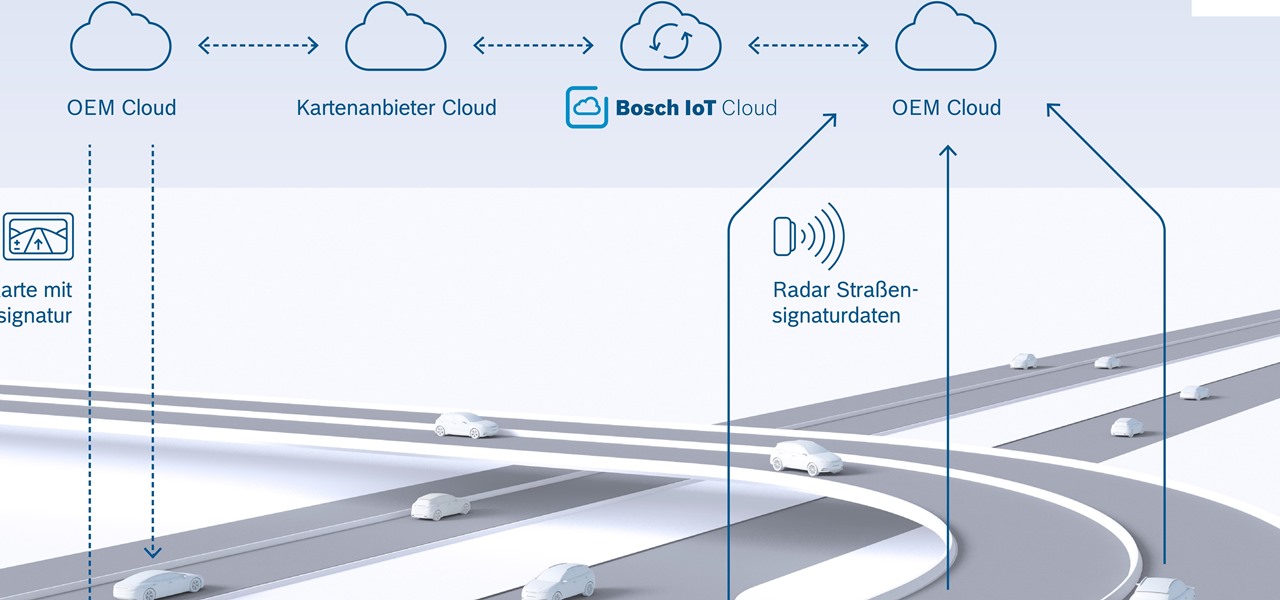
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

You share your innermost feelings with it on a daily basis. Why, then, settle for something drab, prefab and impersonal? With this handy how-to, you'll learn how make a custom fabric-covered hardbound journal.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Every girl dreams of achieving glamour with ease like the fabulous Taylor Swift. Her signature red lipstick makeup look helps her to stand out from the crowd. Watch this video to learn how you can get Taylor Swift's red lipstick look without looking like a clown.

While it's true that all of the Victoria's Secret Angels were born genetically blessed (and somehow big-bossomed and skinny all at once), at the annual Victoria's Secret Fashion Show even they require a football team of makeup artists and hairstylists.

If you haven't already seen her face plastered in front of every Victoria's Secret store and catalog cover, then you certainly will tonight, when the annual Victoria's Secret fashion show airs. Marisa Miller is one of Victoria's Secret's veteran supermodels. The lady has killer curves, bombshell hair we can only dream of having, and beautiful, sunkissed skin.

Loose waves are the hair signature/calling card of summertime beauty, so indulge yourself in this sex goddess inspired look by watching this tutorial.

How to do the Lebron James signature move fake & pass is as easy as a couple of steps. LB23 is a basketball / NBA legend and he's only 24 years old. He is the next Michael Jordan! Watch his Signature Move from Nike.

Watch this piano tutorial video to learn how to play "In the End" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "In the End" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Faint" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "Faint" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Haruka Kanta," the second Naruto opening, on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play "Haruka Kanta" from Naruto on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Breaking the Habit" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "Breaking the Habit" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "From the Inside" by Linkin Park on the piano. The instructions include the scale, key signature, and chord breakdowns. Intermediate pianists will have no trouble learning how to play Linkin Park's "From the Inside" on the piano after watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Wake Me Up Inside/Bring Me to Life" by Evanescence on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play Evanescence's "Wake Me Up Inside" by watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Yesterday" by the Beatles on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play the Beatles' "Yesterday" by watching this helpful how-to video.

Watch this piano tutorial video to learn how to play "Let It Be" by the Beatles on the piano. Instructions include the scale and key signature and chord breakdowns. Beginners and intermediate pianists will be able to learn how to play the Beatles' "Let It Be" by watching this helpful how-to video.

Watch this piano tutorial to learn how to play My Chemical Romance's "Disenchanted" on the piano. Instruction includes key signature and scale, chord breakdown, and melody. Pianists of any level will find this instructional video helpful in learning how to play "Disenchanted" by My Chemical Romance on the piano.

These drink recipes will add a bit of "wow" to your next party. Find four cool cocktails that your guest will love. This how-to video will show you how to mix a Pomepolitan, Green-tea martini, and many more. Shake it up.

In this tutorial, you'll be learning the basics of clipping or masking. And how it can be used to apply effects to a signature. If you're starting off with Photoshop, or completely new to Photoshop, This tutorial will explain how to make a clipping mask.

This lesson covers six odd-time beats that are played in the 5/4 time signature. Unlike most rock drum beats, that are played in 4/4 with four quarter notes per measure, these beats are played with five quarter notes per measure. Watch the included video for step-by-step training on how to count and play these unique beats.

This lesson includes six drum beats that are played in the 7/4 time signature. They are all considered odd-time, due to the fact that they aren't counted like popular 4/4 drum beats. The beats are still counted with quarter notes, but include seven in each measure instead of four. Watch the included video for adddition information.

Are you a beginner or intermediate drummer that would like to learn how to count various time signatures, note values, and sub-divisions? If the answer to either of those questions is yes, you've come to the right place. The video lessons in this section will teach you all the essentials in step-by-step detail!

In this video lesson, you will learn how to count quarter notes within the 4/4 time signature. This will lay out a solid foundation for learning other sub-divisions of time, including: eighth notes, eighth note triplets, sixteenth notes, sixteenth note triplets, and thirty second notes.

We've seen how to digitally sign PDFs in Acrobat before. However, in this tutorial not only do Terry White show you how to do it in Acrobat 8 Professional, but he also shows you how to take your signature to the next level with your own picture.

A specialty among select Miami bars, Purple Rain is a sweet martini with a layering technique that gives the drink its signature purple glow. You will need vodka, wild berry martini mix, cherry juice, a shaker filled with ice, a spoon for layering effect and a purple orchid to garnish.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Firstly, looking like modern screen siren Eva Mendes requires confidence. Lots of confidence. The stunner has posed nearly nude for Calvin Klein and doesn't flinch at wearing extremely form-fitting, low cut frocks at red carpet events. Plus, the girl loves having fun with her makeup.

For those not in the know, the Perrier ad campaign by Dita Von Teese is a sexy commercial that Von Teese did for the sparkling tonic water company that includes naughty burlesque dancing. In the commercial, Von Teese sports her signature pinup makeup look with false lashes, liquid cat eyeliner, and of course buxom red lips.

Kim Kardashian is one celebrity who knows how to work what she's got (and it doesn't hurt that she's utterly gorgeous, either). With darker, bronzy skin, perfect, sharp cheekbones, and gorgeous, huge eyes, she always chooses to highlight these features when she's on the red carpet.

http://www.etsy.com/storque/how-to/how-tuesdays-spooky-shadow-puppets-by-crankbunny-2827/

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

Coco Chanel once said that fashion fades but style is eternal. So even with Lady Gaga's new single "Born This Way" catching fire and Britney Spears in the midst of her pop comeback, time and time again we still go back to perennial favorites like Miles Davis, Frank Sinatra, and Charlie Brown tunes.

New mommy Adriana Lima is gorgeous in a way only Victoria's Secret models can be. Tall, statuesque, and with beautiful light blue eyes that contrast with her dark brown hair, she's really quite a picture of perfection.

Remember Pamela Anderson's "Baywatch" days? Yeah, Pamela Anderson is a little washed up now, but back in the day there was no one hotter in a one-piece swimsuit. And whether she was rescuing a very thankful (and probably turned on) teenage boy from the water or simply hitting up the grocery store, she always wore her signature smoky eye with buxomlips.

If you think about it, beauty of all beauties Angelina Jolie doesn't actually wear that many beauty products. Even when she's rubbing elbows with George Clooney at the Cannes Film Festival she's usually going with nothing more than clean, flawless skin, cat eyeliner, and pale lips.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

Whether you love Barbie or hate her plastic Mattel guts, you have to admit the girl's pretty. And if you were a little girl growing up in the U.S. you more likely than not had a Barbie to play with.

Modern bombshell Scarlett Johannson literally worked her butt off to get into shape for the role of Black Widow in "Iron Man 2." While always lean, Johannson whittled down her famous curves, losing about ten pounds (a major difference for a woman that small) and gaining a lot of lean muscle.

"Clockwork Orange," Stanley Kubrick's oddball crime film, features several teenage characters whose intentions are...questionable, to say the least. After all, Alex DeLarge, the main character of the story, sociopathically rapes a few women in his youth, runs around with a gang, and takes drugs.