
How To: Play "Circus" by Britney Spears on guitar
Learn how to play "Circus" by Britney Spears, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:


Learn how to play "Circus" by Britney Spears, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

To make your very own Spartan Spear, like in the movie 300, you just have to follow a few short, easy instructions. Start off by taking a broom stick, and cutting off the end. Make sure your broom stick is empty inside. Then take a hammer and flatten the last few inches of it, hammering it into a point or a flat blade at the end. Cut off part of the tip at an angle on either side, then open it back up with pliers. A few inches below the opening, take your pliers and press in on the broom stic...

Miss Jessica Harlow replicates the makeup look from Britney Spears' music video "If U Seek Amy." This tutorial focuses on applying eye makeup.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Many superstars have fallen to the devastating power and destruction of the finisher wrestling move known as the Spear. Among the wrestling superstars who have made this move incredibly popular are Edge, Rhino, Bill Goldberg, and the up and coming superstar Roman Reigns. In this professional wrestling video tutorial you will learn the basic concept and performance of the Spear.

If you're interested in learning how to cook asparagus, check out this video. Asparagus can be quite tasy when cooked right!

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

It's been a while since most people have really cared about Britney Spears music, but many of her songs really are great pieces of pop. In this video you'll learn how to cover her song "Everytime" on solo piano, making it distinctly classier than it usually is.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

BoA is sort of like the Asian Britney Spears. Many years ago, the now twenty-something Korean singer launched herself into KPop superstardom with hits in many languages (she speaks Korean, Japanese, and English) and an effervescent style every girl wanted to emulate.

In Halo: Reach, one achievement that may seem impossible is the "Lucky Me" achievement. If you've been struggling to find closely grouped units, or your friends just don't want to stand there and let you kill them, here's one way you can do it in the campaign mode. In this video you will learn how to earn the achievement on the Tip of the Spear mission after you crash in the falcon.

Phish bone keychains feature a highlighted midsection with three different colors of hemp (in this video we use regular rafia-colored hemp, red hemp, and green hemp) that surround wooden beads.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!
If you've ever wanted to make a homemade collection of karaoke songs or belt out your own version of Britney Spears over her own song, then this video might come in handy. Learn how to remove vocals from a stereo recording in Reason/Record with help from Reason expert, James Bernard.

Youtube Makeup diva Julie G gives us another installment in her glamorous makeup tutorials. Whether you're new to makeup application or you're a practiced hand, Julie's style ideas and tips are sure to give you some inspiration. This look is based on Britney Spears's makeup in the "Circus" makeup look, and can be recreated with these makeup supplies: Urban Decay Primer Potion, MAC: Time and Space, MAC: Swiss Chocolate, MAC: Dark Edge, MAC: Carbon, Jordana Easy Liner For Eyes: Brown Suede, Urb...

Introduction to and history of the timbei (shield) and rochin (short spear or halbert), as well as stances and striking points.

Slim stalks of asparagus just scream of spring. Blanching or steaming has long been the cooking method of choice for these tender spears, though all that moisture can leach out the bright green color and make asparagus stringy, even mushy. Roasting or grilling asparagus concentrates the sweet, green-ness of the vegetable and adds a crispy, caramelized crunch that makes it irresistible.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Ex girlfriend tracking you like a stalker? Find the leaks. She may be going through your email or phishing some information. Does she want a confrontation? Lure her to a public place then get her to cause a scene in front of security. Or last case scenario, fake your own death!

Ok, so you clicked through and there's no Britney Spears. I would have used an image of the mysterious Molly Lewis, aka, sweetafton23, but you can barely see her face in her ukulele cover of Britneys Spears' pop classic, "Toxic".
From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Tune into this hot dog how-to video and watch host Scott Herbert get frank about his passion for Chicago-style hot dogs. Also, learn the secret to a frosty root beer float that's especially sweet when made with Whole Foods Market's 365 Everyday Value root beer crafted with cane sugar, not high fructose corn syrup.
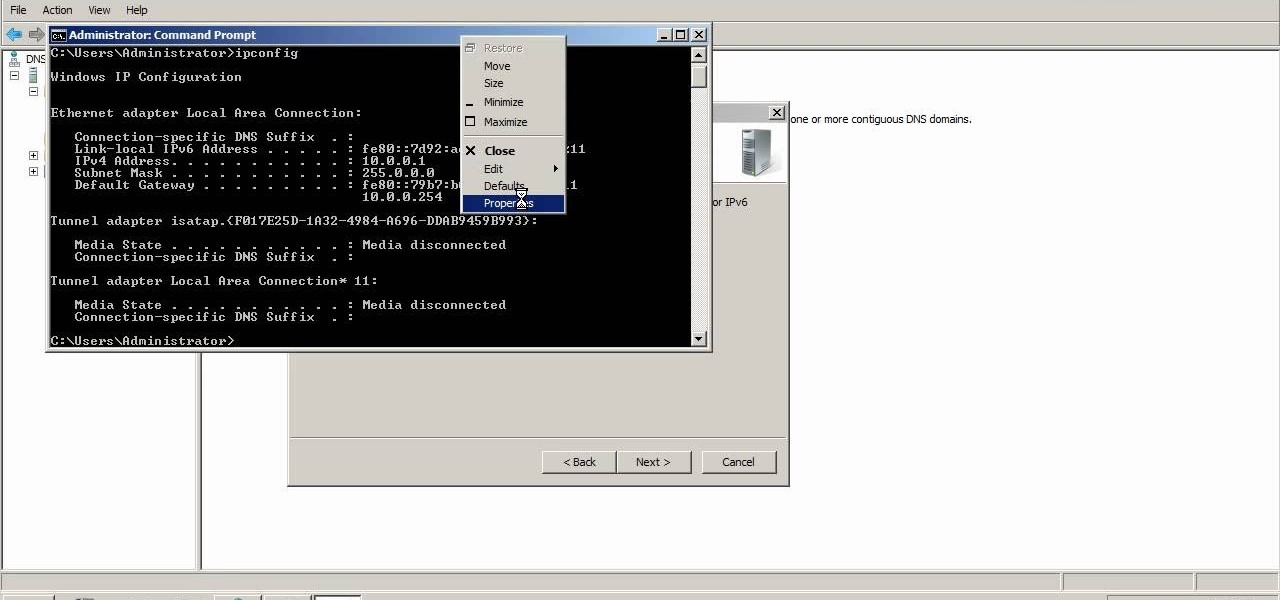
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Sarah East from Grocery School gives a lesson on how to buy fresh asparagus. Look for straight, firm stalks with dark green or purple tips. It is best to choose stalks the same size so they will cook uniformly, though the size does not affect the flavor.

gimme! gimme! gimme! more? This isn't a britney spears song, pffft.

Okay, you've mastered the boffer sword and the boffer sphere. Now what? Perhaps a boffer staff?

Nintendo's first ever game for Android has finally touched down (unless you actually count the abomination that is Miitomo). Fire Emblem Heroes, a classic turn-based RPG optimized for mobile gaming, has come out for Android and iOS in Australia, Europe, and Japan, and is due out in North America and other worldwide locales very soon. Due to Nintendo's staggered release, the game isn't available to us in the United States at the time of this writing, but fret not—there's another way to downloa...

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

This is a nice look. You will like it and it is inspired by Britney Spears. It is not that hard to do. It takes some time to do, but you just need to follow the steps.

Learn how to play "Womanizer" by Britney Spears, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.