Brandon Pinard discusses the most commonly used transitions in television and film: the Cut, the Fade and the Dissolve. He covers the basic definition of each of the three transitions, how they are most commonly used in the film and television industries, and how anyone can improve their own videos with the proper understanding of these transitions.

Film and television cinematographers love sliding camera shots, especially since ER made them a standard device for television dramas. A professional sliding camera setup is expensive though. Why not make one yourself? This video will show you how to turn $20 into a high-quality filmmaking tool that you can use to give your films some very professional-looking shots. Now get out there and follow that gurney with the camera!

At midnight on February 17, 2009, all full-power television stations in the United States will stop broadcasting in analog and switch to 100% digital broadcasting. Digital broadcasting promises to provide a clearer picture and more programming options and will free up airwaves for use by emergency responders.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

If you're not technologically savvy, don't stress. You probably want to jump right into the game, so check out this video on how to properly install your Playstation 3.

Google TV is a revolutionary new way to enjoy your two favorite things in life— Internet and TV. And Sony just happens to be the first company to design television products powered by Google, like their Internet TV Blu-ray Disc Player (Model NSZ-GT1). If you're thinking of getting one, this video provides a hands on, showing you how to use the new Sony Internet TV, paired with practically any television.

In this clip, you'll receive some tips on where to place your high-definition television for an optimum viewing distance. For a complete demonstration of the process and detailed, step-by-step instructions, watch this handy home-theatre how-to from the folks at CNET.

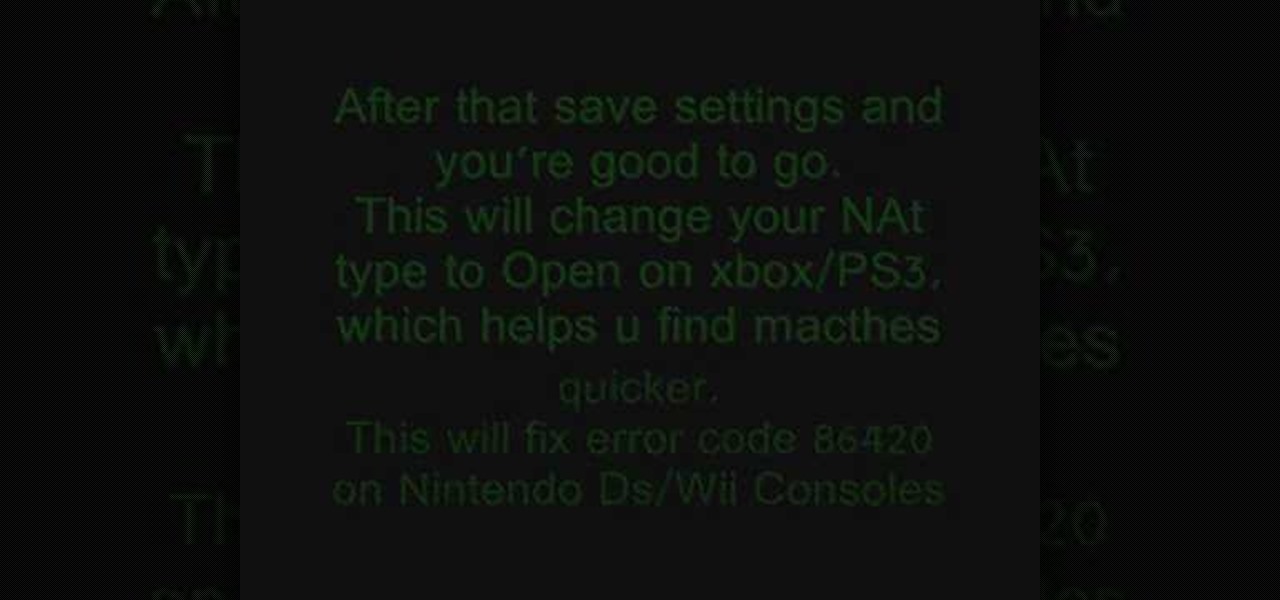
In this tutorial, we learn how to fix error code 86420 and change your NAT type to open. First, go to the website to change the settings for your Linksys router. Next, go to the applications tab that says "applications and gaming". After this, go to port range forwarding, then write in a name next to where it says "application name". Under "start" write the number 1 and under "end" write 6553, then keep "both" marked under protocol. Next, enter in the last 3 digits of your console's IP addres...

After announcing at Google I/O 2019 that augmented reality content would come to Search, Google revealed how it would make that happen with the latest round of updates to ARCore.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Watch this to see how to hookup a digital to analog television converter. When analog broadcasting ends in February 2009, you're either going to have to buy a new TV, pay for cable, or get a converter box.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

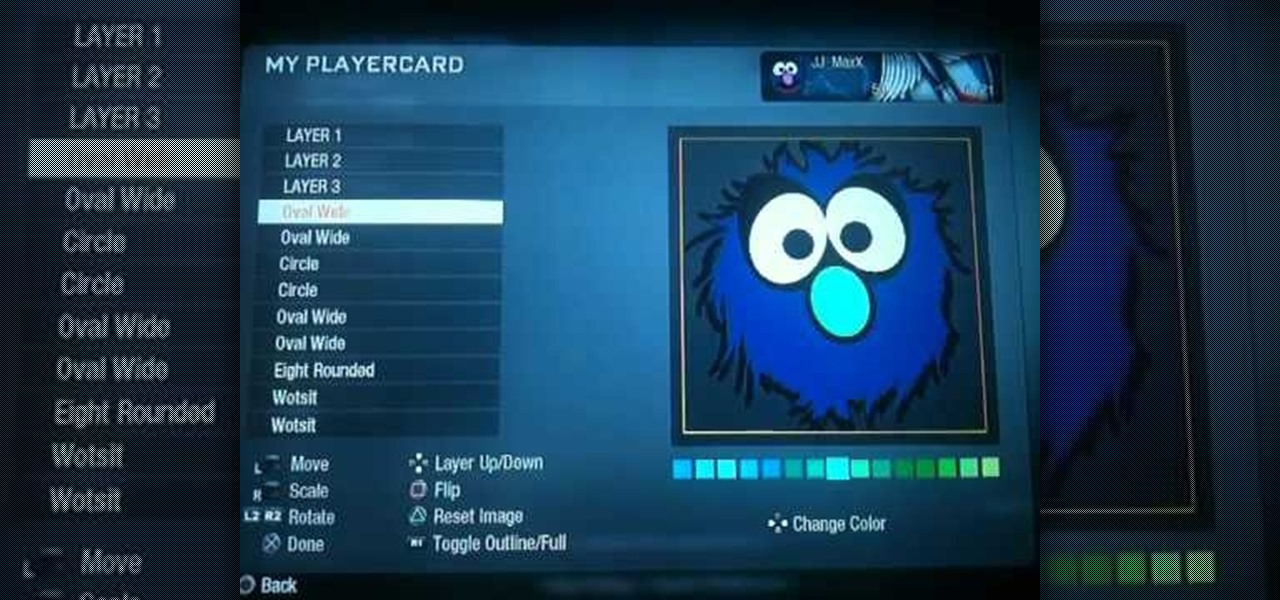
Sesame Street Muppets are beloved by the majority of American television-watching children, but Grover doesn't get as much love as some of the other Muppets like Big Bird and Elmo. Show him some love by making a Grover player card / emblem in Call of Duty Black Ops.

Snooki and her Jersey Shore castmates have taken over reality television, and for better or worse, their New Jersey-ness is spreading like wildfire. If you're thinking about dressing up as Snooki for Halloween, you've found the right video! It will show you how to get the right skin tone, makeup, hairstyle, and the iconic rhinestone sunglasses to make your Nicole Polizzi costume as awesome as possible.

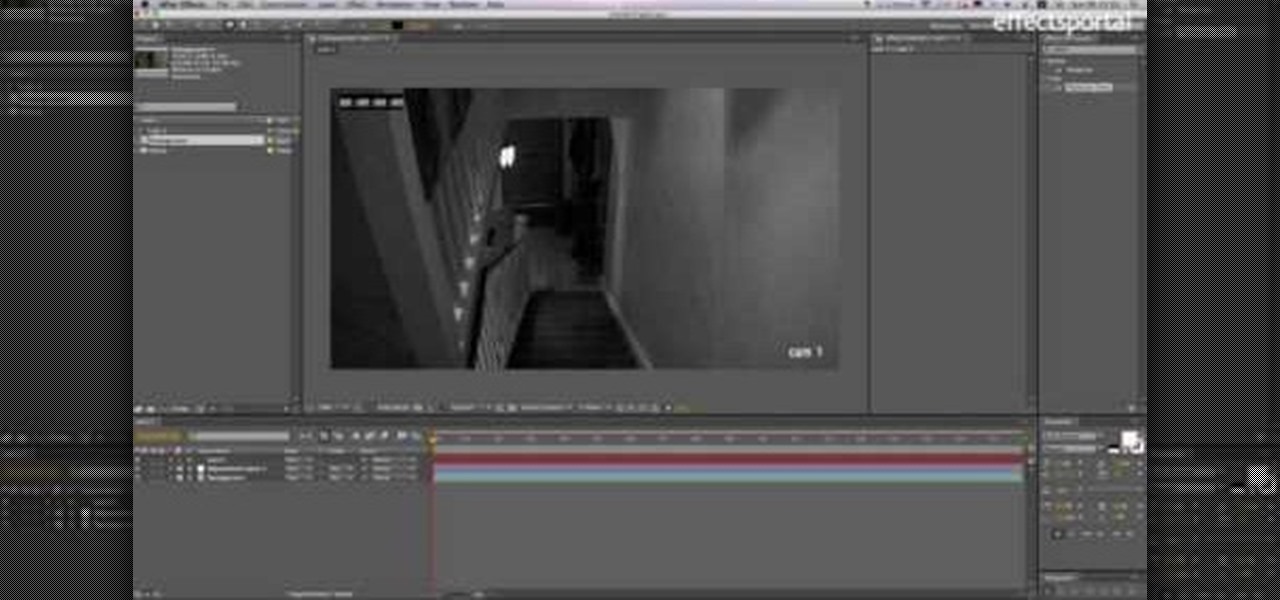
CCTV's (closed-circuit televisions) are more common than ever before, and have become more and more popular to depict in films and in video games like Manhunt. This video will teach you how to create a CCTV monitor effect akin to what a security guard would see on their camera monitor using After Effects. This will work great for any horror movie that you might be shooting, the effect is very creepy.

Ever daydream about making your own comic strip? Well, what's stopping you? With this lesson from television cartoonist Bruce Blitz, you'll learn everything you need to know to produce your very own comic strip suitable for publication in a newspaper or on the web. For more information, and to get started making your very own funny strips, watch this free video guide.

As on an iPhone, iPod touch or desktop computer, you can use Apple's iTunes store on your iPad via the free iTunes application. Learn how to wirelessly download movies, television shows and songs to your iPad with this official video guide.

John Park poses a kitty conundrum: Who's going to feed the cat while you're on vacation? Using a motor from an old VCR, he creates an automated feline feeder. While building this Make: magazine project, John learned that newer VCRs have safeguard technology, limiting access to the motor. Watch John as he demonstrates his solutions to this challenge.

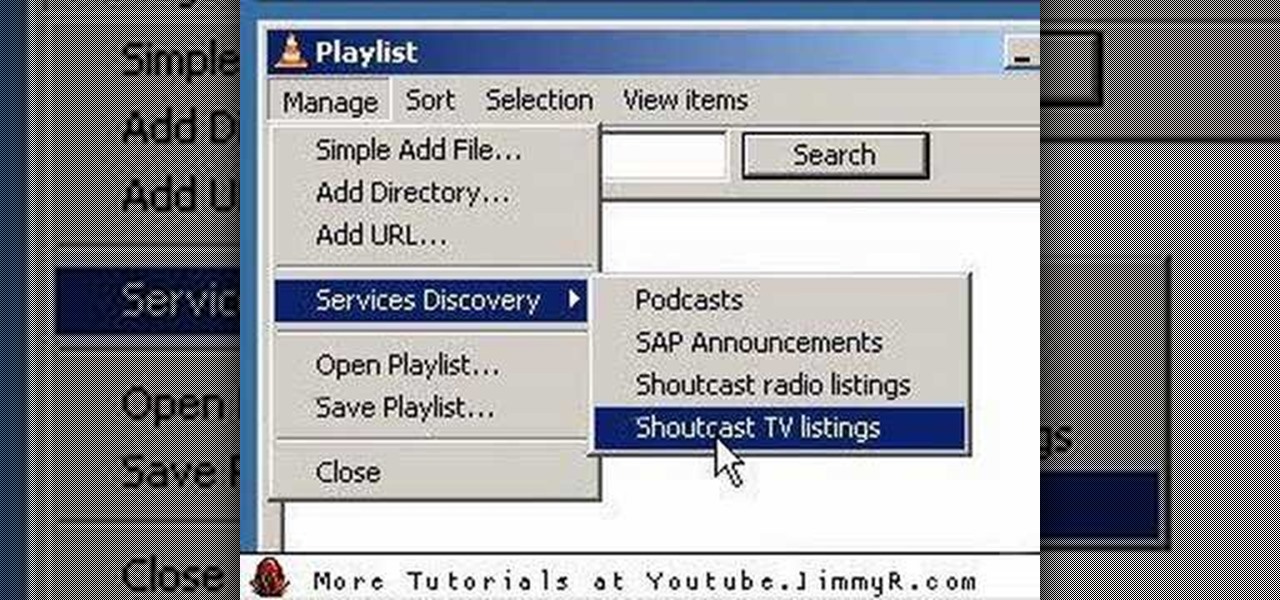
A video tutorial on how to get free streaming TV and radio using the VLC media player. A simple one click procedure to get free streaming television and radio.

AntiPolygraph.org's George Maschke speaks with Nick Frost about how to fool a polygraph (lie detector) test in episode 5 of the tongue-in-cheek 2003 television series Danger: Incoming Attack. Note that the anal sphincter contraction, discussed as a polygraph countermeasure, while effective, is no longer recommended by AntiPolygraph.org, and alternative techniques such as mental countermeasures or tongue-biting are to be preferred.

In this video, we learn how to connect a computer to an HDTV using an HDMI cable. Start out by plugging your HDMI blue port in the back of your computer monitor. Also, plug in a yellow DVI to HDMI converted with a cable connected to this. You can buy these on Amazon or New Egg for only a few dollars, get the generic version. After you have these plugged in, it's as simple as that. Plug these into the back of your television, then use your computer. You will now see the screen of your computer...

In this tutorial, we learn how to watch movies and TV online for free. You can do this through the website Hulu. This is a completely legal website, and you can either sign up for an account or just browse the site. You can watch movies and television shows through here, they have a large selection. They also have a great variety of different short clips for different shows. The player on the website has dimmer switches and full screen mode as well. This is a great website if you want a legal...

Want to watch Internet television on your television? It can be done! And this home theatre how-to from the folks at CNET TV will show you how to do just that, integrating by integrating a Windows PC into your home entertainment center. For more information, including detailed instructions, and to get started using the Internet on your own TV, watch this free video tutorial.

This is an interesting video where the presenter demonstrates how to actually play your iPod on your television by utilizing connectivity with XBox360. The great thing about this video is you actually see how the cables connect between the devices. Once connected, a brief tutorial of how to configure the dashboard follows. It's amazing how, with the right cables, one can quickly have use of their iPod on the television. The video itself is less than 90 seconds long, so you get a great tip for...

Make a Magician's Mask Have you ever heard of the Masked Magician? With the television series Magic's Biggest Secrets Finally Revealed, the so-called Masked Magician (Val Valentino) revealed secret after secret of the magicians repertoire. Valentino creates “the magic” then proceeds to reveal the reality of the illusions before a captivated television audience.

One you understand how a subnetwork works on an Internet Protocol (IP) network, creating one becomes very easy. In this five-part video, you'll learn about IP address and subnets, along with creating an IPv4 (IP version 4) address using Class C, which leaves each network with 256 local addresses. If you're new to subnetting, this is where you start!

Online shopping giant Shopify literally cannot wait for ARKit 2.0 to arrive via iOS 12 this fall to implement its latest augmented reality feature.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

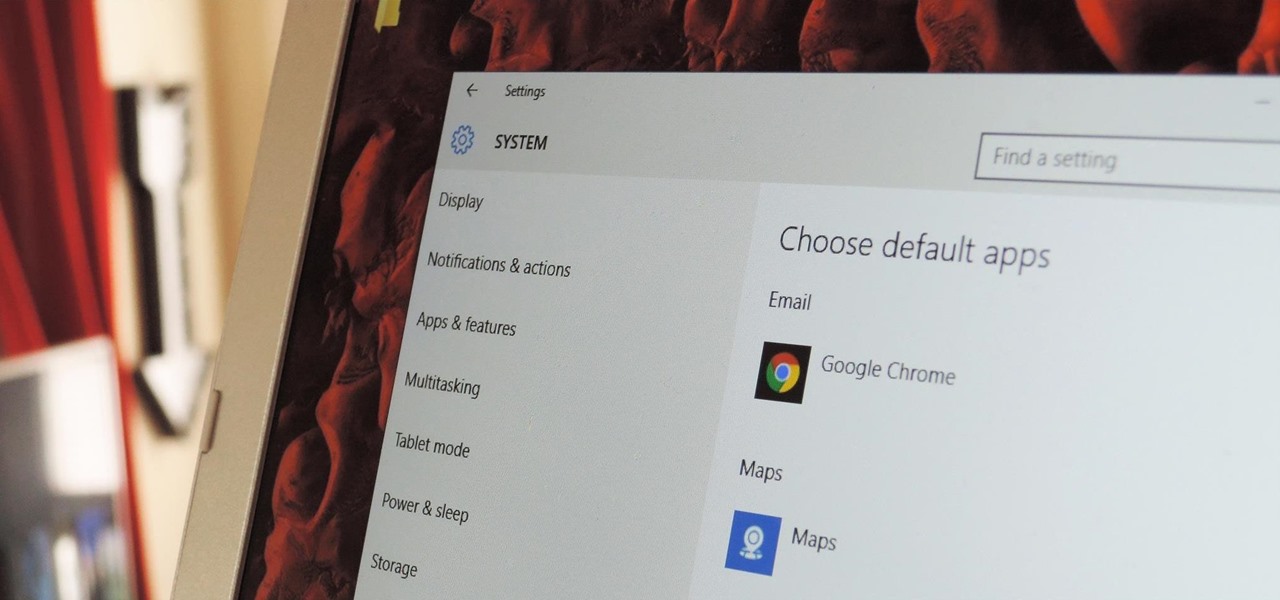
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

Similar to the feature that lets you dim the light on your PS4's DualShock controller, your Playstation 4 is filled with useful tricks that you may not know about, especially when all you want to do is pick up and play. One of these useful tricks is the ability to turn your TV on using the PS4 controller.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

T-Mobile's "Uncarrier" initiative has done wonders for my wallet and my data usage. Before I had to deal with being throttled down to 2G speeds after passing my data limit, but thanks to their unlimited data plans, I'm free to use as much LTE data as I possibly can. The only downside is, when sharing data through a mobile hotspot (tethering), T-Mobile imposes a 5 GB limit (which was recently upped to 7 GB for some).

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The problem with striving to be on the bleeding edge of what's new for your smartphone, or really anything else in life, is having to constantly check websites and forums for new content. And with lots of that browsing happening on our phones, the aimless page loading and refreshing is not just annoying when there isn't new content, but can lead to wasted data usage, not to mention time.