There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

For so many of us, bakeware is bakeware. As long as it's oven safe and able to tolerate the high heat, it's fine to bake in, right? Wrong!

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

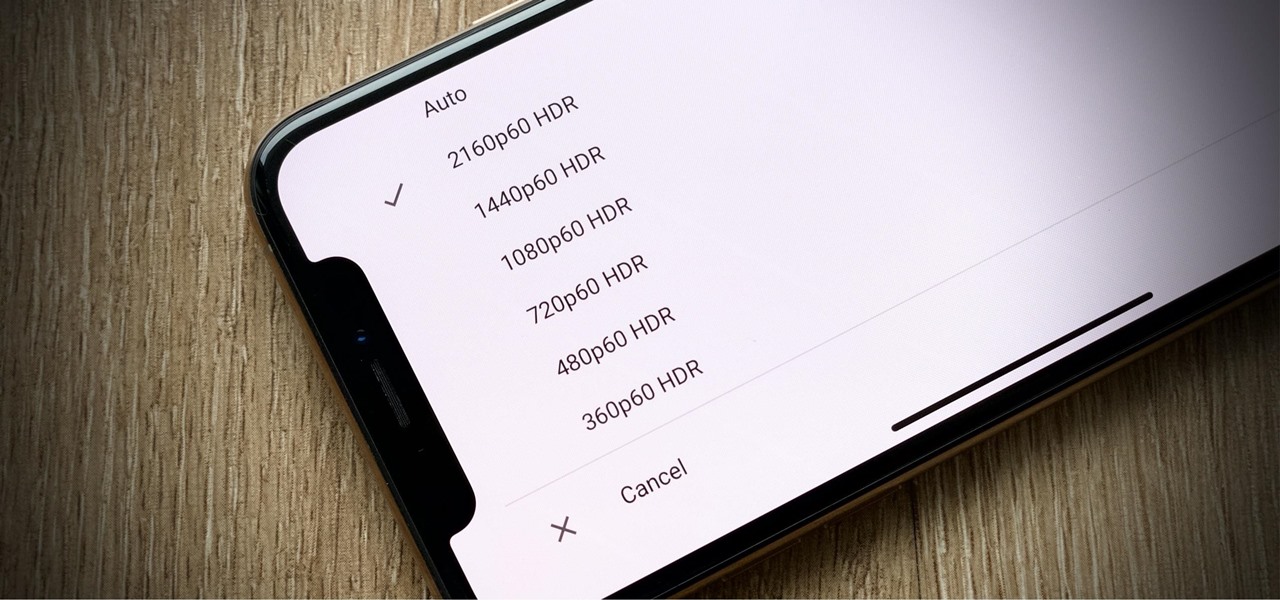
How frustrating is it to watch YouTube in 4K on your computer, Roku, or Amazon Fire Stick, only to settle for measly 1080p on your brand-new iPhone? For years, those of us on iOS had no option for streaming YouTube videos in full resolution, but these days, things are finally different.

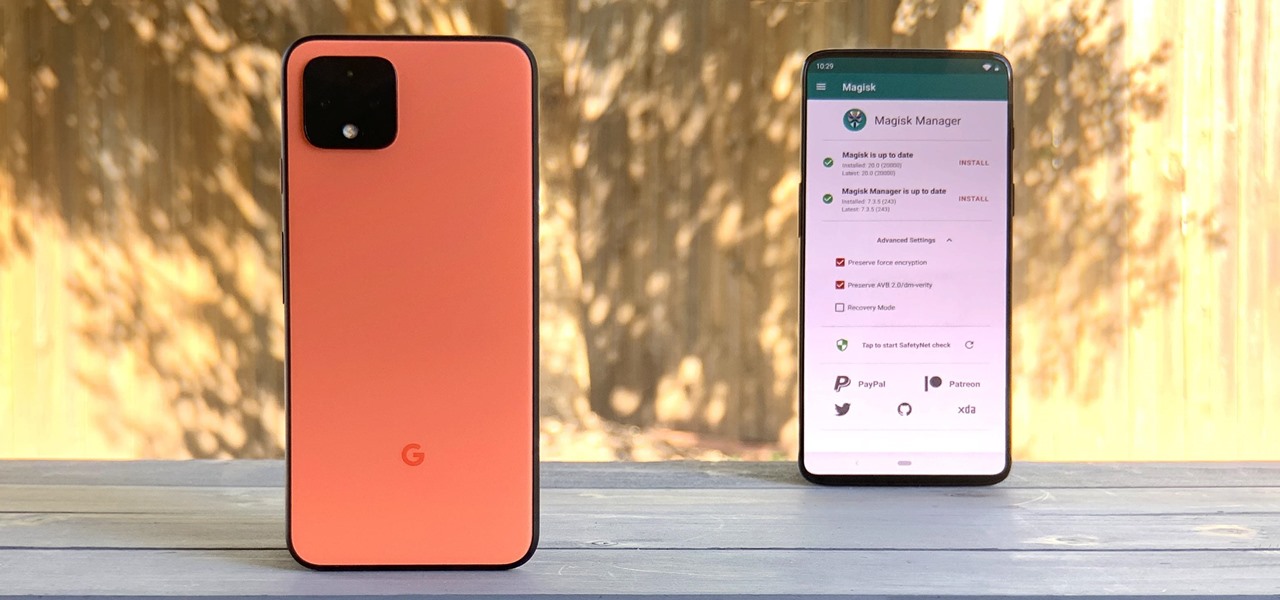
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

Gaming on smartphones has grown considerably since the days of The Impossible Game and original Temple Run. Mobile games can be just as in-depth as console and PC video games, but some of those require external controllers for the best gameplay possible. One controller you can use is the PlayStation 5's DualSense wireless controller, and it pairs nicely with most Android devices.'

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

The Camera app on your iPhone includes new features with the iOS 17 update that will help you take better photos and more impressive videos, but there are a lot of cool new things available that you might not see right away.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

Obesity has ballooned into a worldwide epidemic. The World Health Organization estimates that 2.3 billion adults will be overweight and 700 million will be obese by 2015. Over 20 million children are overweight today. The reasons for these distressing figures are common knowledge: The international switch to high sugar, high fat, low nutrient processed junk foods prompted by global fast food chains and their advertising; the increasingly sedentary nature of jobs; children playing video games ...

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

In this article, I'll show you how to build a simplistic circuit to generate negative ions. Negative ions have been known to contribute to fresher air, happier mood, and general health benefits. However, they also look amazing in the dark (check out the photos below, purple plasma is amazing!). And if all else fails, they make a cool nightlight. If you've ever been around a Tesla coil, cathode ray tube TV or sometimes even on a trampoline, you've probably noticed that smell; the smell of "sta...

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.