A childhood visit from the tooth fairy is one thing, but having a permanent tooth knocked out is another, distinctly less enjoyable affair. Act fast and it could be a temporary one. Learn how to deal with a knocked out tooth.

Get luscious, pillowy, kissable lips—with or without injections. You Will Need

Turn your old t-shirts into pillow covers. You will need:

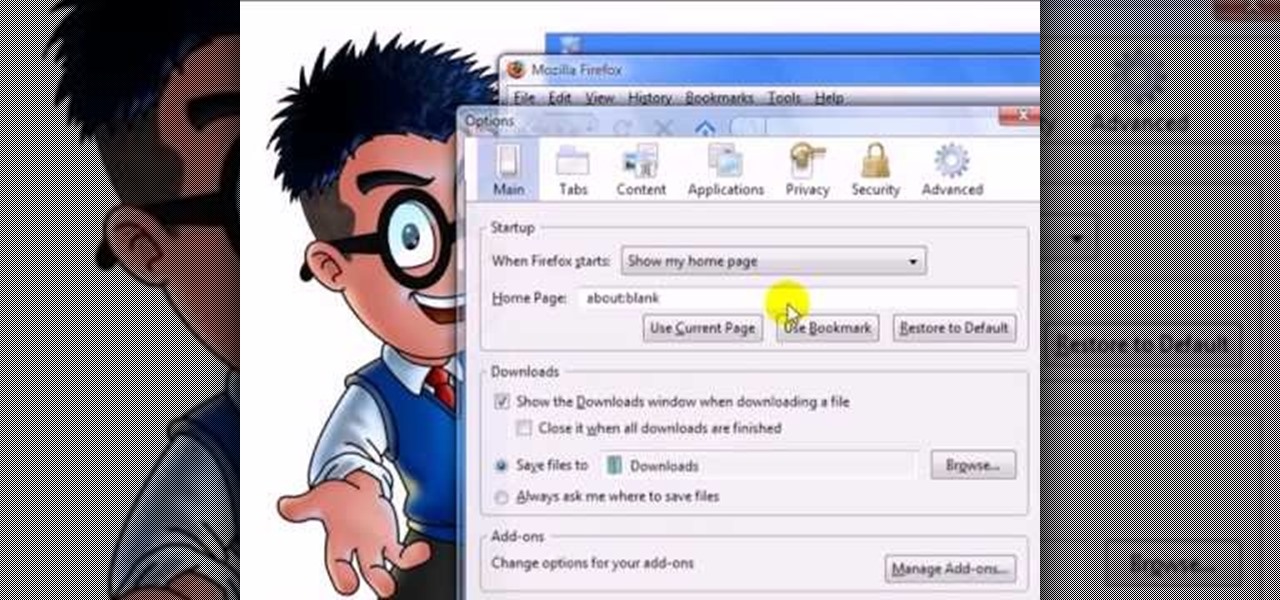
Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Deciding what to remove from your iPhone in order to free up space isn't the easiest thing in the world. You've got to decide which apps, videos, and photos are worth keeping, even though in a perfect world, you couldn't have to part with any of them.

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...

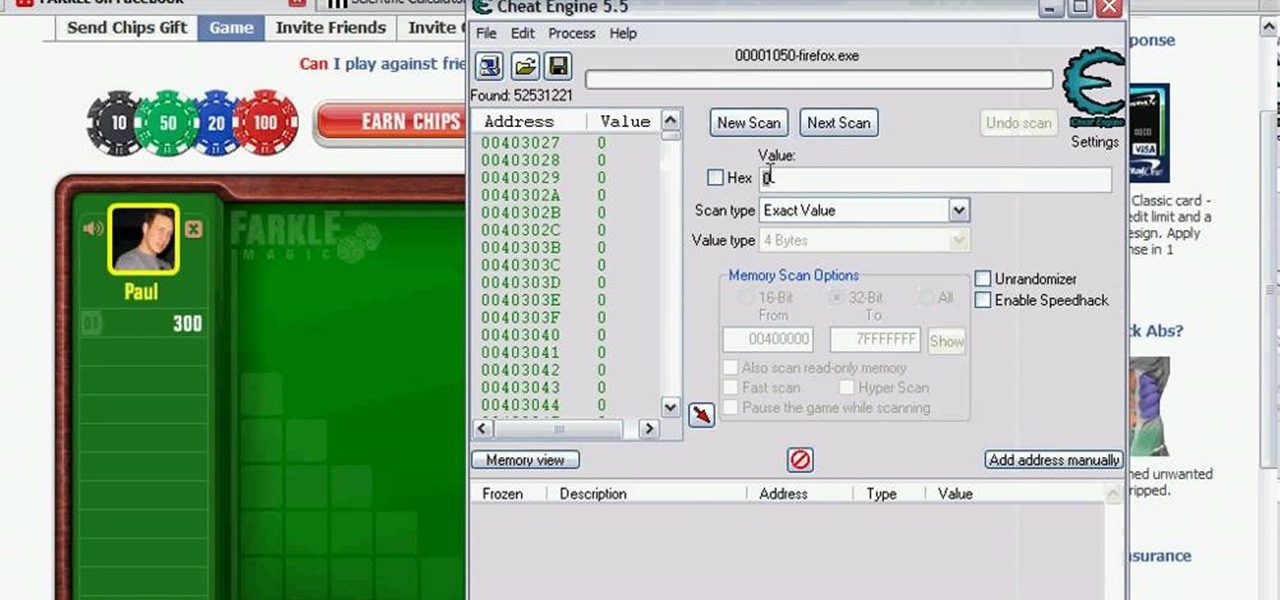
Farkle hacks, cheats, glitches. How to hack Farkle. Watch this video tutorial to learn how to hack Farkle on Facebook for a good score (08/10/09). You will need Cheat Engine for this hack.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Tim Carter shows how to install OSB interlocking panels over a concrete floor. This quick and temporary solution provides a great subfloor to help your basement remodeling.

If you start to feel sluggish and tired, don't worry it's temporary. Your body is going through withdrawl! Not from drugs, but from carbohydrates. Kent tells you how to combat the induction flu and to be happy, it means the diet is working!

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

With the iPhone XS, XS Max, and XR, Apple introduced dual-SIM capabilities to iOS, made possible by eSIM technology. If you recently picked up one of these three new iPhones and need to utilize your eSIM while traveling abroad, you might want to take a look at the data plans offered by GigSky.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

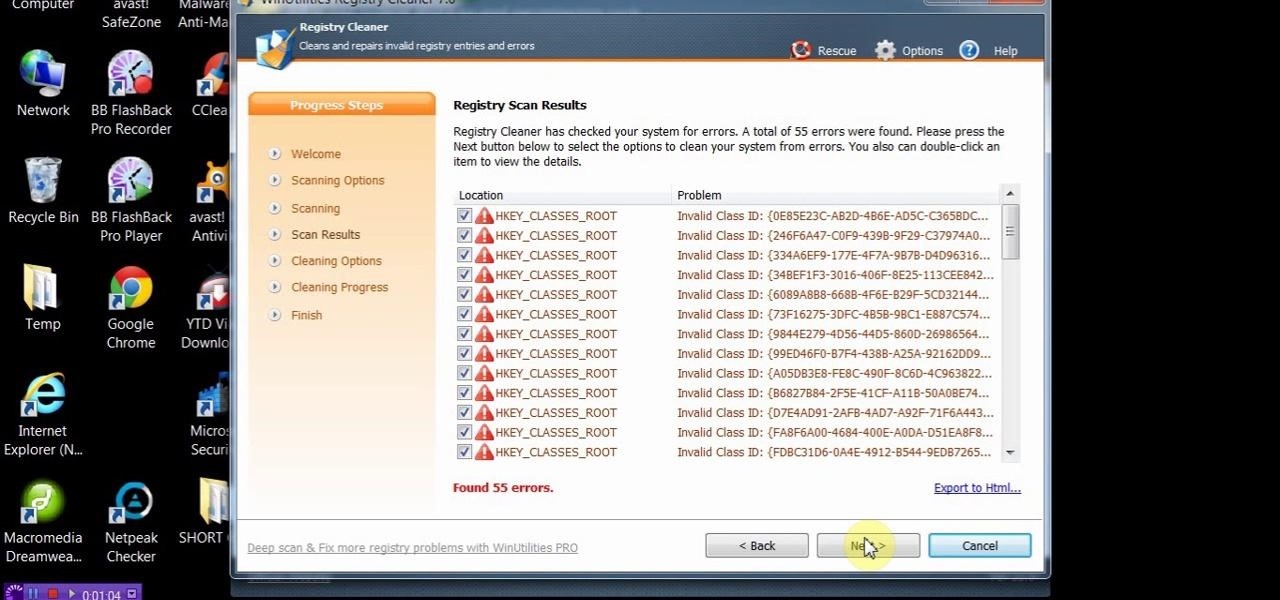
This video will show you how to install and clean your PC with PC clean tool winutilities. This will help you scan your PC for deleting temporary files and make your computer faster.

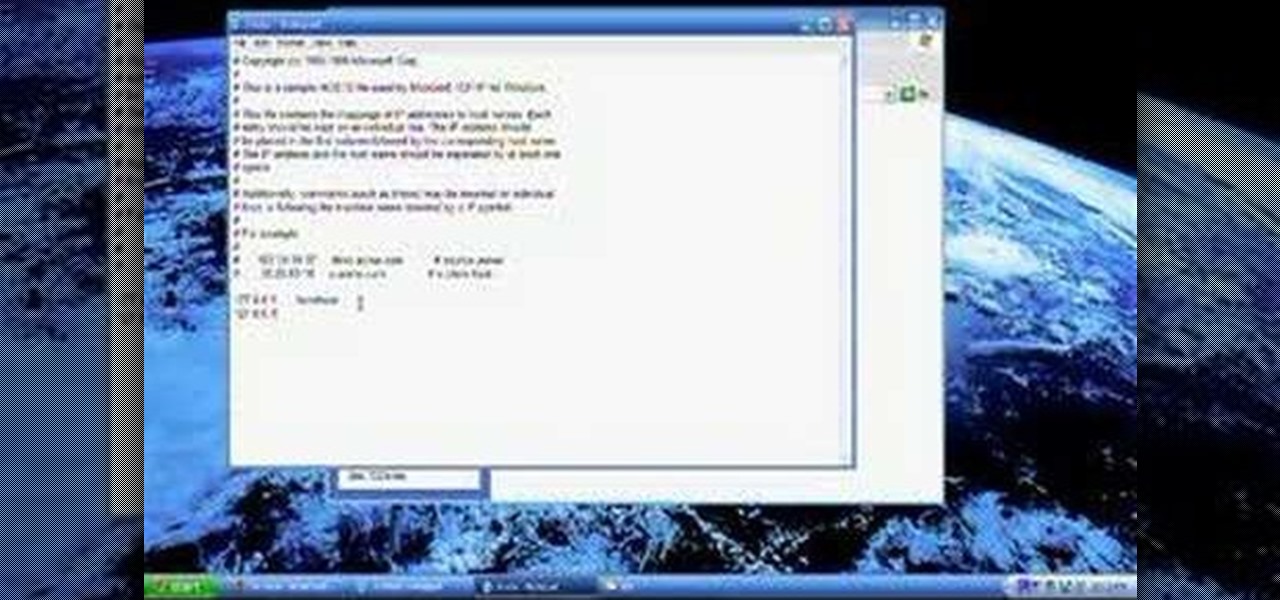
In this video, we learn how to block a website without software. First, open up 'my computer' and then double click on the local disk. After this, open up the 'windows' folder and then locate the 'system 32' folder, open this. Next, open the 'drivers' folder and then open the 'etc' folder. From here, double click 'host' file and then open it with a notepad. Now, after the last text type in "127.0.0.1 (website to block)". After this, save the file and then clean all the temporary internet file...

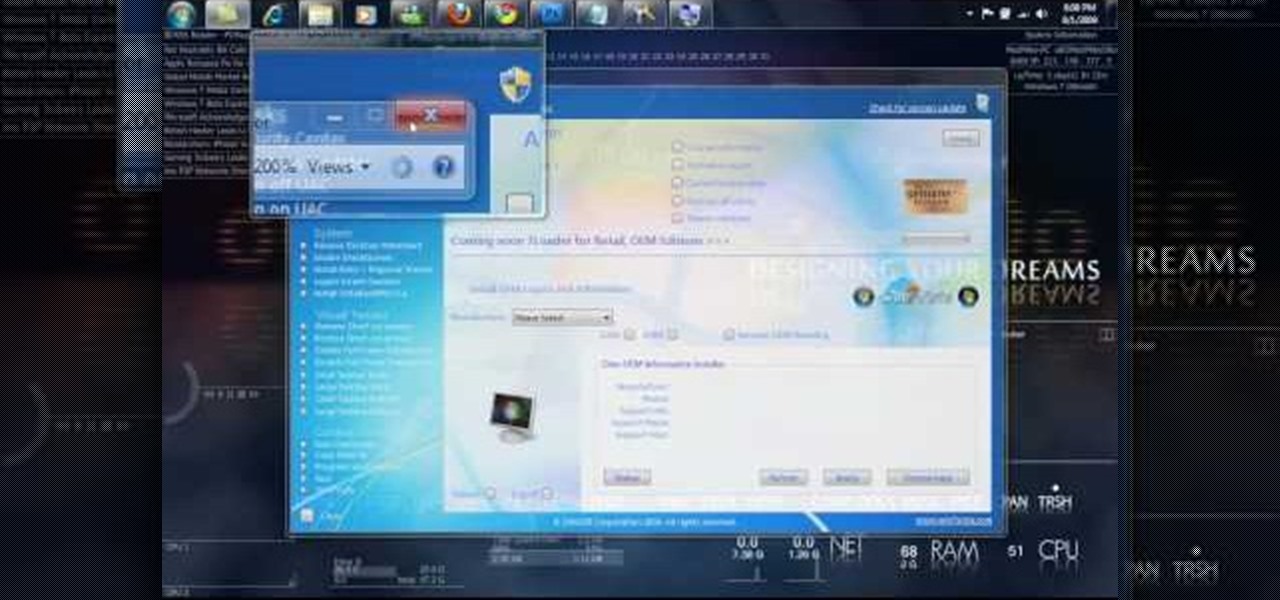
O0OMadMikeO0o teaches you how to activate Windows 7 RTM build 7600. For this you will need the program Windows 7 Toolkit 1.7 by Win7Vista. All you need to do is launch the program and check the box that says Activate Windows 7. After waiting 2-3 minutes, this version of Windows 7 will be activated. Note that this type of activation has an expiry date, so it's only a temporary solution. Before the end of that period, another tool or an updated version of this tool should appear that will solve...

Is your Mac running slow? If yes, then the instructor in this video shows just how to diagnose and fix it. It is not an uncommon problem that a Mac begins to get slow with time. Though there are a million different things that can slow down a computer and it is never easy to pin point the problem, there are a few things that you can do to try and get it fixed. The first thing that you should do is check the free space in the hard disk drive. If it is less than 10 percent then you better start...

With this useful video, you will learn some tips and tricks about how to delete your web browser history, passwords, cookies, also cache form data and temporary internet files.

In our yards where we have brick, stone or pebbles, even mulched areas weeds are constantly growing, creating a nuisance. A weed killer is often used but the results are temporary. This season there are some new products available, these products kill weeds for one whole season. It is a combination of very fast killing ingredients and some that last for a long time. It keeps your patio areas weed free for a year.

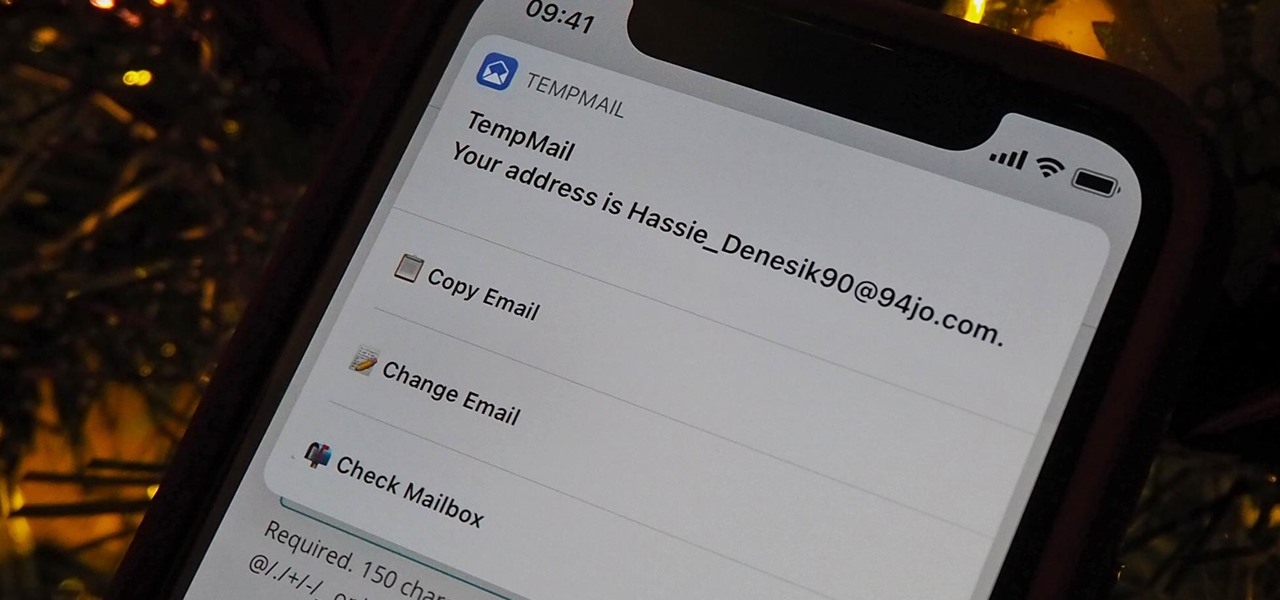
A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

With so many apps being cloud-based, cached data has started to become a problem. This is particularly true if you're low on storage, so developer Dhi decided to do something about it.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

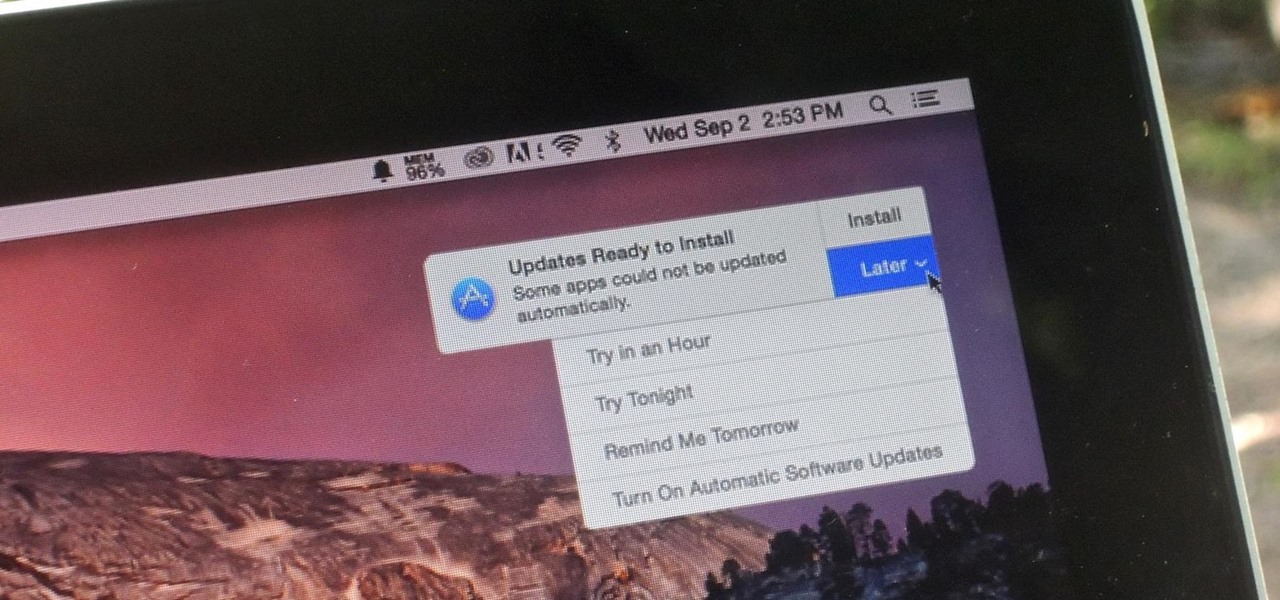
Software update notifications are meant to be a reminder to keep your operating system and apps up to date, but that doesn't mean that they never get annoying.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

Talk about taking one for the team. If you're an eco-friendly earth muffin who refuses to use anything chemical-ridden on yourself and the environment around you, then there exists a gnarly - though effective - approach to killing a tent worm infestation that you may want to try out if you're not squirmy.

Outdoor finishes can be one of the trickiest types of wood finishes to master. Why? Because there is never a one size fits all solution. As woodworkers, we are used to dealing with the seasonal wood movement of our interior pieces. But when one of our creations is destined to live outside, there is much more to consider. Depending on your region's climate, your project could experience anything from snow and ice to hot desert sand storms. How the heck do we prepare for that?!?! Well, it is st...

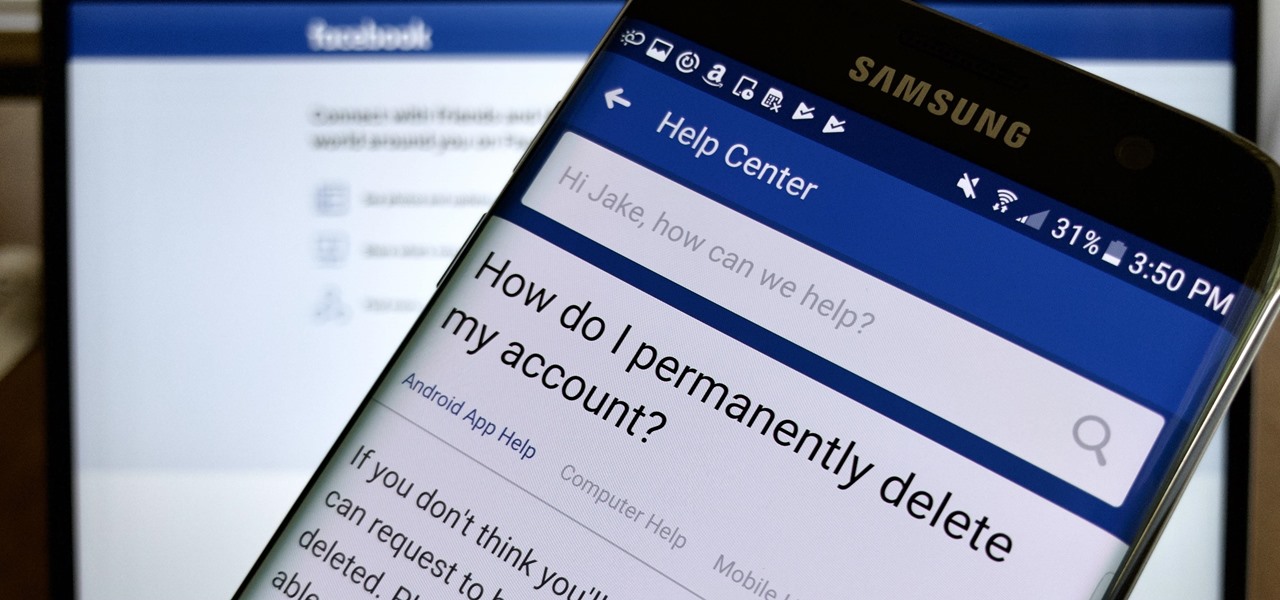
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

Are you a tattoo enthusiast? Well then, there is no better tattoo than mehndi. Here are the reasons: it's natural hence no side effects; it is temporary and fades in a weak giving you the opportunity to try something new each time; it dries up soon and does not have a healing down time. There are thousands of Indian mehndi designs which might be traditional but with a bit of change in placement can look very modern and trendy. One such design is the peacock design. Yes, it is a design seen ve...

If you are a tattoo enthusiast and love trying new designs but apprehensive about a permanent one, Arabic mehndi design is for you. The designs in this form are not ethnic, conventional or traditional but modern and jazzy. It is made using intelligent spacing that not only enhances the design but gives it a trendy look. They are bright and add a lot of glam to the hands as they are made using different coloured henna- brown, red and black and sometimes even glitters. These are the best form o...

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

1. Remove the old makeup and sealer. If you are working on a vinyl or resin doll, you can remove the makeup with a non-acetone nail polish remover. Afterward, wash the face well with soap and water. Work at any stubborn stains with a Mr. Clean Magic Eraser. 2. Sand the head, if necessary. Sometimes dolls will come with set-in stains that no stain remover can touch, or with scratches and gouges in the face. If your doll head is made of resin, in particular, do all your sanding underwater to pr...

Want to make makeup like the Joker? Watch this how to video. Products used:

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.