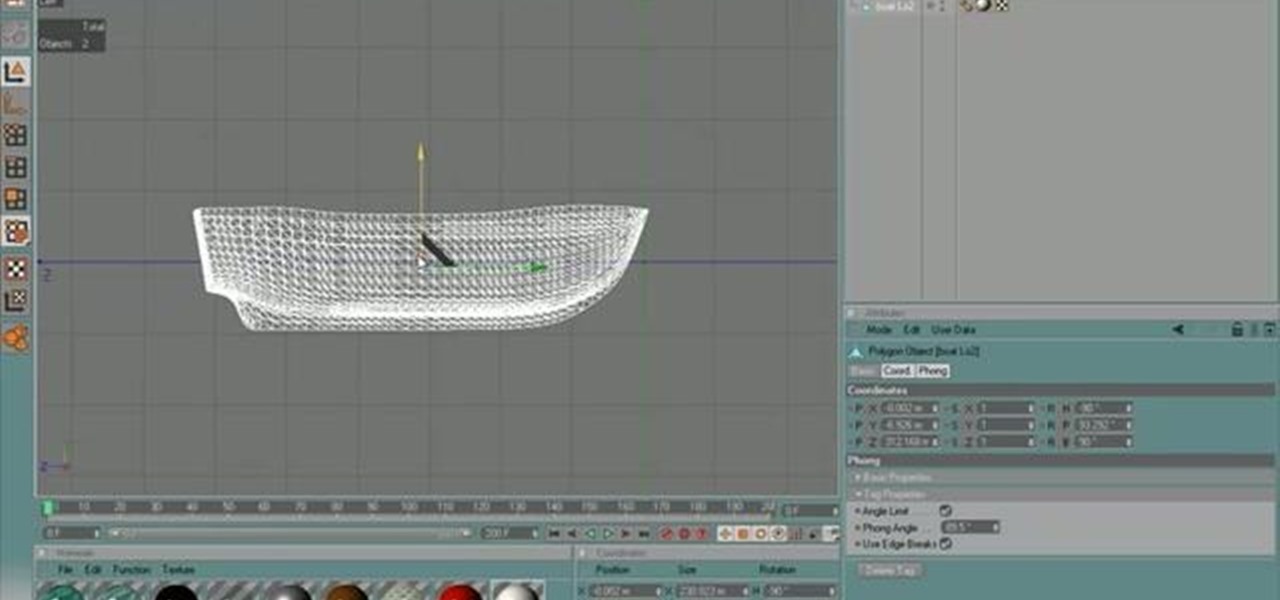
Need some help figuring out how to generate proxy objects in RealFlow? Never fear. This guide will show you how it's done. Whether you're new to RealFlow's popular fluids and body modeling software or are just looking to get better acquainted with the application its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own RealFlow projects, watch this 3D modeler's guide.
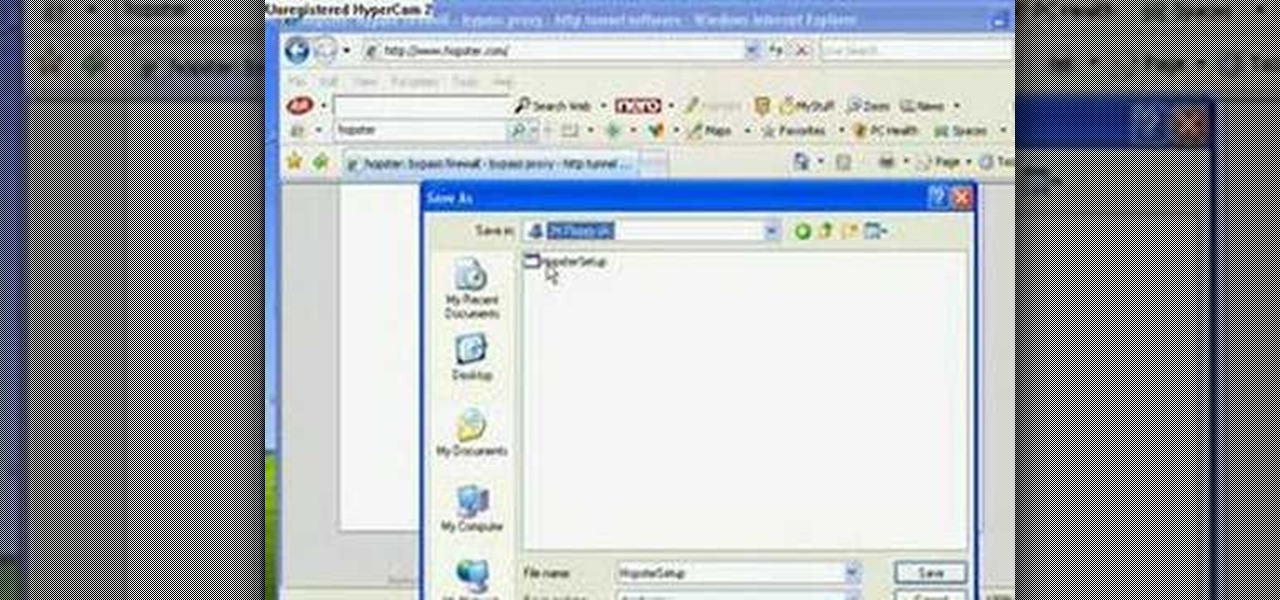
In this video tutorial, viewers learn how to bypass web-sense filter using the software, Hopster. This program allows users to bypass firewall, bypass proxy and HTTP tunnel. To download this program, go to Google and search for the program. Click on the first result and select download. Once the file is downloaded, double-click on it and follow the instructions to install the program. This program runs silently and invisibly so that the administrator won't be able to detect it. This video wil...
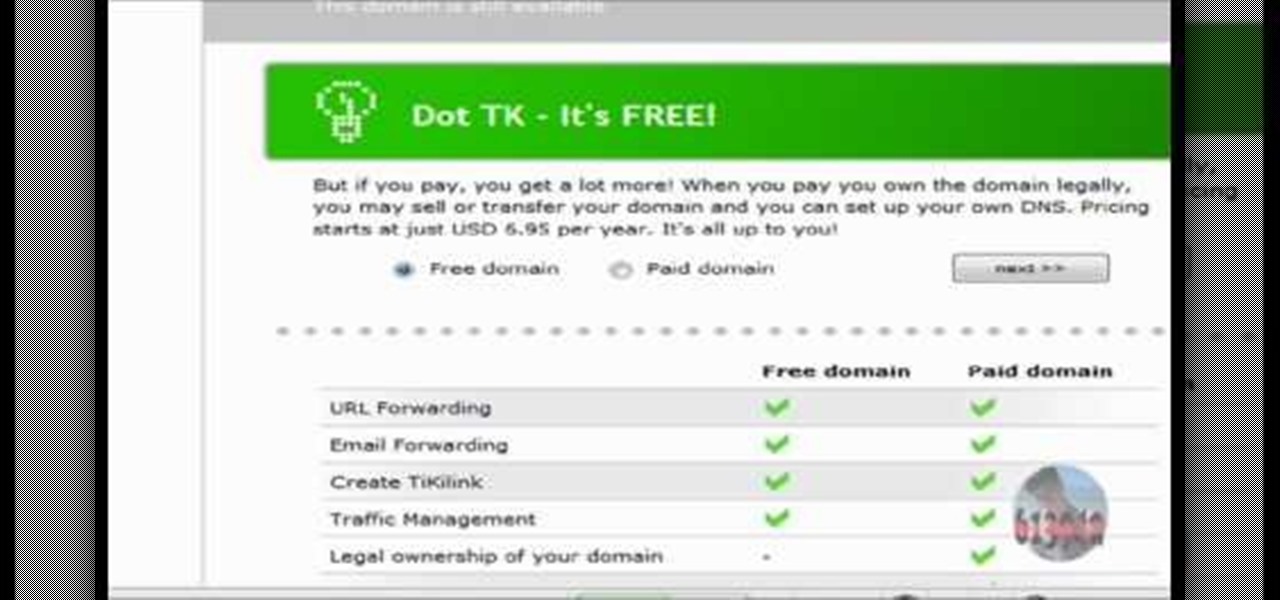
In this tutorial the author shows how to use a proxy at your school and get on the blocked site like MySpace etc. Now he points to the Dot.tk website and how to access it from Google.com. Now if you want to access any website you just need to copy the link and paste it into the pointed field in the Dot.tk website and now you can choose a new domain name for the website. Now you can choose the free domain option in the next page where the new website is setup. Now he shows how to go through th...

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome back, my nascent hackers!

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

The guys from Systm guide you through the makings of a MAME-based classic arcade machine including building the cabinet, mounting a TV, buttons and speakers, and configuring the arcade emulation software.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Wow! No longer do you have to buy those huge marble machine roller coaster toys — you can DIY one! This video covers the materials, tools and techniques used to make a homemade rolling ball marble machine. If you haven't seen this rolling ball marble machine toy in action yet, WATCH IT. It's a looping rolling marble machine made with wood, rebar tie wire and polyurethane tubing, featuring a magnetic elevator.

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.

Many sewing machine repairs can be made at home, and most repairs can be completely avoided through routine sewing machine maintenance. This tutorial shows you how to carefully disassemble your machine to give it a round of maintenance. You will need a screwdriver - make sure not to lose any of the screws!

Before you can mend or create garments with your sewing machine, you'll need to thread it. This video guide will walk you through each of the necessary steps, from winding a bobbin to threading the top of the machine itself. For more information, and to get started threading your own electric sewing machine, watch this free video guide.

Have a sewing machine and want to learn how to use it? If so, this ten-minute tutorial, which presents a general orientation to using an electric sewing machine, may be just what you need. For more information, and to get started using your own machine, watch this easy-to-follow video guide.

In this tutorial, we learn how to bypass a blocked site on a school computer. You will need a proxy to do this safely. First, go to a proxy site like Proxify. Going through here will prevent the school blocking system from coming up and ruining your fun. If you are blocked, you can use a text file document and run CMD on your computer. This would be the more technological way to do it. Try doing the website first to see if it works, if not, then you can try to change the firewall on the compu...

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

Mountain Rose Herbs John Gallagher shows us how to make our own quality powdered herb capsules using a machine in this video. You will need three things to do this, your powdered herbs, zero size capsules and a zero size capsule machine. He shows us the parts of the capsule machine so we can follow his instructions. Find a container to put the base of the machine in, pull apart the capsules, putting the bottom part in the bottom of the machine and the top in the top part of the machine, filli...

Analog reel-to-reel tape is some of the most in-demand recording equipment today. Learn how to use a reel-to-reel tape machine in this free video series that will allow you to utilize this piece of musical recording equipment.

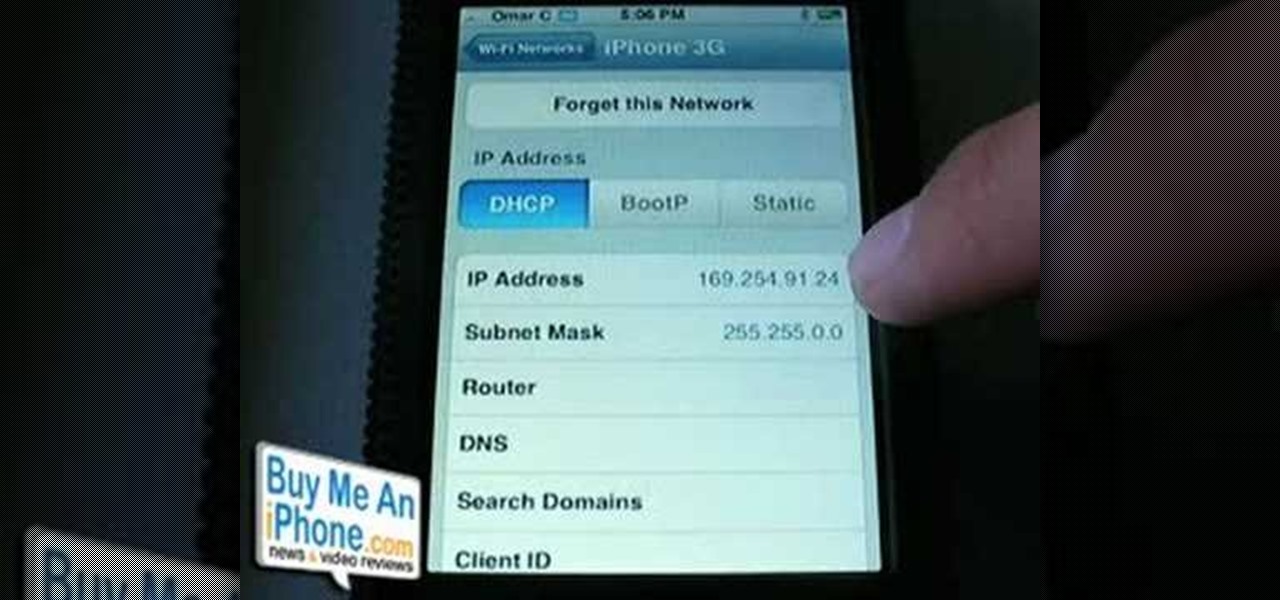
This is a video demonstration on how to tether your iPhone 3G to a Mac laptop to use the 3G network for surfing the web on the laptop. This is against AT&T's policy so try at your own risk. This is in place of the NetShare app that keeps getting removed by Apple or ATT. This let's you connect your computer to the 3G wireless network by using a proxy on your jailbroken iPhone.

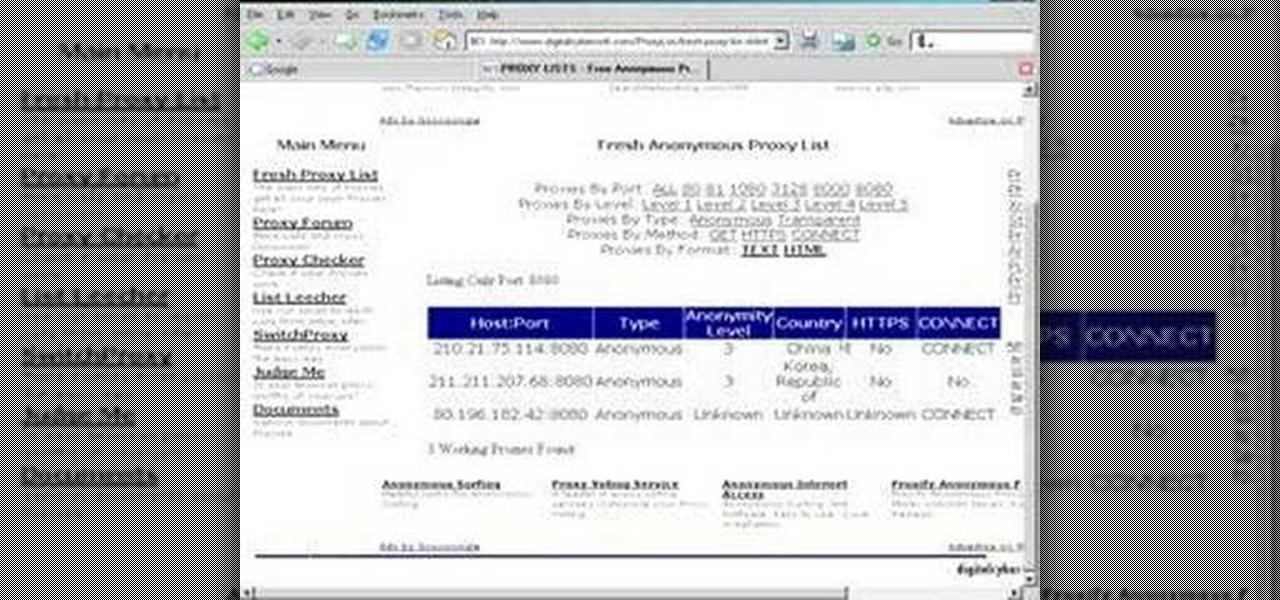
Tutorial on how to use a proxy to hide your IP address when surfing the web. This tutorial covers use with the Firefox browser although Internet Explorer (IE) is exceptionally similar.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Ruth demonstrates how to wind a bobbin successfully every time you attempt. Place the spool of thread on the machine and wind the thread between the two disks on the spindle (found in all machines). It is better to wind the thread twice to avoid the thread come off the spindle. This does not damage the machine in any way. Pull the thread towards the bobbin and pull it through the hole in thy bobbin inside-out. Place the threaded bobbin into the winder making sure the extra thread is on top an...

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Electical discharge machining is a techinque in which electricity is used to machine (cut, grind, etc.) metal. It usually invovles sophisticated tools and equipment, but not here! Watch this video for a guide to making a small electrical discharge machining machine with an old electric doorbell.

Spotify can be a really great music streaming program, but there's nothing like a loud, annoying ad to ruin your aural zen. With this video, you'll learn how to remove ads from Spotify in just a couple easy steps. When it comes to setting the Proxy, copy and paste the following:

Even if you never took home ec, you can create simple projects by learning the basics of sewing machine use.

Your sewing machine needs bobbin thread to create overlock stitches, so keep your machine going by learning to fill your bobbin.

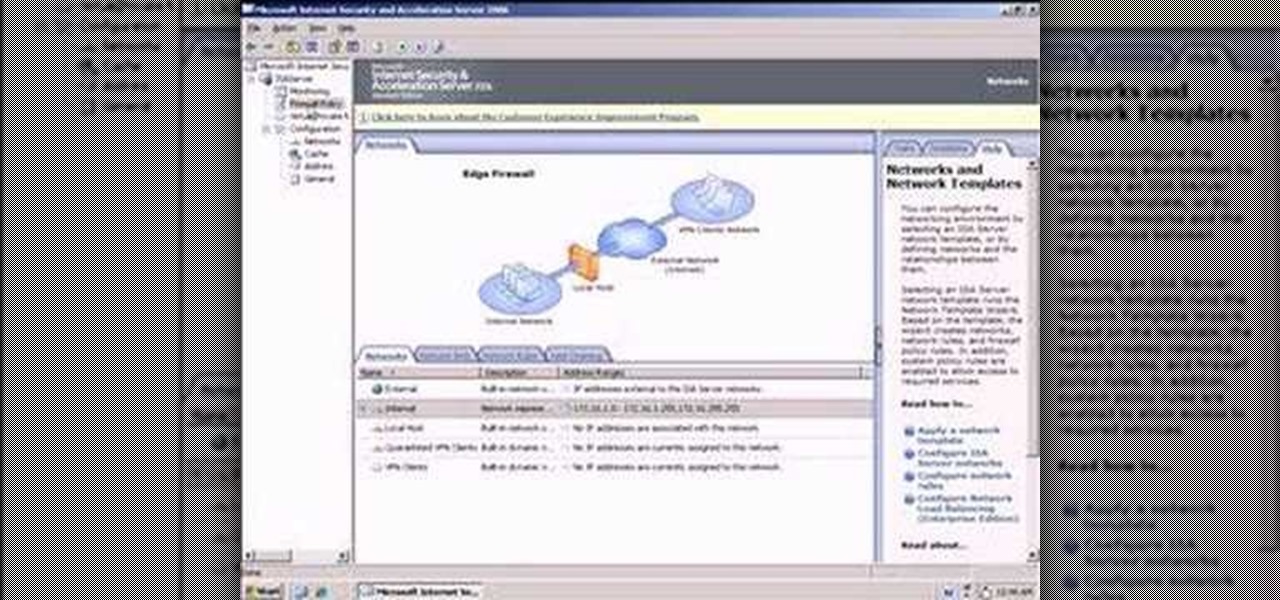
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

Save money by performing your own sewing machine maintenance! While there are differences between a Singer sewing machine, a Brother model or a Janome machine, there are many similarities. This video shows you how to maintain and clean the feed dog area on your sewing machine.

The Brother KH-930e knitting machine is an old but reliable device. It's age means that it doesn't like interfacing with modern computers though, so it's hard to get patterns from your computer to your machine so it will knit your project. Without this video it's hard, that is. Watch on to learn how to hack a Brother KH-930e to receive any pattern from your computer.

Old drum machines make some of the coolest sounds in modern music, but can be very hard to get used to for beginners. If you're lucky enough to have gotten your hands on a Roland TR-909 Rhythm Composer drum machine, watch this video to learn how to program it.

Are you tired of needing seperate synths and drum machines to create your drums and bass / lead lines? If you have a Korg MS-2000 and many other synthesizers, it's possible to program your synth to act like a 16-step drum machine while still being able to play bass and lead lines over the drums. Watch this video to learn how to do it.

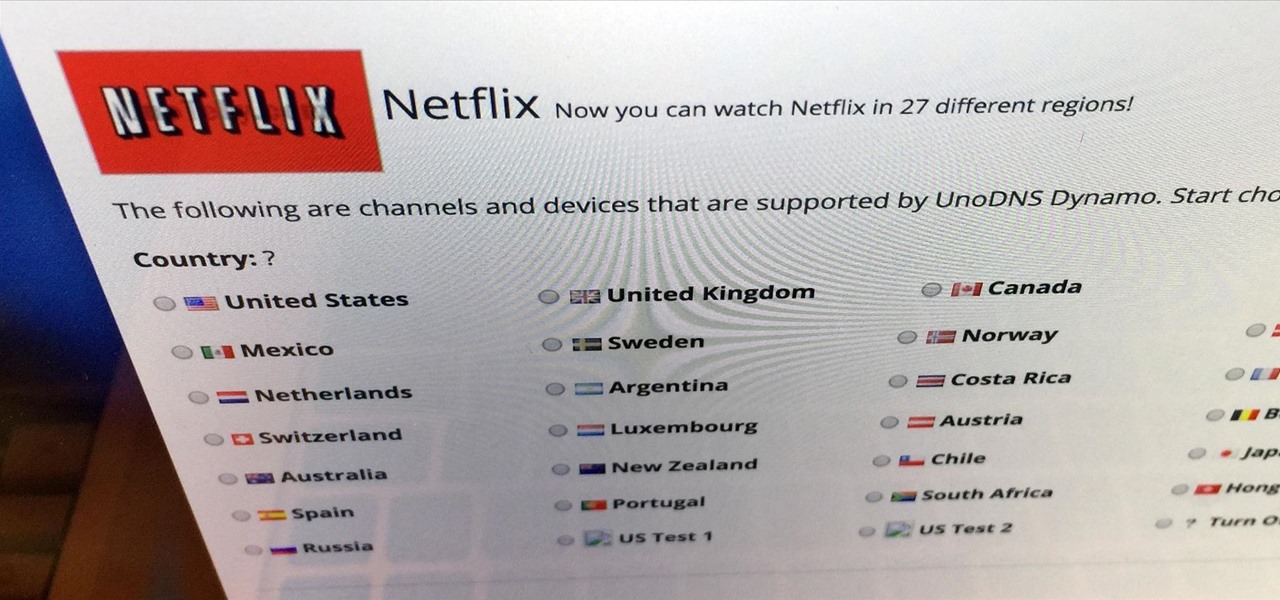
Netflix subscribers (or friends of subscribers) have been able to utilize a virtual private network (VPN) or proxy service to gain access to content in other countries. Unfortunately, the movie and TV streaming service announced today that it will soon block those services so that viewers will only have access to movies and shows that are licensed for the country they're currently in.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

iTunes Radio, Apple's answer to Pandora, provides endless hours of free music streaming, but like other so-called "free" services, every now and then you're going to hear some ads. While you may not be bombarded with them, they can definitely kill the vibe when you're jamming to your favorite stations.

Need to break out of the restrictions your school or workplace have on internet browsing? Maybe you want to waste some time on YouTube, check out some gaming action on Twitch, or simply just browse Facebook or Twitter.

Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine.

One of the most damaged parts of a washing machine can be the controls. This is an important part of the machine as it helps determine how much water is needed in the machine and how the clothes should be washed. This tutorial is going to show you how easy it can be to replace the controls on a Hotpoint machine. So check it out, be safe, and enjoy!

Check out this tutorial for a step by step on how to remove a washing machine motor. This is especially important if you need to fix your machine. Although the Ultimate Handyman is demonstrating on a HotPoint machine, this fix can be applied to most models.