Get ready IG influencers, the Instagram promotional world as you know it is about to change. Instagram is one of the top places for influencers to make money with product promotion. So, of course, it is to be expected that these IG dominators would run into their fair share of disasters. Especially since over 90% of celebrities and influencers on Instagram don't follow FTC guidelines.

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

Last week, Next Reality wrote about how the Microsoft HoloLens team is partnering with thyssenkrupp. Their mission? To bring mixed reality to the workplace. Now, Microsoft has just confirmed in a blog post that the HoloLens has passed the basic impact tests for protective eyewear in North America and Europe.

It's Monday, and what's a Monday at Gadget Hacks without a new leak to ponder over? Thanks to known leaker Benjamin Geskin, we have a dummy iPhone 8 without one of its most-anticipated features.

Augmented reality could come in very handy for those of us prone to losing things—namely, our wallets. Pixie Technology, a company from Los Altos, California, has developed a way to locate your lost wallet and keys using AR technology and tracking chips, a platform they call the "Location of Things."

Before the iPhone 7 models were released, there were many rumors pointing to the inclusion of wireless charging, which obviously didn't happen. Now the rumor mill is back at it again for Apple's next smartphone, most likely being called the iPhone 8, and the possibility of wireless charging is more certain this time.

Fish are delicate, flaky, and can be damn tricky to cook; more often than not, you end up with a hard, dry block of flesh that makes your taste buds sad. And the best ways to cook fish that you know of—c'mon, who doesn't love a fried fish—take way too much effort for you to bother with on a weeknight. Or maybe you're looking for a healthier way to enjoy fish that doesn't require batter or frying at all.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.

Being able to customize the look and feel of your device is the main reason a lot of folks choose Android over iOS. And perhaps the single biggest way to visually overhaul your phone or tablet's UI is to apply an icon pack, which can liven up your home screen with bright colors or make things look a bit more classy with a sleek, minimalist style, for instance.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, StandBy, App Store, Lock Screen wallpapers, Apple Wallet, and more.

The draw of wireless earbuds is convenience, and many still offer the same sound performance as their wired counterparts. The difficult part is finding a pair that will stay in your ear reliably, work when you need them, and give you the best audio quality.

For a long time, digital creators have had to make do with clumsy mice that don't capture the minute movements they need to do their best work. Unless you were willing to spend potentially over $600 for a drawing tablet with a high-resolution screen, you were stuck with a mouse. Creators who work with audio or video were just out of luck, period.

Every state has begun reopening in some capacity. While there are important steps for everyone to get back to work and begin socializing, precautions will be in place for some time, especially with an expected second wave coming this fall. The virus is not over.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

If you or someone you're shopping for has a newer iPhone model or an Android smartphone like the Galaxy Note 9 or Pixel 3, they come with wireless charging capabilities. Problem is, they don't come with wireless chargers. But there's no better time to snag one than on Black Friday, and we've found the best deals out there for 2018's holiday season.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

Coming up at the end of May is the world's largest conference and expo dedicated to all things augmented and virtual reality, the Augmented World Expo, more commonly known just as AWE. And this year, a few of us from NextReality are going to be there.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

I used to brag that I could make a swan out of an apple, but chicks don't dig swans—they dig roses. So now I'm going to brag about making apple roses, because you would, too, if you could get them to look like this: Now that's an apple tart that will win the ladies over. (And definitely 100% tastier than the usual bouquet of roses, and 100% less greasy than a bouquet of bacon.)

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Fried food is the best. That's not an opinion; that's a fact, Jack. And while fried standards like wings, French fries, and onion rings are all stellar, there's no way you should stop there.

Everyone has the same five spirits in their bar: vodka, rum, whiskey, tequila, and gin. They're all great, but every so often the mood strikes to try a cocktail with a little something different. We'd like you to meet three spirits from South America that would make a welcome addition to your next cocktail party.

If you're a sushi lover but not an expert sushi maker, you can still enjoy the flavors of sushi rolls at home with these deconstructed sushi dishes.

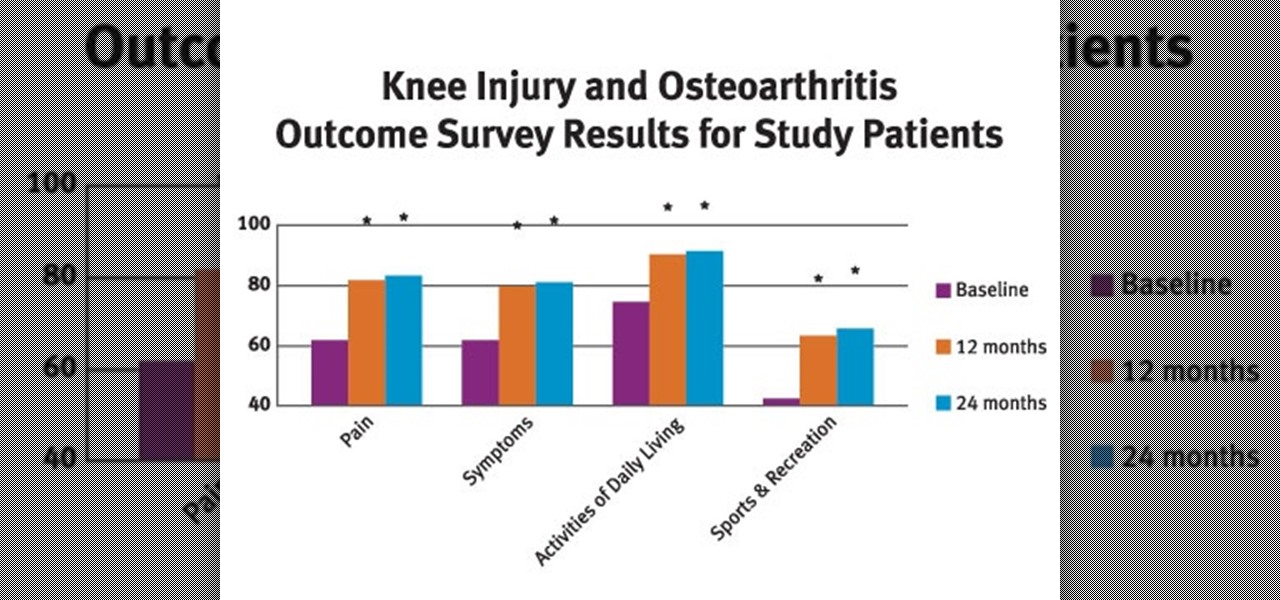
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

Ever since the US Army awarded Microsoft's HoloLens a $480 million contract, the battle for enterprise augmented reality has heated up in earnest.

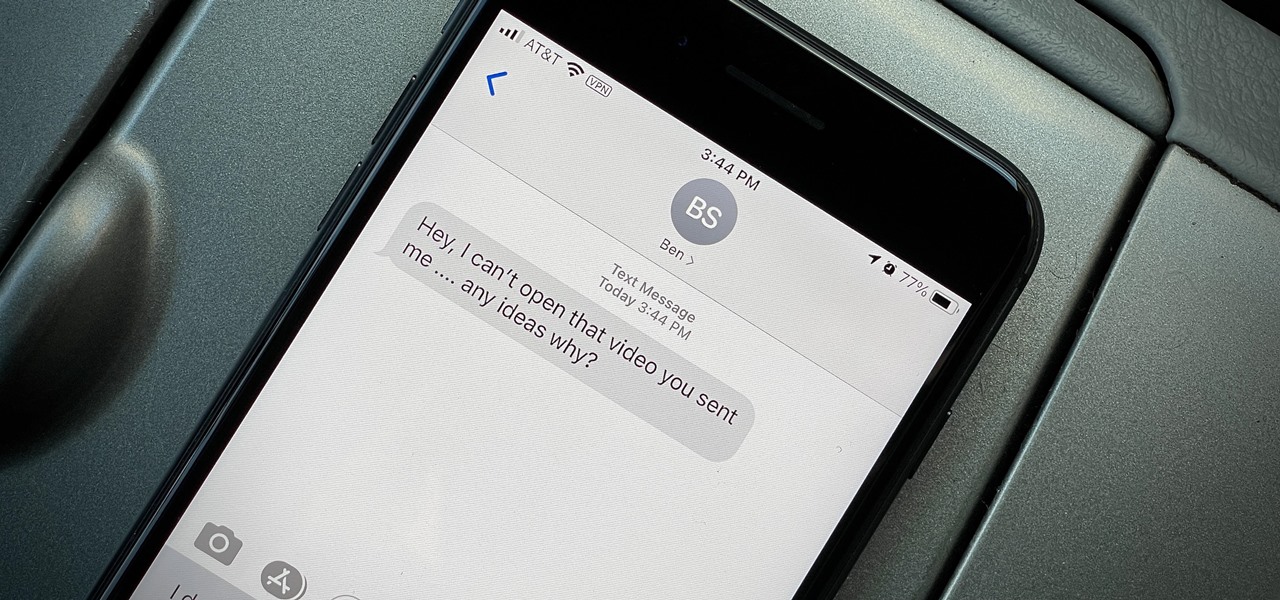
You take a photo or video, send it to a friend, and they say, "Hey, I can't open this." More often than not, your friend won't be using an iPhone, iPad, iPod touch, or Mac. Instead, they're likely trying to open the file with a non-Apple device. But this problem can be avoided if you know what setting to change.

Frequent readers of Null Byte are no strangers to the basic elements of app and web development. Whether you're a seasoned programmer who works extensively on front-end designs or an aspiring app-builder who's working on expanding your portfolio, you're likely familiar with at least a few go-to programming languages and platforms that are popular within your field.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.