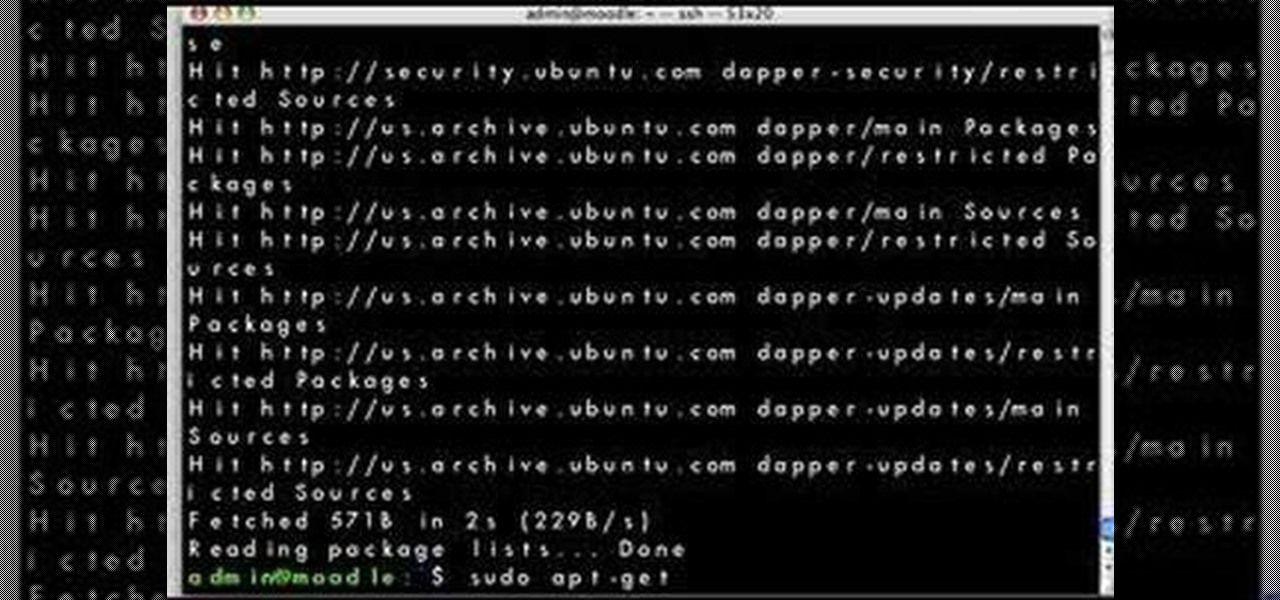
If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.
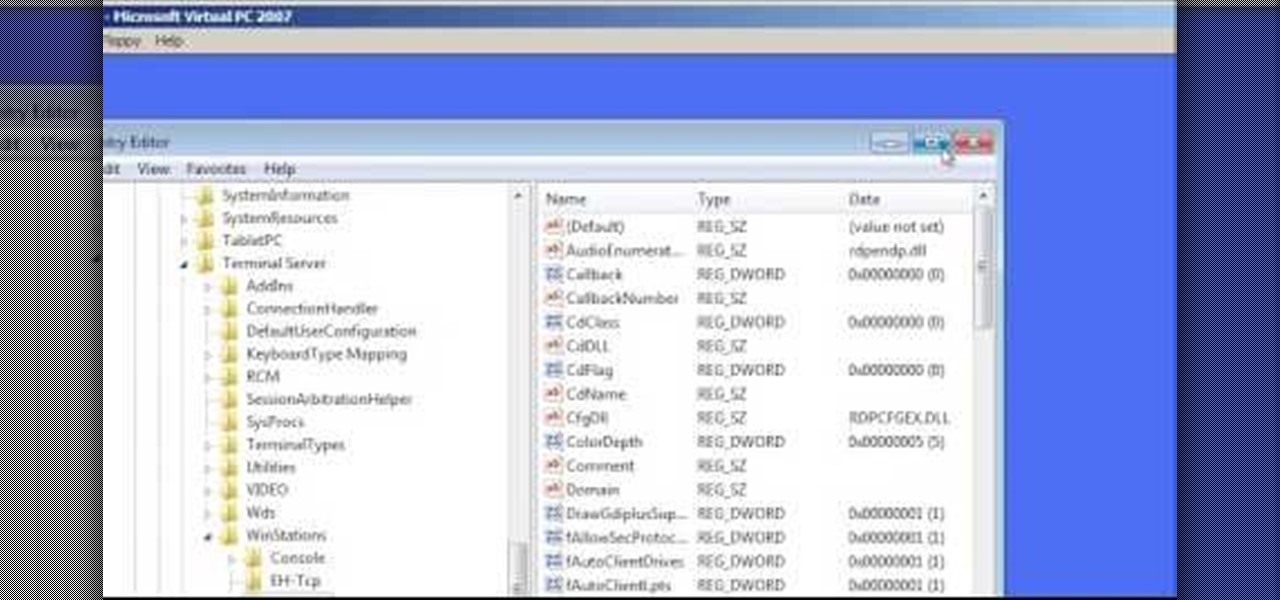
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...

In this video tutorial, viewers learn how to solder speaker lead wires. Soldering is a process in which two or more metal items are joined together by melting and flowing a filler metal into the joint. Viewers are shown how to solder speaker lead wires to the terminals. This video also shows how to solder two wires together and how to solder a wire to a slip on terminal. This video will benefit those viewers who want to learn how to solder and be able to repair other electronic devices.

In this video the tutor shows how to make an ISO image file on a Mac. He shows what the requirements are to get started. He points to the disk utility program from where he points to the option where we can open a disk image from a folder. Now he selects the folder to which he wants to save the image. Now he guides us through the rest of the settings on how to prepare the image. Now we end up with an image file which is in the .cdr format. Now he shows some commands on the terminal through wh...

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Write a fraction as a decimal

If your car has a dead battery, jumper cables can be used to connect to a car with a good battery to start your engine. Begin by positioning the two cars side-by-side, turn off the engines, and lift the hoods to access the batteries. First, attach the red cables to the positive terminals of each battery beginning with the dead battery. These terminals are usually marked with a plus sign or in red. Next, attach the black cable to the negative terminal of the good battery. The negative terminal...

Getting a pro to replace a broken thermostat can be costly, but if you pay close attention, you can learn how to replace it yourself.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

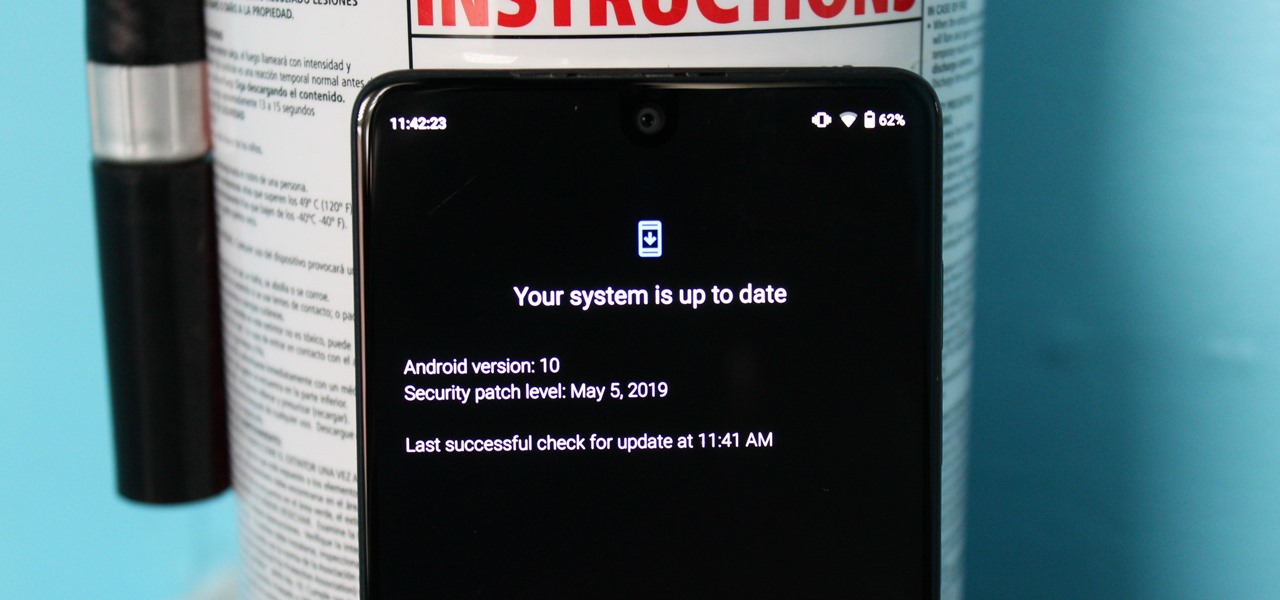
So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

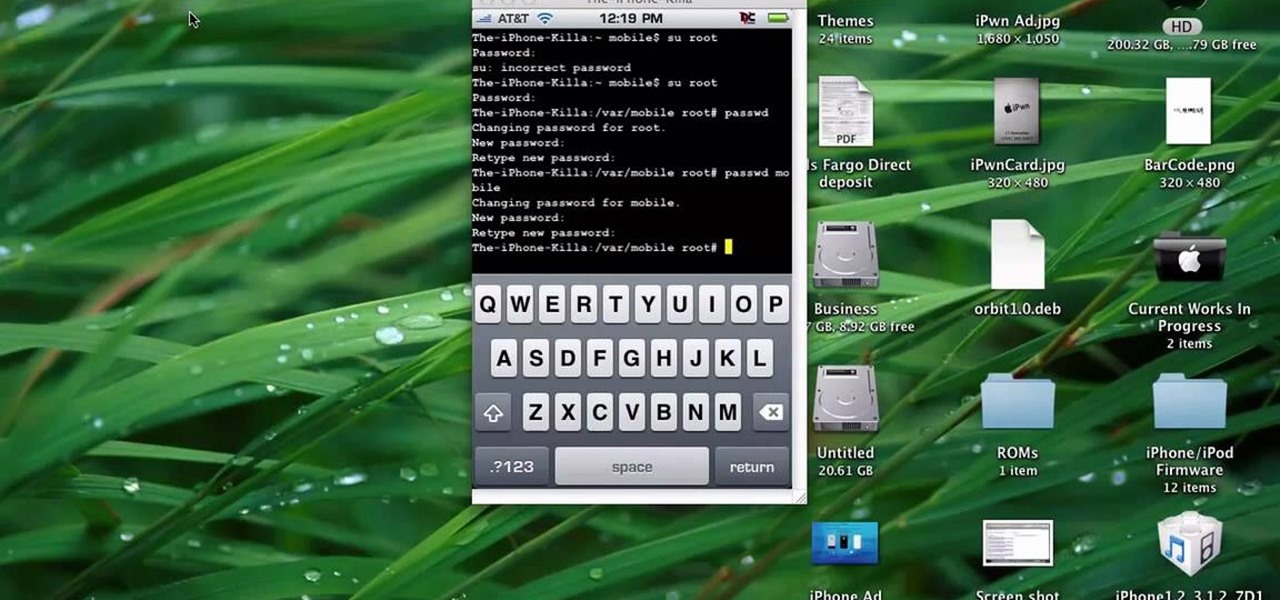
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to enable USB support in VirtualBox on Ubuntu Linux.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Firefox 3.5/3.6 and make it the default browser on Ubuntu Linux.

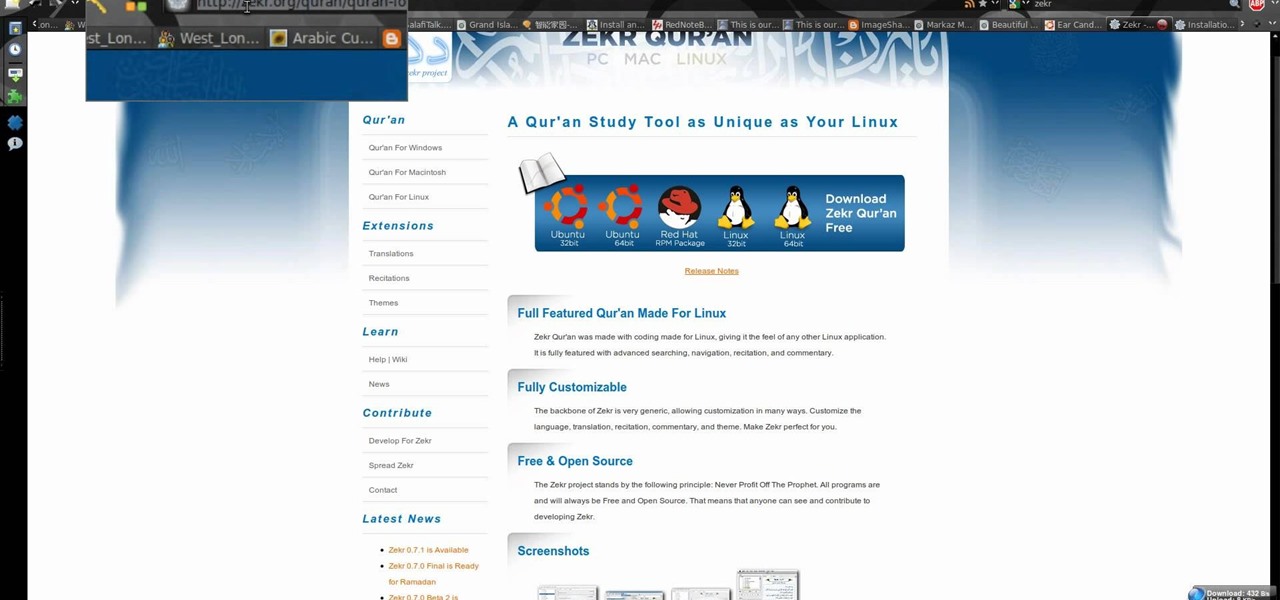
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Zekr (Qur'an Study Tool) on Ubuntu Linux, Windows, and Mac OS.

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Looking for a simple way to update your Linux distribution? This video tutorial demonstrates how to upgrade your Linux distribution via the apt-get command in the terminal. To get started using the apt-get update tool, press play!

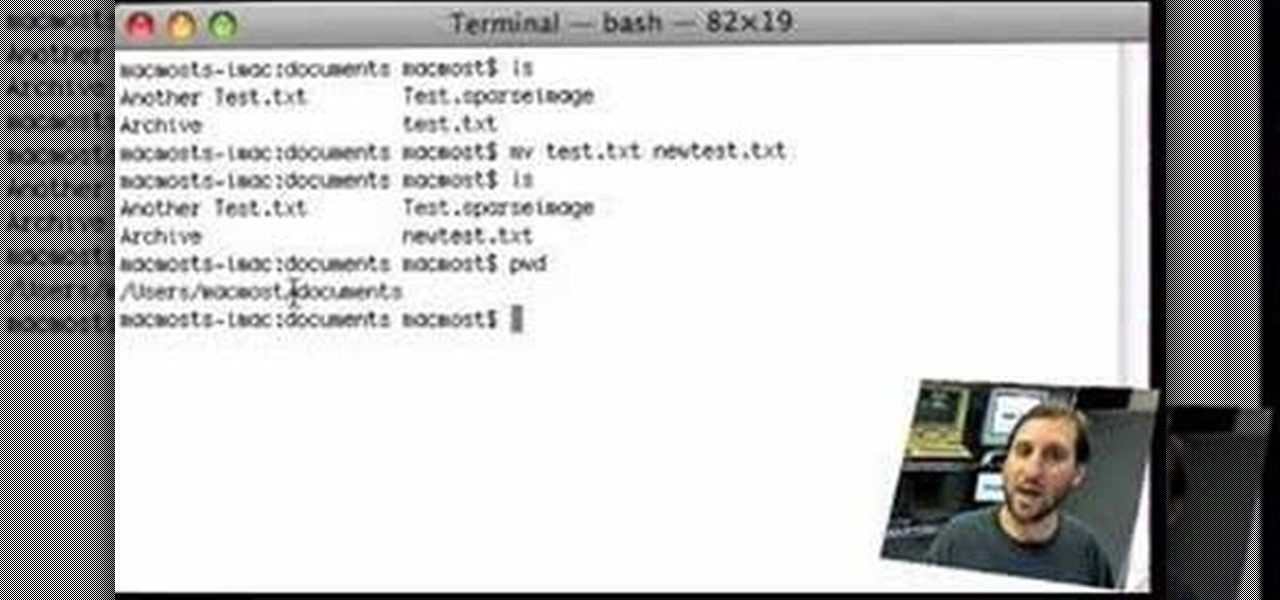
In this tutorial, Gary Rosenzweig of MacMost.com shows you the basics of using the Terminal application. Learn how to navigate, list files, rename, copy and delete. Also learn some shortcuts that experts use.

Gary Rosenzweig looks at various methods for printing lists of files in folders in Mac OS Leopard: downloadable applications, using the Terminal, and simple copy and paste methods.

In this tutorial learn how to eject a stuck CD using a terminal command on your Mac OS X computer.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Earn the secret "Eaten by a Grue" achievement in the single-player campaign mode of Call of Duty: Black Ops with this gamer's guide! In order to unlock this achievement, you will need to break free from your chair and play Zork on the nearby computer terminal.

In this video, we learn how to disable password when waking a laptop. First, go to terminal, then type in "gcomp-editor". Now a configuration editor will open, go to the gnome-power-manager, then lock on the left hand toolbar. After this, un-check the boxes that say "hibernate and suspend", then exit out. Now, go to look at your screen saver preferences and make sure it isn't set to lock when your computer hibernates. After this, when your computer wakes back up, you won't have to worry about...

In this tutorial, we learn how to monitor hardware sensors in Ubuntu. First, go to your Synaptic Package Manager and download any IM-Sensors you need. You will also have to download and install "hddtemp". After you do this, go to your terminal and type in "sudo sensors-detect", then press enter. Answer the questions YES to every question you are asked. When you get to the end, start the chip drivers that are found by typing in "sudo modprobe (driver name)". This is all you have to do to monit...