An easy way to view your CSS code of your website is through the Firefox plugin called Firebug. It's really helpful, especially if debugging your code. Just remember, you cannot save anything with Firebug, it's only for viewing code and adding codes for previewing webpages.

Kristin Holt is here show you some cheat codes that will make defeating the criminal underworld of Gotham City a downright breeze in LEGO Batman: The Videogame.

This Adobe After Effects tutorial shows you how to create the Matrix raining code text effect. Learn how to use this motion graphics and 2D effects compositing software and the automation options available to easily create a Matrix raining code effect in After Effects.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.
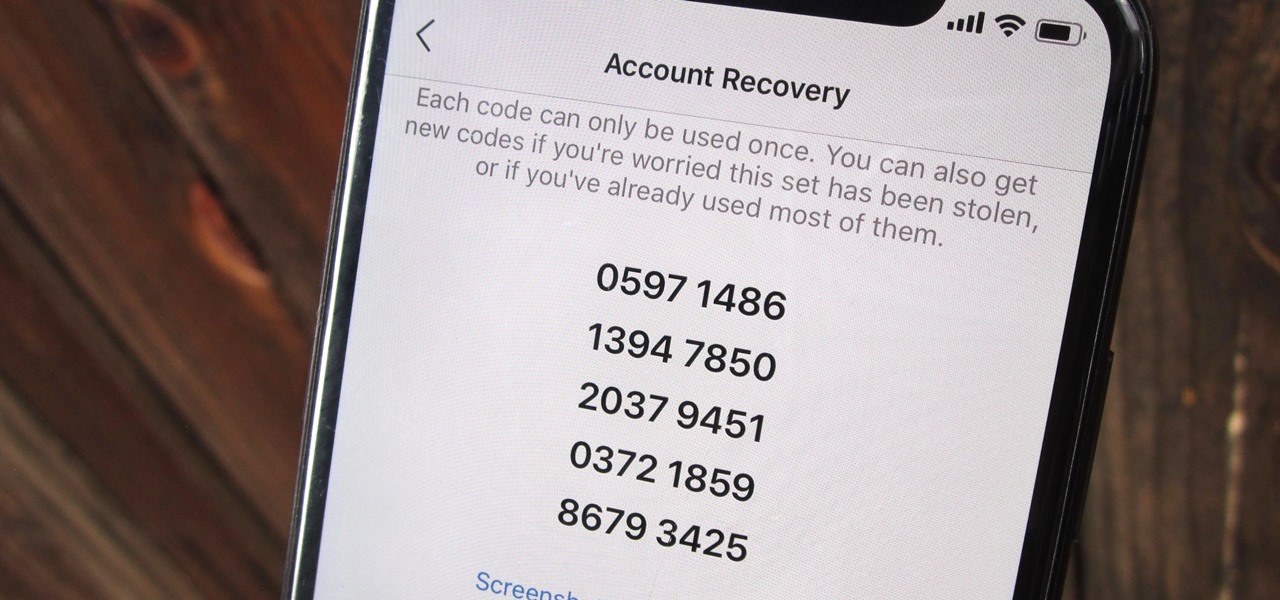
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Why should console players have all the fun? This tutorial shows you how to enter in cheat codes when you're playing Grand Theft Auto: San Andreas on the PC. Get everything you can as an XBox or Playstion player with these codes!

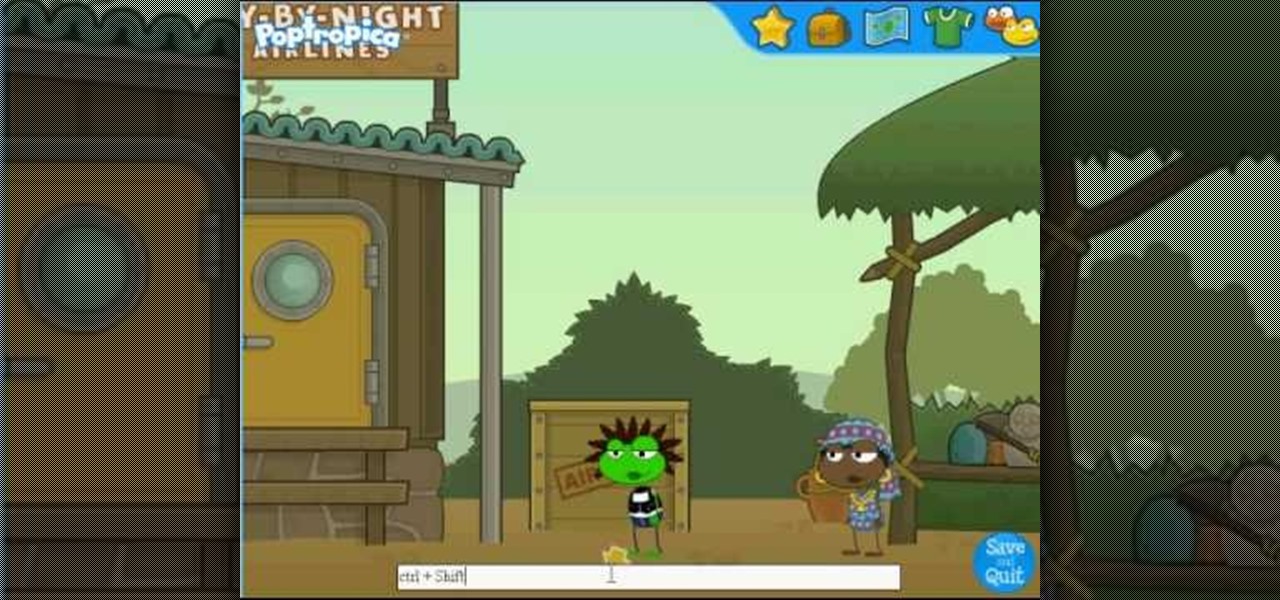
Make sure you watch the very bottom of the video, that is where the cheat codes will appear. Poptropica has the ability to use codes to get some extra goodies, and this video demonstrates a few of the better ones for you.

You can use the cheat codes "fastfire," "moreammo," "pointer," and "nohit" to get you a higher score when you're playing Gun Blood, a simple Flash game about gun duels. There are more codes, though, so watch the video and see what you like best!

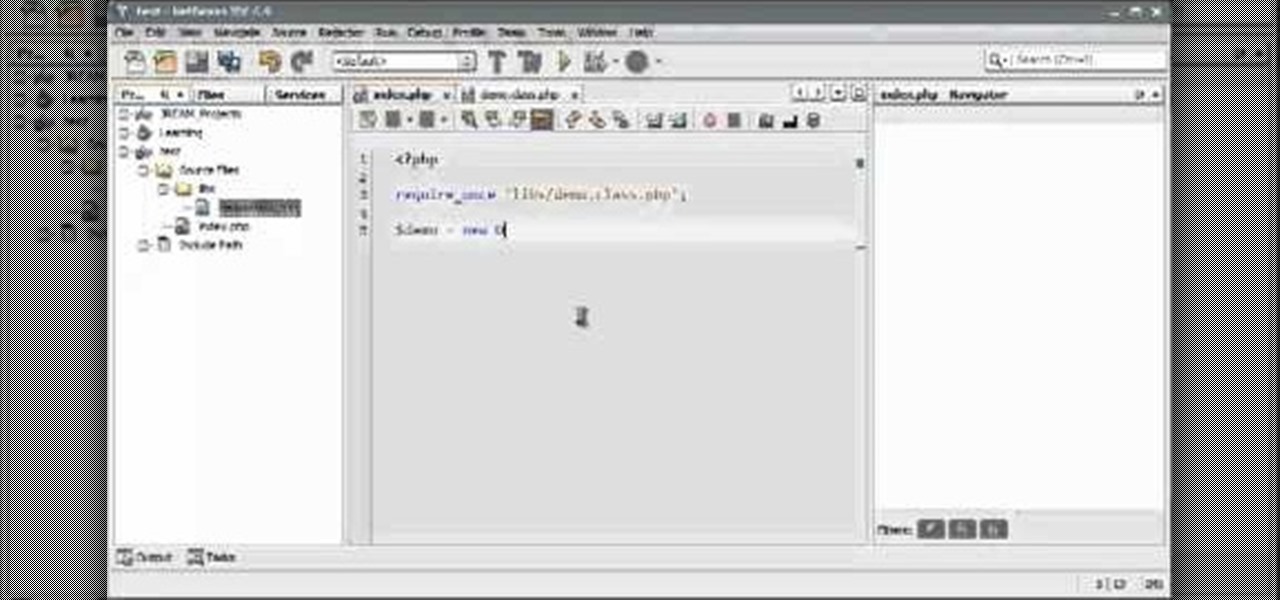
In the world of coding you want to be clean and efficient. A great way to do this is with an IDE, such as Netbeans IDE. If you're ever working with a team, knowledge of a great IDE is a must. Check out this PHP coding tutorial and up your knowledge base.

If you're looking to break into Call of Duty 4, you can use the mod menu to access the cheat codes and give yourself all kinds of goodies. This tutorial shows you how to get to the menu and use these codes for yourself.

If you've already enabled the developer console, you know you can access the cheat menu in the game and enter codes to give you crazy cool stuff. But what to get? Here's a list of codes that you can use to give yourself immortality, kill every enemy in your immediate area, give yourself unlimited money and, of course, play in God Mode!

This tutorial shows you first how to create an object using Adobe Flash CS3, and then you're shown how you can use ActionScript code to make them spin and rotate. You can even cause the spinning to speed up using the right code!

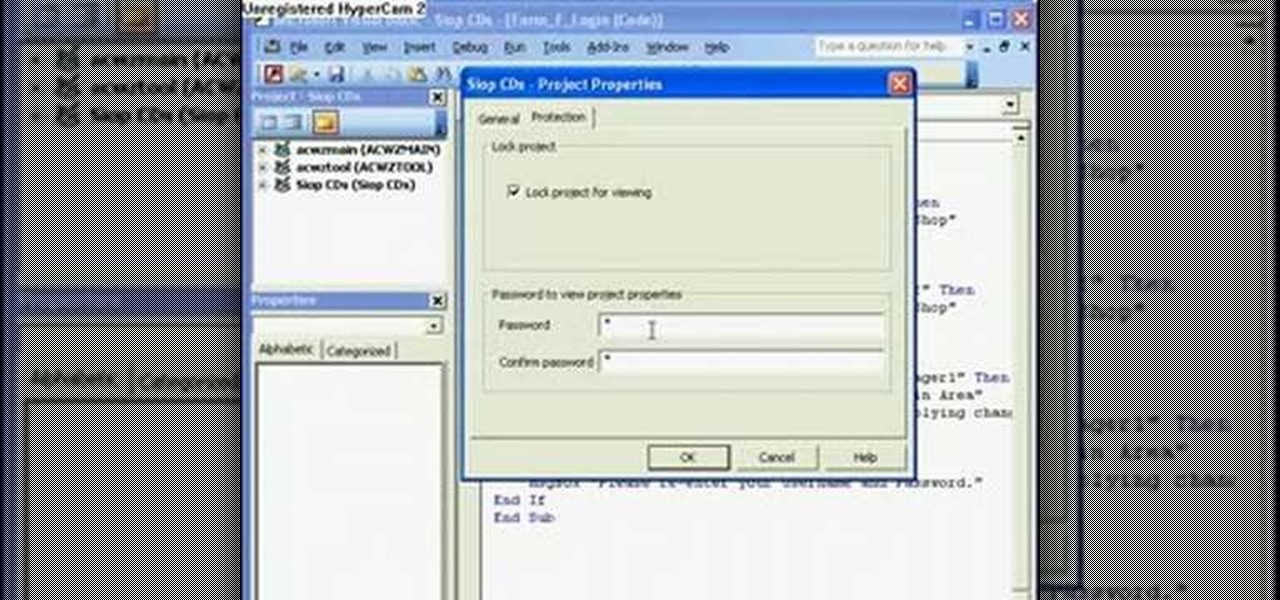
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about protecting your VBA code from snoopy little trolls. For more information on keeping your VBA code secure, watch this MS Access how-to.

In this tutorial, Mike Lively of Northern Kentucky University demonstrates how to create a 3D clickable Carousel in Adobe Flex 3 and Papervision3D. All code can be downloaded from Google Code at:

This simple Adobe Flex tutorial shows how to download source code from Google Code and get it running in Adobe Flex. If you are new to programming and building applications with Adobe Flex, this project is a great way to practice or get started learning about Adobe Flex.

"There are 10 types of people in the world," the old joke goes, "those who understand binary, and those who don't." In this tutorial, you'll learn how to read and write binary code. With this neat tutorial, you'll join the former group. Make sense of the 1s and 0s of binary code, the symbolic atoms of machine language, with this how-to.

Learn how to enter code breaker codes on the PCSX2 Playstation 2 emulator for the PC. Entering these codes will allow you to cheat on emulated PS2 games. YOu will need to use a variety of other programs like Daemon tools to do this.

If you are looking for a UAV code for homebrew then this is the video for you. Check out this site for codes and follow the video to learn how to hack COD: Black Ops with a UAV code.

In this video, the author shows how one can make one's own playlists on YouTube, and also get the code which can be embedded on one's website or blog. All one has to do' according to the author, is to first load all the videos which one wants in a playlist and pause them. Then one has to click the 'Playlists' option under the video pane. In the drop-down list which opens, one can choose one of the existing playlists or create a new one, and then, simply click the 'add' button. This action has...

This is a Restaurant City 3 in 1 Hack (Working From 12th May 2009).

Want all of the GTAIV cheats? This is a Grand Theft Auto hack like you'd never believe. Get the cheat codes for every glitch and cheat in the game.

Mike Lively of Northern Kentucky University shows you how to create a light switch in Second Life with scripting. Part 1 demonstrates how to create a prim switch which turns on (brightens) a prim in Second Life. Part 2 goes through the Light Switch code line-by-line and adds a rotor to the light switch. The code is provided for free distribution on Google Code at

A QR code is a fun and convenient way to link people to a website or app. On iOS, you have a few ways to scan these codes. You can download a QR scanner to get the job done, but Apple has one built into iOS. Or you can add the QR Code Reader tile in Control Center, but that's not even necessary. There's a better way, one that requires basically no effort to pull off.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

QR codes are supposed to make life easier, but having to install potentially shady third-party apps just to scan one is more trouble than it's worth. Thankfully, there's a QR code reader built into all Google Pixels, but you wouldn't know it unless you stumbled across the feature.

When attending networking events, a LinkedIn exchange is a common occurrence. Equally common is the awkward fumbling dance with how to add each other. Fortunately, we have the solution: the ultimate way to add LinkedIn contacts.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

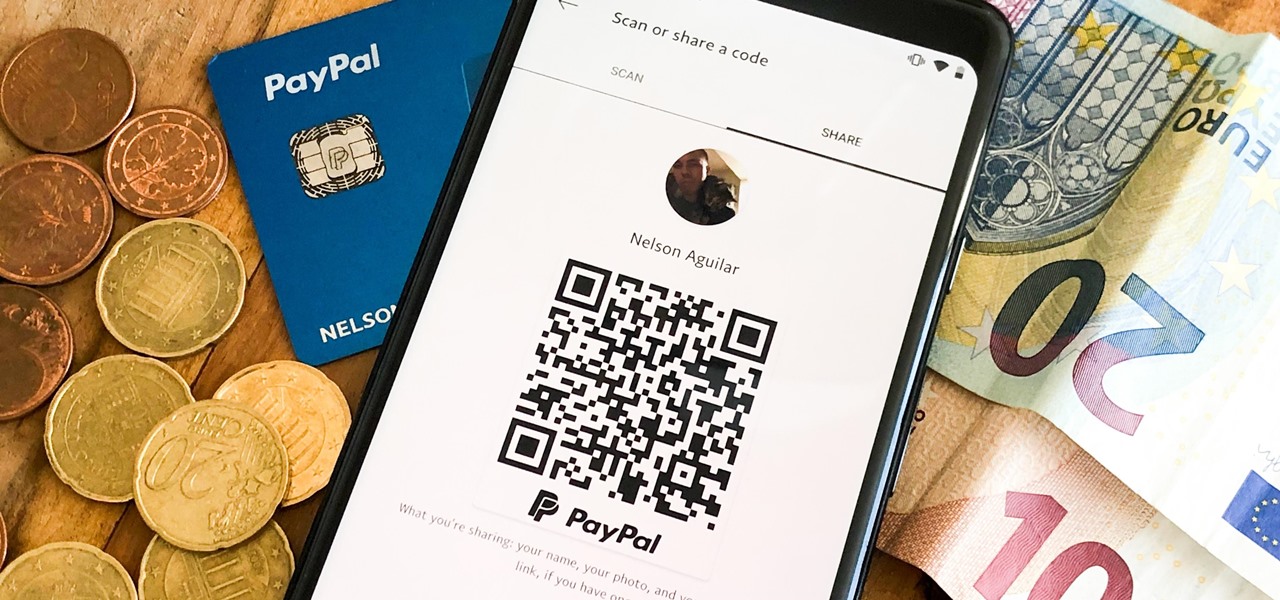
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

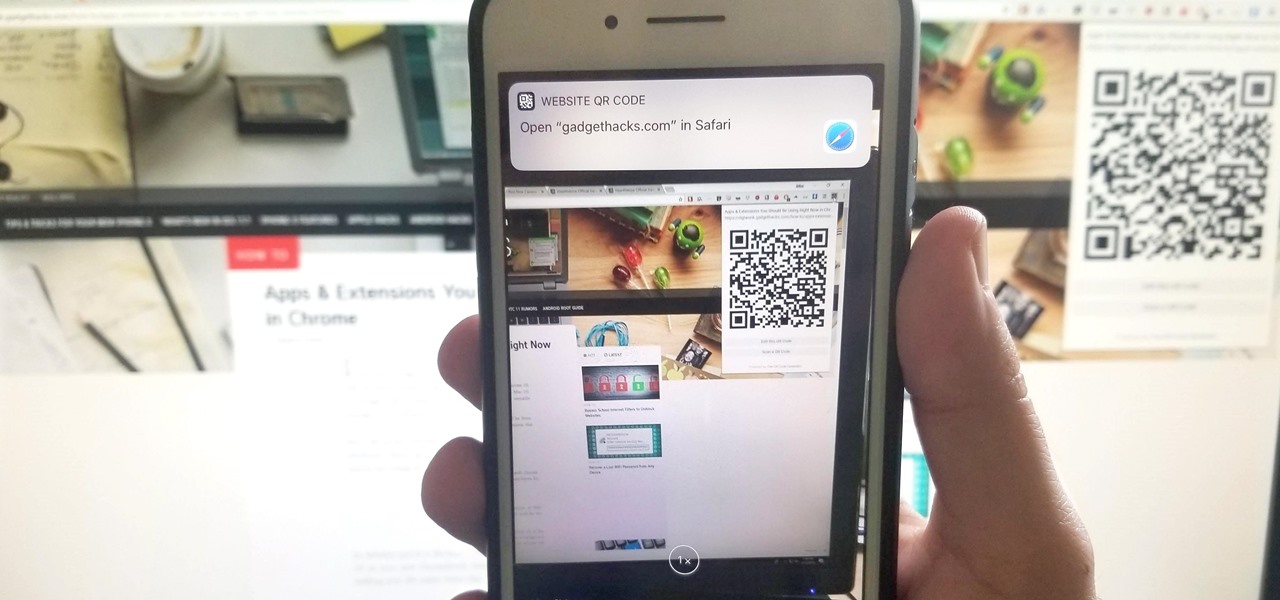
If you have a Mac, you can use Apple's Handoff feature to open one of your Safari desktop tabs in Safari on your iPhone. But if you prefer to use Google Chrome as your desktop browser, whether or not that's because you have a Windows PC, you can't "hand off" open tabs from Chrome desktop to Safari on your iPhone. There is a cool workaround, however.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Determining exactly what of the thousands of parts on a modern car is broken is as difficult as doing the repairs many times. IN this video you'll learn how to diagnose and fix error codes P0171 and P0174 on a 2001 Ford Escape, which indicate vacuum problems.

Code your Flash-based website so that your content can remain the same, no matter if visitors are viewing your site on a computer screen, smartphone display or even a high-definition TV. This tutorial shows how you can code your fluid website to achieve the true fit effect.

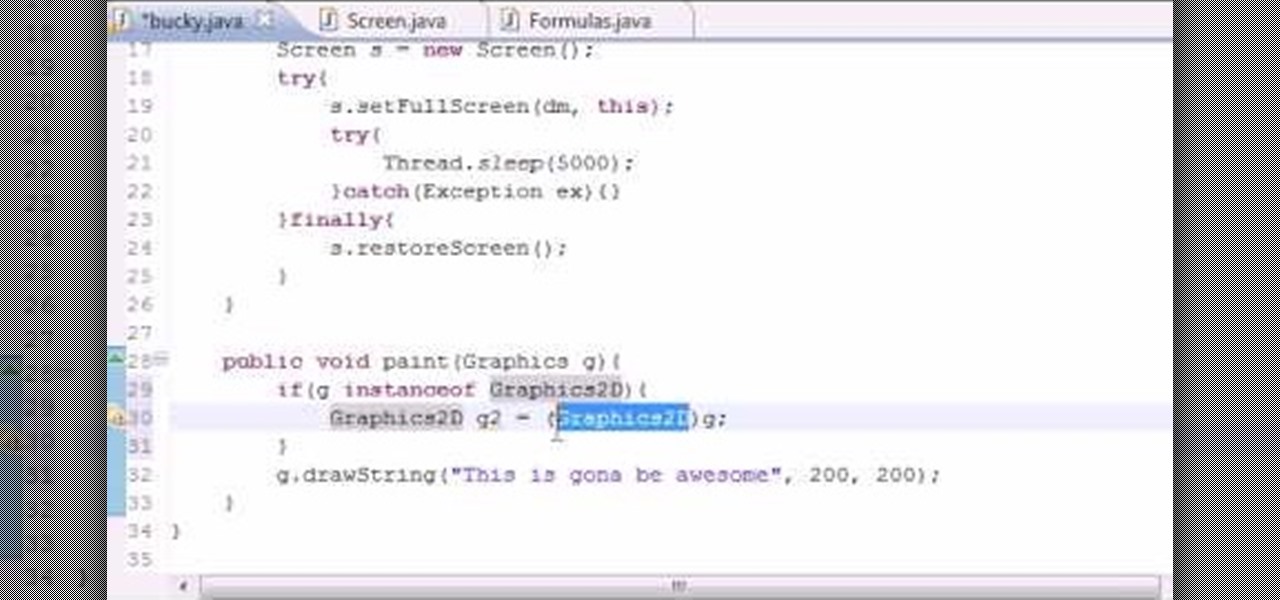
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to anti-alias text when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

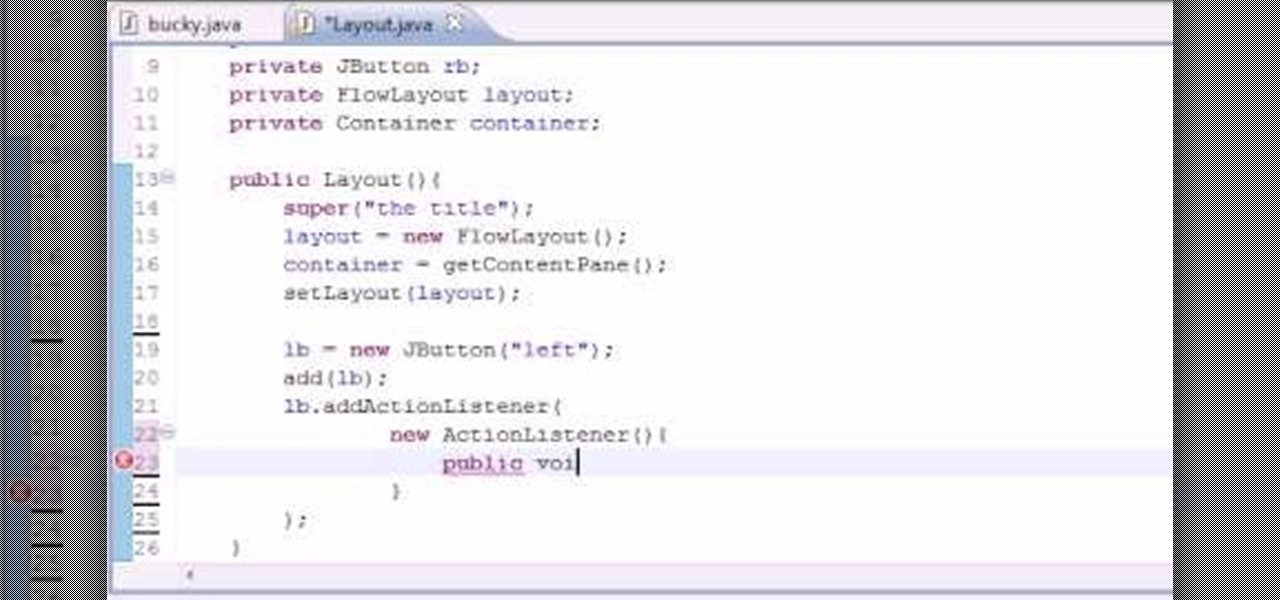
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to work with the FlowLayout class when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

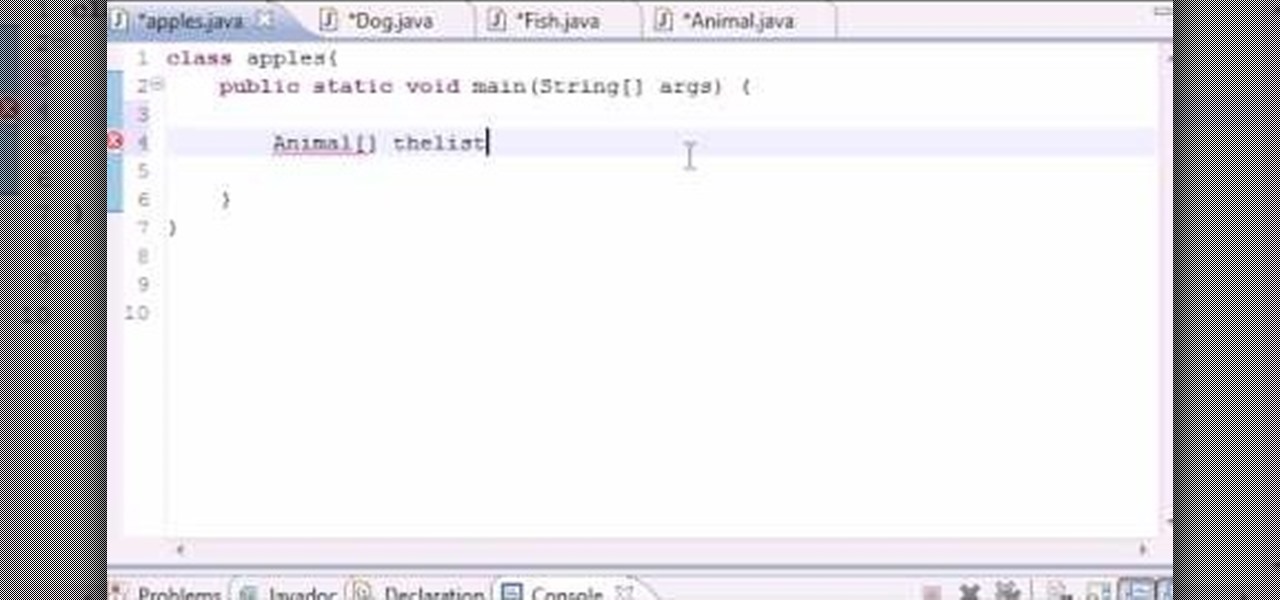
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to work with simple polymorphism when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.