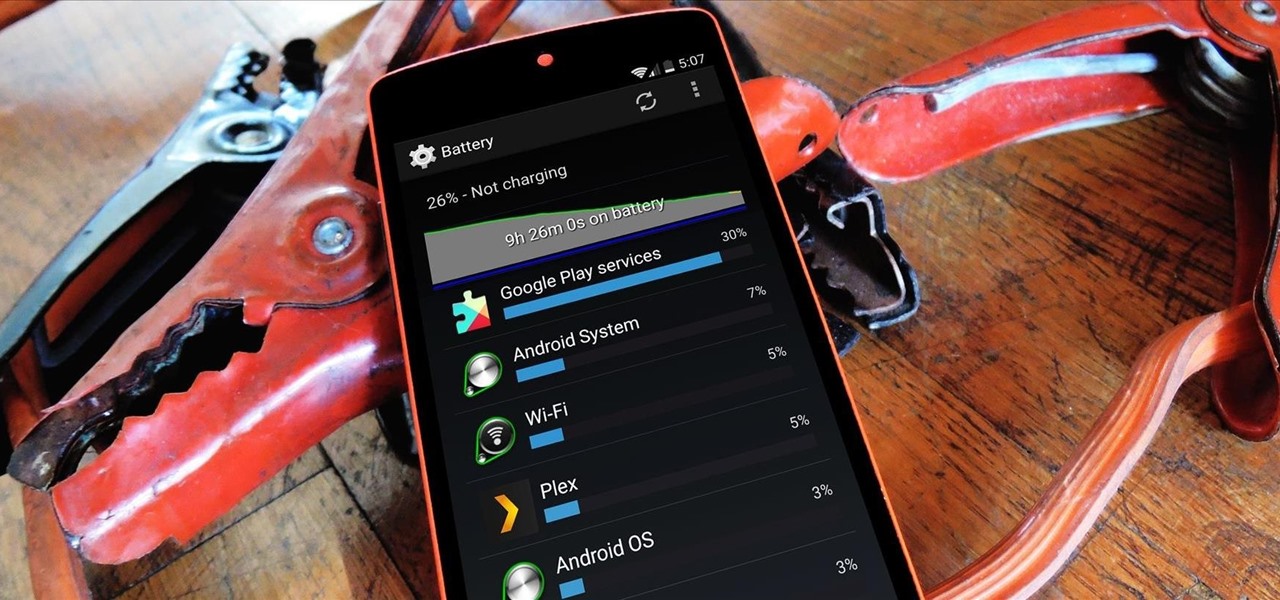
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.
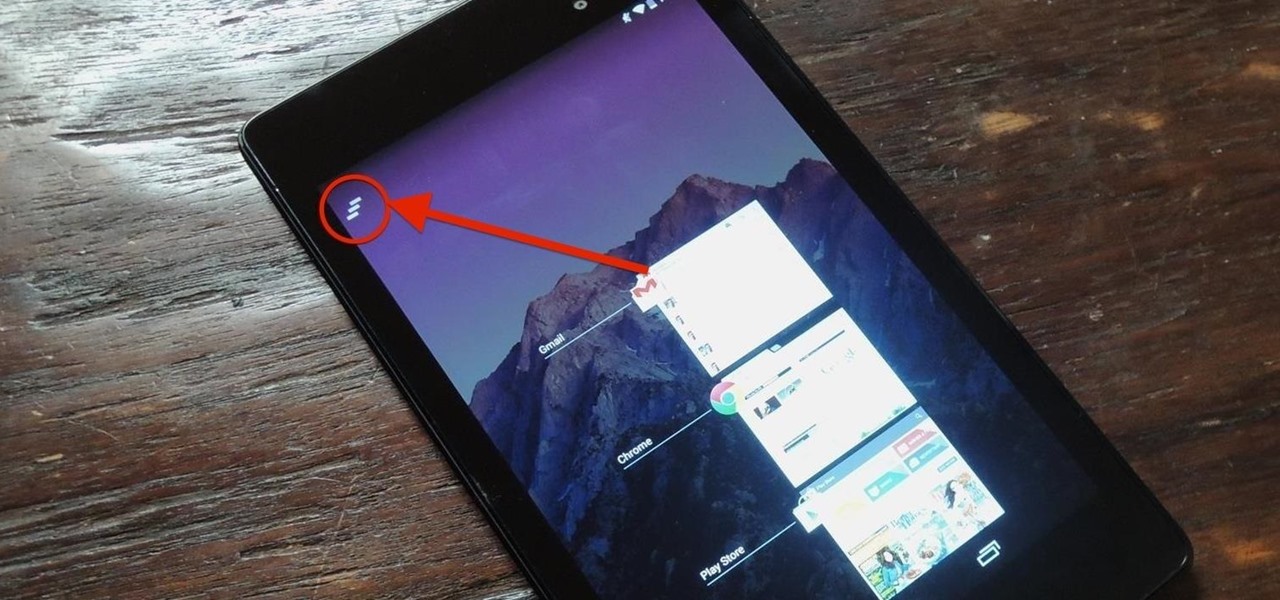
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).
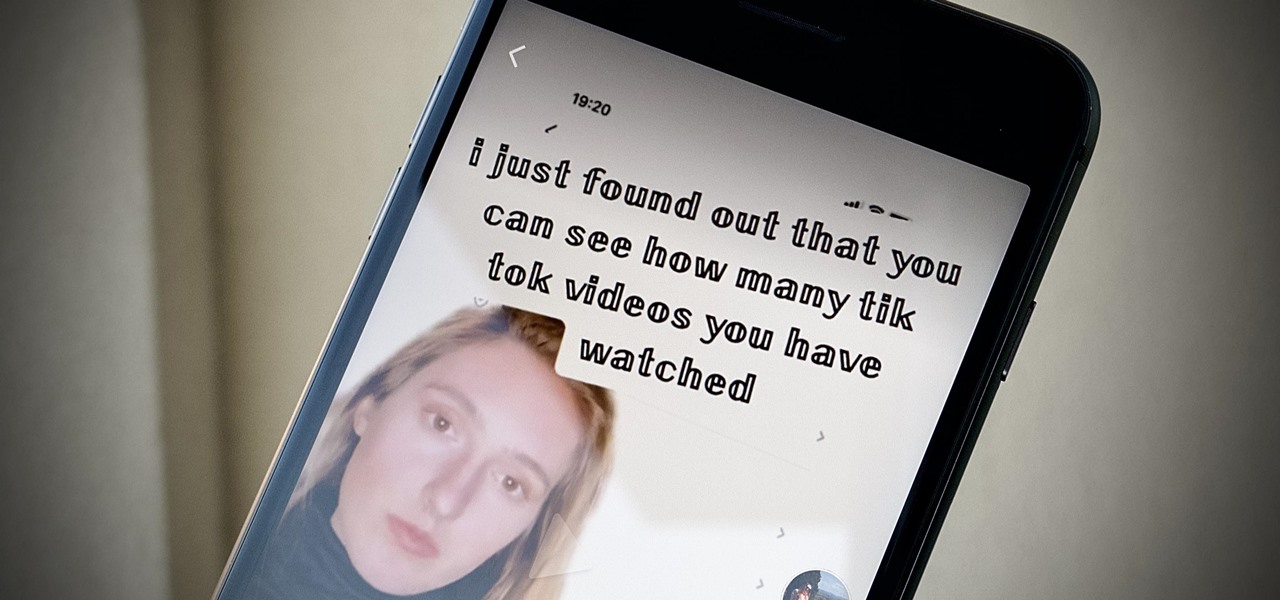
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?
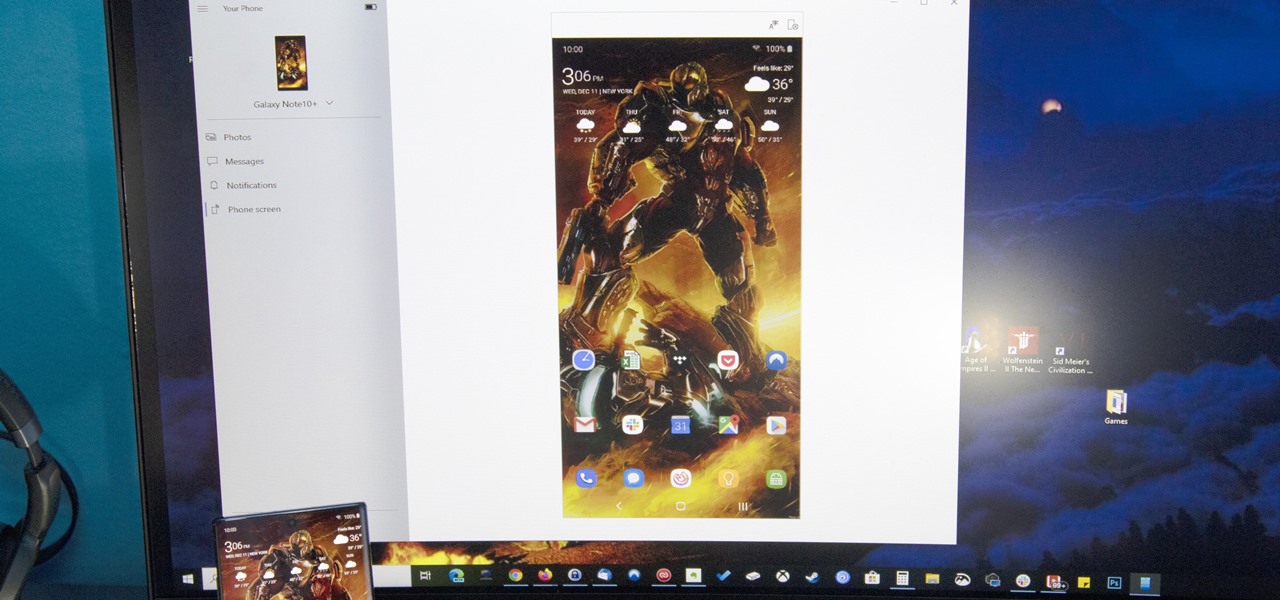
After exiting the mobile market, Microsoft has redirected its efforts to better integrating their services with Android. Thanks to a partnership with Samsung, that Windows integration is even better if you have a Galaxy phone.
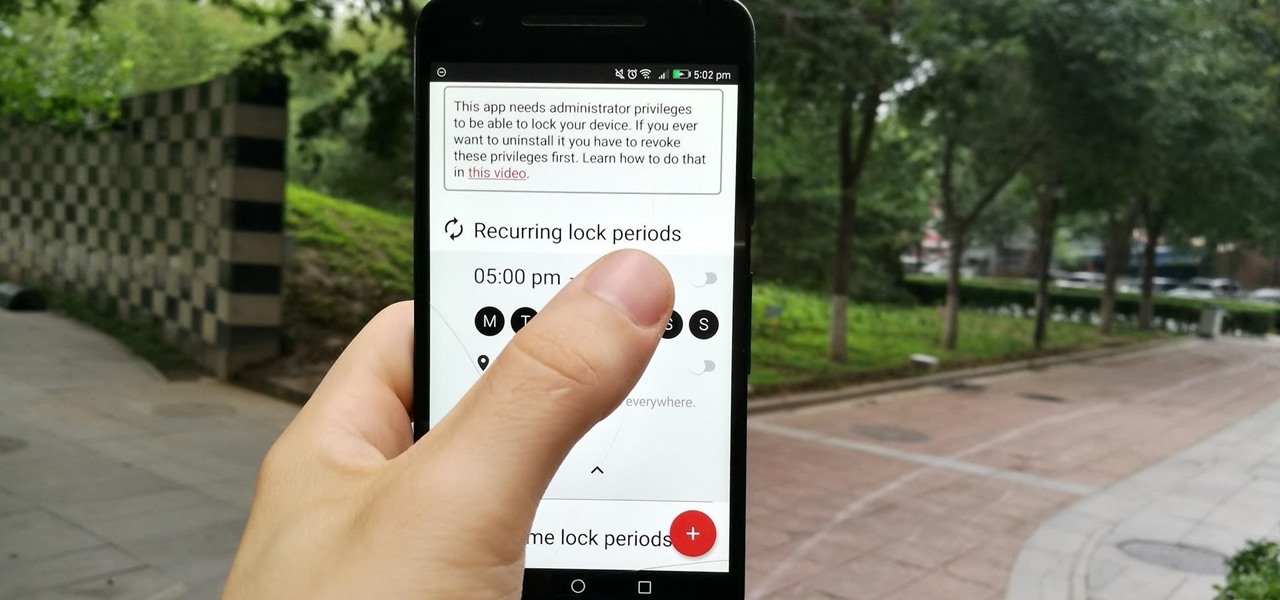
The OnePlus 7 Pro comes with a new Zen Mode feature to help increase your concentration and reduce distractions. It takes things a step further than Google's Digital Wellbeing by disabling your device and stopping sounds. But even if you don't have a OnePlus, you can now get this distraction-free feature on any phone.
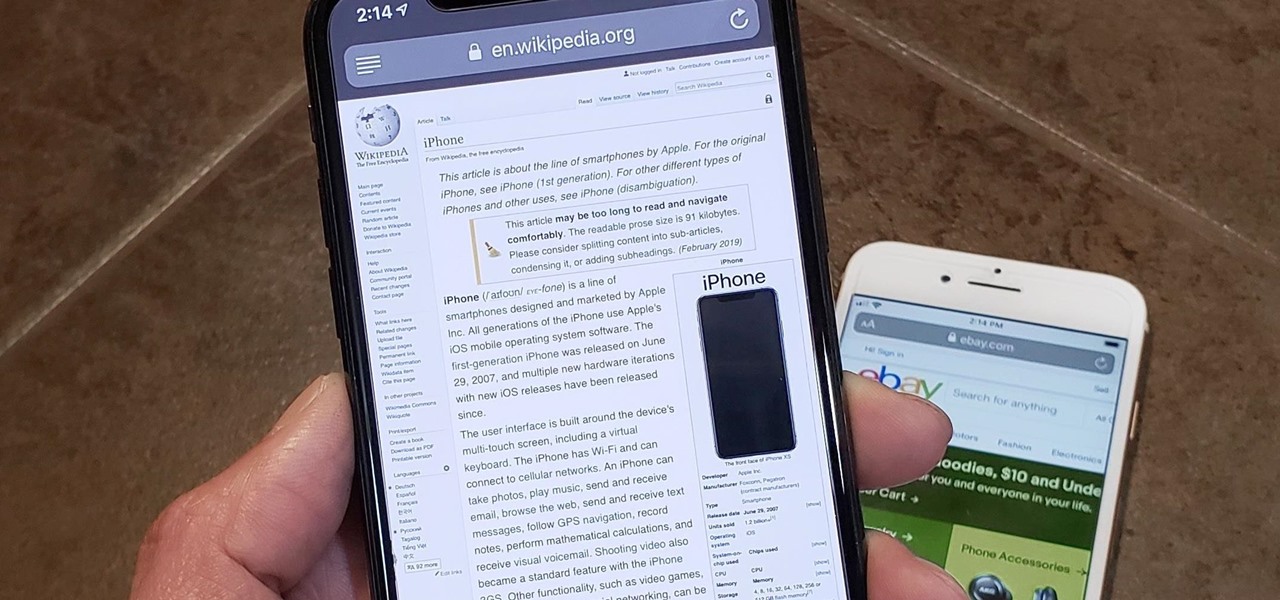
In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

Apple likes to play their cards close to the vest, don't they? The iconic company doesn't usually reveal much about their projects until it's time for an official announcement. But sometimes ... They can't stop a leak of information from happening, or they just leak the news themselves like Steve Jobs used to. That brings us to today's news. It appears the tech giant has hired an augmented reality specialist from NASA to join their AR team.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implementation that all devices can use—meaning that in the near future, we may finally start to see apps that let you log in to your account with your fingerprint instead of a password.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

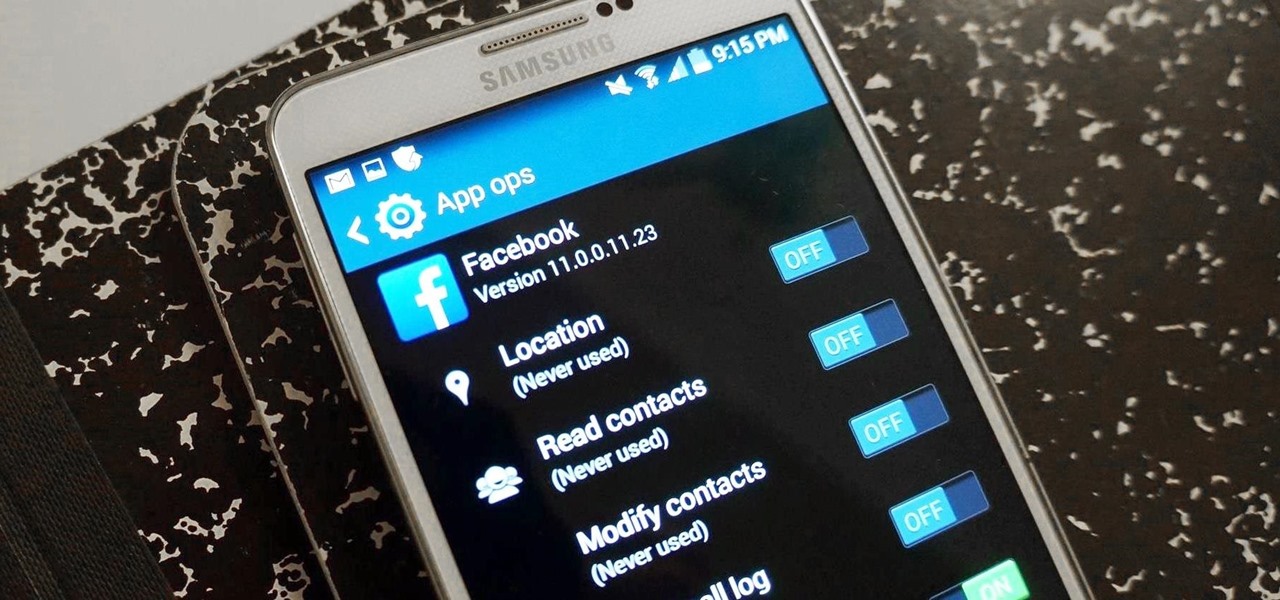
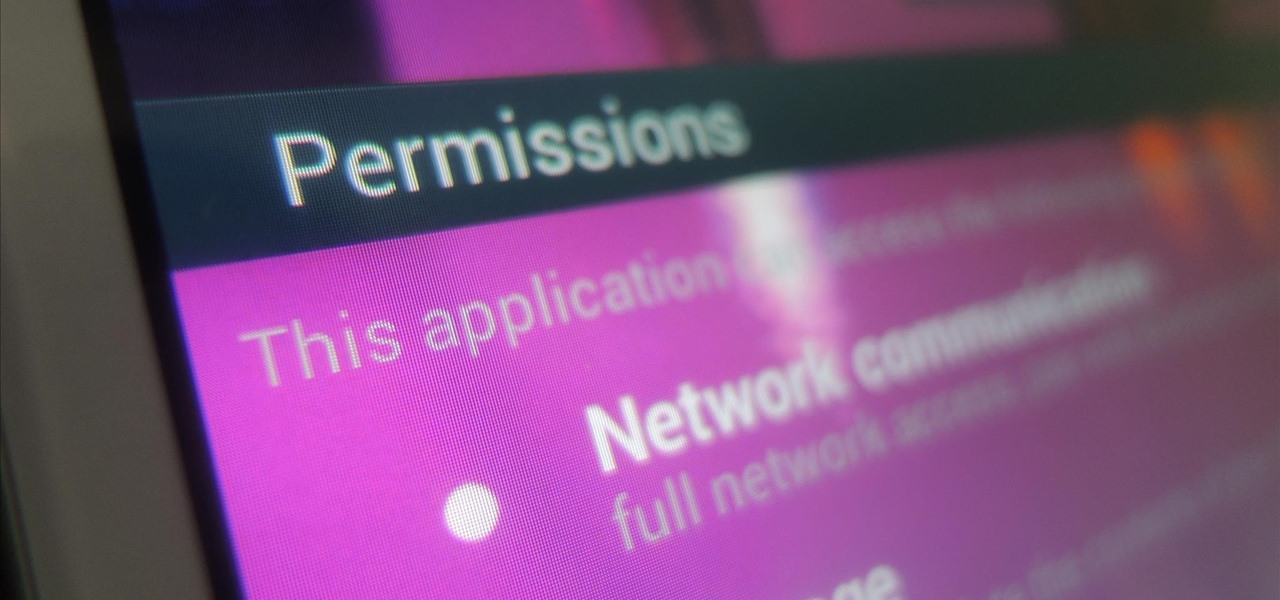
It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

Developer Options is your first step to becoming a power user. If the Pixel 4a feels a bit slow, Developer Options can fix that. You want to root your device for unprecedented controls and powerful apps? You need to enable OEM unlocking in this hidden menu. ADB, secret features — Developer Options is where it all originates.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfully, there's now an app that will give you LED-style alerts with a ring around your S10's camera.

When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

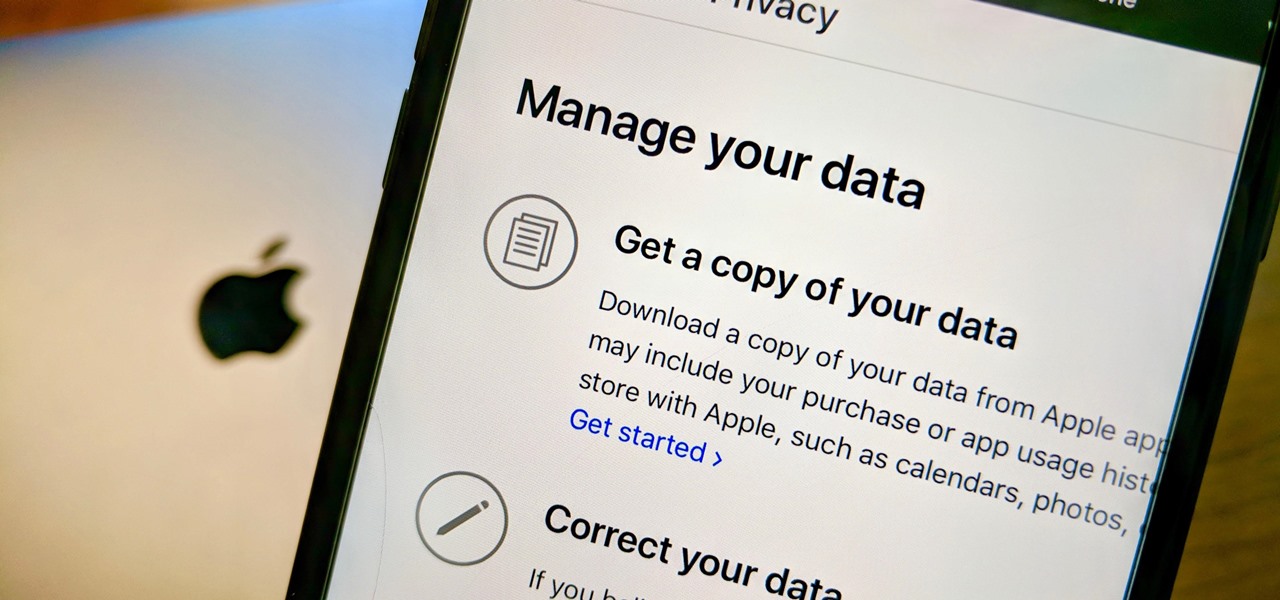
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

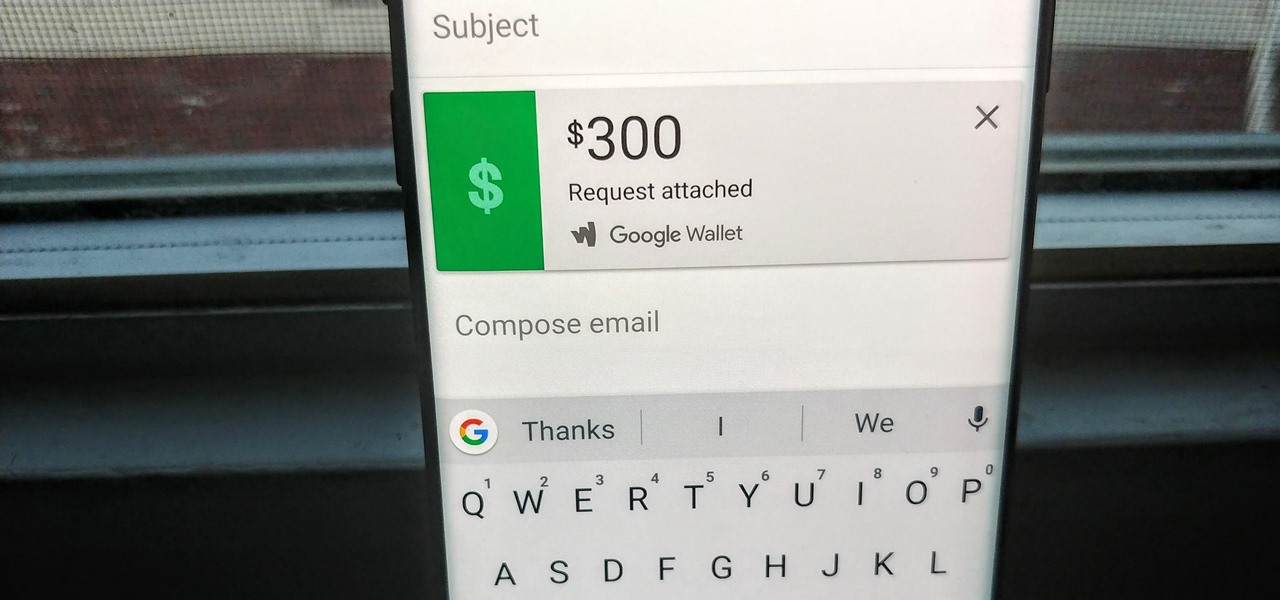
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

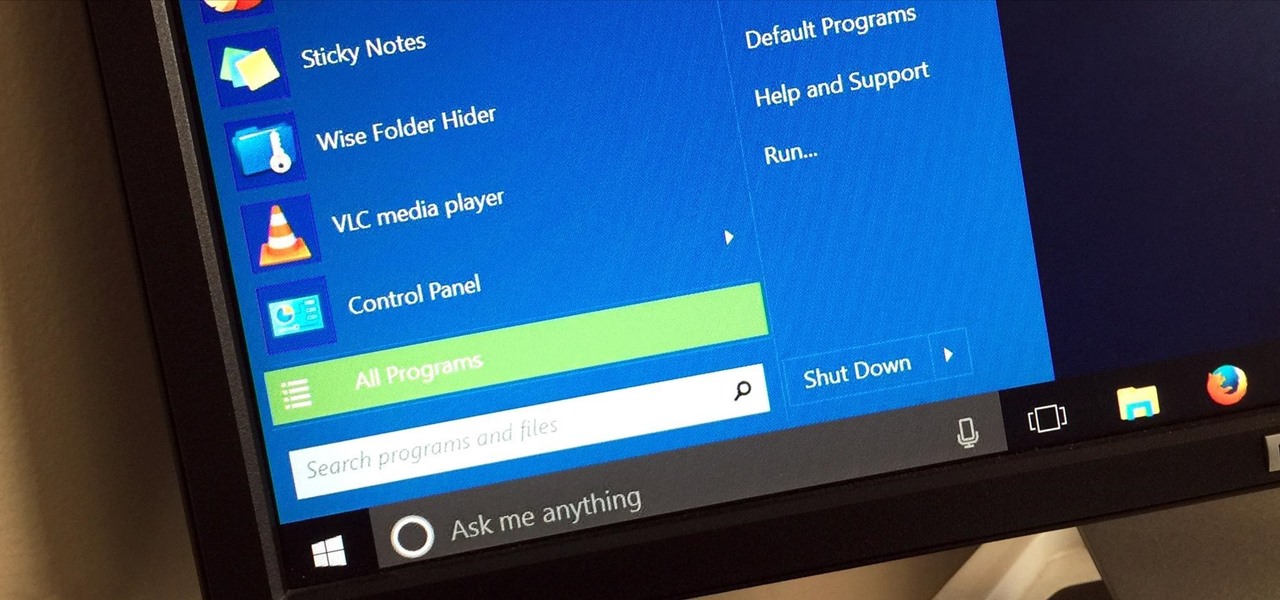
If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.