After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.
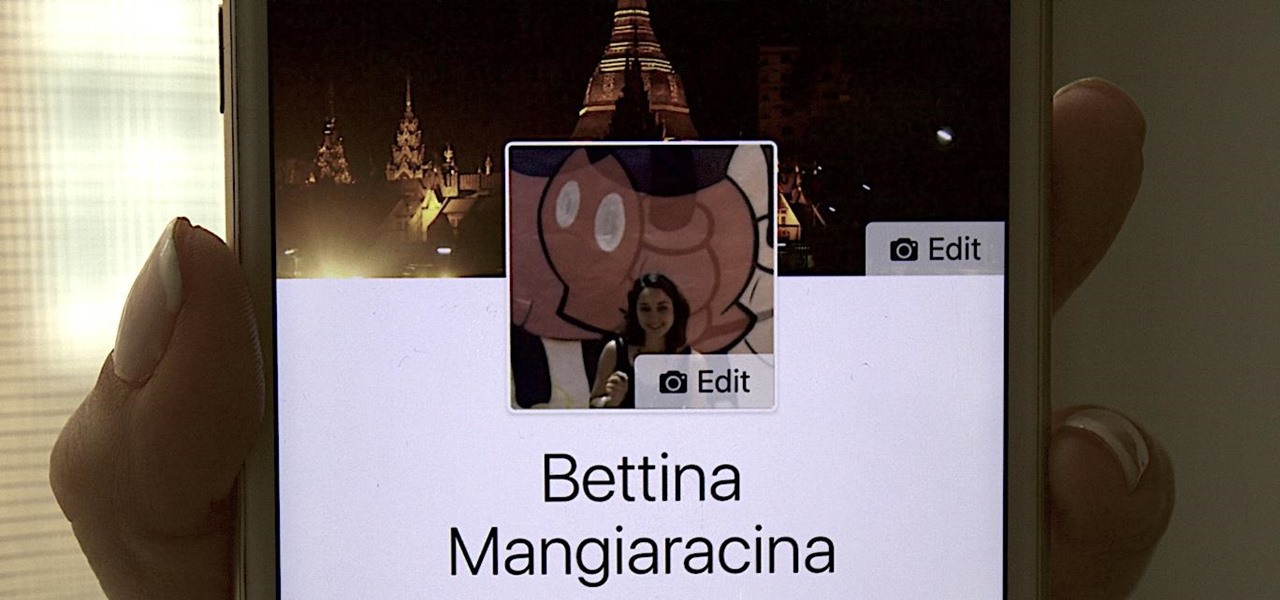
Changing your Facebook profile picture to a video is a great way to stand out from the crowd. A regular video file isn't the only option, though — if you're an iPhone user, you can also upload a Live Photo as your new profile picture to add more pizzazz to your Facebook page.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

So, you've just plugged in your new Chromecast with Google TV. You lean back to watch a TV show or movie and you notice that people look kind of ... odd.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

An iPad can serve as a second screen for a Mac via Sidecar, available since iPadOS 13, but Apple isn't the only manufacturer to support such a feature. Samsung has had a similar tool since One UI 3.1 that lets you turn certain Samsung Galaxy tablets into second displays for your PC — and there's a hidden feature that expands it to more tablets and even Samsung Galaxy smartphones.

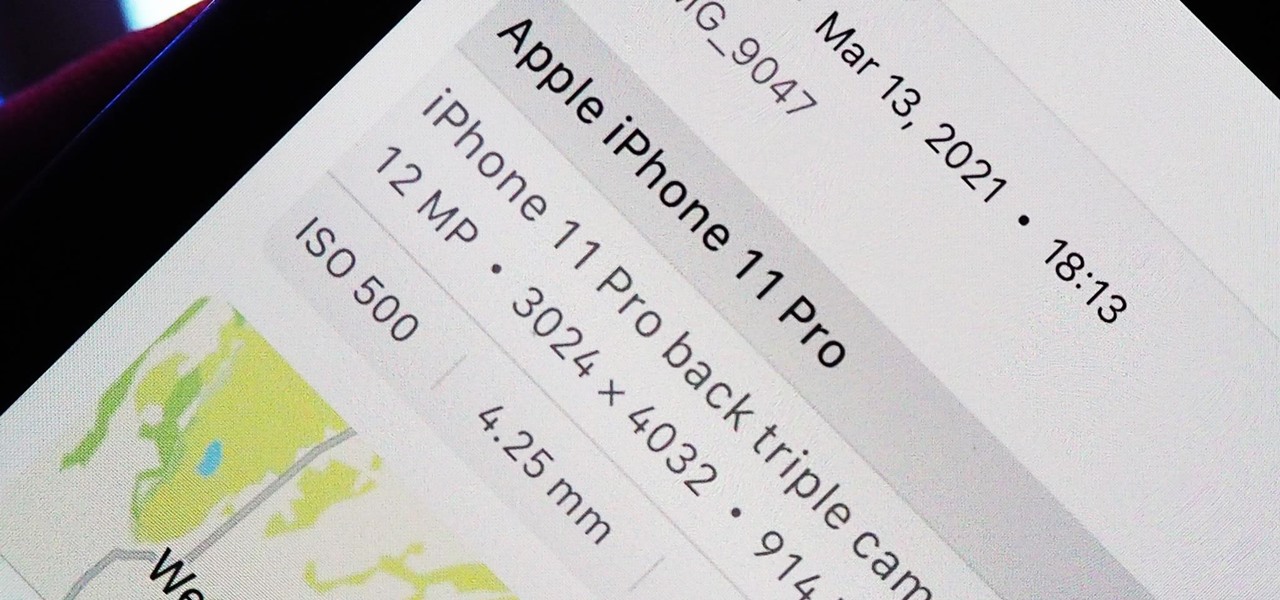
Apple introduces several new privacy settings with iOS 15, including the ability to better manage the metadata in your photos. With just a few taps, you can effectively spoof a photo's geolocation and change its creation date and time, providing a sort of disguise over your personal information. If you constantly take and share photos, it's a welcomed feature, but its results are not permanent and can be reversed.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.

Snap introduced some fantastic new augmented reality abilities in version 3.4 of Lens Studio, the company's tool that allows anyone to create AR lenses for the Snapchat app. The newest features include improved hand tracking and full-body segmentation.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

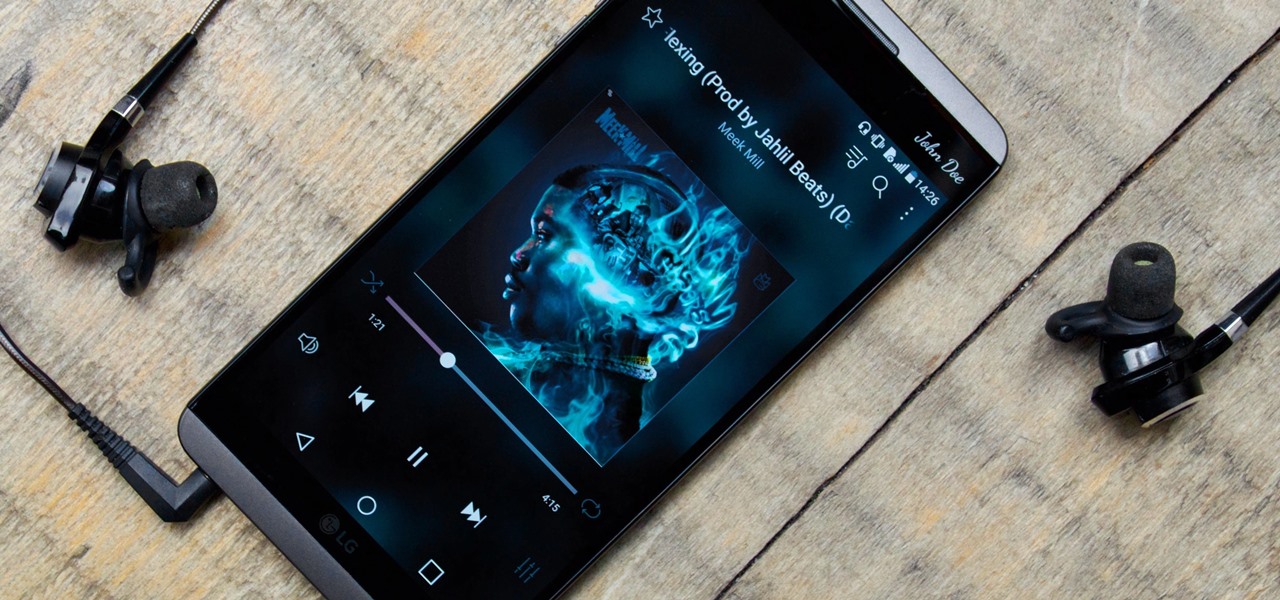
While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

At launch, Chromecast with Google TV is fairly limited in the number of compatible apps. Many of the usual suspects are there, but there are some interesting omissions, like Google Stadia (though support is coming). However, at its core, the device runs on Android 10, which means you can sideload apps, including those that don't officially support Chromecast with Google TV.

Don't believe what you read on the internet, especially today, when web giants like Amazon, Google, and the like showcase their otherworldly products and services. If they seem too good to be true, they probably are—but that doesn't make them any less fun.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

Spotify has caught up to Apple in monthly podcast listenership and is even forecast to surpass Apple soon, but Apple just made some serious changes to its Podcasts app for iOS and iPadOS that could keep Apple at the top.

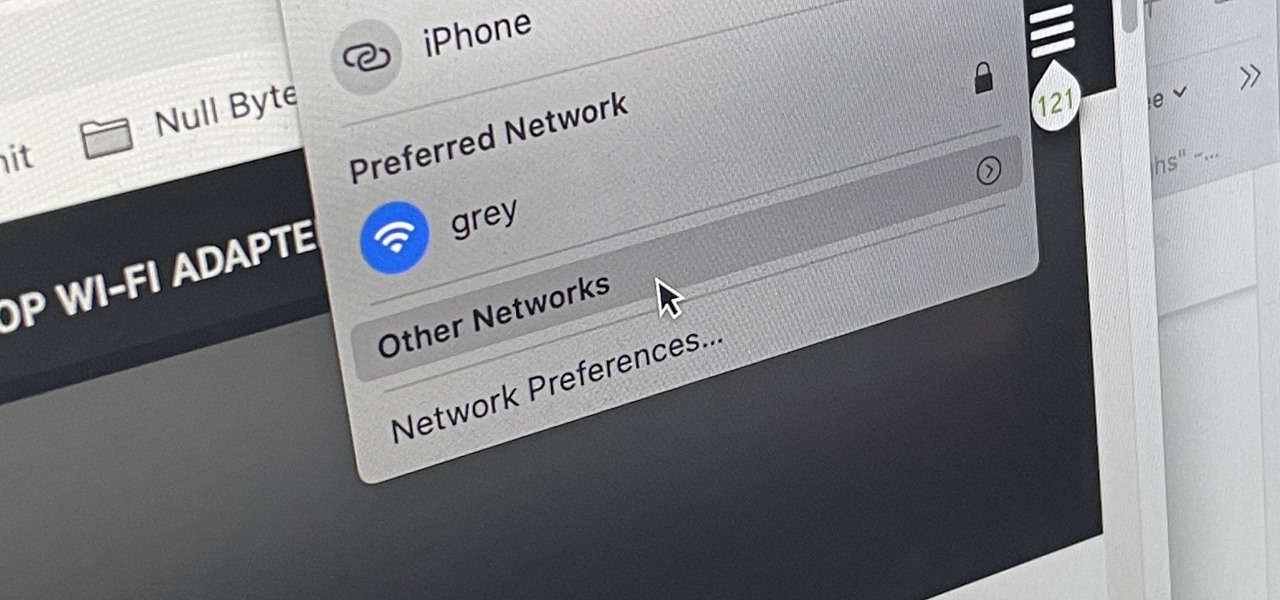
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

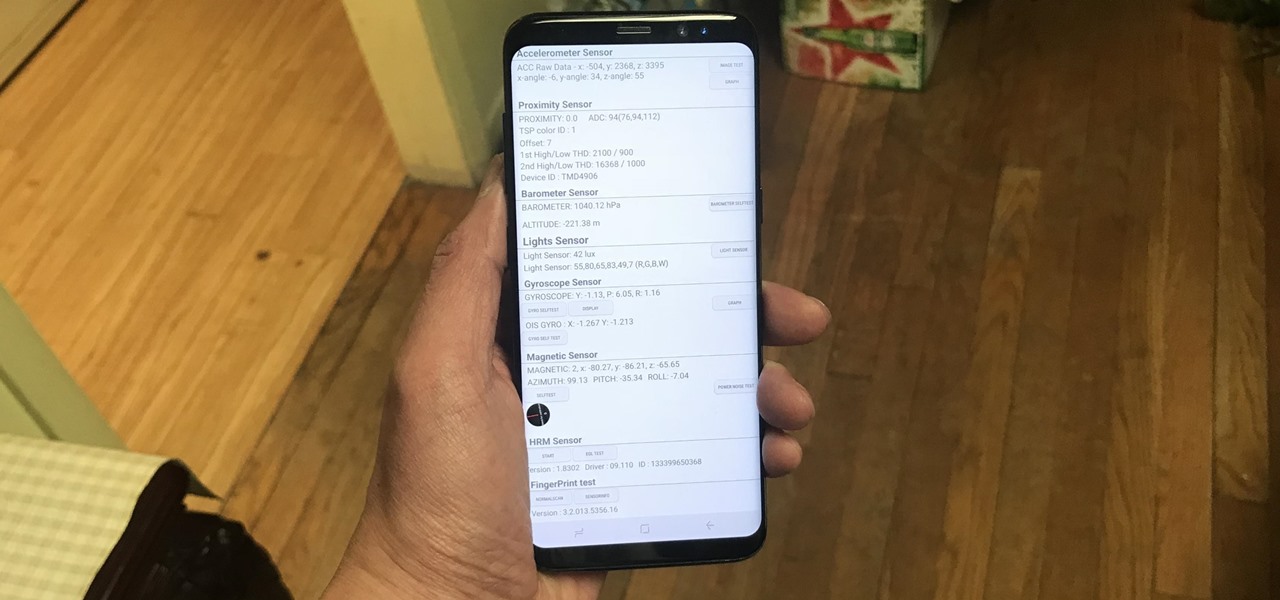
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

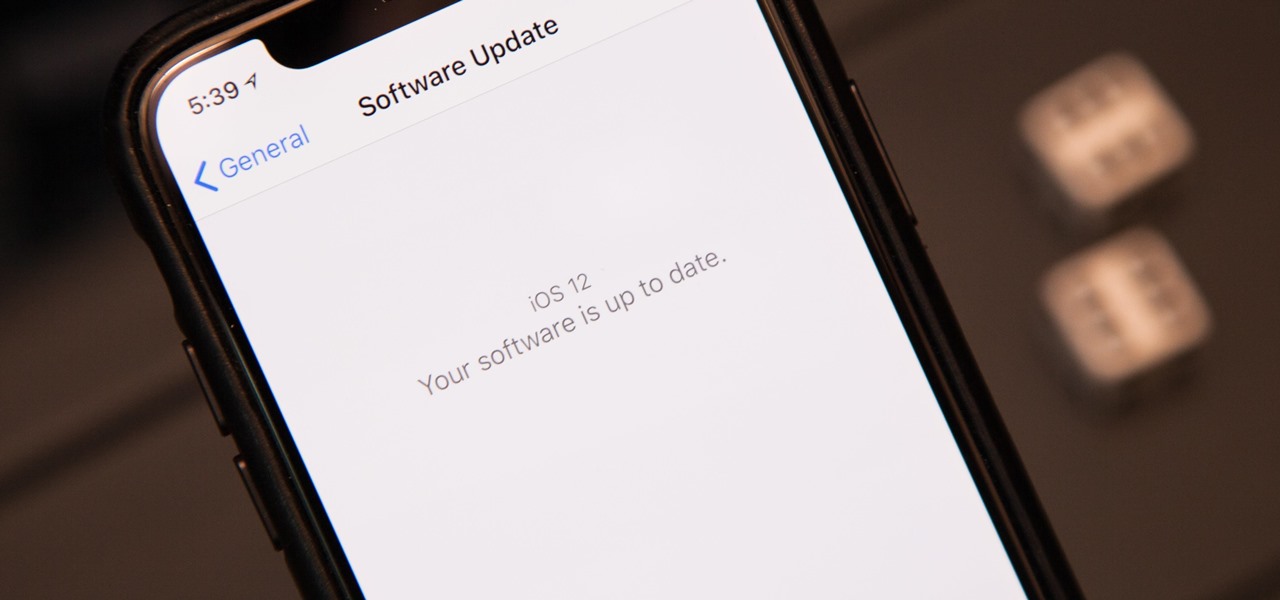
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

In this video, we learn how to make the perfect rice in an cast iron skillet. First, place 1 cup of basmati rice into the skillet with 1 and 1/2 cup of water. Now, add in 1 tsp of butter and 1/2 tsp of salt into the skillet and turn it on high heat, and let it come to a simmer. Once it starts to simmer, stir it and turn the heat to low, then cover it. Let it sit for 20 minutes, and don't uncover it while you're waiting. When the 20 minutes is up, remove the lid for three seconds, then place t...

Eating any type of shellfish can be messy especially if you don't know the right way to remove the meat. This how-to video demonstrates how to pick the meat from a cooked crab. Remove the legs, grab a small knife and start cracking open the sell to uncover the delicious crab meat.

Introduction In this article you will find instructions to replace a broken LCD screen of a LG KF600 phone. To execute these steps a new replacement LCD should be bought beforehand. Stores that sell replacement KF600 LCD screen can be found on the Internet. These instructions can also be used for other type LG phones that are part of the same family or have the same internal structure.

Watch as Gordon Ramsay comes into your kitchen to show you how to cook like pro. Watch this how to video and uncover the mystery behind a Bailey's ice cream baked Alaska dessert. Here's a hint, part of the secret includes making the Italian meringue that surrounds this delicious dessert. Make a Baileys baked Alaska with Gordon Ramsay.

This Hearty Turkey Chili- Cincinnati Style is yet another tasty creation of Chef Hubert Keller. Ground turkey, sauteed vegetables, and savory spices complete the flavors of this recipe.

Kimchi can be spelled in a variety of ways (gimchi, kimchee, kim tee), but what is it exactly? It's a Korean pickled dish made with vegetables and varied seasonings, and it's the most common side dish in South Korea. In this video tutorial, you'll gain the recipe for making kimchi with cabbage, sea salt, mustard greens, garlic, and other great ingredients. See how to make it!