Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.
In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While Modiface, YouCam, and others have been playing in the virtual make-up marketing pool for a while, here comes Google ready to splash down with a cannonball.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Looking to work on your form? Try this free video golfing lesson for size. In short: When putting, to be able to release the putter down the line to your target, the club must travel slightly inside the target line. For a complete overview of how to become a better putter, watch this video guide.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

This video will show you how to target your audience for Facebook post. You could set country, language, age group, qualification, etc. for watching your post. Watch the video and follow all the steps. Employ the technique in your Facebook account.

Looking for a way to speed up the boot time on your favorite programs in Windows? This video will show you a little tweak to make your most-used applications start up in no time. Basically, you just go to the "Shortcut" tab in the program's properties menu. Then add " /prefetch:1" to the end of the target location in the "Target" box. This tweak works on PCs running Windows 7, XP or Vista.

In this Pets & Animals video tutorial you will learn how to train your dog to perform the "cop-cop" trick. In this trick the dog learns to put its feet on your feet. Step 1 – teach the dog to target a book or a mat with their feet by offering them some treat. You can do this either by appreciating or clicking when both the feet touch the book. The next step is getting the dog to target the book with their feet while they are between your legs. You have to continually reinforce the dog to ma...

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

The SOFLAM is a gadget that you can use in Battlefield 3. It is a team based gadget that you deploy and use to laser target. It is different than a mortar and can be a little hard to use. This guide will show you how to get the most out of a SOFLAM so that you can tear up the other team.

This Giant Bomb walkthrough will take you through the Iron Golem boss fight in Dark Souls. The Iron Golem is the last boss in Sen's Fortress and has a long reach. You will need to target the back of its legs in order to defeat it.

Just because you need to assemble an outfit for work doesn't mean it has to look all boring and aging. As long as you stay mostly covered up and don't pull out your neon-colored cheetah print stockings, you'll do just fine accessorizing and dressing fashionably.

Pretty Little Liars is the newest part of the increasingly puzzling lineup of shows on ABC Family that seem to be creating a new demographic to target as they go along. The girls on it are very pretty, and this video will show you how to create a makeup look inspired by the show's star Alison DiLaurentis.

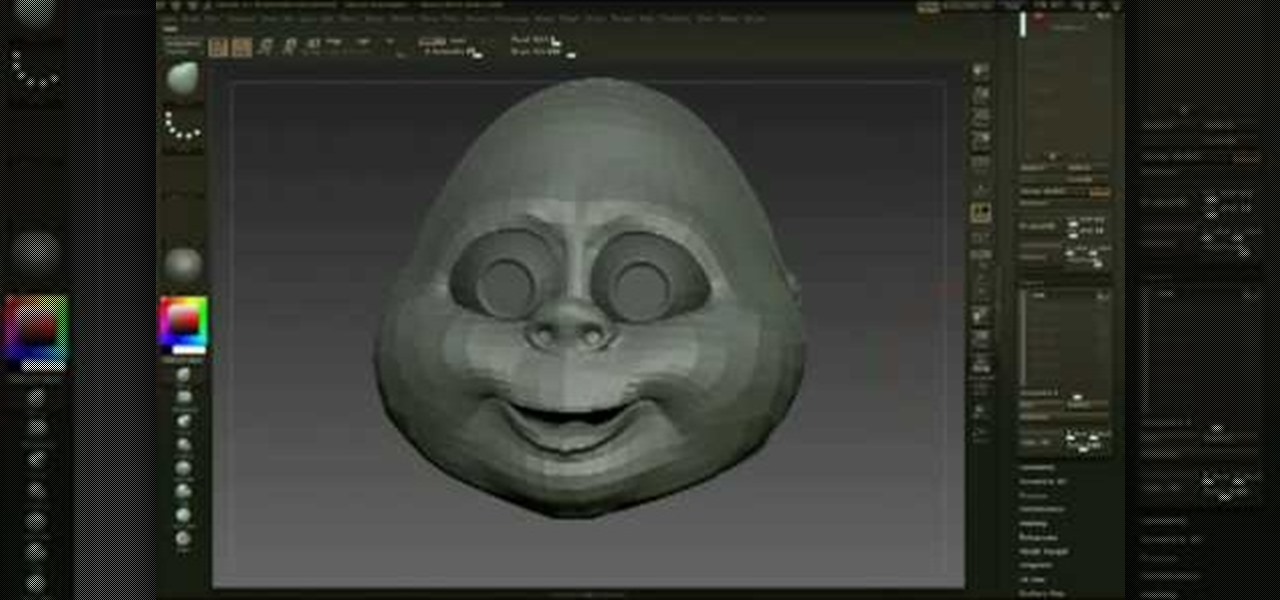
THis video from accredited 3D art instructor Andrew Klein covers how to create symmetrical and asymmetrical blendshapes using the 3D sculpting program Zbrush. This is a fairly complex process, utilizing transpose masking features, move brush, smart resym, and morph target tools to accomplish its goal of creating a really cool animated 3D mask.

In this video tutorial, viewers learn how to properly shoot and sight in a compound bow. It is recommended that users use a release. Your body should be perpendicular to the target. Hold the bow vertically, and hold it with a relaxed and secure grip. When you are ready to begin shooting, learn a technique that will help you relax and steady the bow. When you draw the bow string back, you should be looking through the peephole on the bow string and where the target and pins come into view. Thi...