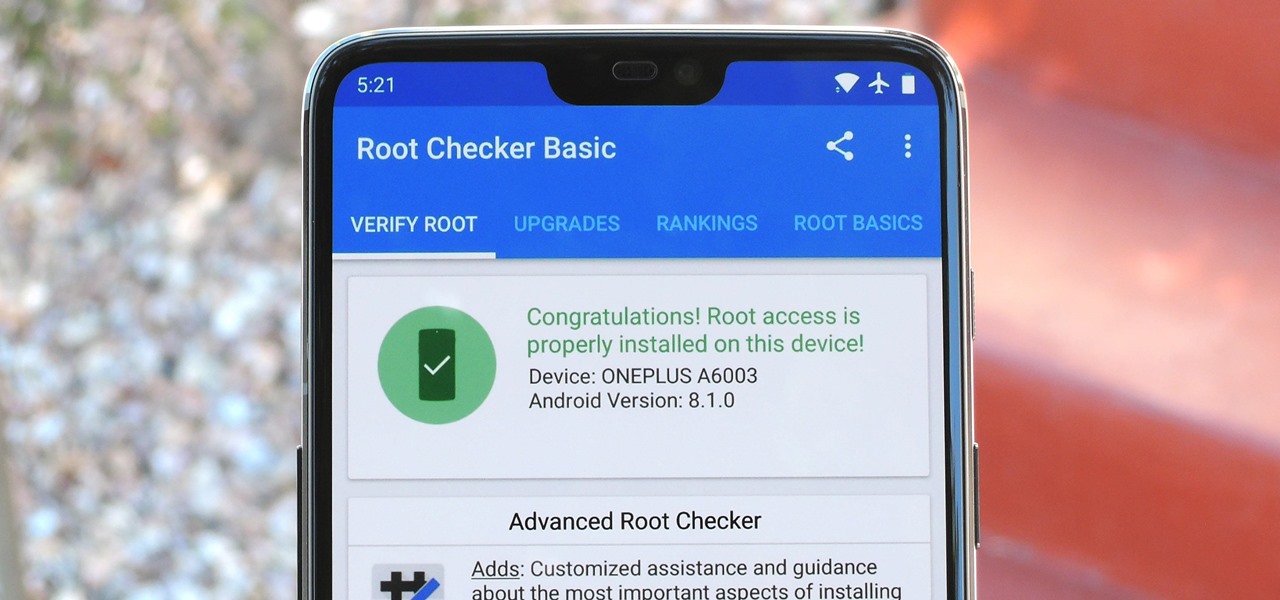
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

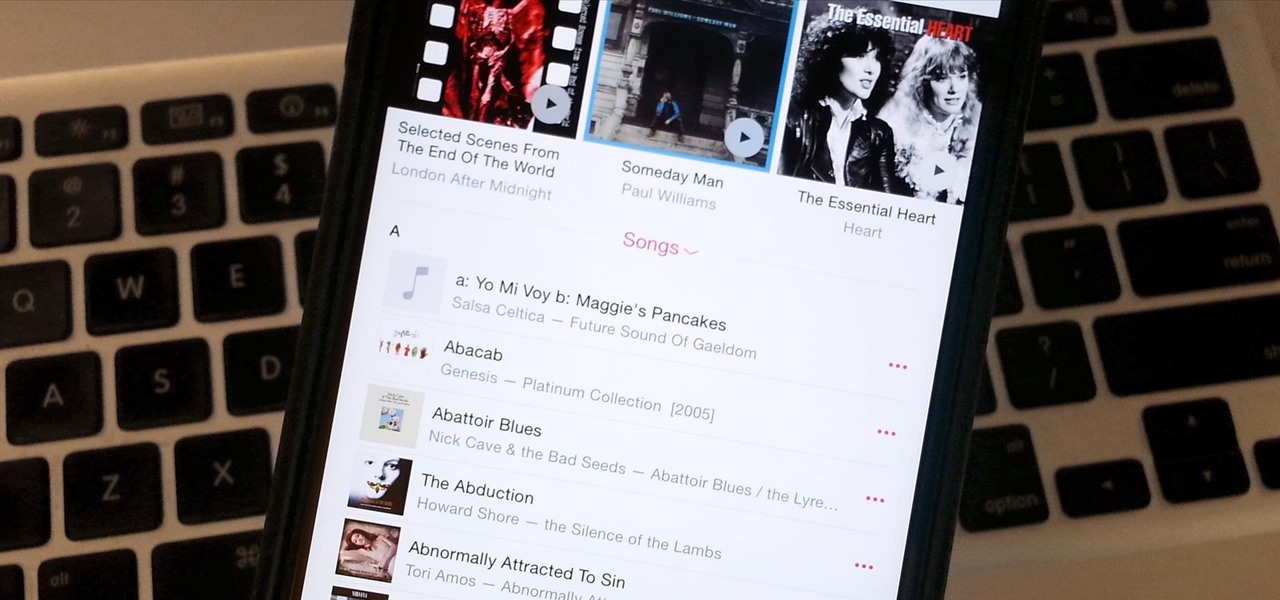
If you updated to iOS 8.4 already to try out the new Apple Music service, there's one important change you need to know about—there's no longer a "Shuffle" option for all songs in your library.

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

Silence can therapeutic at times, but unsettling at others. When I'm in bed at night, I need some sort of background or white noise to help me fall asleep. Pure silence just does not do it for me. Whether it's a fan oscillating left to right, or the TV playing, I need background noise to soothe me to sleep.

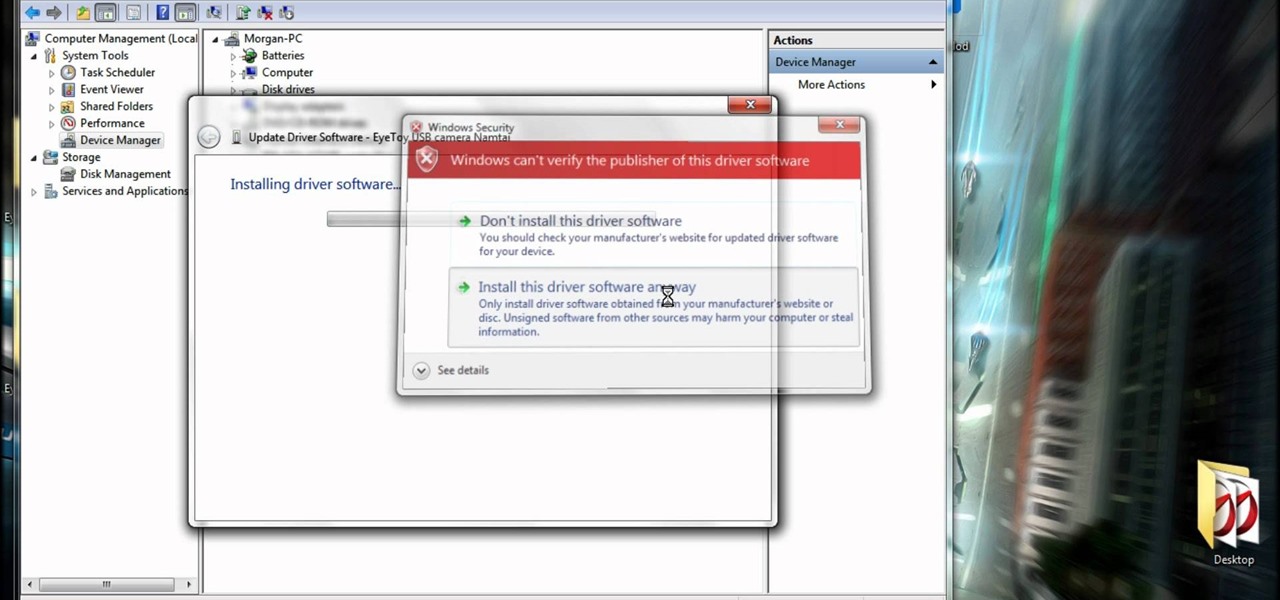
If you have a PS2/PS3 Eyetoy, but don't want to go and spend $30+ dollars on a new webcam, then this is for you.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.