
News: Sneaky! WhatsApp Adds Encryption to iCloud Backups on the Sly
WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!


WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

If you're like most busy workers, your day doesn't get started until you have your first jolt of fresh coffee. When you are feeling extra sluggish and need a boost, try a strong Cuban coffee that is sure to start your engine.

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create some cool effects for your custom map in Starcraft 2, including a voting system and a creep t...

In this economy any job is better than none at all, right? Of course, but if you know you are worth more than you're making, follow this tutorial for tips on how to ask your boss for a raise. You'll never know if you don't ask! Good luck!

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.
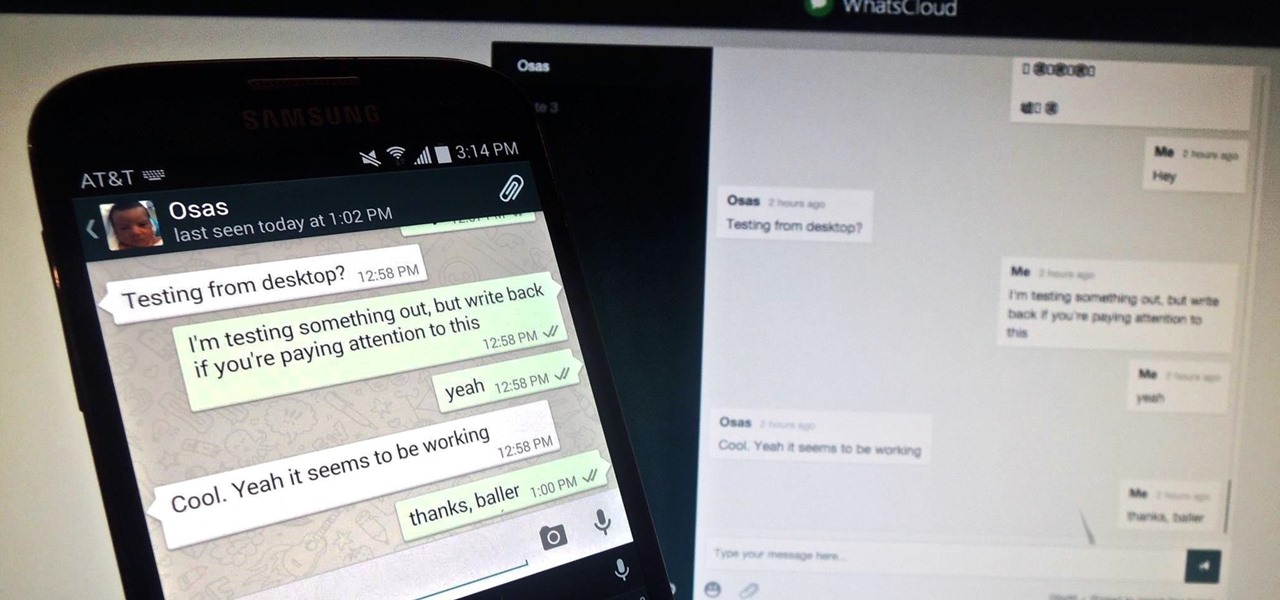
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...
Do you worry that if your PC is stolen someone can copy all of your data? Then you should encrypt your hard drive and removable USB drives too. In this video tutorial, you'll see how Windows 7 has beefed up Bitlocker, its built-in encryption program, and learn how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just under two minutes of your time. For more information, including complete, step-by-step ...

Encryption is the process of converting you data in to other obscure form so that no one can read it. Encryption can also be done using batch files. Batch files are scripting programs in windows which can be used to program small automatic operations. To do this open a notepad to write the batch program. First turn of the echo by inserting the command '@echo off'. Now write the rest of the program as shown in the video. Now save the image as a bat file. Now you can encrypt this batch file. To...
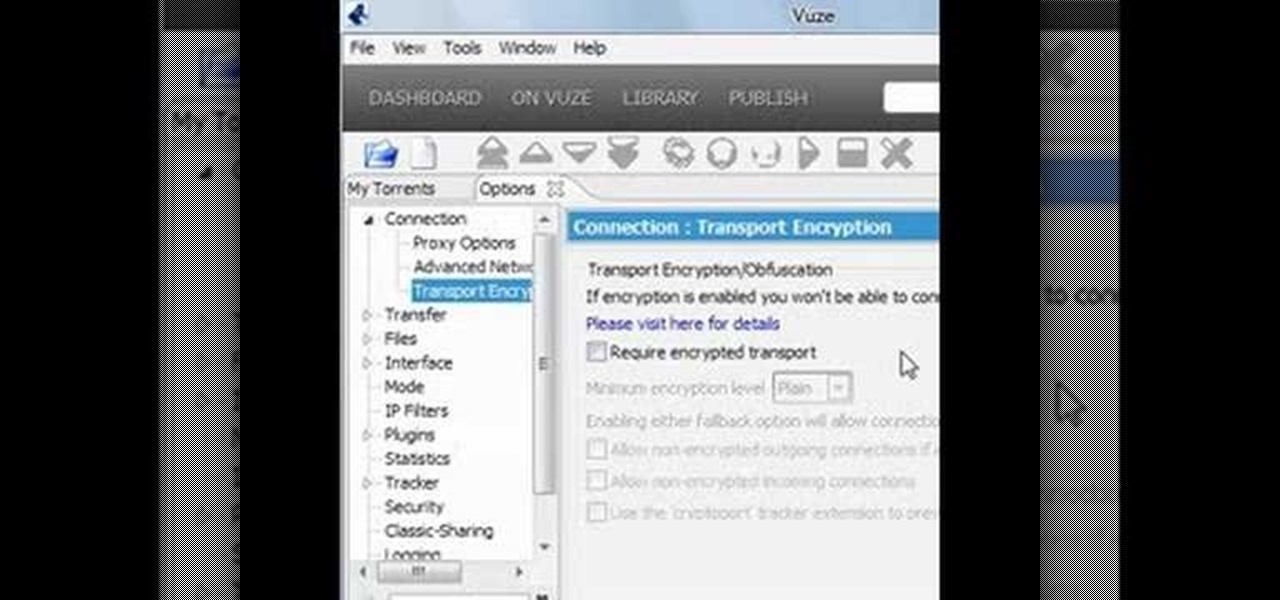
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...
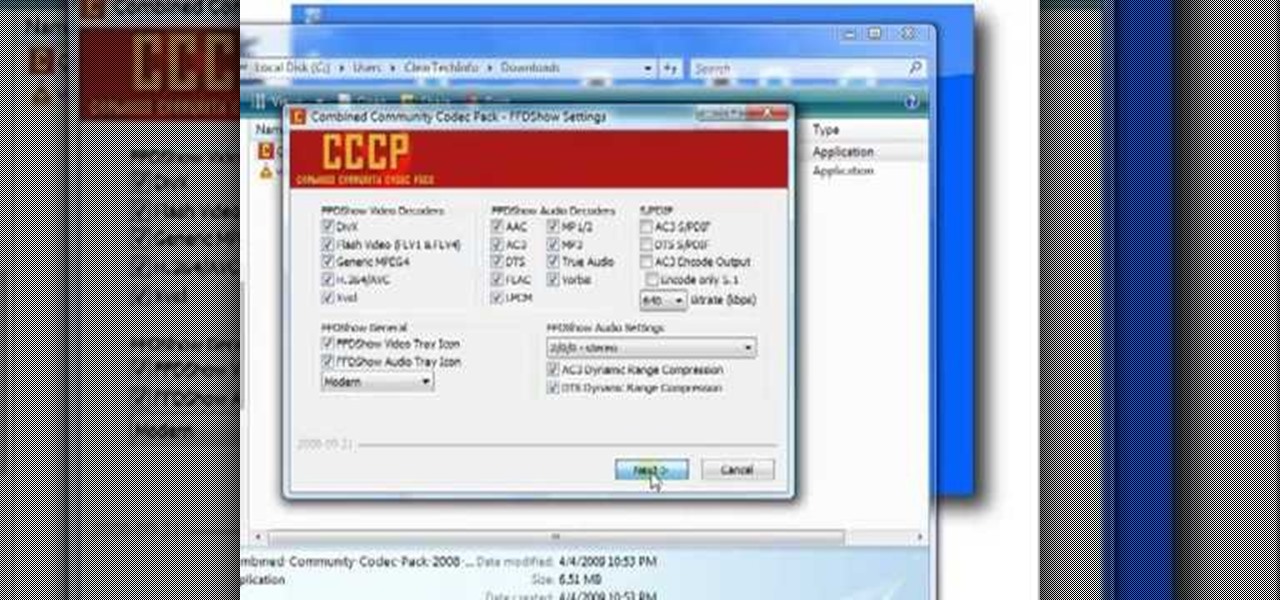
In this ClearTechInfo tutorial the instructor shows with examples on how to hear and view any audio or video file on your Windows PC. This is a basic tutorial where the instructor shows how to open and play them. Video files in many formats are not recognized directly by the Windows media player like the avi format and mkv format files. Even if we try to open these files it shows an error message that the file is not supported by the player. So in order to play these kind of files we need to ...

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.
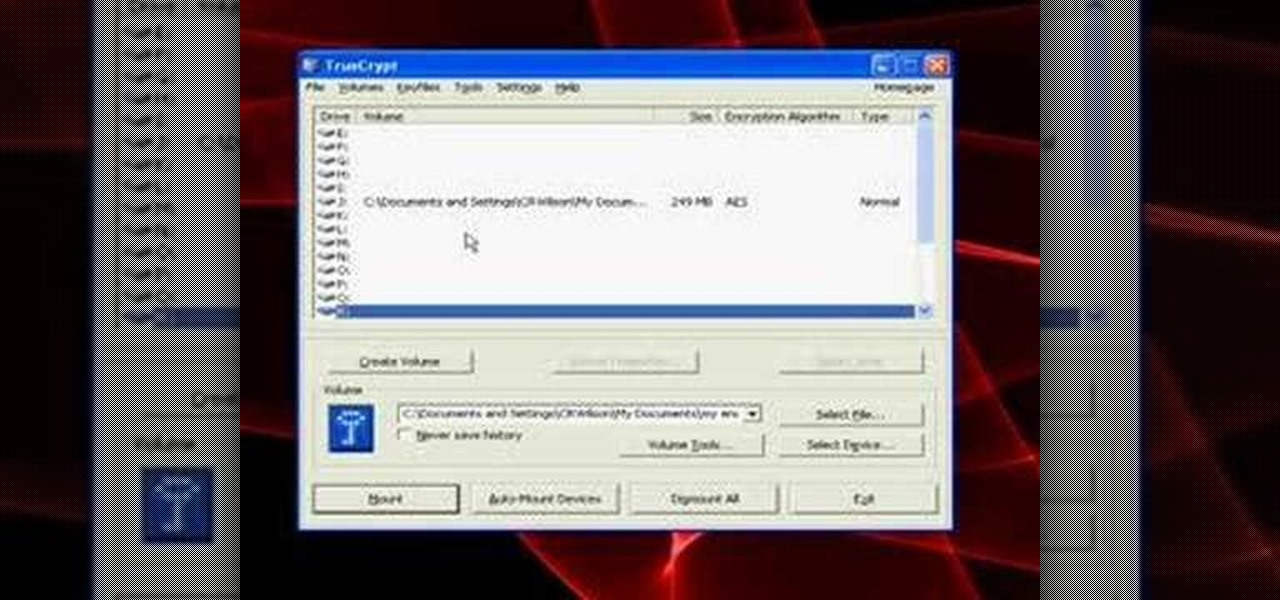
A tutorial on how to open, mount volumes, create volumes, and dismount volumes with Truecrypt, the free, open-source encryption software. GRAB LOW RES VERSION AS A DUP LINK!!
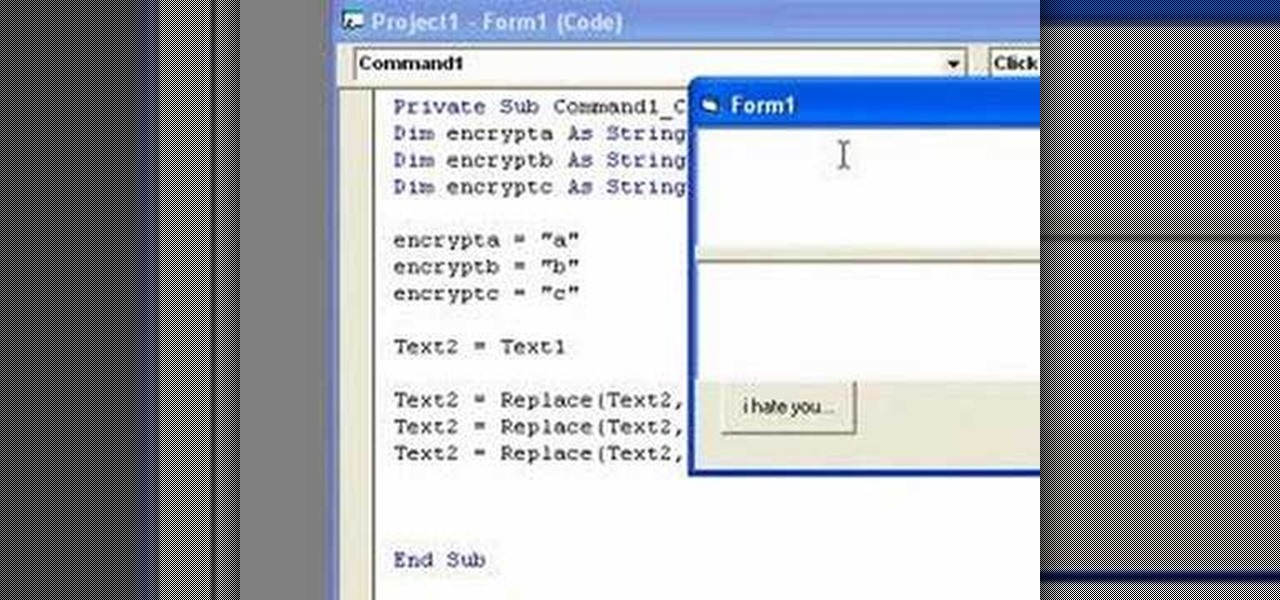
In this clip, you'll learn how to implement video encryption and decryption in a VB app. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.
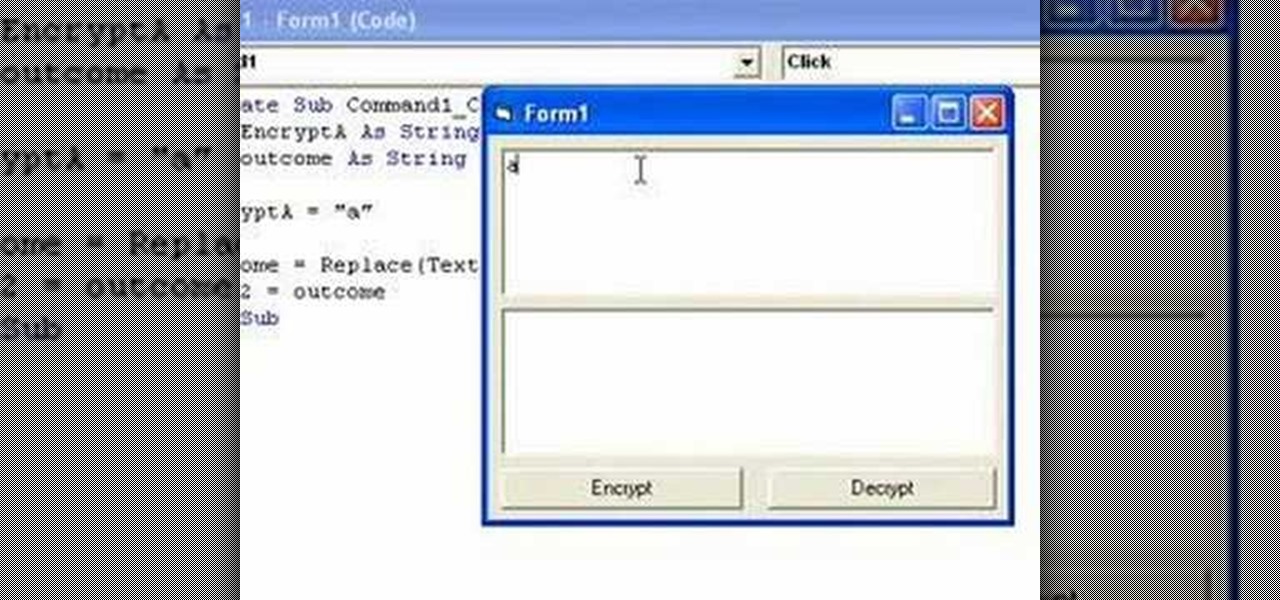
In this clip, you'll learn how to implement simple text encryption and decryption in MS VB 6. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Visual Basic programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.
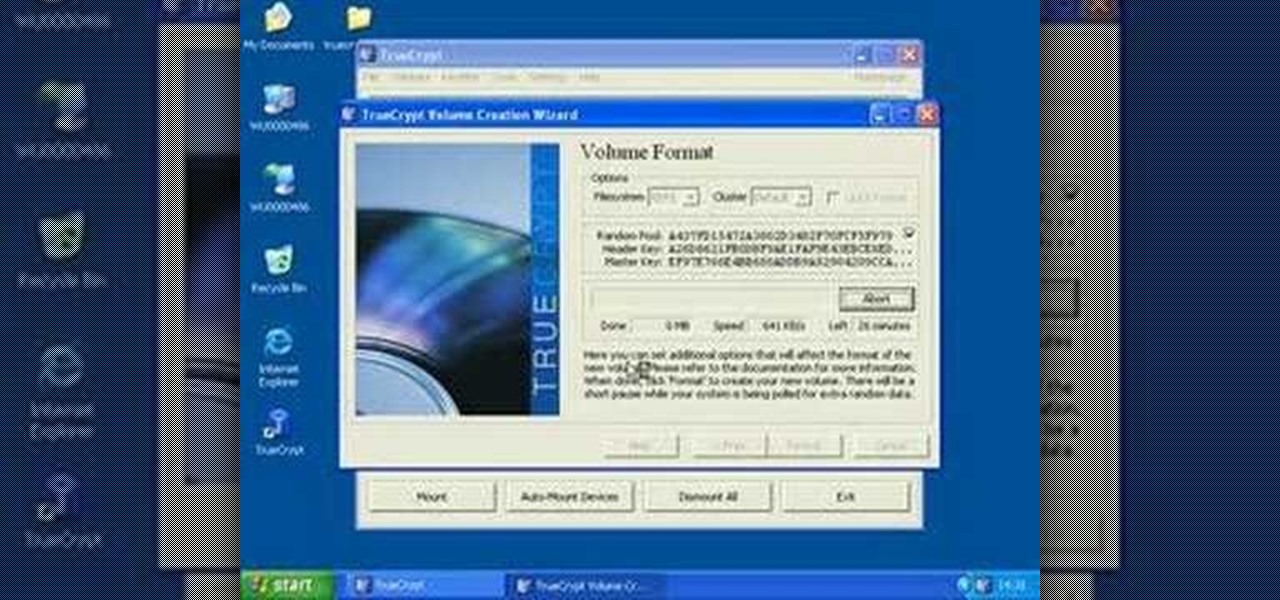
This video tutorial will explain you how to secure a USB thumbdrive (or flashdrive) using the free, open-source encryption software TrueCrypt.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.
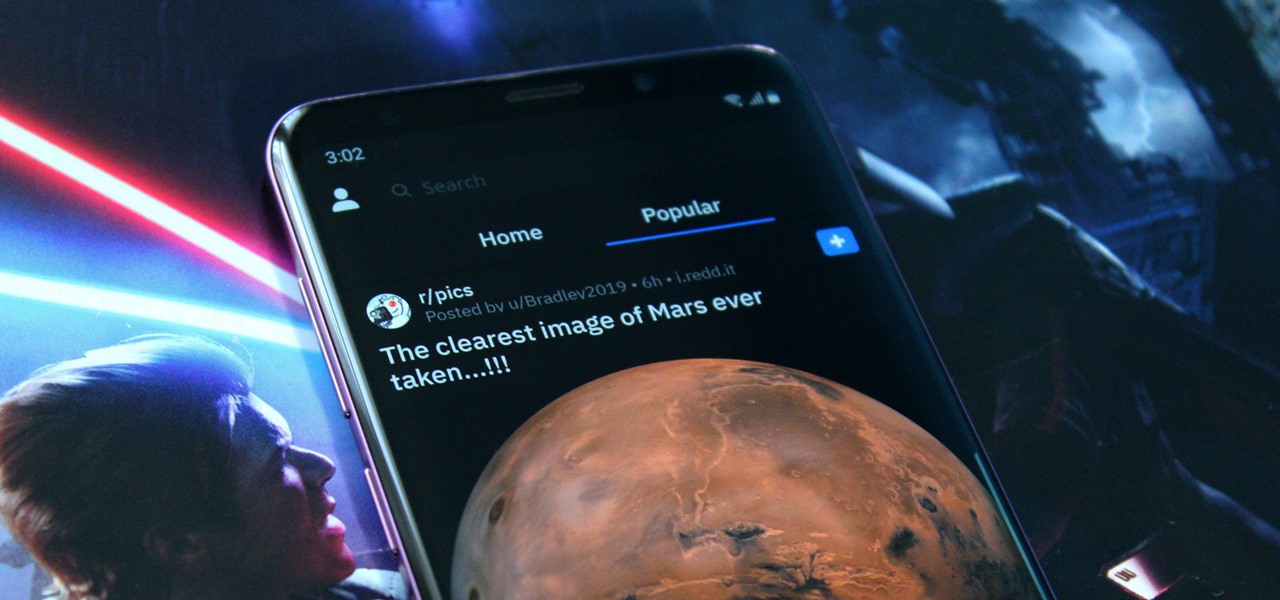
With both iOS 13 and Android 10 around the corner, system-wide dark mode is moments away from hitting your phone. In preparation, many developers have been adding a dark mode to their apps, including the official Reddit app.
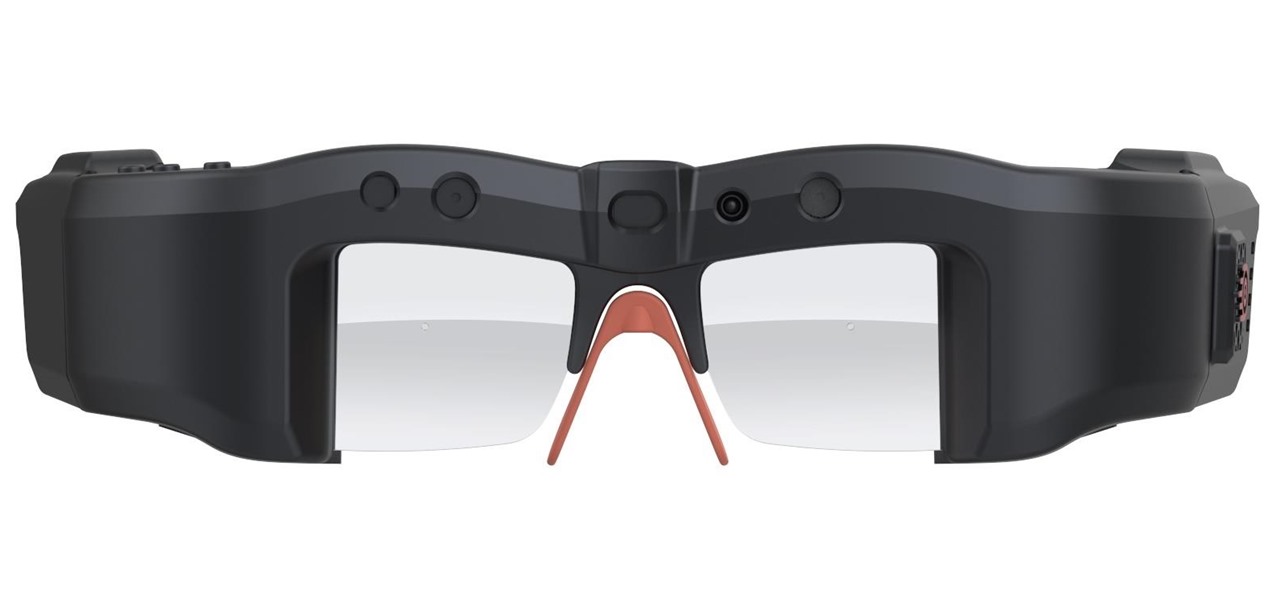
Augmented reality wearables maker ThirdEye Gen, Inc. has officially released what it claims are the "smallest mixed reality glasses" in the X2, which will be available for hands-on demonstrations at the company's CES 2019 booth this week.

One the main gripes against cutting-edge augmented reality headsets like the Magic Leap One and the HoloLens is the price — they're pretty expensive compared to most consumer devices. Well, now some of that pain has been relieved for those looking to pick up a Magic Leap One as the company has just announced a financing option that allows anyone with a spare $96/month to gradually pay their way into full ownership of the device.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.
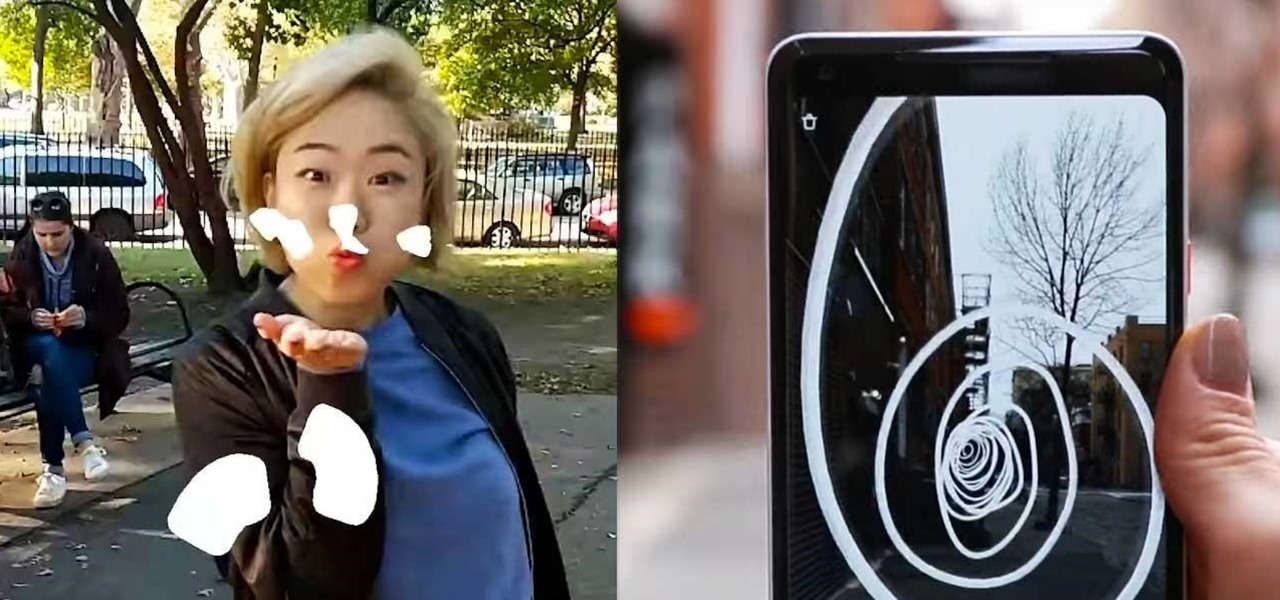
As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.

Though Google and Apple have released their own software-based toolkits for AR, components suppliers continue to advance their technology to better support AR experiences on the hardware side.

IKEA can help customers determine if a couch fits in their living room, but who is going to help them figure out if their new SUV will fit in the garage?

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.
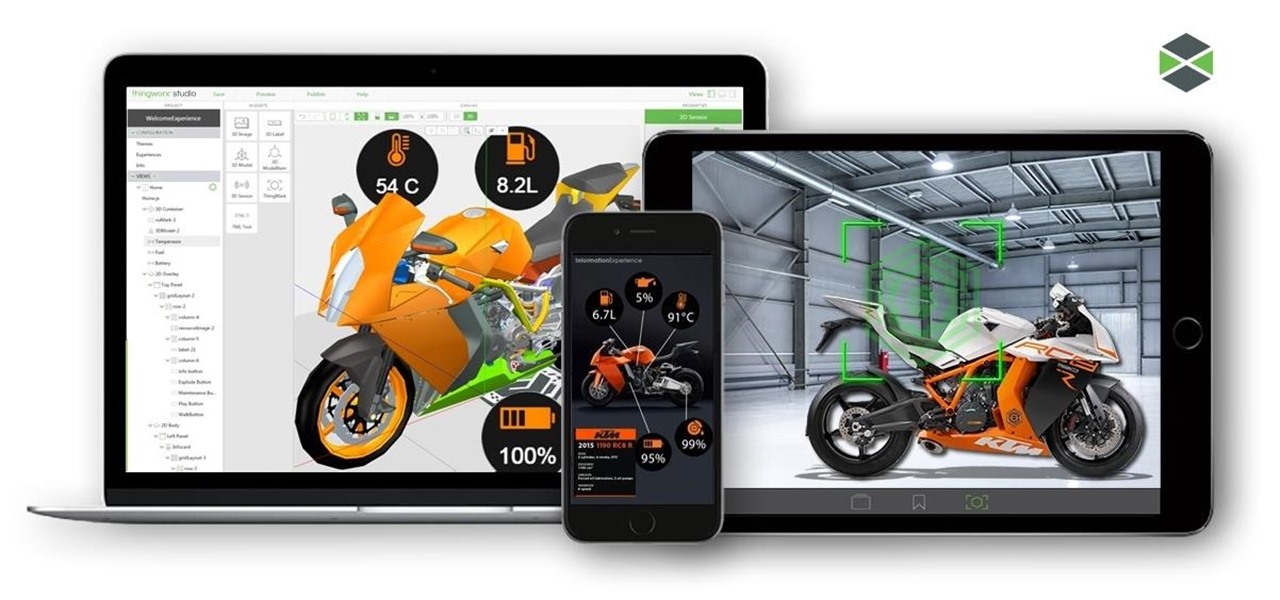
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

Headphone drama has been all the rage in the past year, with Apple killing off the headphone jack and trying to force AirPods upon its users (Apple, stop trying to make tiny, expensive, easy-to-lose earbuds happen. It's not going to work).

Snapchat accidentally—and then intentionally—announced their digital eyeglasses, known as Spectacles, over the weekend. While we'd hoped their augmented reality-heavy platform would result in related hardware, Spectacles unfortunately seek to "reinvent" little more than a video camera.

Virtual reality headsets like the Oculus Rift and HTC Vive tether to desktop computers with robust GPUs in order to harness their power. The free-roaming, cordless Microsoft HoloLens forgoes those chains but loses a bit of graphical processing power in the mix. However, a recent report suggests we may get the best of both worlds.

Wish your dull room was a little more refreshing? Through the power of mixed reality and the Microsoft HoloLens, one app can transform your space into a relaxing tropical island.

Apple announced their new iPhones today, and the 7 Plus features two camera lenses on its backside. That could push smartphone photography ahead in a major way. It may also serve as the basis for their foray into virtual, augmented, and mixed reality.

Data visualization has many applications in virtual and mixed reality, since a third dimension literally adds important depth to the represented information. A new app called HoloFlight is a good example of this, combining flight-tracking data and the Microsoft HoloLens to surround you with a look at every plane in the sky.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.