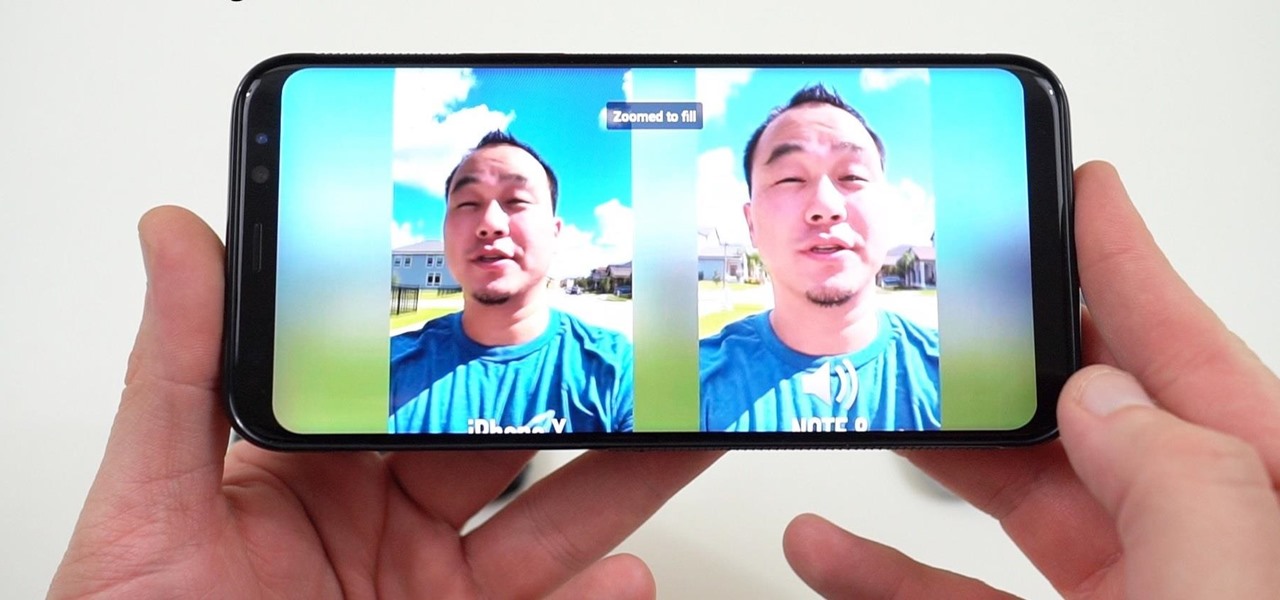
Google launched the Pixel 2 XL with a unique pinch-to-zoom feature in the YouTube app. The feature is pretty basic, allowing users to expand the video to full-screen on devices with 18:9 aspect ratios with a simple pinch gesture. Considering its simplicity, it was strange that the feature was limited to the Pixel 2 XL. Today that exclusivity has ended as the feature is rolling out to the Galaxy S8, Galaxy S8+, Note 8, LG V30, and LG G6.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

Good news for those suffering from the "i" glitch, otherwise known as the "A [?]" bug: Apple has just released an official patch to fix the issue, in the form of a software update named iOS 11.1.1.

For some strange reason, Google left several of the Pixel's best software features disabled by default. One of the more interesting tweaks that fall into this category is a gesture that puts your fingerprint scanner to use after you've unlocked your phone.

We've already seen plenty of shopping potential for mixed reality headsets, from holographic car showrooms to trying on clothes and picking out furniture. Very few of those ideas have been put into actual practice, but we're getting closer, and consulting firm Valorem is making headway. They created HoloTire for the Microsoft HoloLens to demonstrate the advantage of experiencing a product in mixed reality. I'm hard-pressed to think of a more boring product to put on a holographic pedestal tha...

In the wake of Google Glass' failure, we can expect other companies to fill the void in due time. Perhaps unsurprisingly, Snapchat may be one of the first.

Samsung's Galaxy S7 is an incredible piece of technology, but the Skype app that's preinstalled on some models may have some nasty issues, such as video and audio that freezes. Luckily, the fix for these problems is a simple one, although somewhat buried in the phone's Settings app.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

The new iPhone 6 and 6 Plus have bigger displays, and that means more overall screen real estate, something that the new Safari app has taken into account by letting you access desktop versions of mobile websites. Even if you're sporting an older device, you'll still be able to request the desktop version of a site online in the browser.

Seemingly out of nowhere, something strange started happening on my Nexus 7. Every time I restarted my device, the camera application on the far right of my dock kept disappearing on me.

The GoPole, a telescoping extension pole designed specifically for GoPro cameras, allows you to capture unique and up-close 180 degree POV shots of your most awesome adventures. This tool is especially great for extreme sports like skateboarding, skydiving, surfing and snowboarding—all sports that are hands-free and allow you to take pictures without much problem.

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.

Cheetos fingers is defined as the unpleasant (but mostly pleasant), oddly-colored residue left on the thumb, index finger, and middle finger after ravenously eating through a bag of—you guessed it—Cheetos. It can usually be cleaned up by licking your fingers (my favorite) or washing your hands (boooooo). For the folks who enjoy the latter, Cheetos fingers are an annoyance. As someone who enjoys this idiosyncrasy, I've never quite understood the disgust in getting your fingers all cheesed up.

One of the most popular (but smallest) maps in the first Call of Duty: Black Ops was Nuketown. The tiny map allowed for maximum death tolls, making it an awesome map to play (and die) on. In the latest Call of Duty: Black Ops 2, that map returns in the form of Nuketown 2025, a futuristic version of the same level. It was available for free on November 13th to anyone who pre-ordered the game, purchased a launch copy, or purchased the Hardened or Care Package special editions of the game, thoug...

Anyone who does a lot of photography knows that the right exposure can make all the difference in the world. Taking a picture of something in motion requires a long exposure, so if you've ever wondered why your fireworks photos never quite turn out right, your shutter speed could be the key. Photographer David Johnson decided to put a twist on the classic long-exposure fireworks photo. Normally, when people take photos of fireworks displays, they just set a long exposure for somewhere over 3 ...

Enjoy hot chocolate during the stifling summer months by putting it on ice. To make iced hot chocolate, you will need:

Make sure and watch this episode as we tackle another heavily requested effect... making someone look blown in half! Jam packed with cheap special effects, Frisbee fun, and a Test Film guest directed by Maniacal Rage!

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

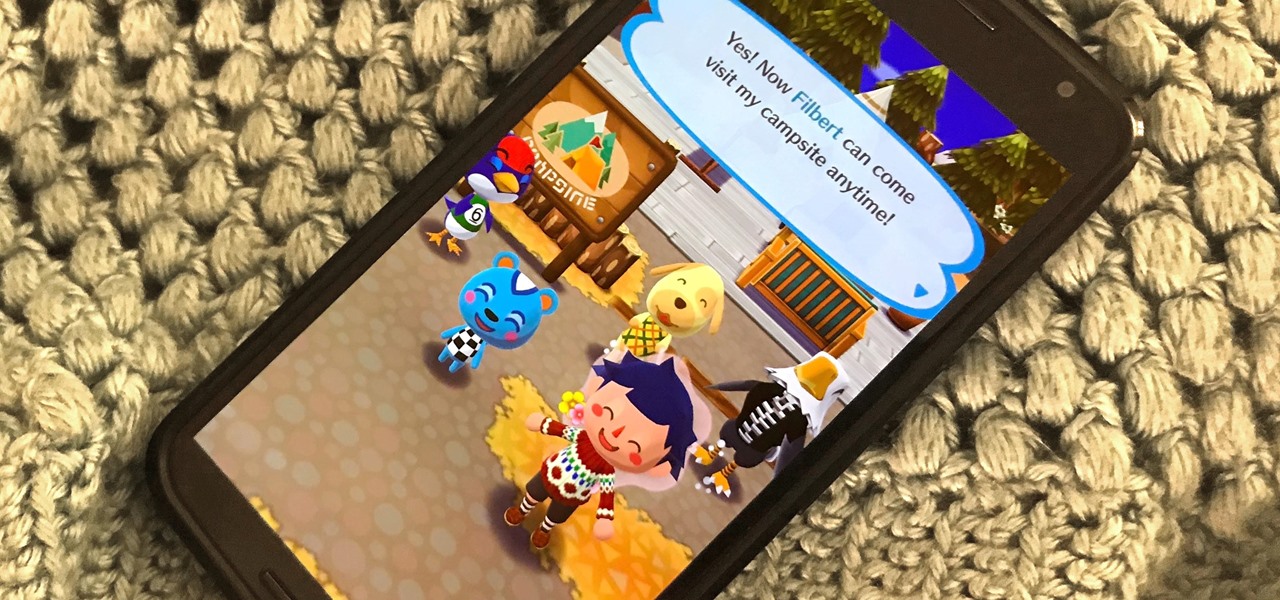
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends.

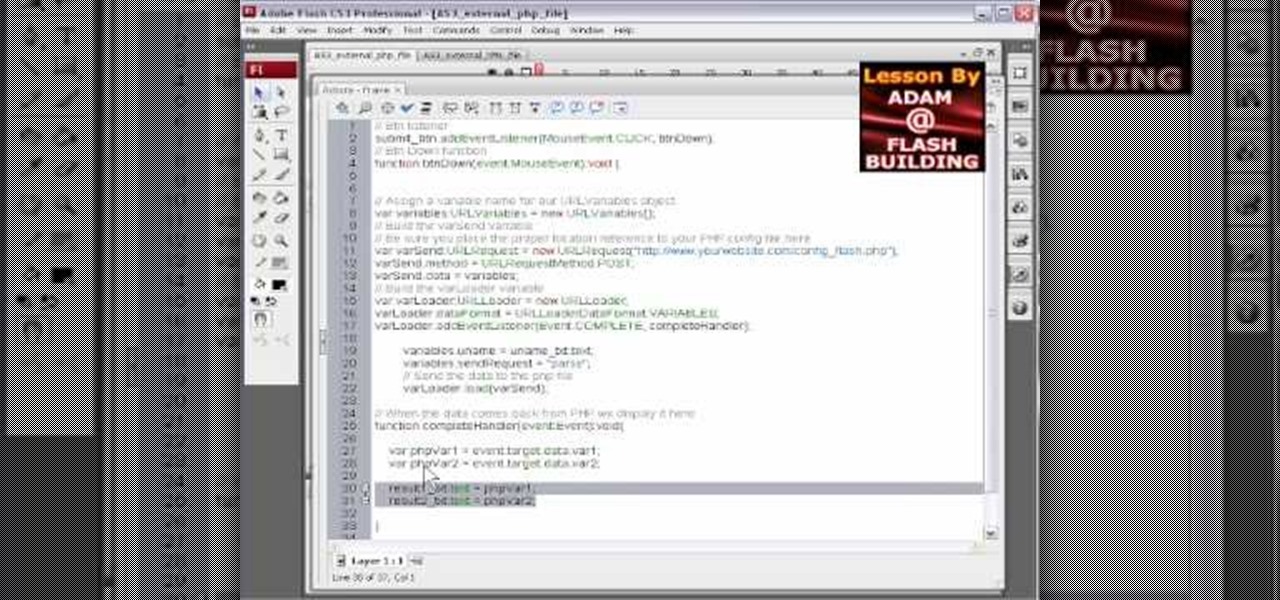
All the files you need are in a free download on DevelopPHP. PHP has to be on a server. It will not run on a local machine. Type your name. There are two variables which show up in the dialog boxes (which are stacked.) You can change the user name. It sets up a URL request and a URL loader and sends some URL variables and are placed into the value of names and pairs. They get posted to the PHP file. Place the URL reference location of where the PHP files are on your server in the line that sa...

Neighbors are a great way to develop your own little community in Cafe World. You can visit your neighbors, sample their special of the day, and leave them gifts.

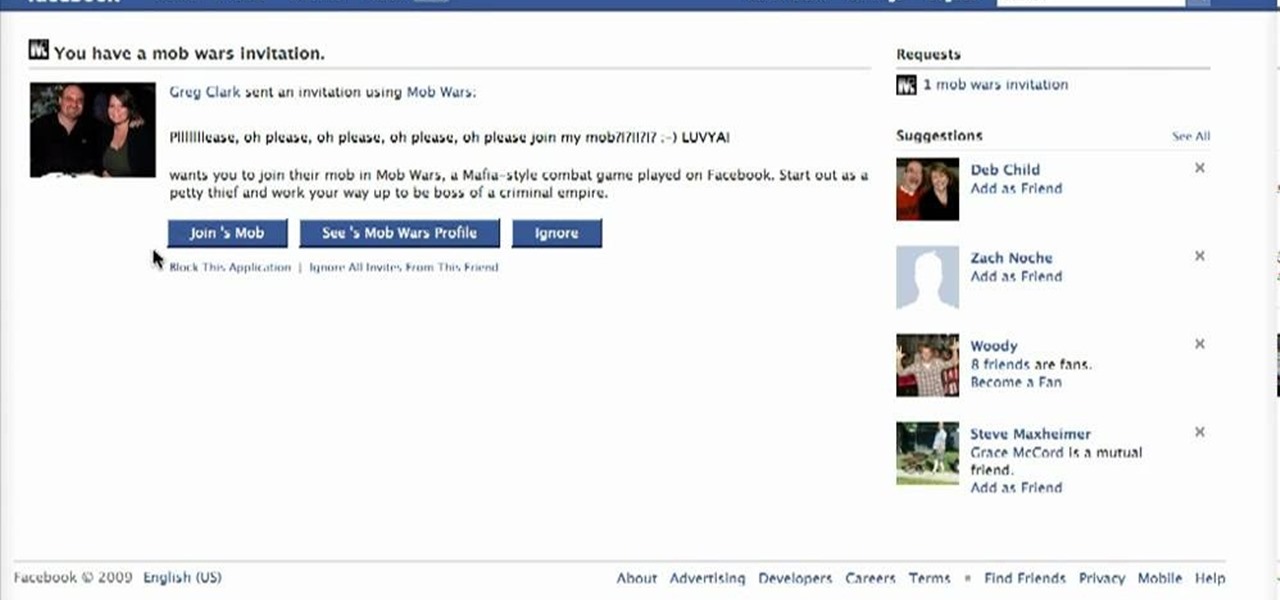
In this how-to video, you will learn how to block third party applications on Facebook. On your main page, you will see requests on the right. Click on the request to check the invitation. You will be presented with a few choices. If you are never planning on accepting an invitation to the application, you can click on the Block Application at the bottom. You can also ignore all invitations from a person by clicking the link with the same name in the same page. This will make using Facebook m...

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

On Monday, with just days left before Christmas, Lowe's dropped a surprise augmented reality treat in everyone's lap: a brand new Magic Leap One app.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

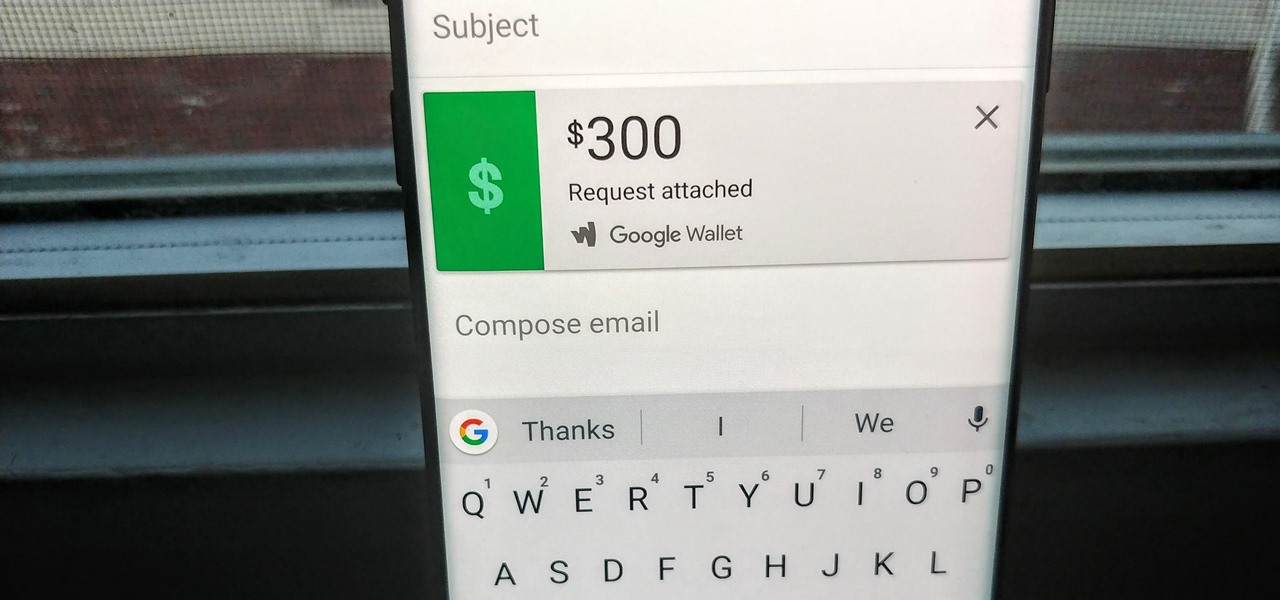
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Maybe you're tired of receiving annoying messages from apps or people on Facebook? Why not block them so you don't have to deal with them ever again? Take a look at this guide for information on how to block online games and apps on Facebook from sending you notifications, requests, or other information. You can even stop people on Facebook from sending you event notifications or posting on your page by blocking them too.

Embed Facebook directly into your Internet Explorer or Mozilla Firefox browser's toolbar using this nifty new add-on directly from the people at Facebook themselves. This addon shows you on the toolbar the number of pokes, friend requests, unread messages and upcoming events that you have, in addition to quick links to various sections of the Facebook site. In this demo video, Patrick from Tekzilla explains the cool new features and details.

Thirteen isn't an unlucky number for this Limbo walkthrough; it's the number of videos in this series, a series which shows you the complete process, through trial and error, life and death, and as least amount of edits as possible.

In this clip, learn how to get amazing amounts of goodies in the mail for free! Kitty, the coupon diva, will show you how to request things like free samples and manufacturer coupons from companies so you can stock pile them and save. Get extra freebies every time you open up your mailbox with these awesome tips.

A cranberry glaze can be used to make your turkey look scrumptously sexy and polished to a Midas glow. The glaze also adds succulent tart flavor to the richness and density of your turkey meat.

If you're a small business operator and AT&T is your carrier, you'll want to take advantage of the AT&T Online Account Management portal for small business customers. This video shows how to request an online registration code (required to register your account), how to use it to register your account, and how to set up your username and password.

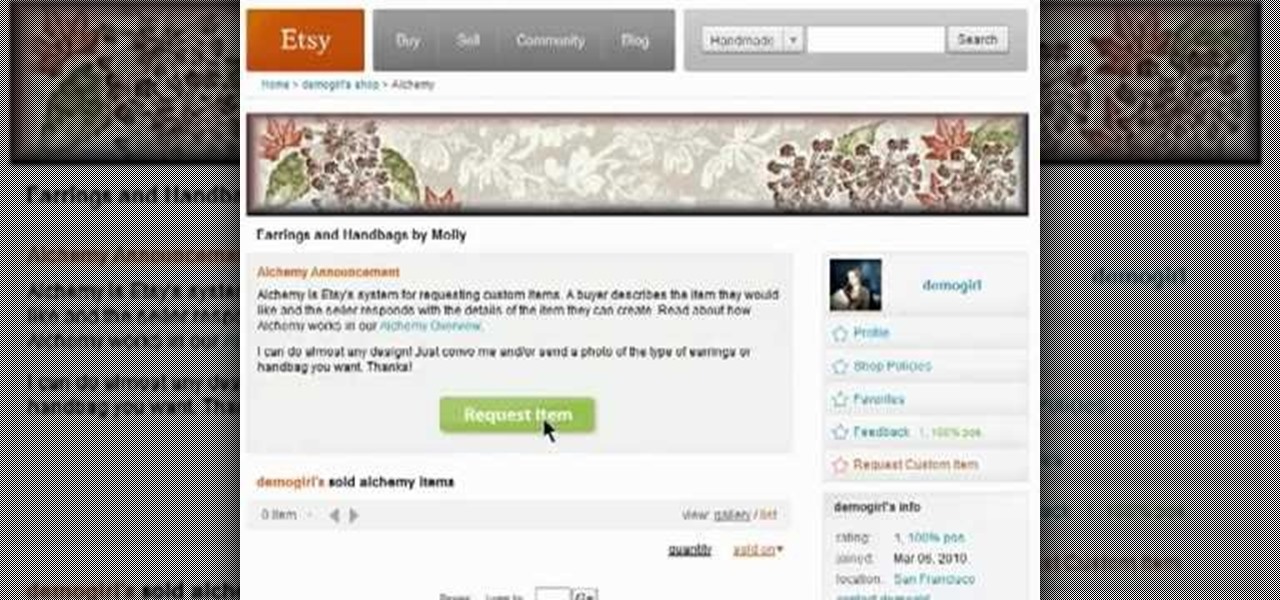
Need some help figuring out how to utilize the Alchemy feature when selling things on Etsy? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using Alchemy yourself, take a look.