Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...
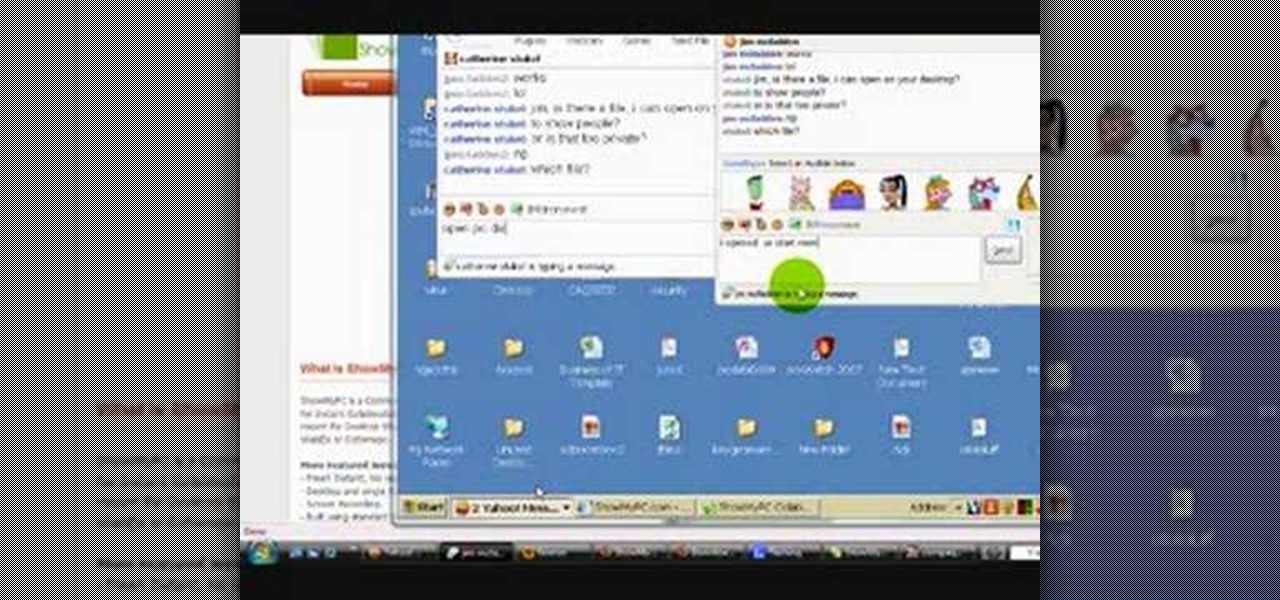
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the website ShowMyPc.com and be able to see what your target has been up to. Even better, you can use that computer and the files on it as if it were your own desktop!

What's in a name? Quite a lot. Learn how to choose a good one that targets your desired demographic. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this video guide.

Party poppers are magnificent. They can be used for a plethora of pranks— basically, any prank where the victim / target has to open something. You can use party poppers on practically any household item, but this video covers the much used dental floss container. The exploding floss prank is easy to do yourself, and requires only the floss container, the party poppers, scissors, and a screwdriver. Once your prank target goes to use their floss, they'll have quite the grin.

In this video tutorial, viewers learn how to shoot a compound bow. It is deeply recommended that users who use a compound bow should have a release. Put your arrow on the string and push it in until you hear a click. Now hook the release into the D-loop. Your feet should be shoulder width apart and the tips of your feet should be on the target line. Now look at the target and pull back the bow. Your hand should be at the point of your jaw, arrow at the corner of your mouth and string on the t...

In this video tutorial, viewers learn how to avoid a bad finish to cure a golf push shot. Usually, when players make a swing for the ball, their arm separates from their body. This will take the club to the right of the target and as a result, pushes the shot. To correct this, connect your left arm to your left side as you make a swing. This will allow the club to stay with your turn and go down the target line. This video will benefit those viewers who enjoy playing golf and would like to le...

In this video tutorial, viewers learn how to burn fat with a cable workout. These exercises will require a cable machine. There are four exercises in this workout. These four exercises are: cable wood chop, reverse wood chop, one arm cable row and exercise ball cable crunches. When performing these exercises, do not use a heavy weight. These exercises mainly target the abdominal and core muscles. They also target biceps, obliques and back muscles. This video tutorial will benefit those viewer...

How to aim your shot in World Golf Tour in four easy steps. When aiming for a shot, simply click the target and drag it on your desired location. The Yardage Indicator will change as you move the target closer or further. If it turns red that means that you positioned it outside the maximum carry distance for that club. You can also consider changing your club. Hit the Space Bar or click on Zoom to give you the aerial view to get a closer look and adjust for a precise aim. Be sure to take the...

Kathy Kaehler, author, celebrity trainer, spokesperson and mother, gives us a rundown of the best exercises for fellow women and moms on how to target their belly fat and love handles, and specifically the best ways to tighten these areas. Kathy first does advise us that if you're going to be targeting like this the most important thing first will be cardio and general fitness. Then, she offers us first the side plank, where you place one elbow to the ground, lying on your side, and then elev...

Fantasize about role playing? One of the most popular venues for role playing medieval fantasy is the board game, Dungeons and Dragons. Get a group of three or four together and have a blast!

The obliques exercise is a classical pilates exercise which targets the abdominal muscles to flatten the stomach and strengthen the core. Keeping the elbows wide helps keep the shoulders down and increases the rotation in the trunk, which helps shrink your waist. Be sure to stretch your legs fully each time and stop the knee at 90 degrees of hip flexion to encourage greater strengthening of the abdominal muscles. Watch this how to video and you will be strengthening your obliques with pilates...

In this video tutorial, Chris Pels will show how to deploy a web site using the Copy Web Site Tool in Visual Studio. First see how to connect to a remote web site and deploy an entire site to the target location. Next, learn how to synchronize an entire source and target web site. In addition, see how to copy and synchronize individual or groups of files including how the Copy Web Site tool provides status indicators of differences between files. As part of this process see how the tool provi...

Starting a business has to involve a desire to benefit someone else other than you. If all your reasons for starting a business are to benefit you, chances are good that you have missed the big picture. At least one reason you have to want to stat a business needs to be to help someone else. Either use proceeds from the business to help a charity of your choice or to solve a problem or provide a solution to a need for the target group that your business serves. Focus on one issue to start wit...

In this video tutorial you are told how to use the Wagon Wheel Cue Ball Control training method. This is called Wagon Wheel because each target ball is aligned to RESEMBEL the spokes of a wagon wheel. Set your cue ball and your object ball in the same position each time. The objective is getting the cue ball to one balls width of the target ball. Using THE FOLLOWING cue ball, direction and speed. By using a piece of chalk the instructor helps line up the balls. By using either a quarter stick...

Component 1. Frame And Posture. The benefits of dance shoes never outweigh the benefits of proper spin technique. Your body should be straight lower abs and stomach should be tight. Your arms are in proper position. If you lift your hand it should be in 90 degree angle.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

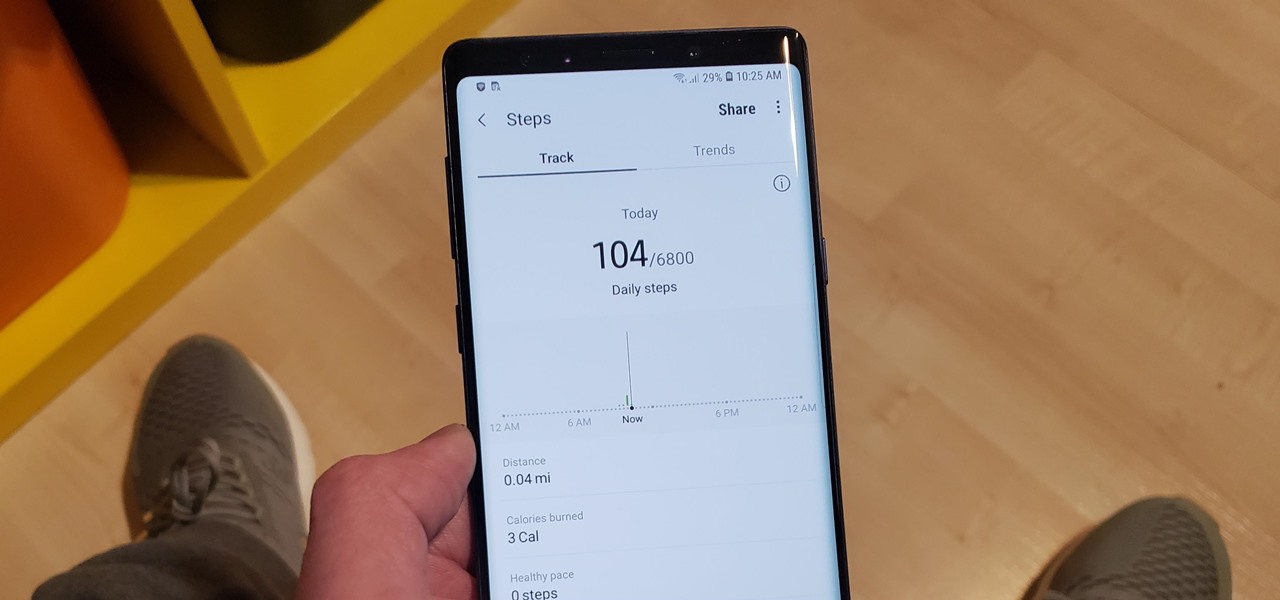
Once known as S Health, Samsung Health has become one of the most comprehensive health apps available for Android. In fact, we all can benefit from the features the app brings to the table — whether you're a marathon runner or a couch potato. If you're in the latter category, the app has a simple feature that can nudge you towards becoming more active.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

If you've ever wanted to hone your paintball skills, without spending a ton of money and making a huge mess, Show Me Virtual and Apple's ARKit have an app for you.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Your target in level 3-13 of Angry Birds is not so much a pig fortress but a series of pig-defended hilltops. Still no problem for a properly trained bird army. Watch the video for a guide to beating level 3-13 with three stars.

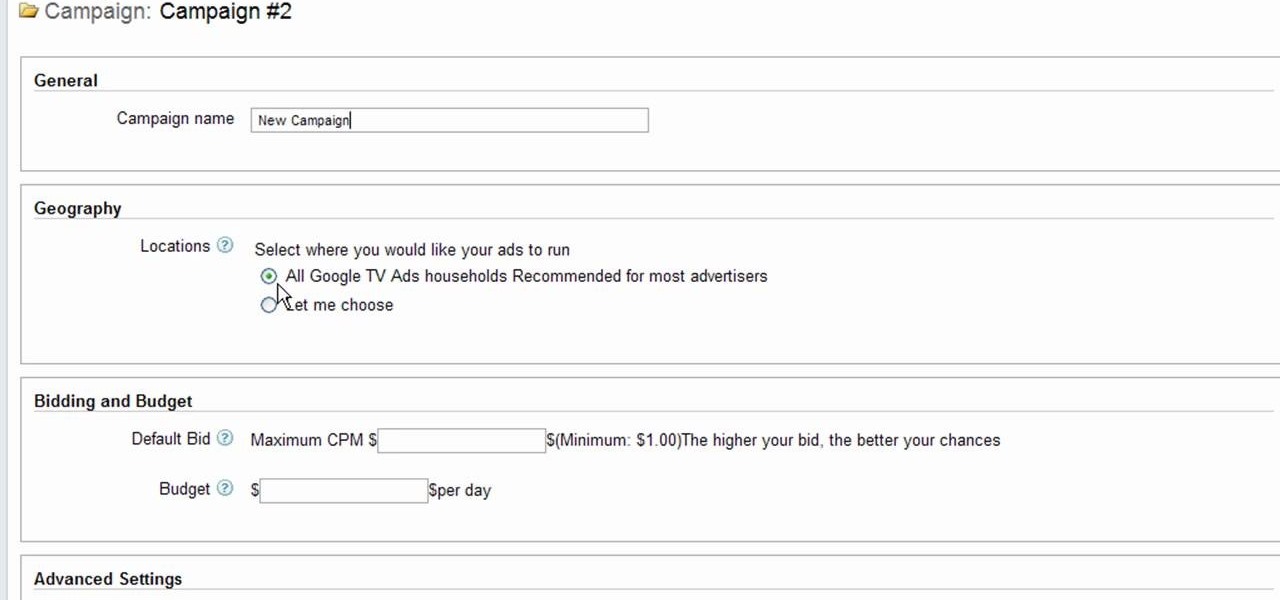
Interested to know how to start a new cable television ad campaign with Google AdWords TV Ads? This official video from Google will teach you how to use the new interface to determine just that. For all of the relevant details, and to get started creating your own televised advertising campaigns, watch this clip.

It's been a few years since Finding Nemo became the highest-grossing animated film of all time, but it's cultural appeal lingers on. If you want to capture some of that Nemo cuteness for your Halloween costume, watch this video to learn how to make a really cute Nemo costume with no sewing required.

The ground and pound is one of the most controversial aspects of MMA fighting, and is a great chance for you to do a lot of damage to your opponent. In this video UFC fighter Joe Lauzon will show you how to use an elbow technique from guard to defend yourself and get a solid elbow shot in at the same time, using Joanne from MMA Girls as his target.

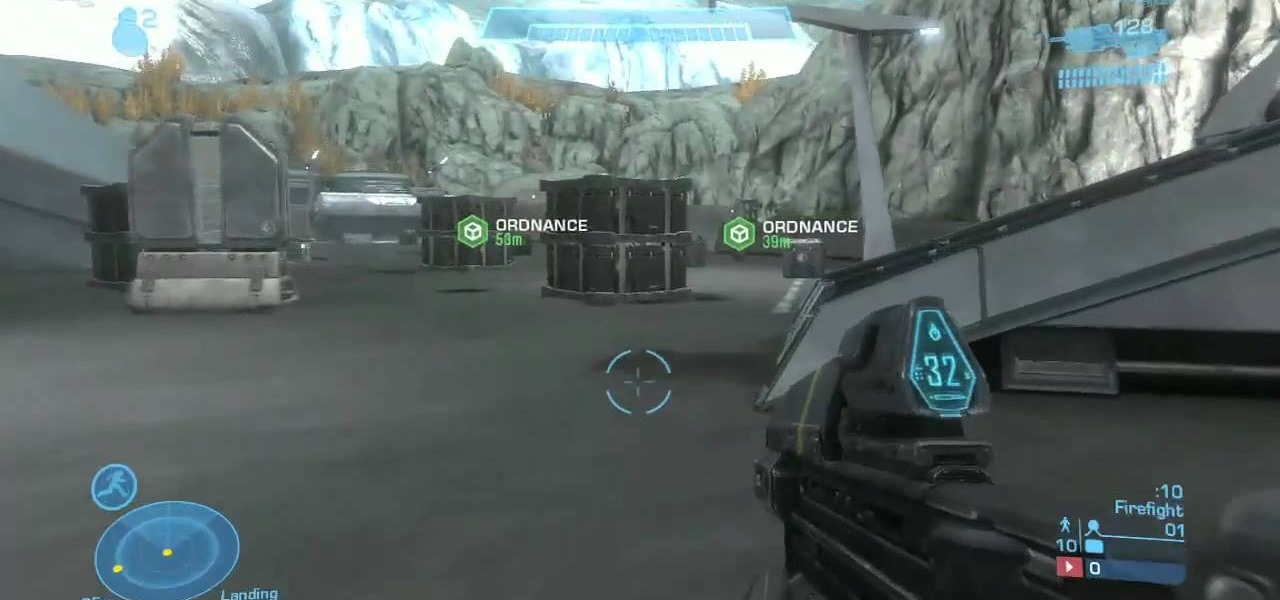
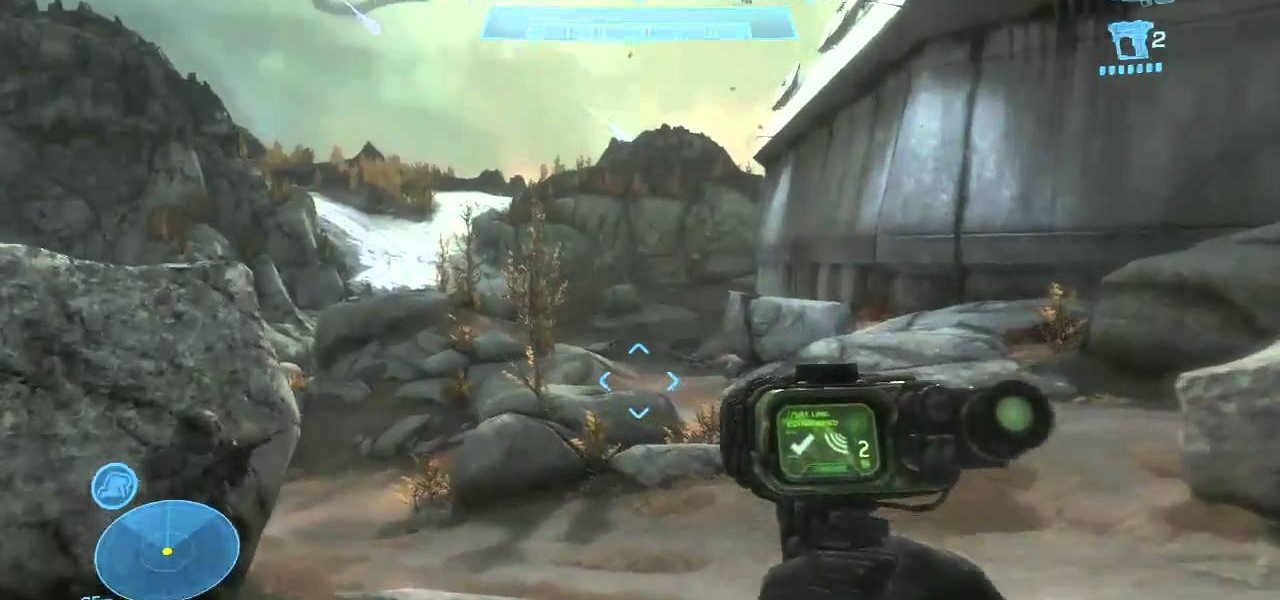
Halo: Reach has so many tough to get achievements, but the easiest one that you can get pretty fast is the "Crowd Control" achievement, and you can get it on Courtyard using the target locator. In this video you will learn how to effectively kill off multiple Covenant drop ships to get the achievement in about five seconds!

Two Corpses in One Grave is a difficult achievement in Halo: Reach if you don't know where to look on mission 3. You will have your chance right after you acquire the Target Locator when two Wraiths show up for the killing! Just be sure to aim straight and true and you will be alright!

Thanks to modern technology, we don't have to visit our nearest Target or Rite Aid to get our pictures professionally retouched and printed. With many printers offering photo-quality ink and paper companies that offer photo-quality paper, you can use your home printer to create professional-grade photos.

If you're planning to become a veteran yogini, you'd better start practicing and loving the up dog pose now, because you'll be spending the greater part of your yoga flow doing up dogs and down dogs.

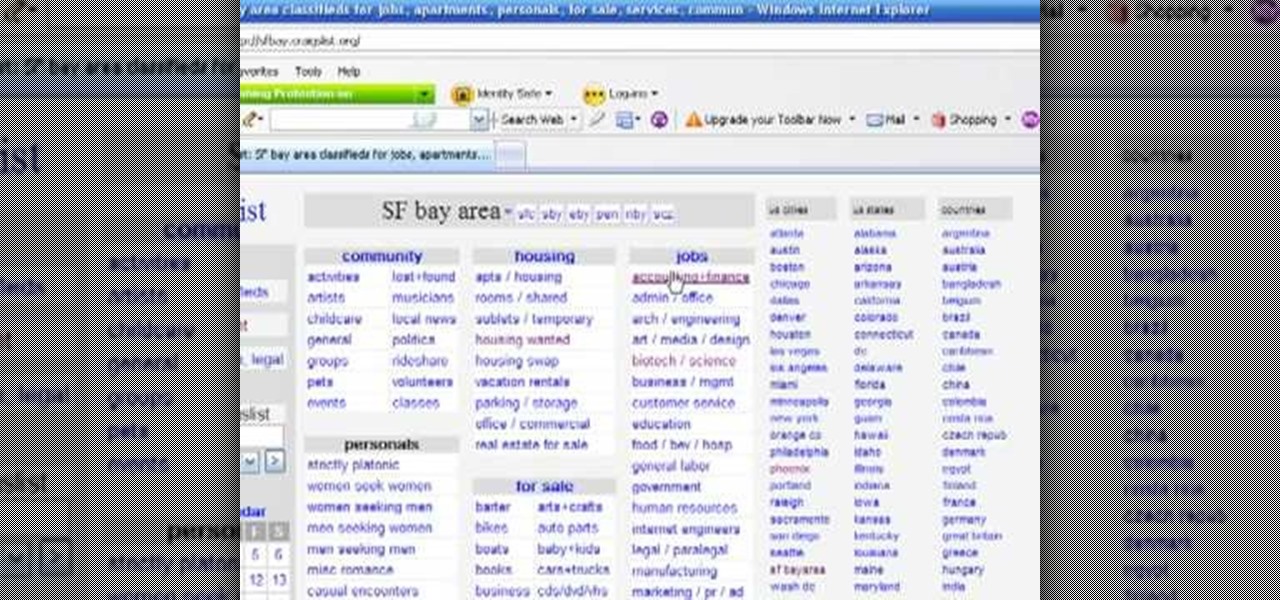
Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.