In this how-to video, you will learn how to properly study for a test or for homework. The author offers a few great tips. You should avoid cramming and study well before the test date. Make a list of everything that is going to be on the test. Memorize facts and formulas. Make up questions that you think are going to be on the test. Take all the school tools you need in order to complete the test. Lastly, if you prepare well, you will have a great chance of doing well. You should try to stud...

Solve this chess study by Schultz (1941). Grandmaster Alexandra Kosteniuk shows you just how to do it in this chess video tutorial. White plays and wins. In order to win, white needs to promote his pawn down the board -- the unstoppable pawn, to get a queen in this chess endgame.

Learn from this chess video tutorial, hosted by Grandmaster Alexandra Kosteniuk, on how to solve the chess game study from the Book of Salvio (1604). White plays and wins by sacrificing his rook and moving his pawn up the chessboard to get queened. It's as simple as that. Endgame chess is a great thing to learn to become a master.
Find out how to dramatically reduce study time & increase your grades. Included is a flow chart to see exactly how to reduce your study time.

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.

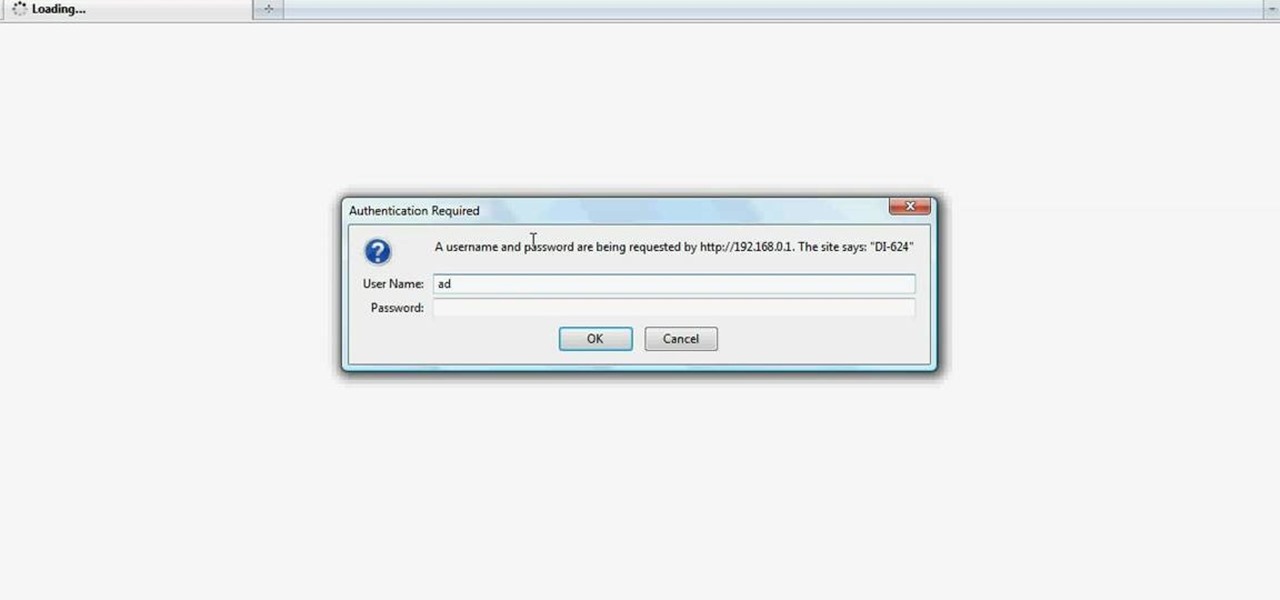
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

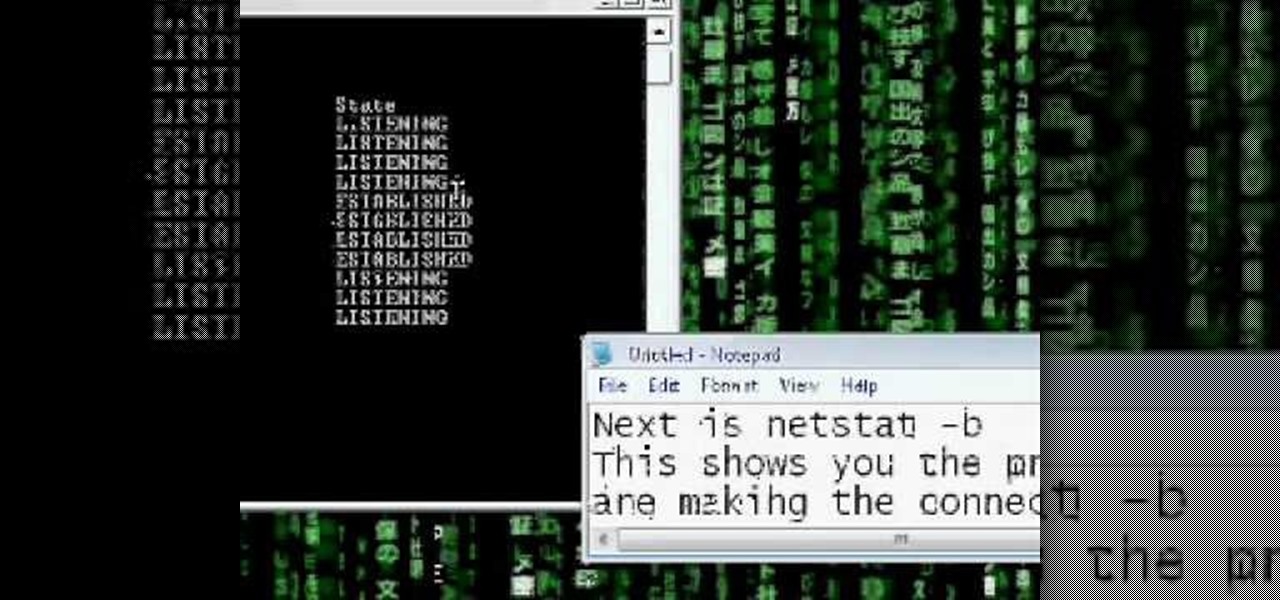
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

In this tutorial, we learn how to know the difference: census, study, & sample survey. The census is when everyone's opinion is needed. An example is when you will see census studies happen throughout the year from the government seeing how many people live in one household. A study is when you only need the opinion of experts. This can be when companies are releasing a new product and need the opinions of doctors or dentists about it. A sample survey is when a few people's opinions are enoug...

If you have a ton of books and no place to store them, a bookcase may be needed. Buying one from the store is an easy way out, but building one on your own is another great idea. Not only will you have the power to determine how it looks and what size it will be, but you'll feel satisfied knowing you made something useful.

If you are looking to improve your classical piano technique then this how to video is the place to start. You will learn how to practice and study Chopin's "Ocean" etude opus 25 number 12. This detailed lesson goes over where to place the accents, analyzes the dynamics and staccato playing technique. This piano tutorial teaches you the best way to practice it so you can Chopin's "Ocean" etude op.25 no. 12 quickly and easily. With this concise classical piano lesson you can improve your techn...

Let Grandmaster Alexandra Kosteniuk teach you how to play a game of chess in this chess video tutorial.

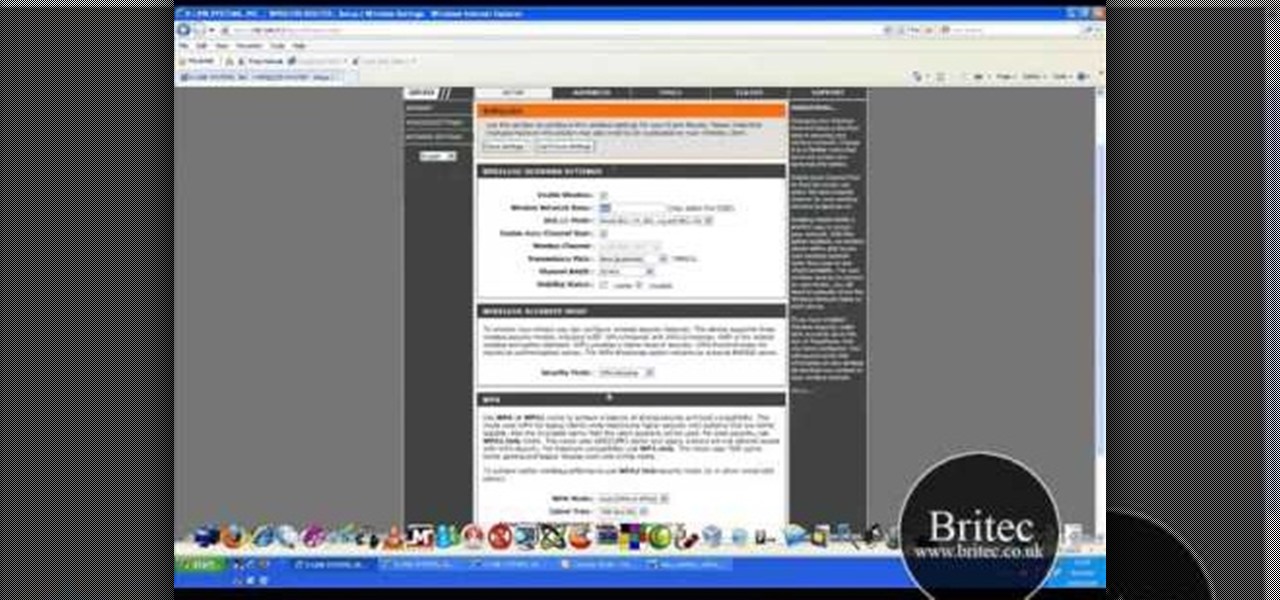
This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

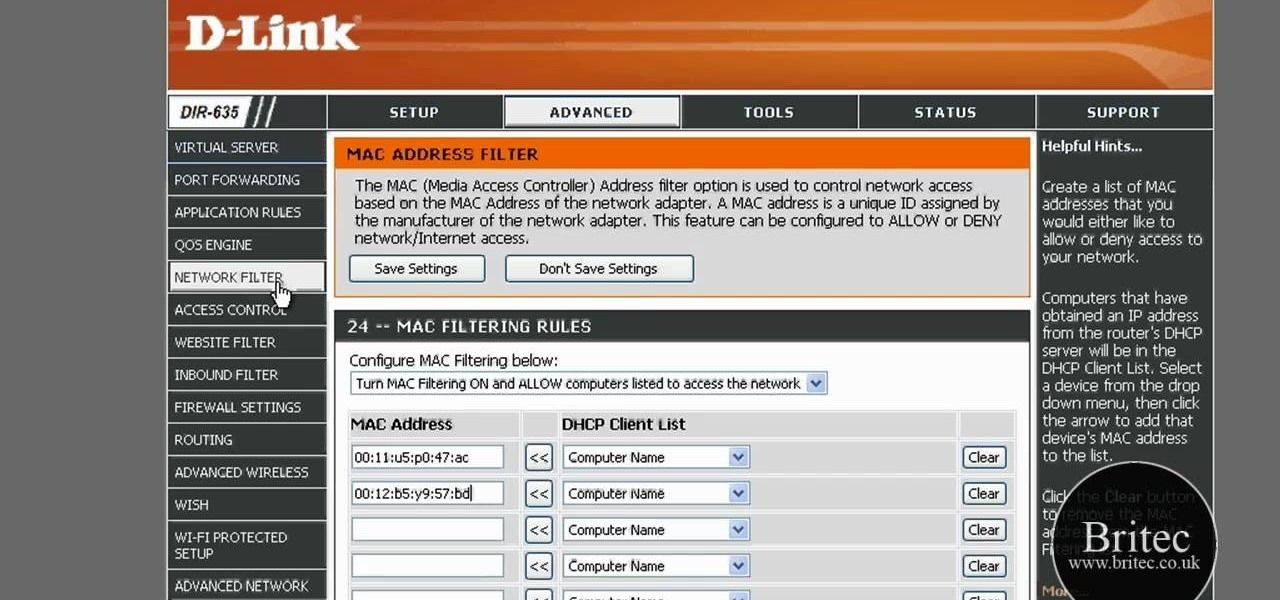
The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Keep Your Word is an innovative and simple Mac application which will let the user keep track of different words - useful for anyone whose area of study gives them a lot of vocabulary words or glossary terms to keep memorized.

If high school students spent as much time on studying as they tend to spend on looking for new ways to cheat, everyone in America would have straight A's. But, cheating is so much more fun than studying, isn't it?

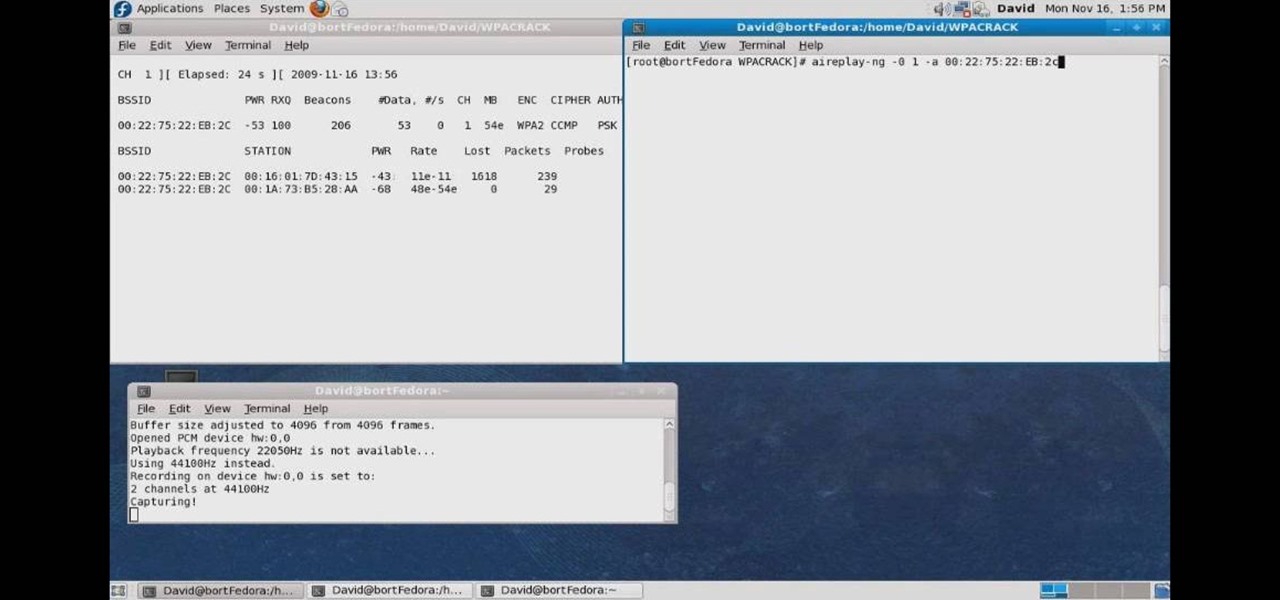
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...

This video shows you the method to find if someone else is using your Internet connection. There are two methods for this. The first method involves opening the start menu and click on 'Run'. Type cmd in the text box which opens as a result of clicking on 'Run'. Type NET VIEW at the command prompt. This will show all people using your network. The second method involves going to Start menu. Go to Connect to and Show all connections. Click on My network places. Click on 'View workgroup compute...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

Research group OpenAI, a research institute co-founded by Tesla CEO Elon Musk, says it is possible to trick driverless cars' neural networks into mistaking images for something else.

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

Learn two quick study habits that will help increase your grades on tests and exams.

Today's word is "pause". This is both a noun and a verb. As a verb, it means to stop an action temporarily.

Law and business are frequently connected more closely than many are comfortable with. Thus, writing business case studies is a big part of legal life in law school and when working at a firm. Watch this video to learn how to write a great business case study.

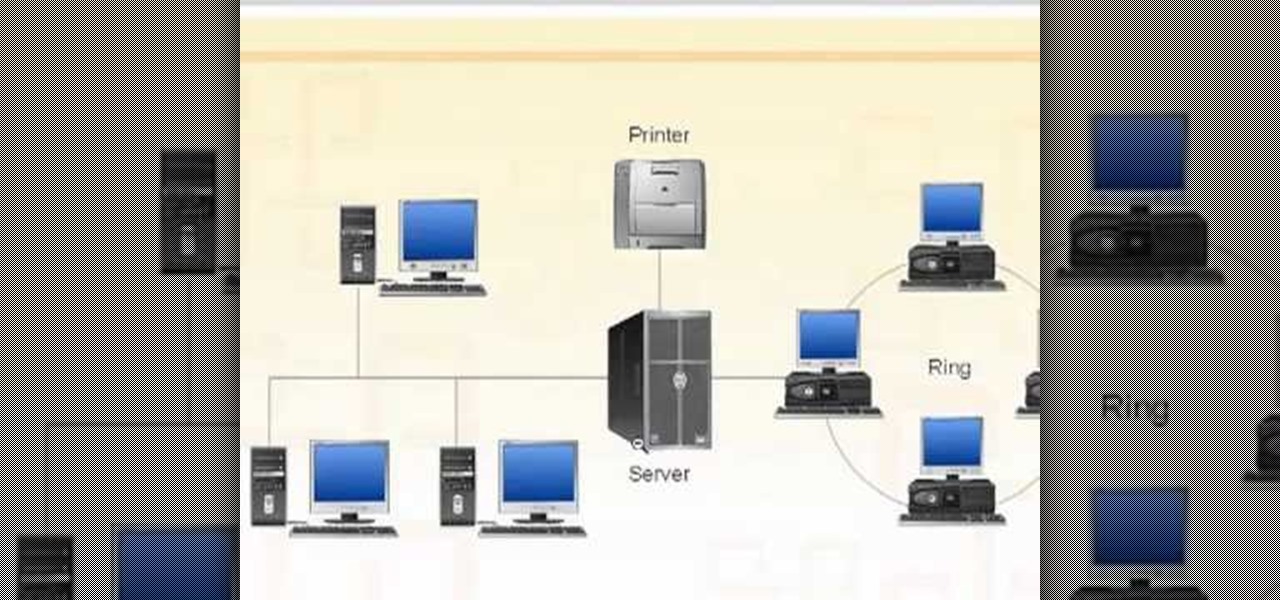
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

If you want to connect your Mac notebook or desktop to a wireless network, you'll need to set up the wifi connection on your computer first. Take a look at this walkthrough to find out how to find and connect to available wireless networks in OS X. This is a great skill to know if you own an Apple laptop and need to connect to the Wi-Fi networks at different locations.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.