Believe it or not, there are a variety of ways to customize app icons in iOS. While iOS 12 made gave us an unofficial built-in way to do it, and iOS 13 improved it, and iOS 14 made it the best it could possibly be, there's still another option if you don't like using the Shortcuts app.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.
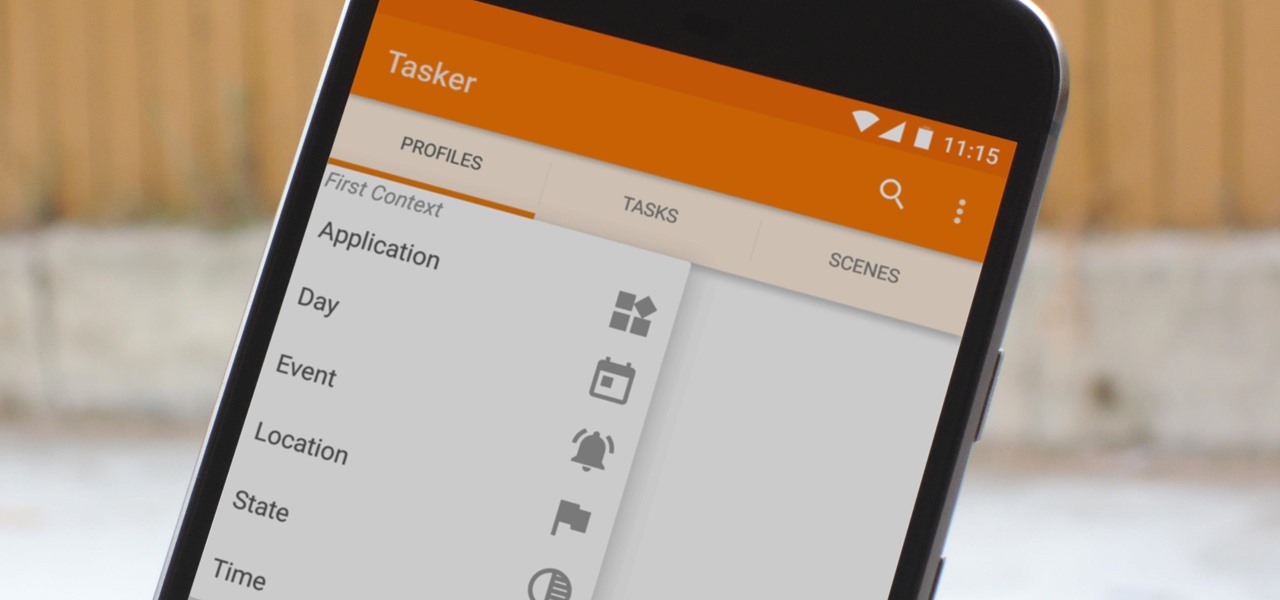
When you hear people say that Android is more flexible than iOS, it's because of things like Tasker. You can do virtually anything with the venerable automation tool, from saving battery life to controlling your smart home with your fingerprint. But before you get to that, you'll need a good understanding of all the basics.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

While there are many ways to see the exact battery life left on your iPhone, you can take all the work out of it by making your iPhone verbally tell you the current percentage every time you start or stop charging it. Best of all, this trick works whether you use wired or wireless chargers.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

If you're doing the same tasks on your Android phone repeatedly each day — like playing a specific playlist at the gym, viewing work documents, or watching your favorite music video — you can save some time by automating your routine, turning each task into a one-tap gesture on your home screen.

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to go up a level in MyBrute with Cheat Engine 5.5 (09/09/09).

This scorpion toy was constructed by Make Magazine with a Twitchie Robot Kit. If you're afraid of real life scorpions this friendly toy might help you get used to them. His plush body is made from some fabric aiming to make him look like an Arizona bark scorpion, which are tan/yellowish/translucent. Twitchie is Arduino powered and comes pre-programmed, so it's an excellent kit for beginners in robotics, because no programming is required! You can download and modify the code if you want, and ...

Dr. Aris Latham suggests setting standard plans for breaking a fast for most of people that he interacts with because the animal body has been programmed to eat in a certain way. This is necessary to train your body well so as to survive and be healthy. Divide your day into 3 equal parts of 8 hours. Take the sleep part of the day where you deal with the waste in your body and create energy within the body. The next period when you get up is basically when you break your fast when your were sl...

The first day of Hanukkah is here, the day you start lighting the candles of the menorah. So, why not ditch the wax and light the "lights" this year?

Watch this instructional video brought to you by Nikon's Digitutor to learn how to operate the Nikon D80. This Nikon D80 video tutorial demonstrates how to use different solutions for various shooting situations, search from control panel, search from viewfinder, use the caerma body: front, top, back, maulti selector and mode dial, attach a lens, insert the battery, set the time and date, insert a memory card, format a memory card, adjust the viewfinder focus, use different shooting modes suc...

Microsoft's new mobile operating system is officially out on the market, and programmers are hard at work developing new mobile apps for Windows Phone 7 devices. But there's a lot going on in this new platform, which means there's a whole lot to be learned, and the only man in the world with a Windows tattoo is here to help— Charles Petzold.

This beginner's guide is designed for people with little or no prior knowledge of computer languages, who want to learn to program by using the Visual Basic language. If you have some previous programming experience, maybe in another language or from a few years ago, then you may also find this guide useful. Whether or not you have programmed before, you should already be familiar with computers before reading this guide. It assumes that you can perform simple tasks like starting a program, a...

So you've found yourself opting to be a vegetarian. The transition into a new way of eating and living is not always easy and as a result people often ditch their vegetarian goals and revert back to their previous eating habits. Here are some steps to ensure a successful transition to vegetarianism:

It's more addictive than Angry Birds, perhaps as relaxing as transcendental meditation, and satisfyingly simpler than GarageBand. It's Otomata, a newly programmed generative sequencer designed by Batuhan Bozkurt, a Turkish sound artist, computer programmer, and performer. But really, it's best described as an audio/visual music toy that anybody can play online—with beautiful results.

Very cool project by Benjamin Gaulon. Gaulon has created a graffiti writing paintball robot, entitled PrintBall. He uses technology from (previously posted) EyeWriter to tag with his eyes, plastering a wall with paintballs.

These soccer playing robots from TU Freiberg Robotics are programmed using Knesthetic Bootstrapping, which control the Bioloid's motions. Players can send commands to the soccer bots via Wii Remotes, and users abroad can control them directly online. If soccer's not your game, robots can play chess, too.

What can I say—it's amazing. Loaded with over 350 LEDs in a matrix, this Daft Punk helmet simply radiates awesomeness. Made by Harrison Krix of Volpin Props, this DIY project took four months to build (much shorter than his last helmet of 17 months).

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Since the early genesis of the brilliant Microsoft Kinect hack, inventive applications have been popping up nonstop. One of the most fascinating projects to surface recently falls within the realm of 3D printing. "Fabricate Yourself"—a hack presented at the Tangible, Embedded and Embodied Interaction Conference in January—allows users to pose in front of an Xbox Kinect, which then converts a captured image into a 3D printable file. What does this mean exactly? Think Han Solo trapped in carbon...

Engineer-turned-artist Jim Campbell's recent installation "Scattered Light" converts New York City's Madison Square Park into a ghostly world of light bulb pixels. Campbell dangled 2,000 floating LED light bulbs programmed to display shadowy human silhouettes passing by.

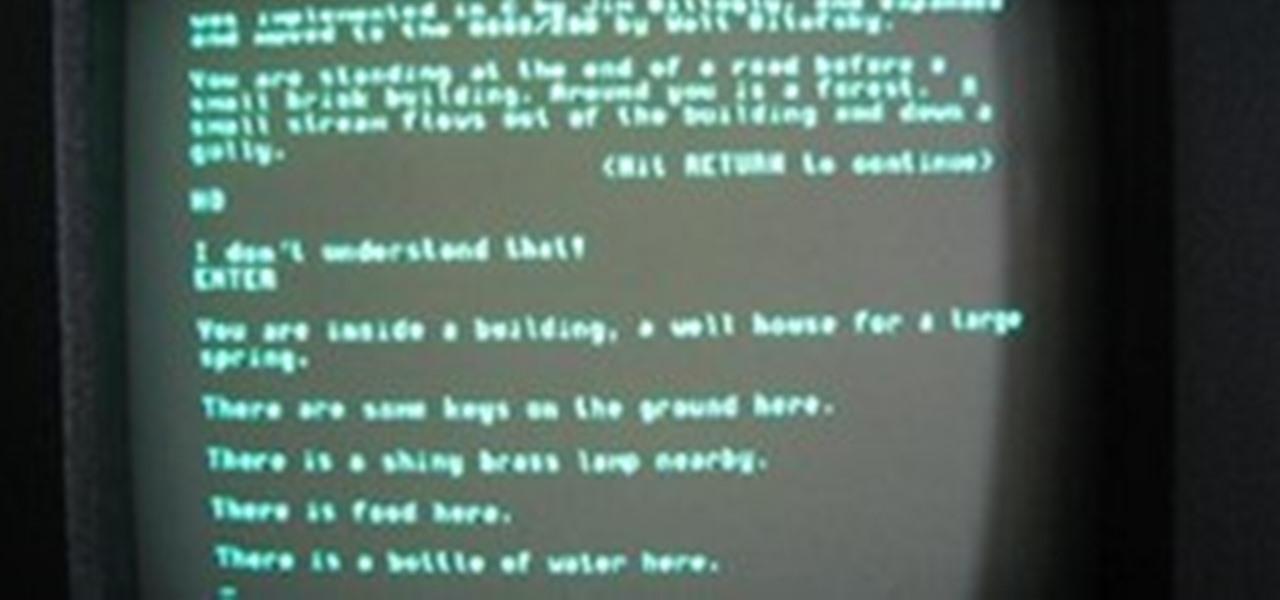
Adventure gamers would love to know what was the first adventure game. Well, it was a 1970s computer game titled "Colossal Cave Adventure", also known as "Adventure". Designed by Will Crowther, the game was in FORTRAN and initially had 700 lines of code and data, which was later expanded to 3,000 lines of code and more than 1000 lines of data.
You may be familiar with the general layout of 3ds Max 8's user interface, but a few of version 8's interface features aren't readily apparent to new users. They are, however, critical if you want to navigate quickly in 3D space. The goal of this chapter isn't to show you the nuts and bolts of the interface, but rather to introduce you to a few of these fundamental features that will enhance your productivity.

My mind is playing tricks on me! Discover Magazine systematically dissects five fantastic optical illusions. The scientific explanations are logical:

Graffiti with your eyes, or let your robot do the work for you. Via Flong,

Just like magic - incredible new project from Sweatshoppe in which video is "painted" onto a wall. Video demonstration below, (don't miss it! absolutely visually amazing).

Beginning this week, Null Byte will be hosting a new feature called Community Byte, a weekly coding and hacking session held in the Null Byte IRC. This is a chance for our community to do something fun, and make something awesome together!

No matter if you've used one or not, you've got to admit that 3D printers are pretty darn awesome, especially the self-replicating ones that extrude molten plastic and the shoebox-sized versions that use mesmerizing stereolithography to build tiny objects layer by layer. But what's even cooler? A solar-powered printer that uses the sun's energy to melt sand and make 3D objects out of glass.

Soft focus photography can produce some beautiful images when used properly. It's used a lot in beauty and glamour shots, but can be applied to other types of photos as well. Some digital cameras have pre-programmed settings for soft focus shots, but if you're using a DSLR, you'll need a special lens or filter to do it.