When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

In this clip, you'll learn how to quickly set a security pattern on an LG Droid Ally Google Android smartphone. For more information, including a complete demonstration and detailed, step-by-step instructions, and to get started setting up your own security secreen, watch this helpful video guide.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

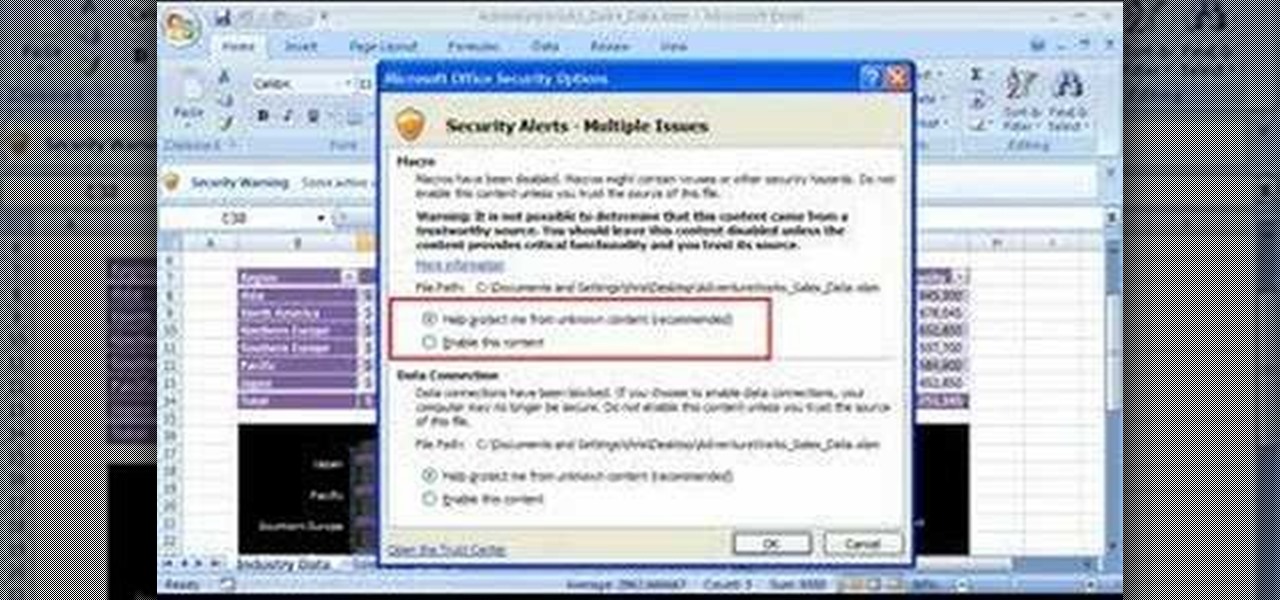
Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

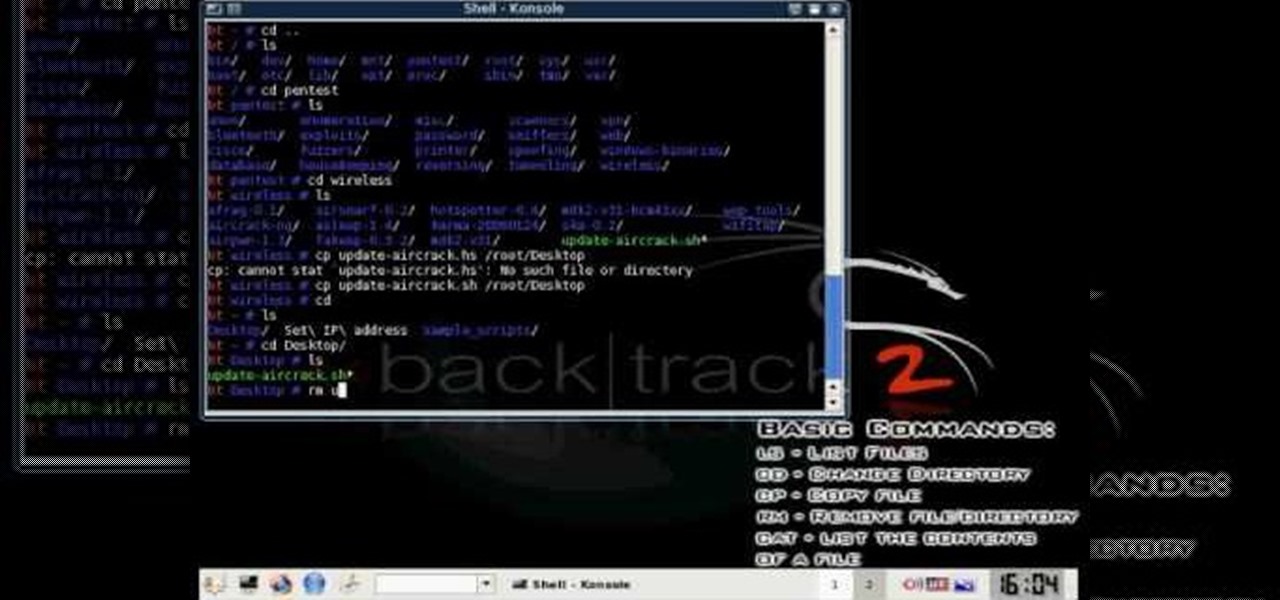
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

In this tutorial, we learn how to sign up and set up a Twitter account. Twitter is a social networking site where you have 140 characters to tell your friends how you are feeling, what you are doing, or talk to them! You can follow people and other people can follow you. You can choose who follows you, which will create and strengthen online relationships. You can even get business referrals from this! Just by getting yourself out there, this is a great tool. To sign up, you will simply go to...

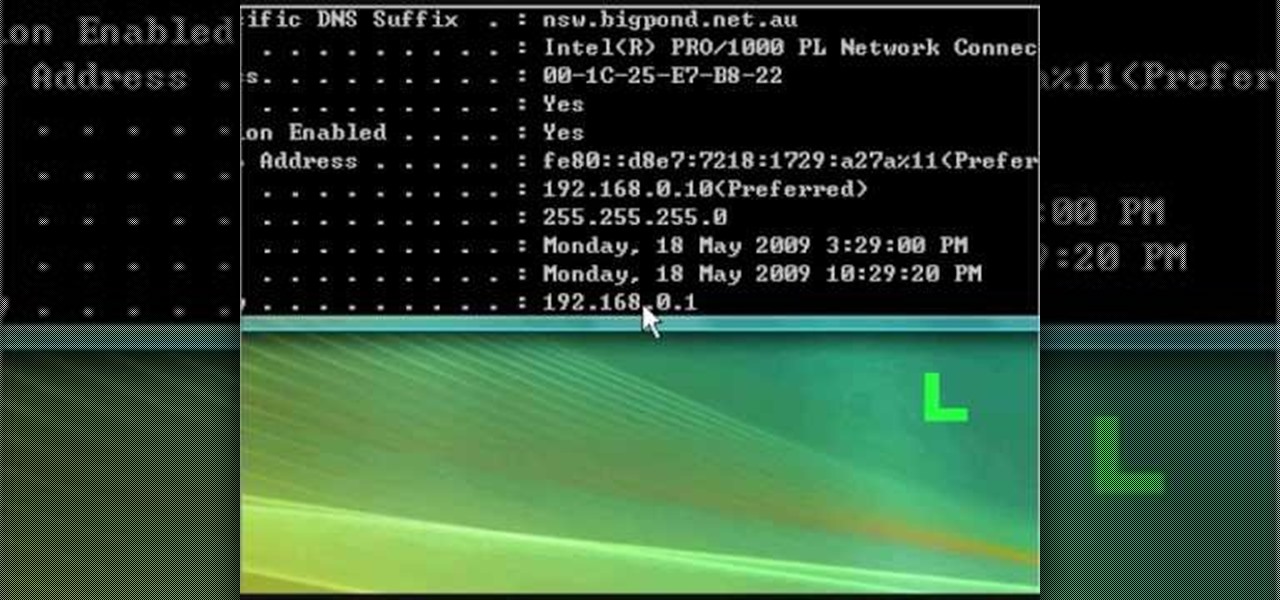
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

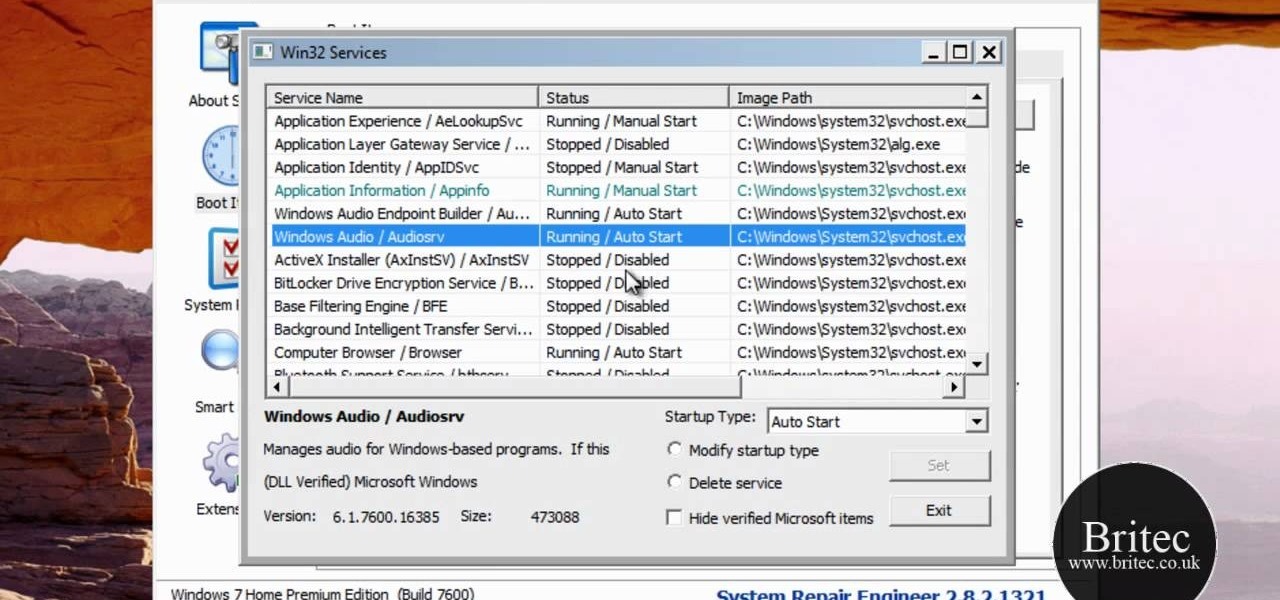
Your Windows computer may be experiencing some issues, and those issues may be a direct result of computer viruses and malicious software from the internet. One of the simplest ways to find these issues and repair them is by using a freeware program called System Repair Engineer (SREng). But that's not all it can do… check out the video to see a basic overview for using SREng.

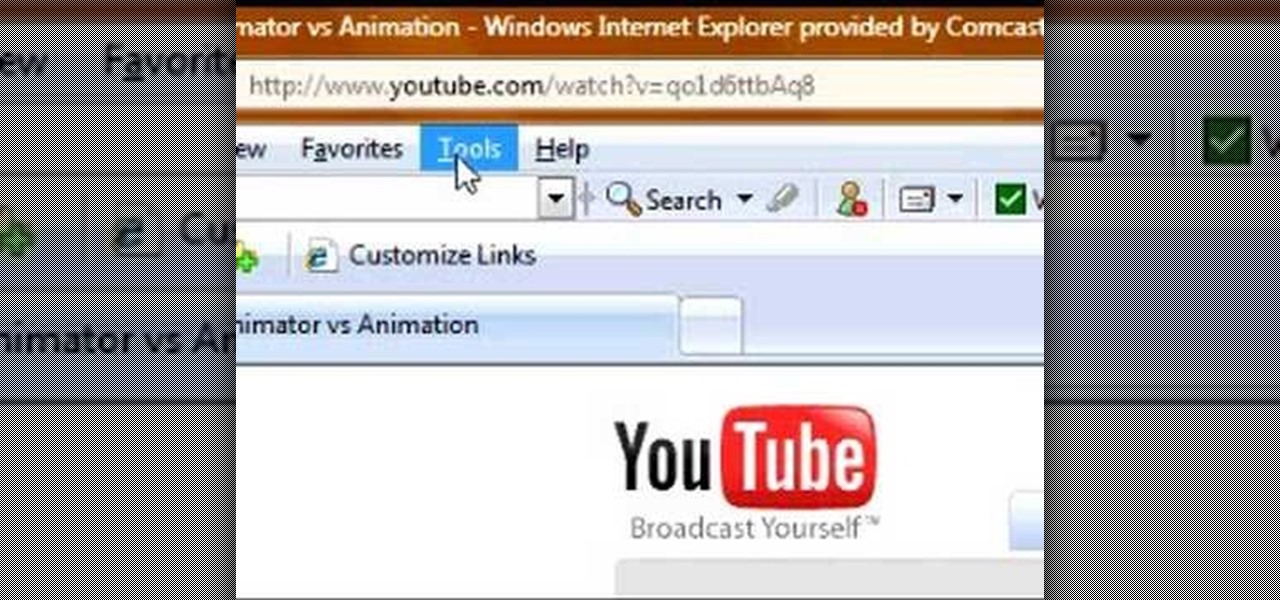
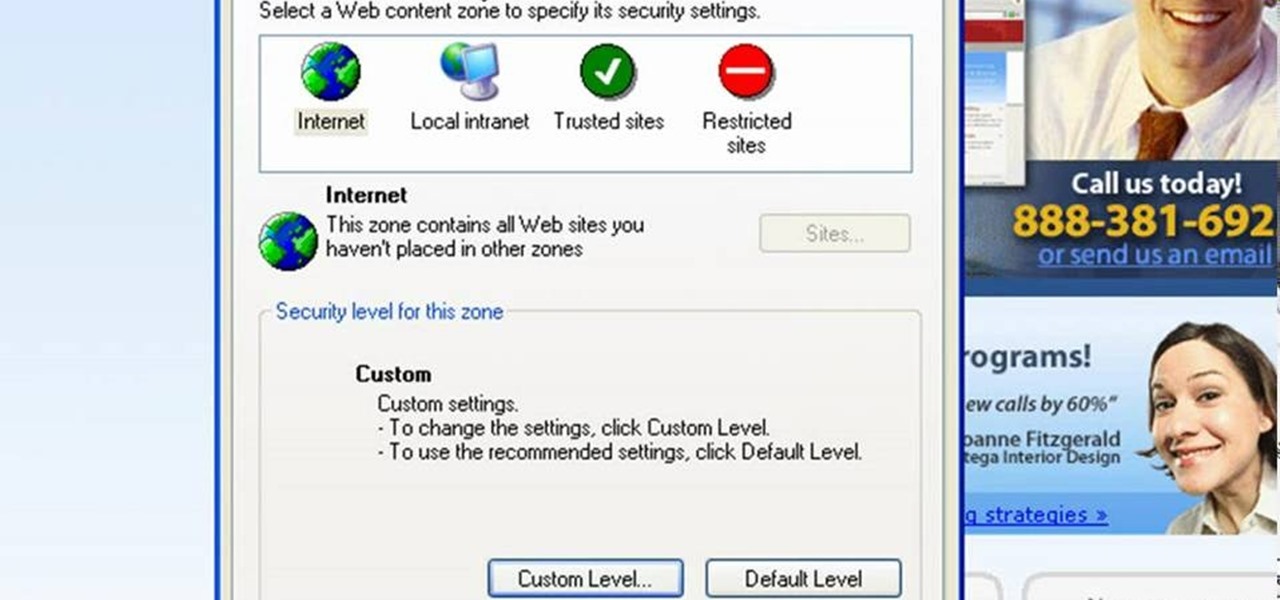
In this video tutorial, viewers learn how to enable JavaScript and update Flash in Internet Explorer. To update the Flash player, go to the link provided in the description and install it. To update JavaScript, click on Tools and select Internet Options. Then click on the Security tab and click on the Custom Level button. Now scroll down the list and find Active Scripting Option. Check Enable and click OK. When the Prompt window pops up, click Yes and click OK in the Internet Options window. ...

This video will show you how to enable JavaScript, accept cookies, and allow pop ups in Microsoft Explorer. The first thing you will need to do is to go to tools on the menu bar, then choose options, and choose the security tab of the new window that will pop up. To enable JavaScript click custom level, scroll all the way down until you see the scripting section, make sure that all three radio buttons are set to enabled, and finally click ok. To enable cookies, go to the privacy tab and make ...

Learn how to fix or recover a corrupt windows registry following the steps outlined in this video tutorial. To begin, take the hard drive out of the computer with the corrupted registry and connect to another computer. To find the files you need to replace go to Start and My Computer. Look for the hard drive that you just added and double click on it. Go to Tools and Folder Options. On the View tab under Advanced Settings click Show Hidden Files and Folders, and unclick Hide Protected Operati...

This video will allow you to view your saved usernames and passwords in Firefox. This may be useful for users in case you forget what your user names or passwords are for different sites and would like an easy way to find them. Under the Firefox toolbar, go to "Tools" and then "Options" in order to get a popup which will allow you to view different aspects you can change in Firefox. Go to the security tab and then click on the button which says "Saved Passwords" in order to view all your save...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

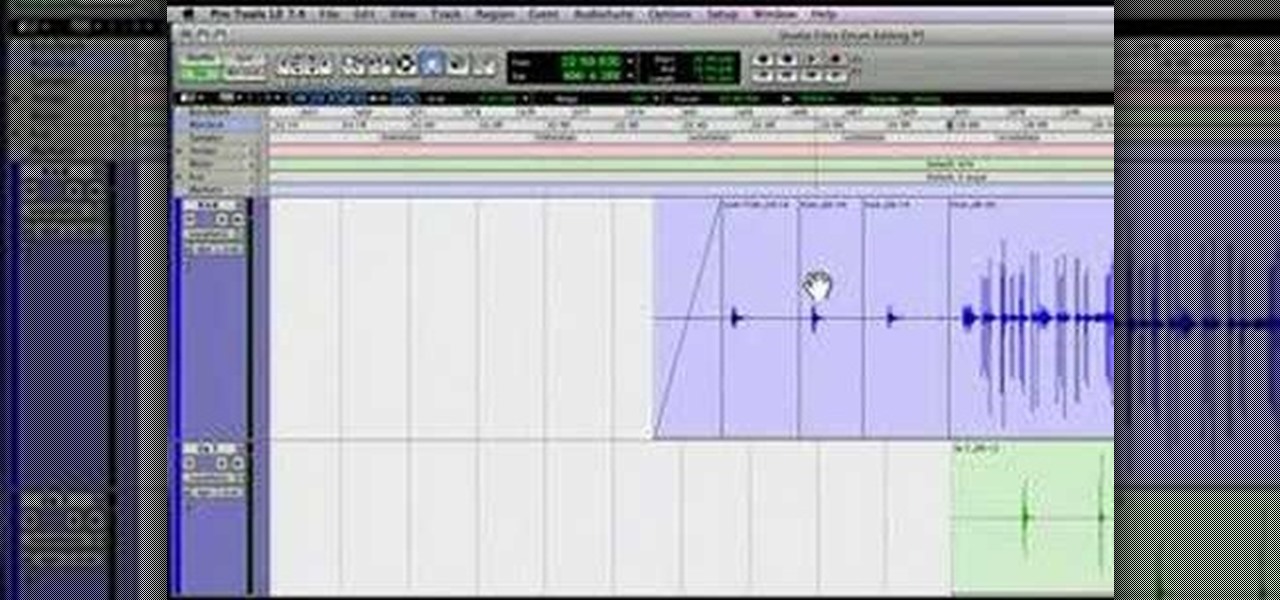
This audio editing software tutorial will show you how to use all the different editing tools in Pro Tools. This includes the zoom, edge, selector, grabber, scrubber, and pencil tools. (Connor Smith also talks about the multiple types of zoom tools, the time compression/expansion and loop tools, and also the object and separation grabber tools). So if you aren't familiar with the editing tools available in Pro Tools, watch this tutorial and get started editing music!

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

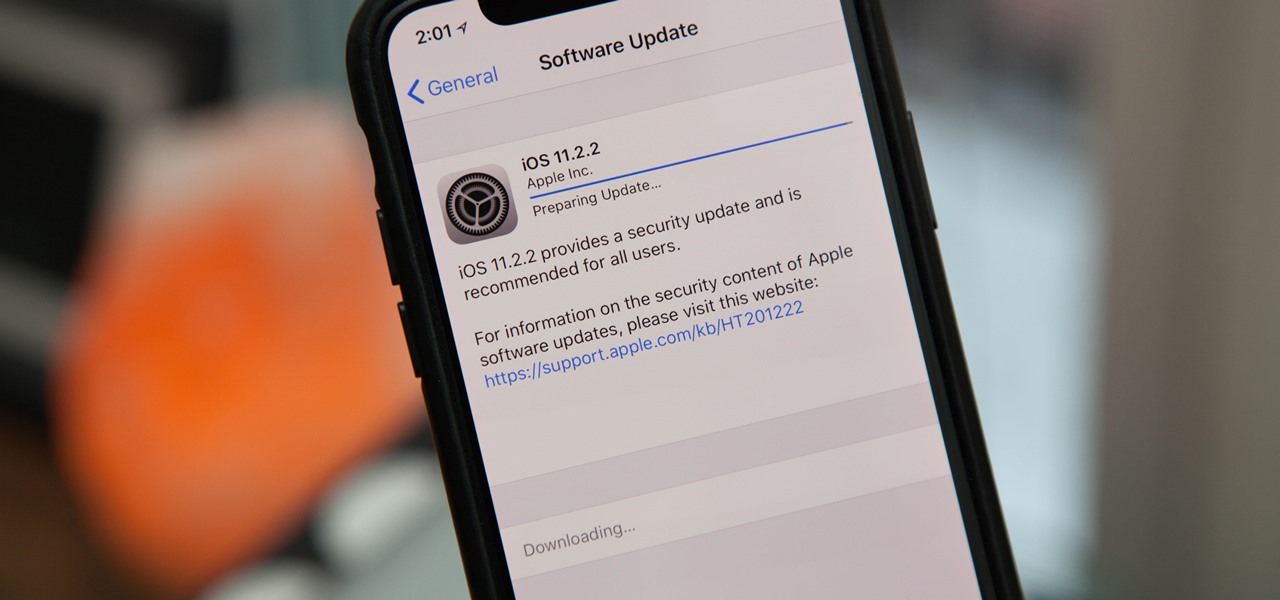
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

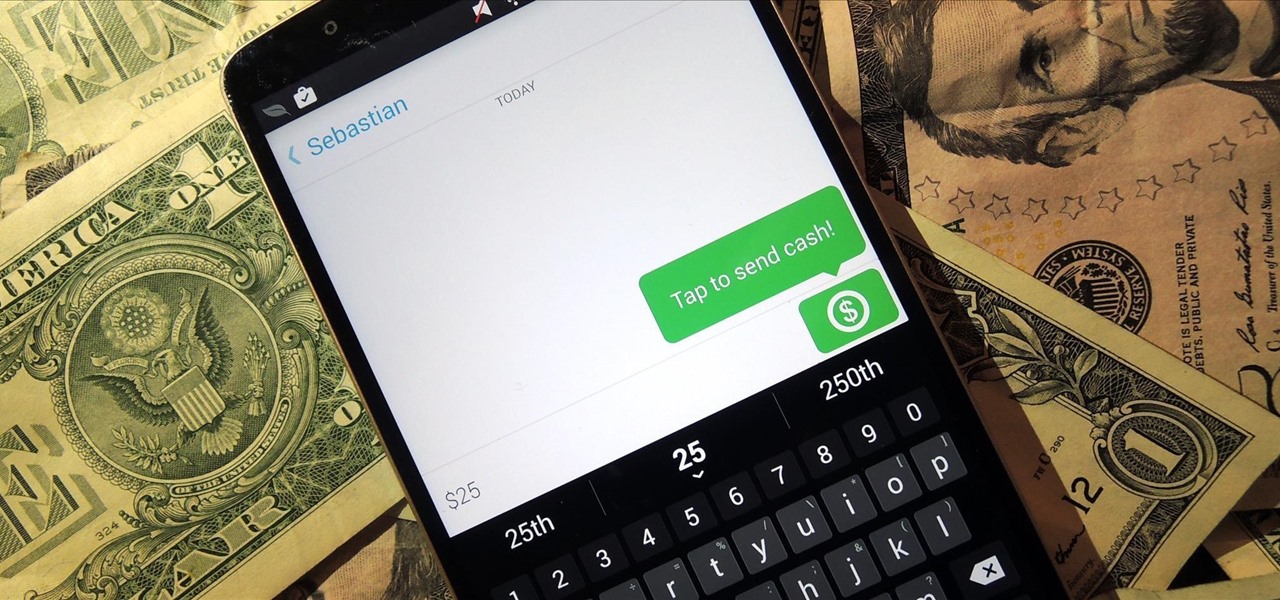
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

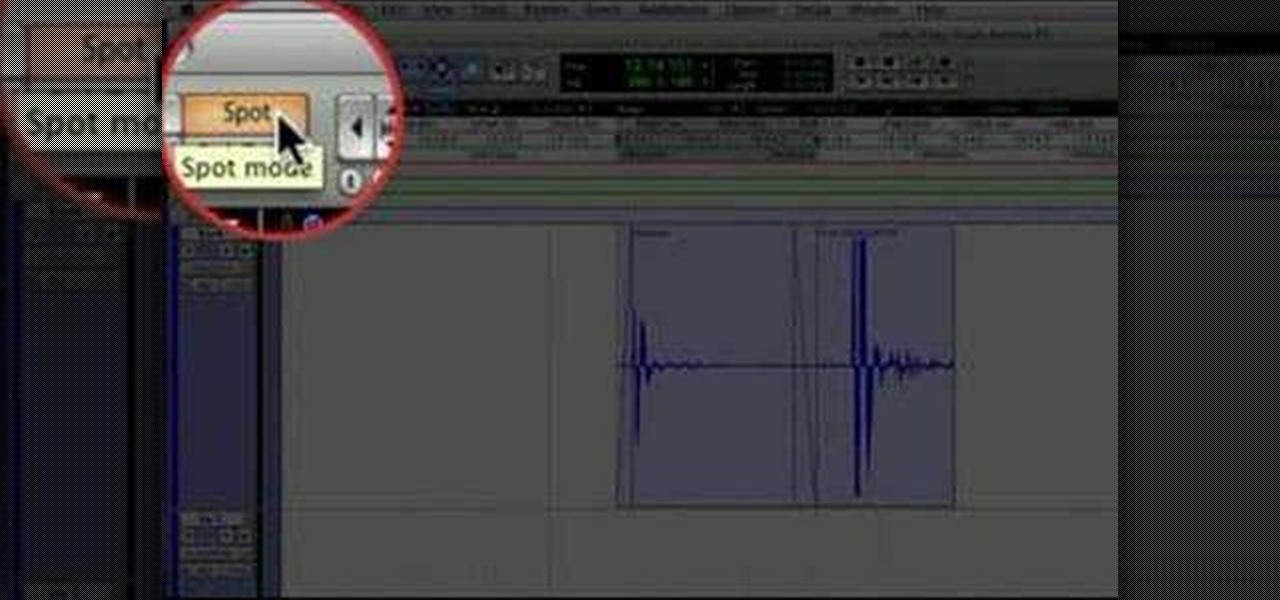
This audio editing software tutorial will show you how to use the smart tool in Pro Tools. Besides showing you the smart tool, Connor Smith will cover the different edit modes (shuffle, spot, slip, grid, and relative grid) available in Pro Tools.

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

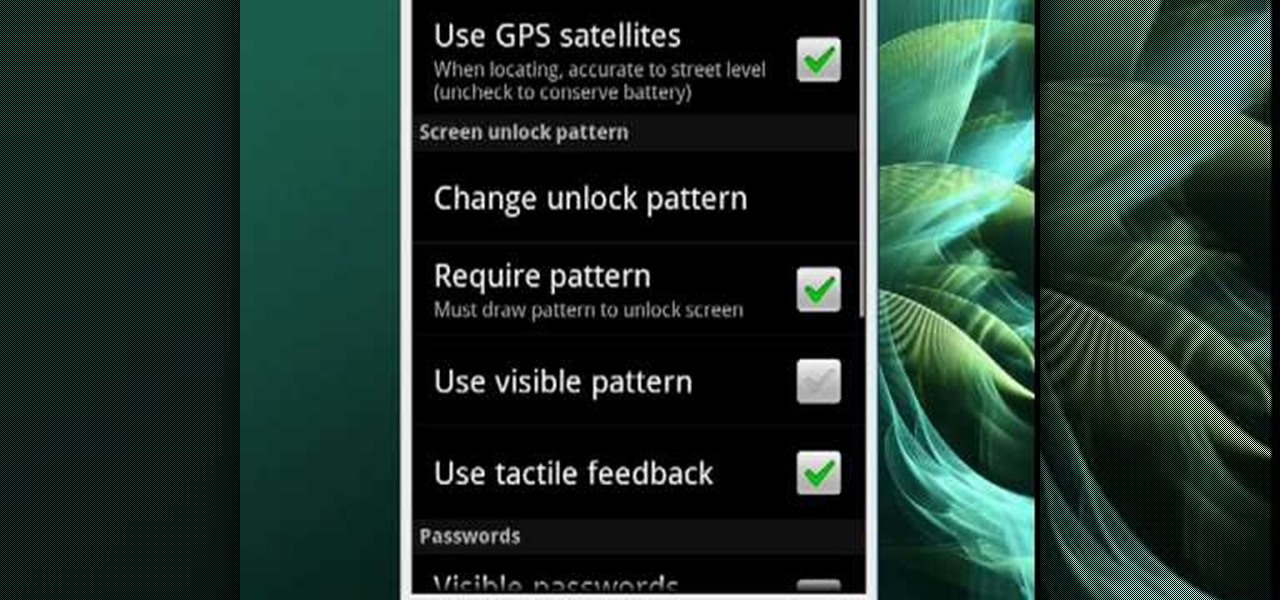
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

Before you can get started recording or mixing in Pro Tools 9, you'll need to create a new session for your project. This free video software tutorial from Lynda presents a complete and thorough overview of the process. Whether you're new to Pro Tools or just new to Pro Tools 9, Avid's first native, software-only version of their popular Pro Tools DAW, you're sure to find much of value in this brief video.

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.