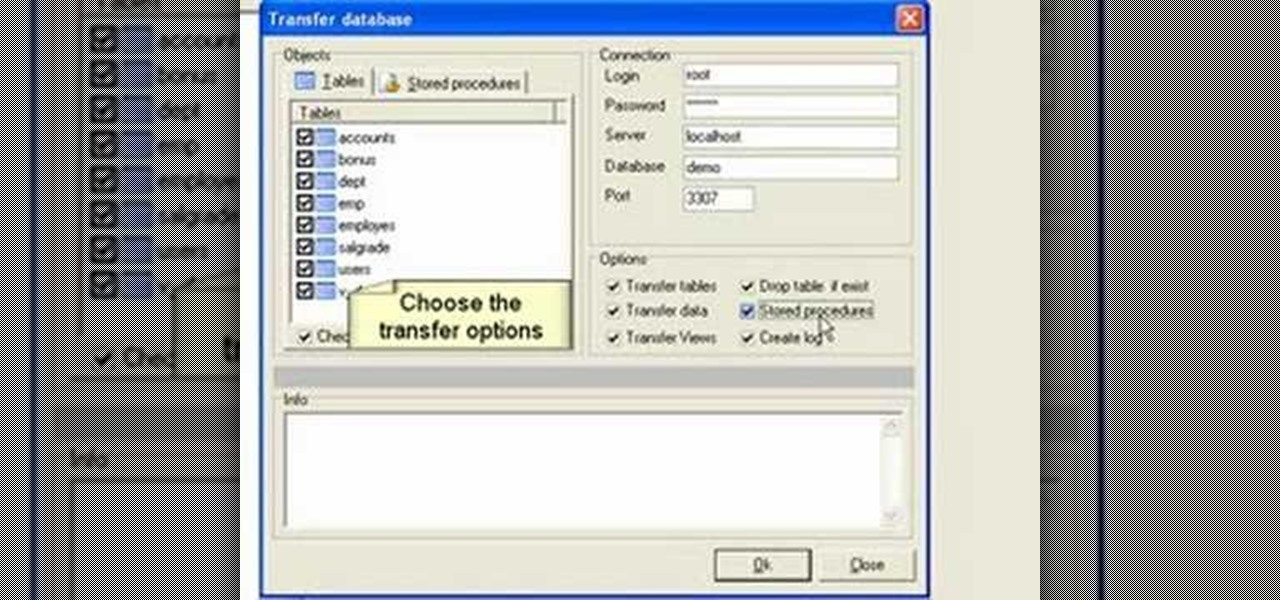
If you're new to DreamCoder for MySQL, one of the things you may want to know how to accomplish is how to exchange information between two remote MySQL databases. Happily, this tutorial will walk you, step by step, through the process. To learn how to transfer data between two MySQL databases simultaneously within DreamCoder for MySQL, take a look!
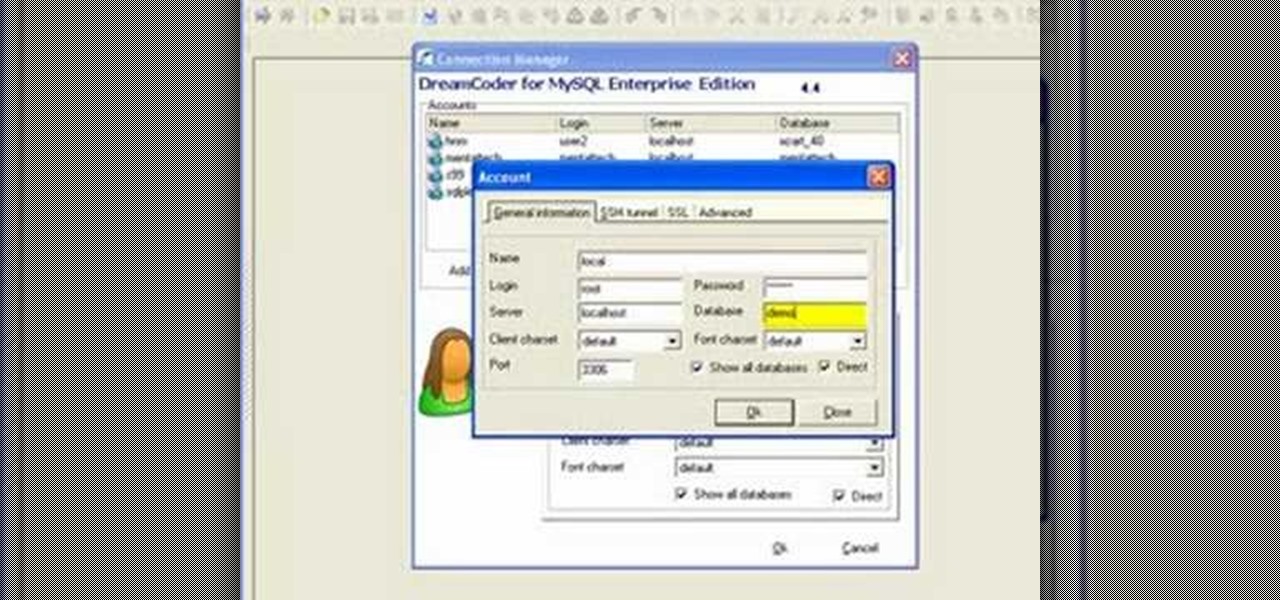
If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Watch this instructional crochet video to crochet a bullion or roll stitch flower. This is a difficult crochet stitch to accomplish. You should master the bullion stitch before beginning to crochet this flower design. Use any type of thread and crochet needle to complete this project. The bullion or roll stitch creates a complex crochet weave for hyper-designed crochet projects such as this intricate flower.

Watch this instructional crochet video to crochet a bullion or roll stitch. This is a difficult crochet stitch to accomplish. This video provides an alternative method of completing the crochet stitch using a homemade tool. Use any type of thread and crochet needle to complete this project. The bullion or roll stitch creates a complex crochet weave for hyper-designed crochet projects.

The HV20 comes with a manual focus roller, which is a good thing. However, it is a bit awkward to operate. Here is a minimalist friction tool that can be used to accomplish the same task (well, perhaps with enough practice). It is small, portable, cheap, and light-weight. Watch this video tutorial and learn how to build a manual focusing stick for a Canon HV20 video camera.

What is a freegan? It's an anti-consumer movement, and a way of getting free food by dumpster diving. Get a crash course in dumpster diving with an accomplished Biology professor who demonstrates the lifestyle of a freegan. Watch this video ecology tutorial and learn how to dumpster dive.

This quick, simple how-to video will show you how to transfer mp3s from your iPod back to your iTunes, a functionality disallowed by the iPod. This is accomplished with a freeware application named Senuti whose slogan, fittingly enough, is "Everything in reverse."

You can add character to your windows by casing them, an easy process that you can accomplish with a few mitre cuts. Learn how to case windows using this decorative style.

Today's word is "endeavor". This is a noun as well as a verb. As a noun, it means an effort or attempt to accomplish something. As a verb, it means to strive or attempt.

Today's word is "achieve". This is a verb which means to attain, accomplish, or obtain something successfully by effort.

Today's word is "thwart". This is a verb which means to prevent from accomplishing a purpose or a plan. For example, you can say "The police thwarted three terrorist attacks at LAX last month."

Watch this video to see how to make a paper flower pop-up card. To make things even better, you only need one piece of paper to accomplish this pop up paper card flower. Just grab your one piece of paper, some scissors and some glue and you're ready to make awesome flower cards.

Sometimes you need to print a perfect 5x7" or 8x10" photo that will go into a frame with correct aspect ratios. Or maybe you need to make an image for a video that will be just the right size for DV. Photoshop has a variety of ways to accomplish this task, and in this video Terry White will show you some of the easiest ways.

Darren Matthes explains that he uses a series of 16th notes to accomplish his Cajun or Dixieland beat. He claps it out and gives pointers on how to crash the high hat on the upbeat and

Learn how to explore the world of photography from a kite's point of view with this aerial photography rig (also known as KAP). Bre Pettis and the accomplished guys at Make Magazine decide to use a VEX robotics kit to do the job.

In this free video exercise lesson, you'll learn a popular variant on the push-up, one designed to target your triceps. With pushups, as with any body-sculpting exercise, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. For more information, and to get started using this exercise yourself, watch this handy home-fitness how-to.

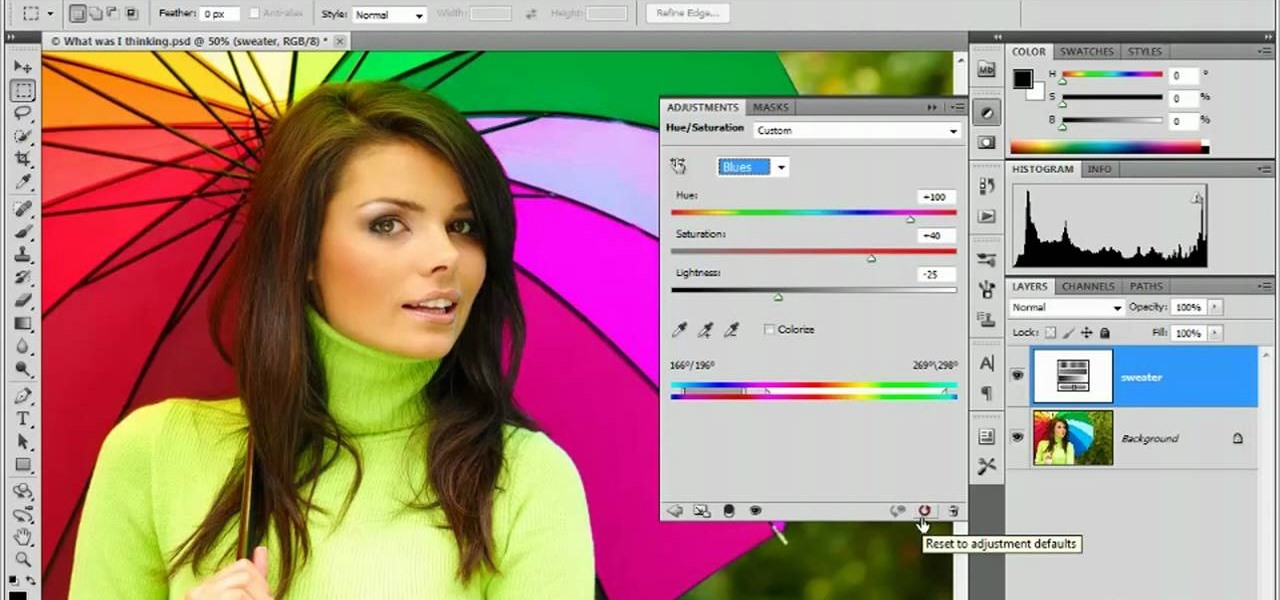
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Department store chain Target is the latest retailer to offer an augmented reality cosmetics app for customers to virtually try on lipstick.

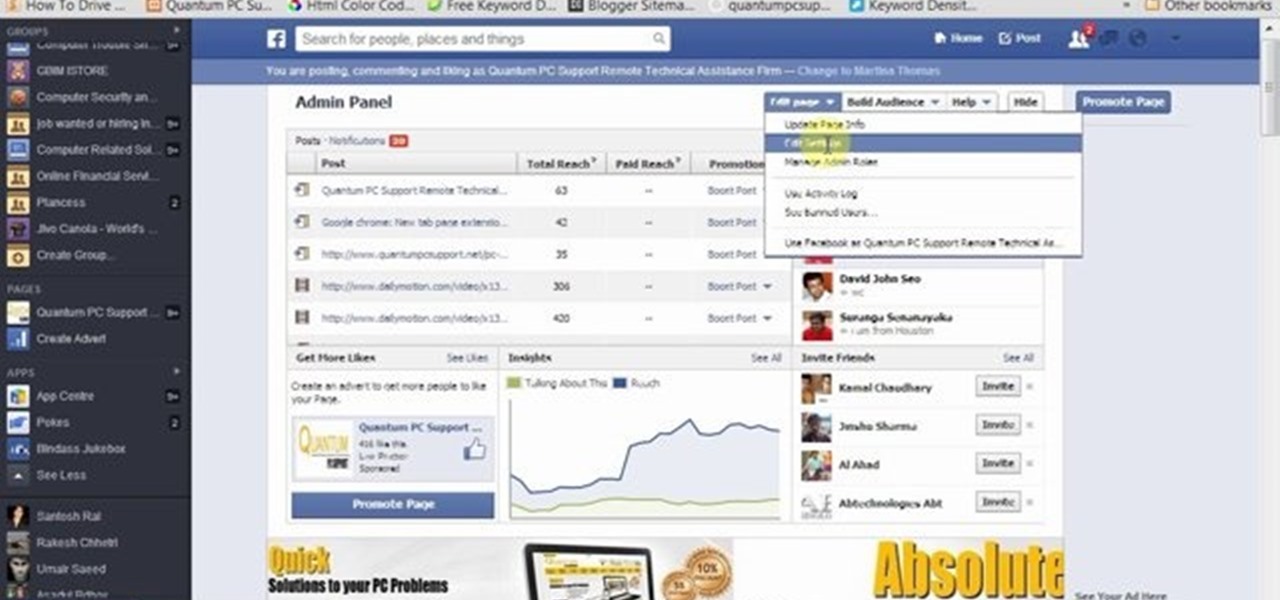
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

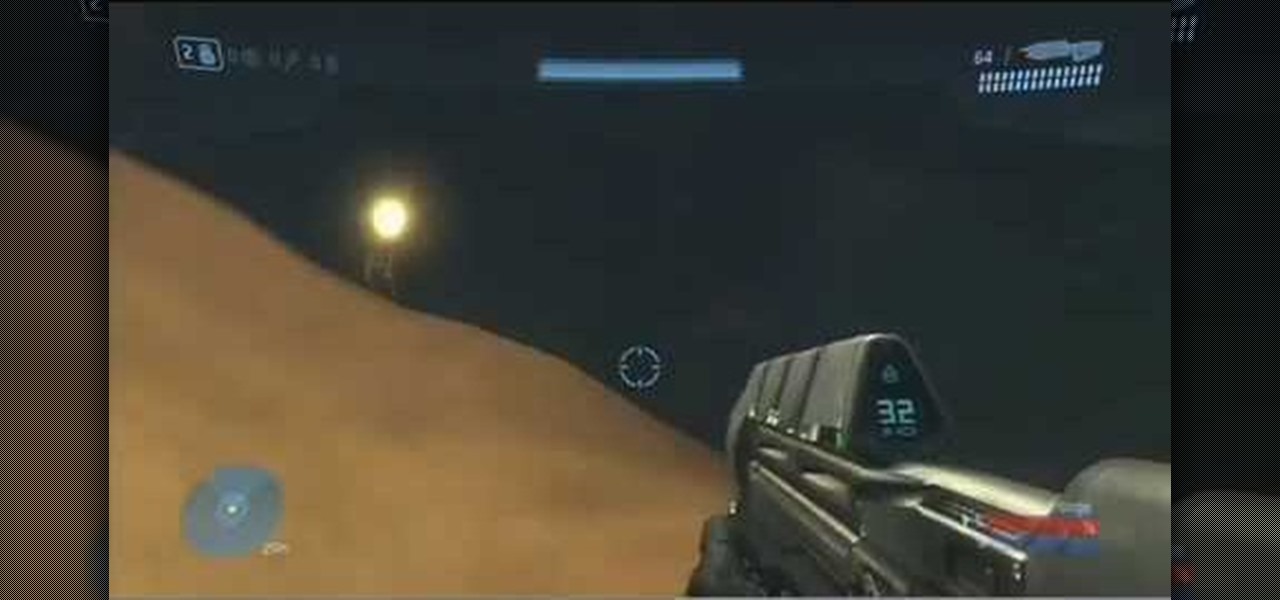
In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

The Toolbox in Office 2008 for Mac is more than just a simple formatting palette. There's so much you can do, so much you accomplish, but you need to know how to take advantage of everything offered in the Office Toolbox, whether in PowerPoint, Entourage, Word, or Excel. The Microsoft Office for Mac team shows you just how to format, insert, research, and clip with the Toolbox in this how-to video. Check out all of the things it can do!

What's better— forking out the dough for a new headlight or simply restoring it to its original beauty? The latter is definitely the choice for penny-pinchers, and is easy to accomplish with a restoration kit from 3M. This video will show you how to use the 3M Headlight Lens Restoration System to restore your headlight's shine.