Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.
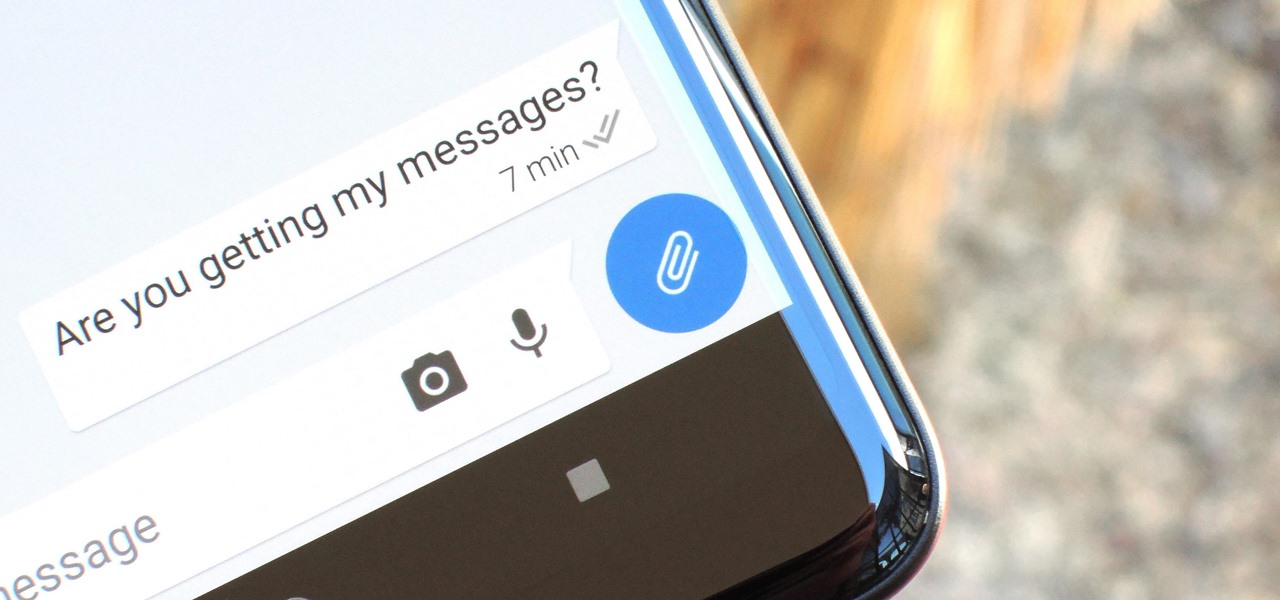
After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.
In this tutorial, we learn how to drive traffic to your website using Twitter. To get started, you will sign up for an account and then go to your profile. Start to follow people and have them follow you back as well. If someone mentions your name then all of their followers will see your name and can click on you to see your profile. If you have something interesting on your profile, then they will want to follow you! It's important to have your main website link on your website and a bio wi...

Want to make an Inverted Traffic Light cocktail like a champion bartender? This clip will show you how it's done. With the proper technique, mixing the perfect drink can be easy. So easy, in fact, that this free video bartenders' guide can present an overview of the process in about a minute's time. For more information, including a full list of ingredients and complete instructions on how to mix this drink yourself, take a look.

Collin teaches us how to race at Laguna Seca raceway in this tutorial. When coming out of the pit lane, wait for the workers to wave you on. Make sure there is not traffic around you because you will be doing over 100mph. Once you are sure there is no traffic, turn in the late turn so don't dual apex it as you are turning. By this time you will turn four and then turn five after this on the right hand side of the track. Next, turn six with a small amount of braking bringing the car out and ru...

It's time for another Achievement Hunter video from the guys who know how to do it best. The game they're playing this time is the first DLC for the psychological hit thriller, Alan Wake. The Signal takes players deeper into the story of Alan Wake and find out what's actually going on with his life.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

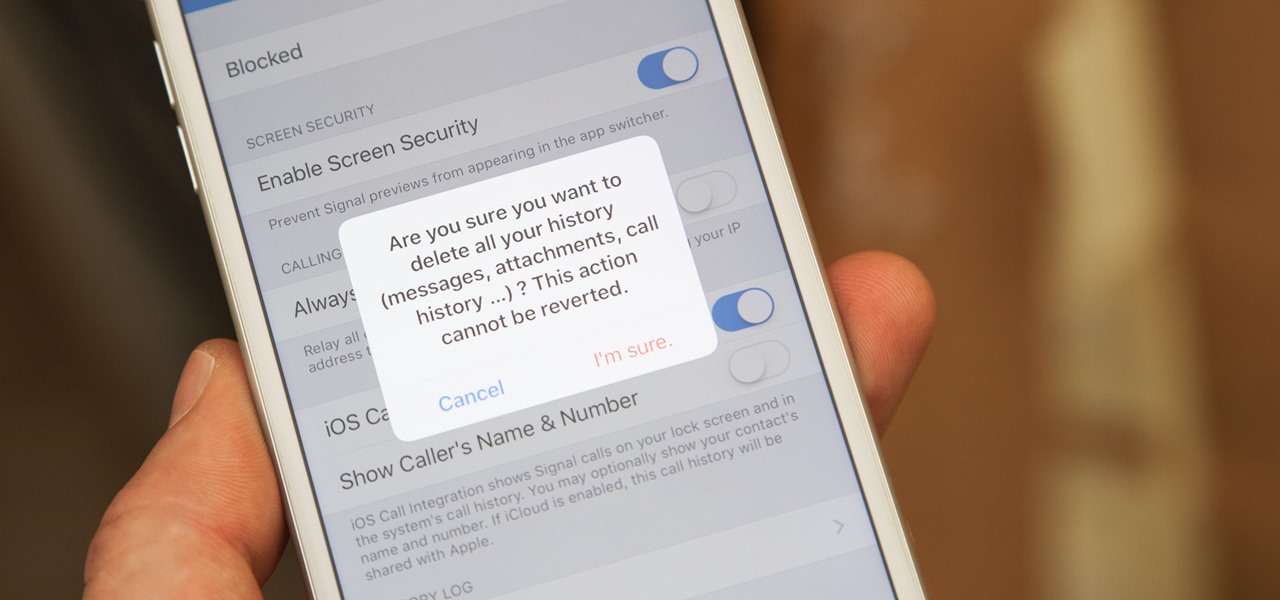
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, stopping those who text and drive right in their tracks.

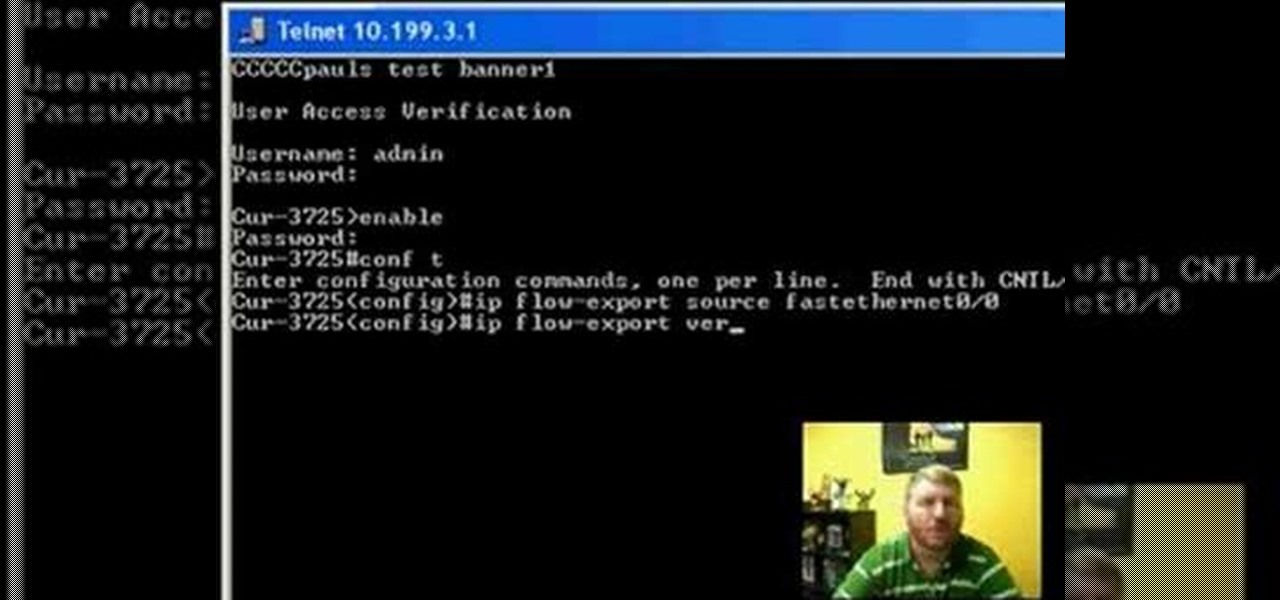
Netflow technology allows you to monitor web traffic to your website - find out who comes to your site, where they're coming from and where they go afterwards. You can configure a Cisco router manually to monitor netflow going through the router.

Horseriderchamp productions presents this video on how to do join-up with a horse. Here, in this video, the lady demonstrates this with her one year old horse 'majestic. She says that join-up is basically creating bond or relationship with your horse and there are three signals to join-up. The first signal she says is to have horse's one ear locked on you when they start to look on you and start to make small circles, and she says that once you get the signals, when you turn to speak to them ...

Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Carriers really suck, don't they? We constantly have to monitor our data usage, even though many of us are on "unlimited" plans, which, in reality, will just be throttled to a slower 2G or 3G connection when we hit a certain download threshold.

In this video we will show you how to replace the turn signal on your 93-98 Volkswagen Jetta.

If you ride your bike or motorcycle a lot, especially in a large city, you've probably had a few close calls. No matter how safely you're driving, you never know what other people are going to do, and being on a smaller vehicle makes you difficult to see.

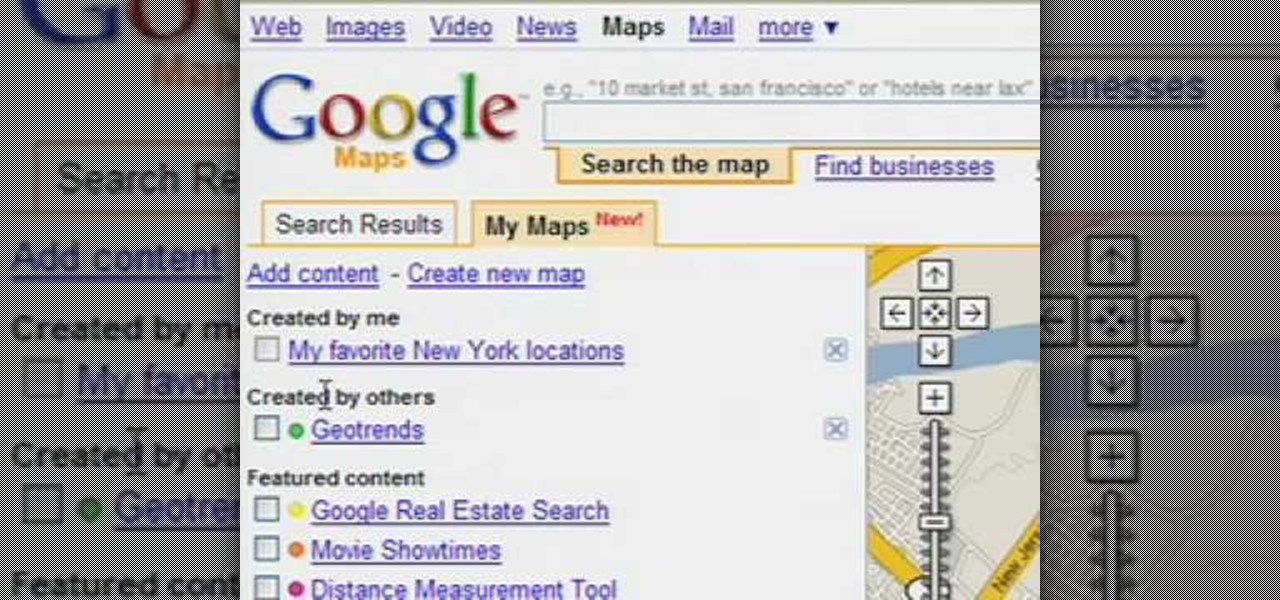
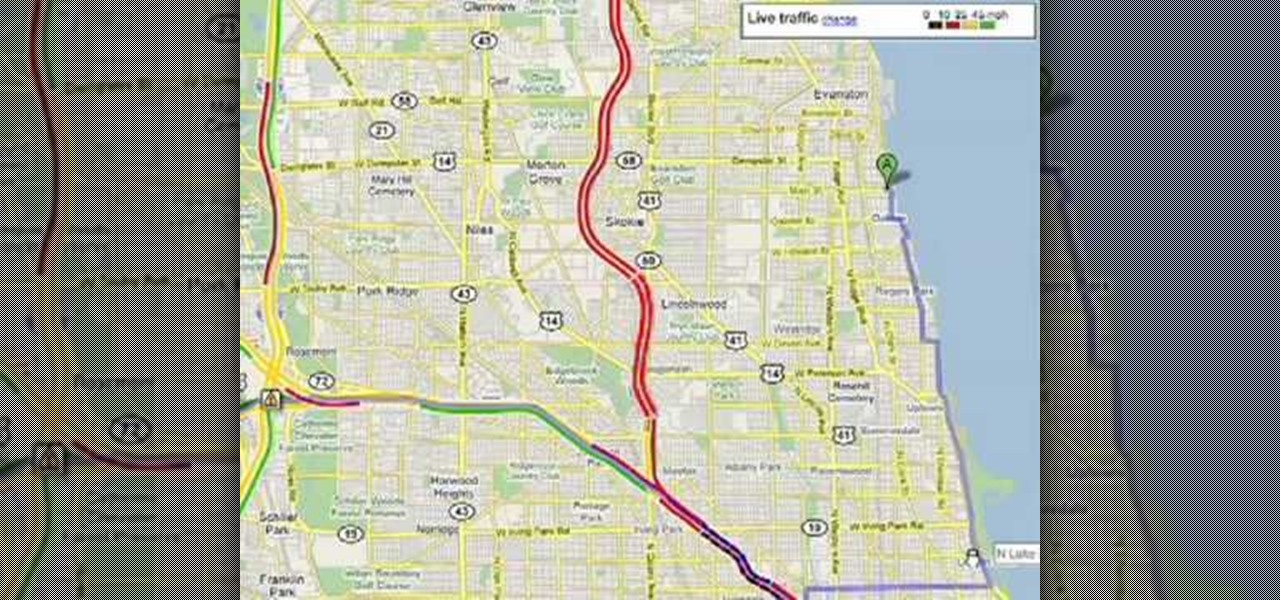
Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way. Print directions with Street View, photos included.

Needless to say, we're talking minor traffic violations. If you've just led the cops on a high-speed chase down the freeway, you're on your own.

Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, you'll need the following items: (a) a piece of parabolic cookware, (b) heavy tape, (c) a USB WiFi stick, (d) tin snips, and (5) a USB extension cable. For detailed instructions on building your own wireless signal extende...

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

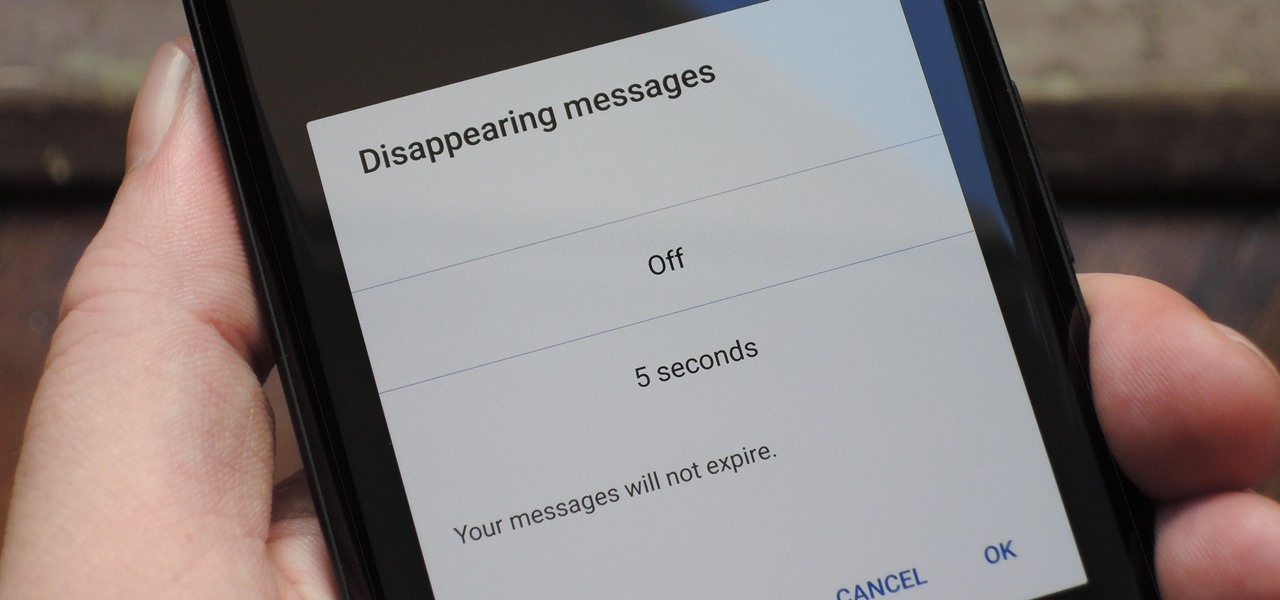
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

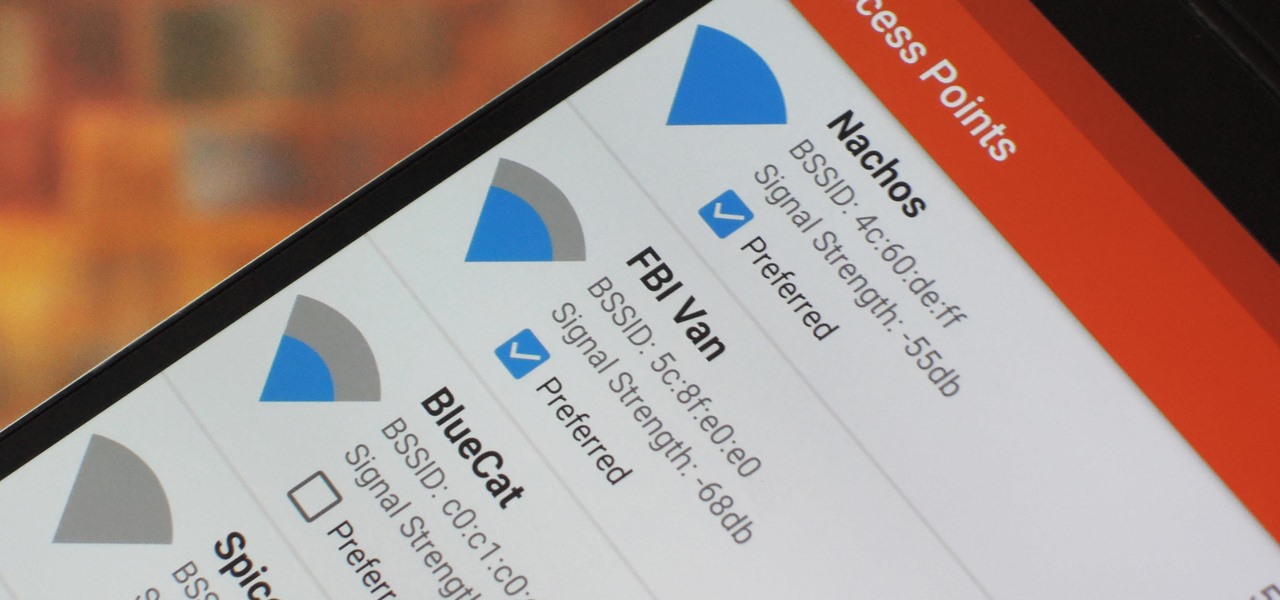
Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

L.A. Noire is one of the most realistic video games ever created. To solve the cases in the game, you'll need to think and play like a real detective. This video will show you how to beat the first traffic desk level, called The Driver's Seat.