Ah, butter—the (literally) heart-stopping star of the dairy world. Everything tastes better with it, from pie crusts and cookies to veggies and steaks. Hell, you can even fry things in butter if you want the best-tasting fried foods of your (short) life.

If your iPhone has a Home button, such as either iPhone SE model, old or new, then it has a secret triple-click gesture to activate a suite of shortcuts. These options, dubbed accessibility shortcuts, can work wonders for folks that are hearing impaired, have limited use of their hands, or have vision problems. Still, the shortcuts have plenty of everyday applications that everyone should know.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

No matter what device you have, Android lag will get you down. It's our little green robot's only major downside, and you've probably noticed it quite a bit on your Nexus 7 tablet. Apps open slowly, actions stutter or pause, and loading files takes forever.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

Before I really get into this article, it's important to note that you do not need a Steampunk persona (or "steamsona") in order to be a Steampunk, or wear Steampunk clothes. Some people like to pretend to be a different person when dressed up in Steampunk clothing, but that is entirely optional, and only to be done if it appeals to you. That said, even if you aren't actually acting as your character, it may still be helpful to have one in mind when putting together an outfit. Personally, I'v...

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Pretend you're a phone thief for a moment. You might be a pickpocket or a stickup kid, but you're in possession of other people's phones on a regular basis. Now ask yourself this: what's the first thing you do after you steal a phone?

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

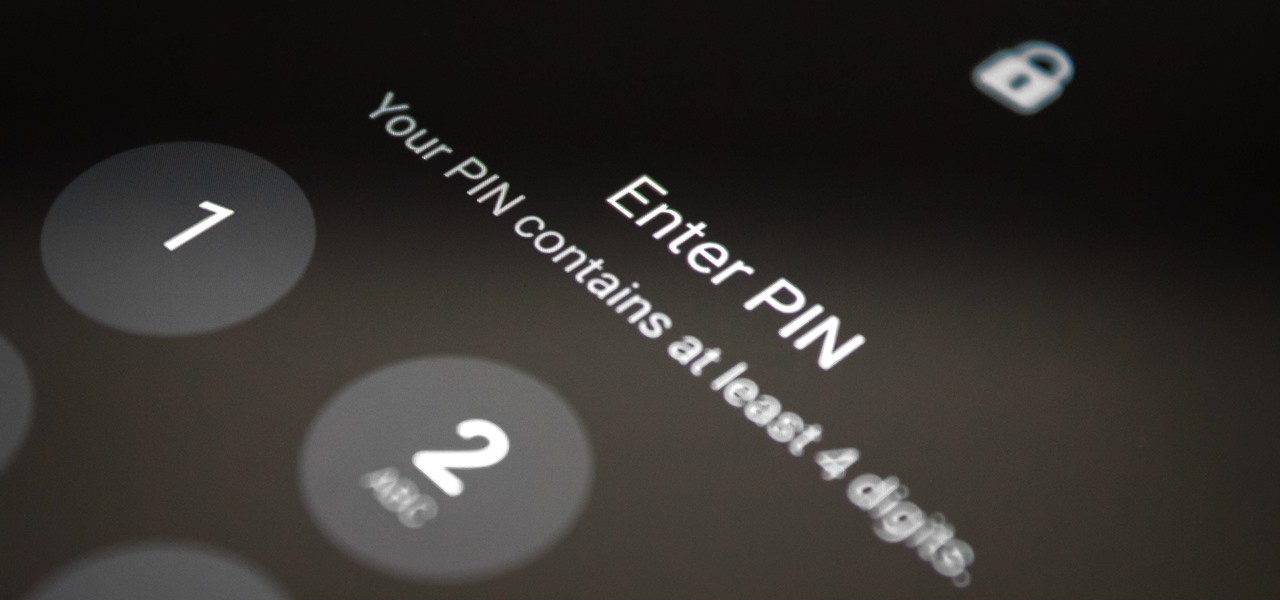
For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

If you want to make clothes for your cat, you're on your own. As I recently said in this article, cats will just totally flip out if you make them wear things. Your dog may also flip out, but I've found them to be more tolerant, personally.

While I am a writer with a degree in Creative Writing, I haven't published any Steampunk fiction. However, as a panelist and track director, I've been on panels with many well-known Steampunk writers and have gleaned insight from the things they've said. I've compiled some of those things into this post, which will hopefully be helpful to all of the writers out there!

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

The face tracking of cats and dogs are probably my favorite AR innovations that have come to Snapchat Lenses over the past few years.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

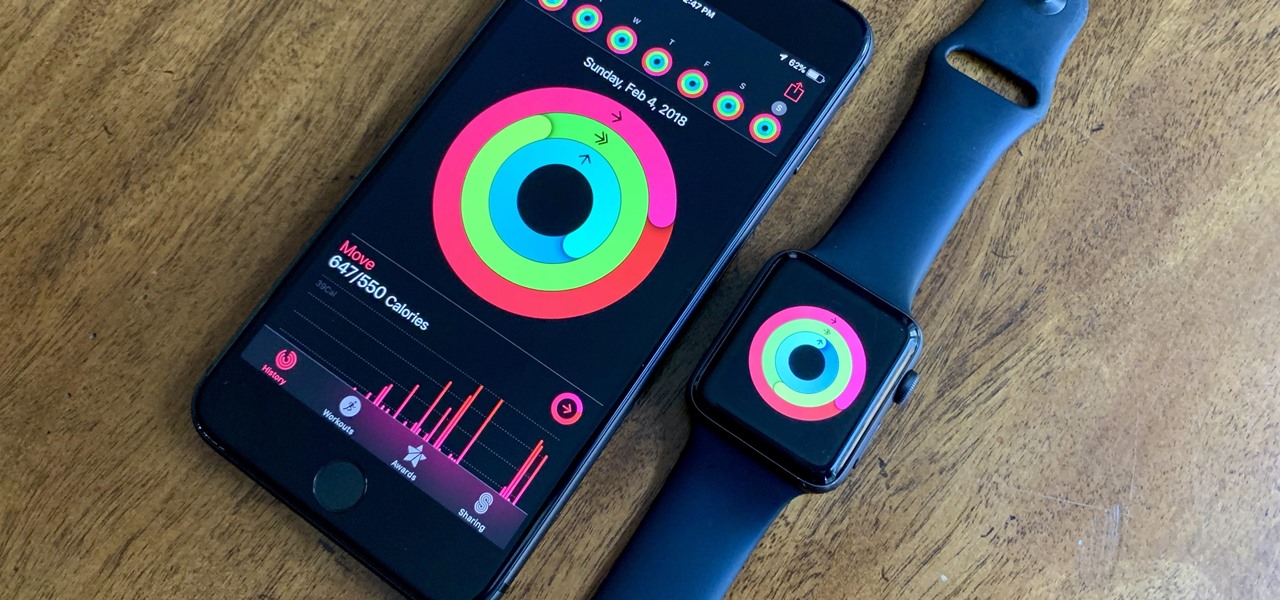
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.