There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

If there's an iOS app you want to hide from your iPhone's home screen, there are a few built-in ways to do so in iOS 14, but there is a clever workaround you can use in older iOS versions. Plus, it also works in iOS 14 as a way to disguise app icons instead of just hiding them, so no app is what it seems.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

They say cheaters never prosper, but how will your know for sure if you don't give it a try? By a little repositioning of the blindfold and some spacial awareness you can be the master at this classic party game.

Easter isn't the typical occasion for pranking your friends, co-workers, or boss (if you dare). But this Easter egg-inspired prank by Redditor cheesewing is pretty ingenious, and handing out chocolate eggs any other day of the year might raise some suspicion.

We are planning a surf trip for late April to Bocas del Toro. The excitement is part pure glee and part a slight suspicion things will spin wildly out of control as soon as we leave LAX.

Whether you really need to pinch pennies for a long road trip or are really at the end of your rope with your financial and living situation, desperate times call for desperate measures--and sometimes that involves living in your car for an extended period of time. It is certainly not easy, but with the right equipment and know-how, making your car your abode is certainly possible if you make the continuous effort to keep things clean, be smart about where you park your car and avoid arousing...

I sometimes play on a survival server where griefing is not only allowed, but almost encouraged. Keeping yourself safe and other on their toes is important. :)

As of right now, Guinness World Records claims that the highest human flight with a rocket belt is 152 feet, accomplished by Eric Scott in 2004. But they may need to update their records soon thanks to Martin Aircraft Company in New Zealand, whose Martin Jetpack finally showed the world it can fly—really fly.
Some interesting news this week, from Obama's new political ad, to the $20,000 payments by Cardinal Dolan. Take a look:

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

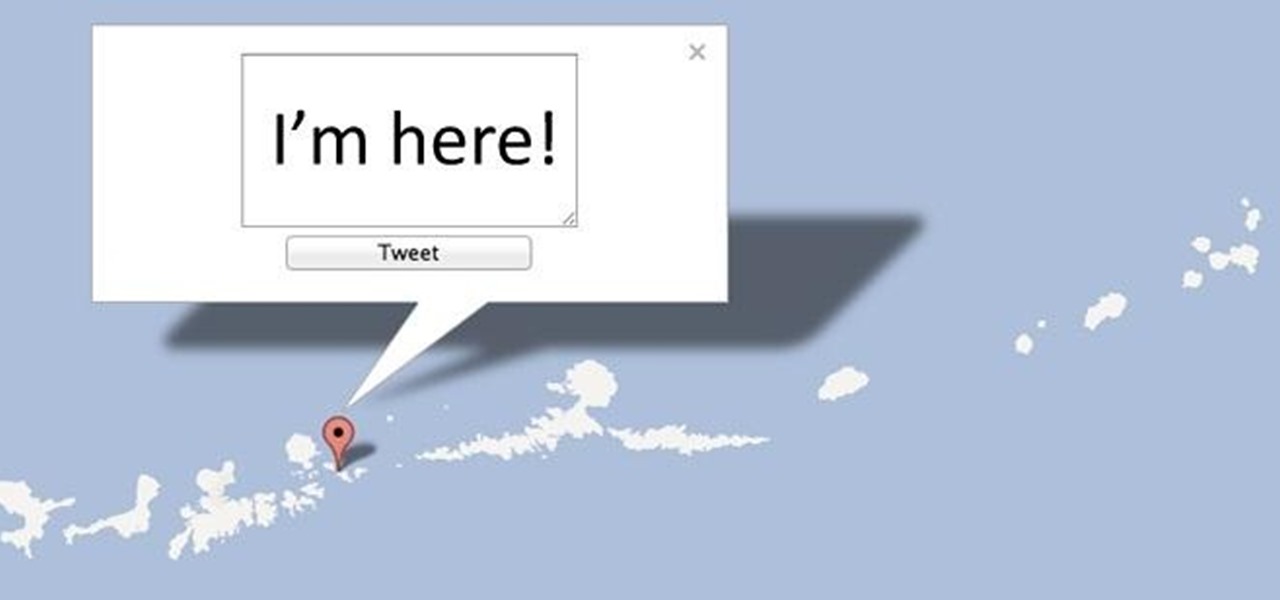
There are plenty of reasons not to use location information when you tweet, whether you're trying to stay safe or just don't want your crazy ex showing up while you're in line at the grocery store. But a new website called 'Please Don't Stalk Me' could actually make broadcasting your location work to your advantage—it lets you tag your tweets with any location you choose, anywhere in the world. Playing hooky? Send a tweet from 'home' to take care of any suspicion from your boss and coworkers....

Disguise yourself how ever you like. Go to an airport. Have your suitcase full of fake illegal items such as powder (drugs), crushed up leaves (weed), guns and Knives dynamite make sure everything looks as real as possible and also something metal to set off the detector (so they search your bag).