A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.
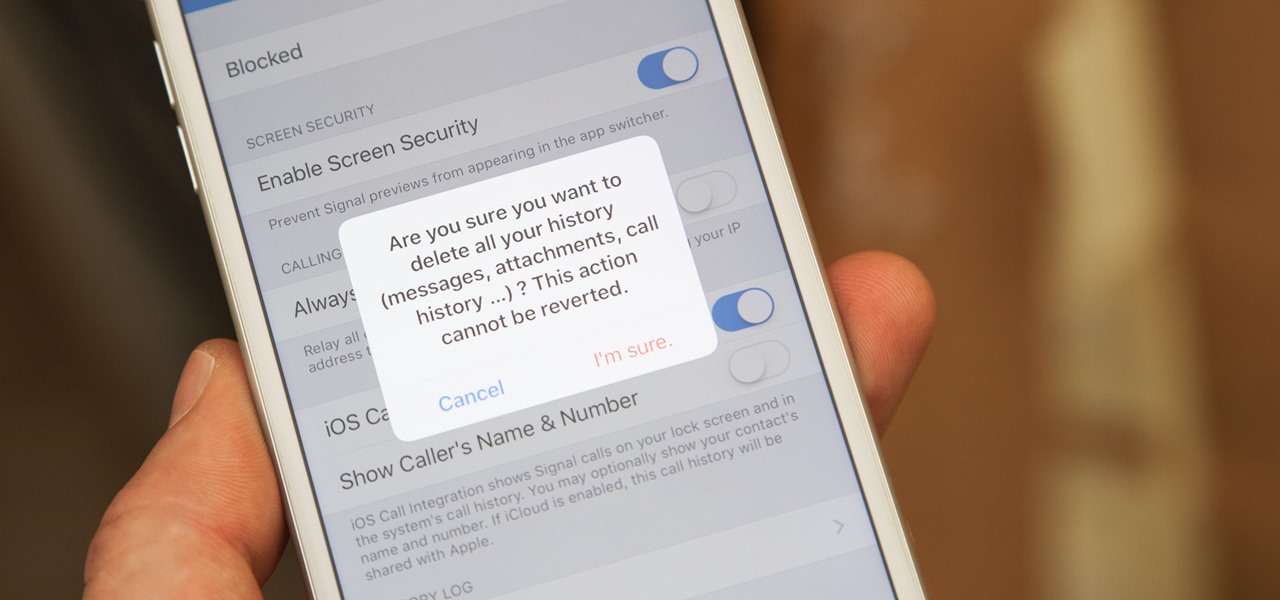
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

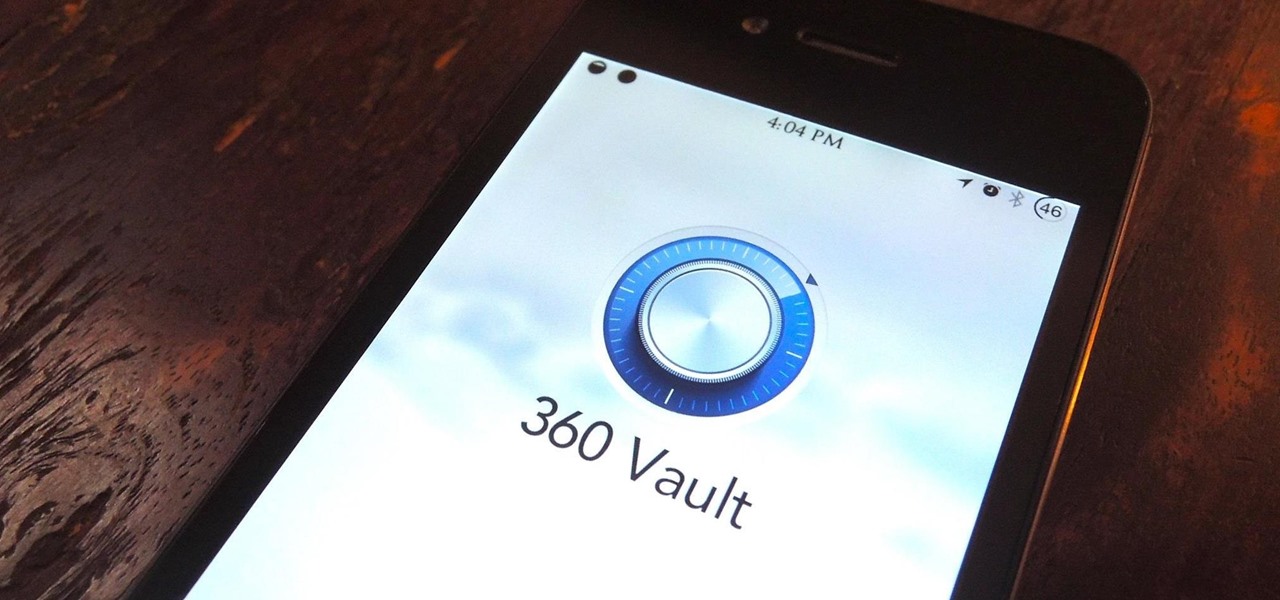
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

To get the "Hail Mary" achievement on Read Dead Redemption, it's going to be quite a challenge. This is almost impossible to do while standing on flat ground, but it is possible.

This achievement can be earned on the Outlaw to the End downloadable cooperative mission in Read Dead Redemption. To get the Dodge This achievement, start a private match with a friend on the Herd mission. Once the mission starts, select the bolt action rifle and the rolling black rifle. Use the bolt action as your primary weapon, and shoot the TNT crate next to the tent on the righthand side. Quickly switch over to your rolling black rifle. Have your teammate use one of the repeaters to weak...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

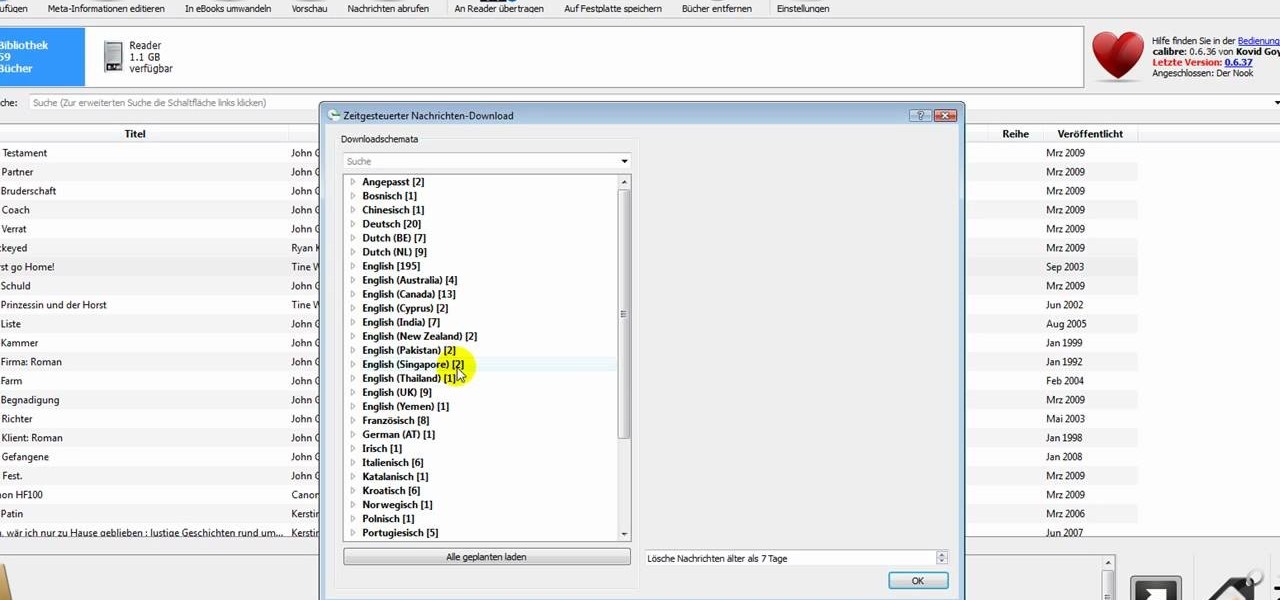
In this clip, learn how to add your own personal files to your Barnes and Noble Nook and make it a portable carrying device. This tutorial will show you all the steps you need to get anything from photos, videos, music files and personal documents onto your e-reader. This process is pretty easy and once you view the clip, you should be all set to start side loading. Who needs an iPad when you have a Nook?

In this video, presented by the experts at the St. Louis Community Credit Union, learn how to prevent thieves from stealing your identity or account information. These days, between paper bills, Internet banking, social networking and all the other ways we interact, there are many ways for crooks to get into our private lives.

When conducting mobile convert surveillance, you will be following someone and it is important to dress appropriately for the environment and carry your surveillance equipment in a bag that will fit into the scene.

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

Have you ever had to close an application with private info in order to let someone else use your PC? LockThis! is a windows application that lets you secure individual programs without the hassle of having to save your progress and closing the program. To use LockThis! just hold the control key and click on the application that needs to be locked and simply enter your password on the dialog that pops up and your done. Now anyone can use your pc without you having to look over their shoulder....

Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

In this video, we learn how to clear Firefox location bar and browsing history. To get rid of an individual one, use your keyboard to go to the one you don't want. Then, press shift+delete and that one will be deleted. To remove them all, go to tools then click on "clear private data". Check the box of the browsing history, then click on the button to clear all the data. If you still have items in the list on your browser, then that means you have those websites bookmarked. To remove those, y...

Matches may not be the ubiquitous part of every person's going-out equipment that they once were, but they are still useful both for lighting fire if you don't have a lighter and for pulling these two hilarious bar pranks. The first is a simple counting game where you manipulate your victim into making piles of matches of sizes you guess correctly, because you rigged the game. The second involves challenging the victim to make six equal half of eleven using a pile of matches. Both are funny, ...

Do you have something important that you want to hide from your parents or friends? Well, then check out this tutorial. In this video, you will learn how to take an ordinary Pepsi bottle and turn it into a secret stash box. Because the bottle is see-through, no one will ever suspect there is something inside of it.

In this Computers & Programming video tutorial you will learn how to hide and lock folders in Windows. When you want a private folder that you don’t want any one else to open and see. You will need this feature. For this open a new folder. Open the folder, right click on it and go to ‘customize’. Then select ‘change icon, click on a blank icon, click OK and ‘apply. Now you will see that your folder icon on the desk top will disappear; only the name will be visible. Now rename it with a small ...

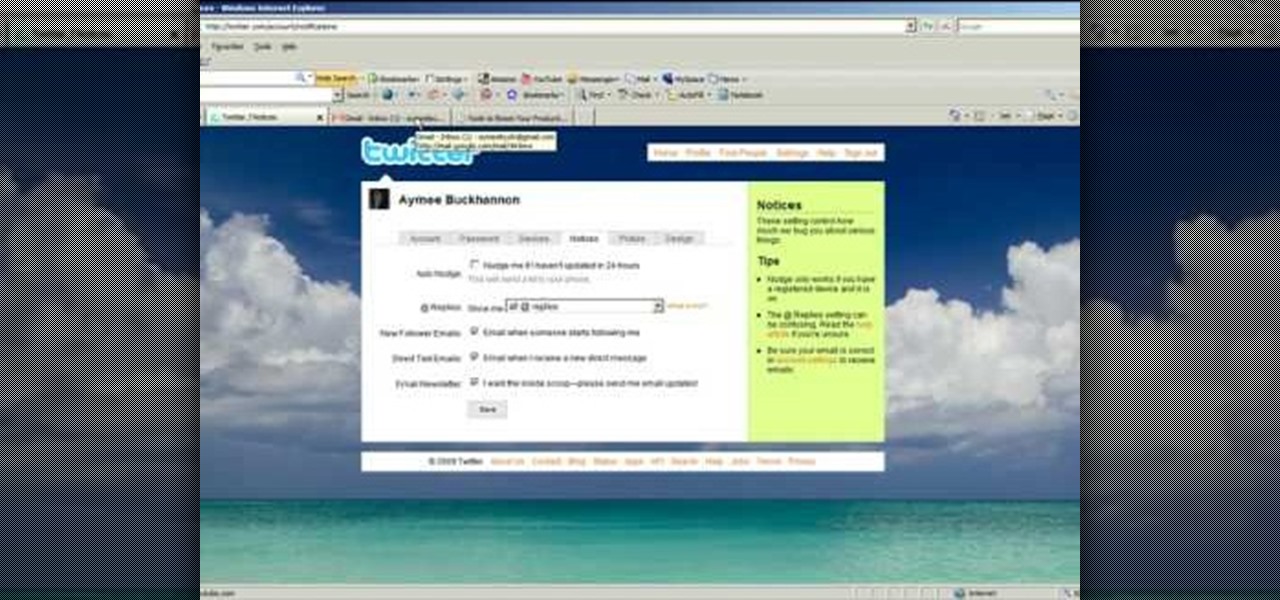
Twitter is the latest popular social networking forum. Twitter is used to keep your friends updated with what you are doing using 140 character messages called tweets. In twitter you can follow your friends and you will be notified when ever your friends posts a new message. Similarly other people can follow you on twitter to know what you are doing. In twitter you can customize to send an automatic private response to your new followers. To do this open your twitter account. Go to the notice...

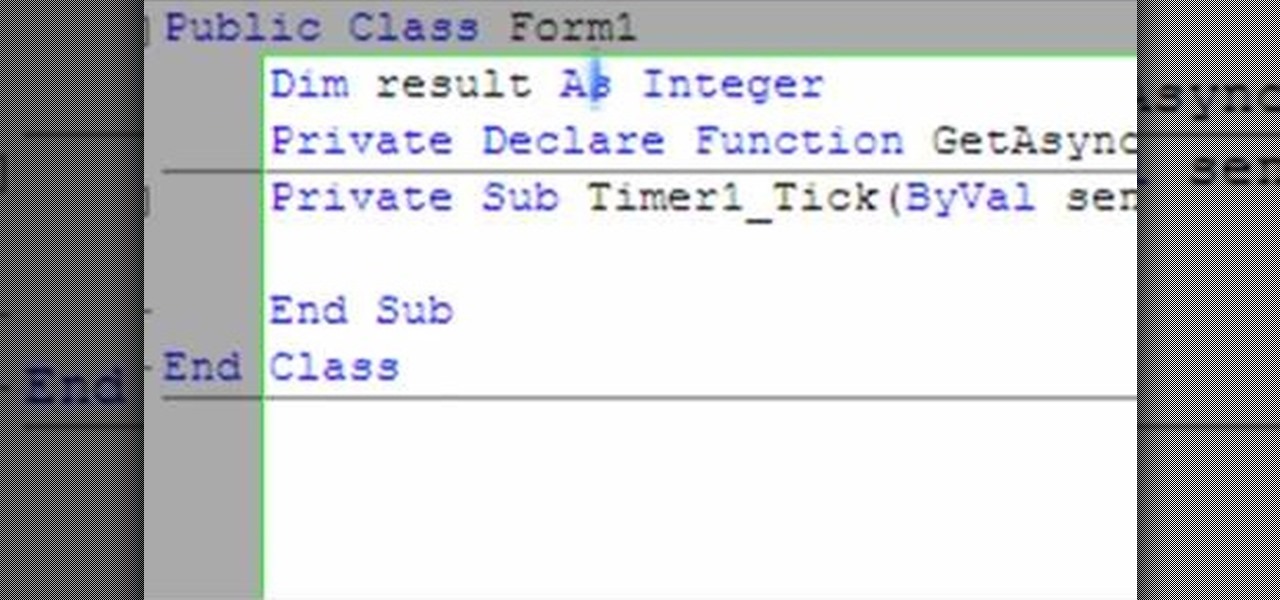
The following video shows how you can make a keylogger in Visual Basic 2008. Follow the steps below to create your own keylogger. First you will want to open a new application and name it according to your preferences. Then you want to click on the toolbar button and click textbox. In the textbox values, you will want to select the value of true for 'Multiline' option and the value of True for 'Read only'. On the toolbar, select the 'Behavior' tab and mark it as 'Window'. Go back on to the ma...

Pilates is fantastic exercise. If you are a beginner, though, it can be confusing to choose the right type of class. Check out this tutorial before you head to the studio and ensure you get the most out of your exercise routine.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Two characters from the popular sci-fi animated comedy Rick and Morty have already made their way into augmented reality courtesy of ARKit experiments. Now, it's possible to become one of them on the iPhone X.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

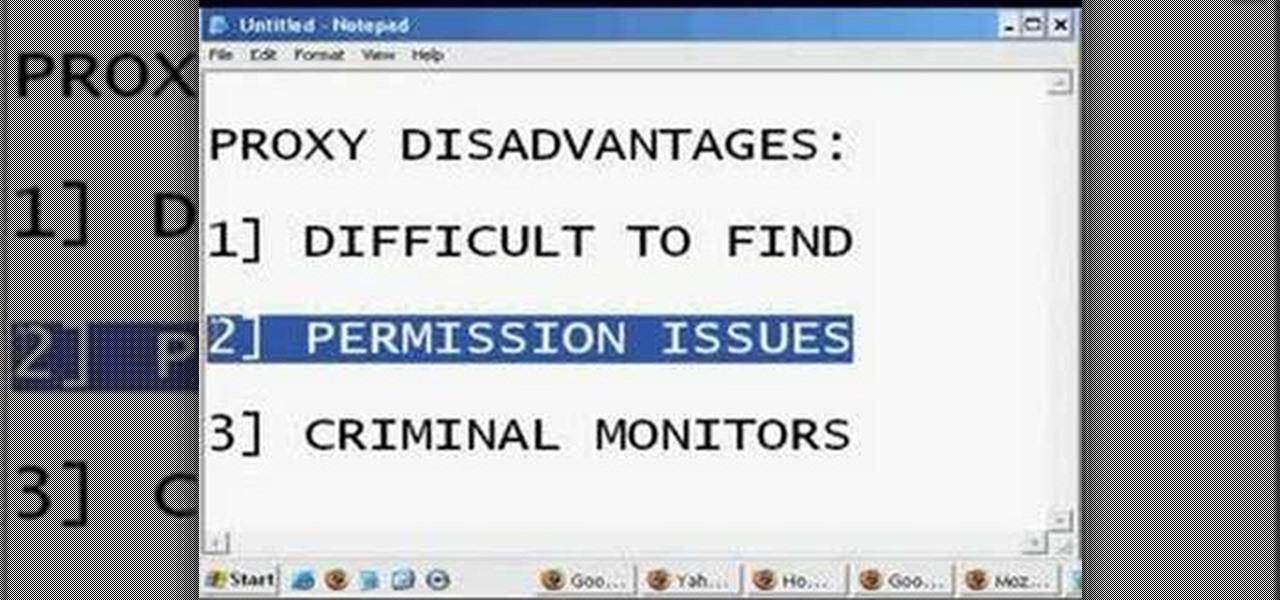
In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...