I don't know what they are feeding the kids in Canada but there are so many great bands coming out of there. Vancouver's Terror Bird are no exception. Made up of Nikki Never (Modern Creatures) and Jeremiah Haywood (Twin Crystals), these two have released a few cassettes and a couple singles now. "Sociopaths are Glam" is my favorite so far. This was a cassette release on Night People out of Iowa City. The music is dark and murkey, lo-fi synth pop. They pull from mid 80's dark wave but their m...

Burger Records, a vinyl/cassette label based in Fullerton, Ca. and run by members of Audacity and Thee Makeout Party, have reissued 3 cassette tapes from Cleaners From Venus. "Midnight Cleaners" (1982), "In The Golden Autumn" (1983), and "Under Wartime Conditions" (1984). These cassettes have been loooong out of print and nearly impossible to find. If not for blogspots, some of these tracks would never be heard again. Martin Newell (Mr. Cleaners or Mr. Venus???) started recording and releasin...

The Job Board is a weekly entry of the most ridiculous Cinematography related jobs posted online. Note: This posting was from a year ago.

When your opponent throws down "AA", you tell them no abbreviations, but alas... it's not. They build "ZA" on the board for 64 points, and you say it's slang, but it's in the dictionary. Next is "EF", and you let them know that spelling out letters is not allowed and ridiculous... but it's totally legit.

This delicious new trend is the lovechild of everyone's two favorite foods: hamburgers and sushi. Yeah, that's right... meet the sushi burger.

According to the electronics giant, Samsung and Google have signed a global patent license agreement that, according to Samsung's official blog, "covers the two companies’ existing patents as well as those filed over the next 10 years." The patent war in the smart device realm has been raging for years; whether it's Apple and Samsung at each other's throats or one half of the tech sector suing the other, litigation has been the main weapon in a conflict that used to be won with innovation.

Evidently, when you are thinking about a problem, you use up glucose. This can be seen by monitoring blood glucose as people work on math problems and the like.

A rare textile woven from the silk of more than one million spiders is currently on display at the American Museum of Natural History in New York City. The incredible textile measures 11 by four feet, and is the largest piece of spider-woven textile in the world.

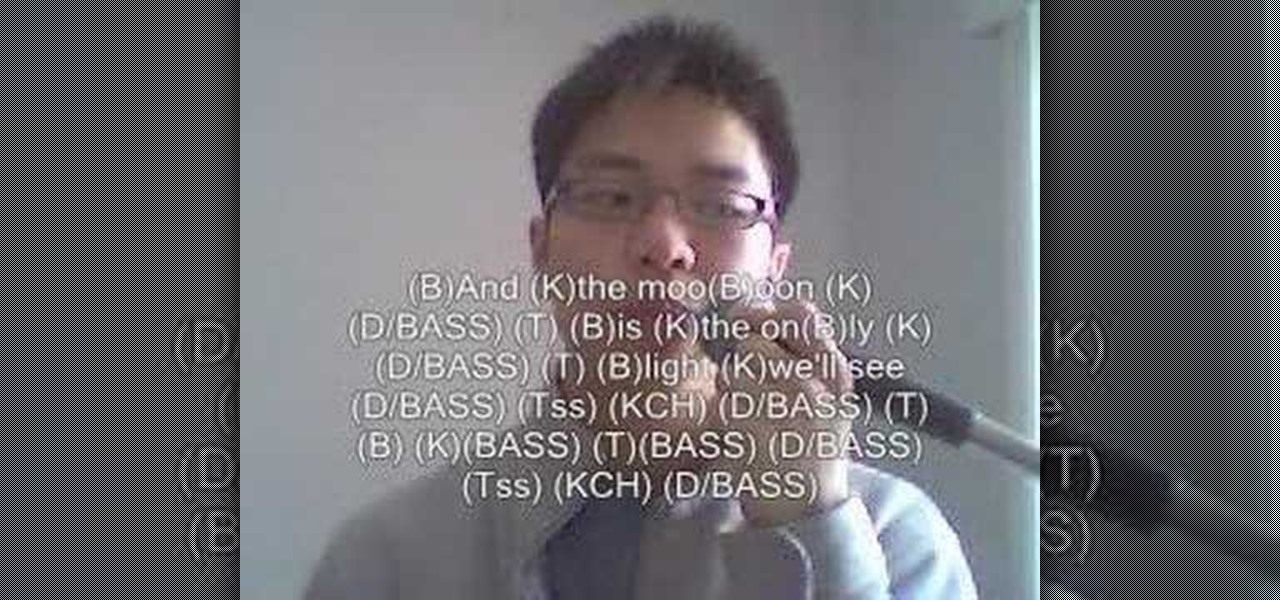
In this how to video you will learn to beatbox "Stand by Me" by FaithSFX. This tutorial is great for intermediate beatboxers.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

As a USC student with limited funds, I'm always trying to figure out how to make the most out of my night when I go out. LA is great because there is so much going on for little to no cash if you know where to look. Echo Park/Silver Lake definitely has the most options, see below for my breakdown.

You may have already heard of Zazzle, an online service that allows you to print on a variety of goods (tees, mugs, posters, etc.). You can design-it-yourself, or choose from Zazzle's library of available designs.

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

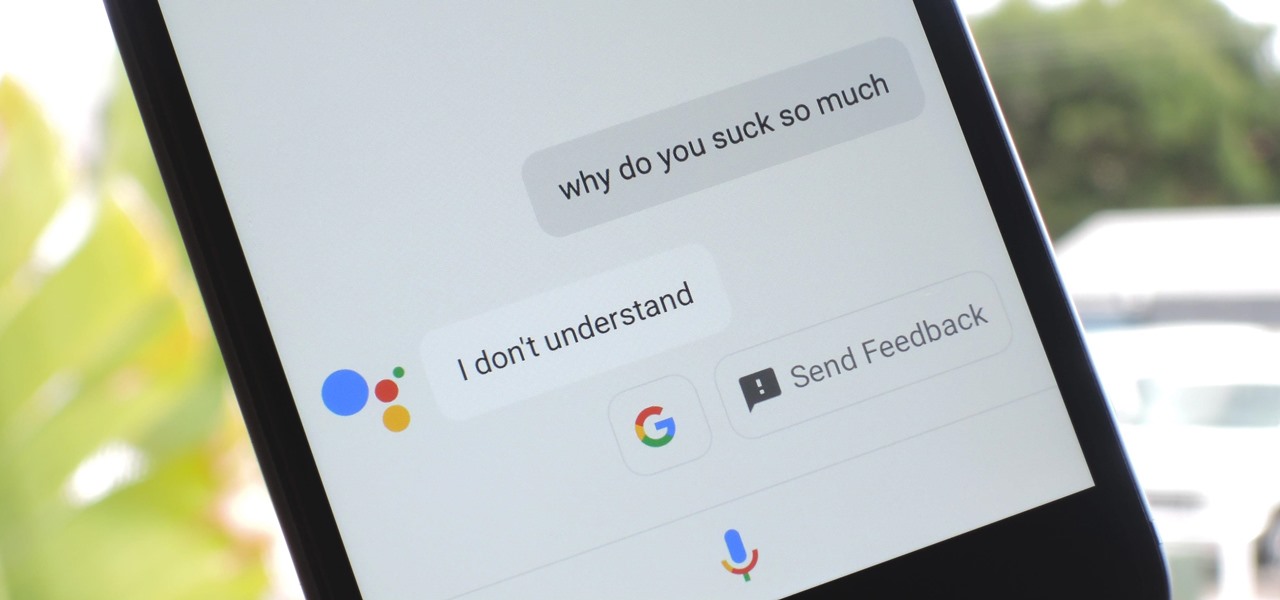
Google Assistant was just released for iOS today. You may know it as the AI-powered assistant that makes Google Home tick, or perhaps you've heard from one of many review sites about how much better it is than Siri. Well, before you run off to the App Store to install Google Assistant, let me save you some time: It sucks.

Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

Soba noodles and vegetables are a great healthy and satisfying meal and it's good for your heart! In this video series Jane Murphy shows you how to take a traditional lo mein or chow mein type Chinese dish, and make it heart healthy by making it with soba noodles and lots of veggies.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

Now that you have your two-letter words down and have practiced your skills, it's time to move on to another important part of Scrabble gameplay—the opening move. There's a well known adage that states, “The player going first will win 54% of the time—all other things being equal."

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.

No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're not going to win by only playing two-letter words, but there are definitely occasions when the game could slip from your hands by not playing them.

D.I.Y.: Start Your Own Cassette Label! By adam_schragin on Aug 4, 2008 at 10:56am in DIY

The biggest win in the race for consumer augmented reality smartglasses to date belongs not to Apple, Facebook, or Google, but Snapchat's parent company, Snap.

Even as someone with super pale skin that burns instead of tanning, I don't use sunscreen nearly as often as I should. Or, uh...ever. My skin cancer prevention routine mostly involves hiding from the sun as much as humanly possible. If you're like me and hate the greasy feeling of sunscreen, there are other ways you can protect your skin by increasing your sun tolerance. Your diet actually has a lot to do with how easily you burn, so by getting enough of a few key nutrients, you can decrease ...

Ok, so you've memorized the list of valid 2-letter words, but when challenged after playing one, can you smugly demonstrate your dominating intellect by spouting out the proper definition?

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Label Profile: Night-People [Night-People founder Shawn Reed, playing live in Montreal as Wet Hair]

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.