SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.
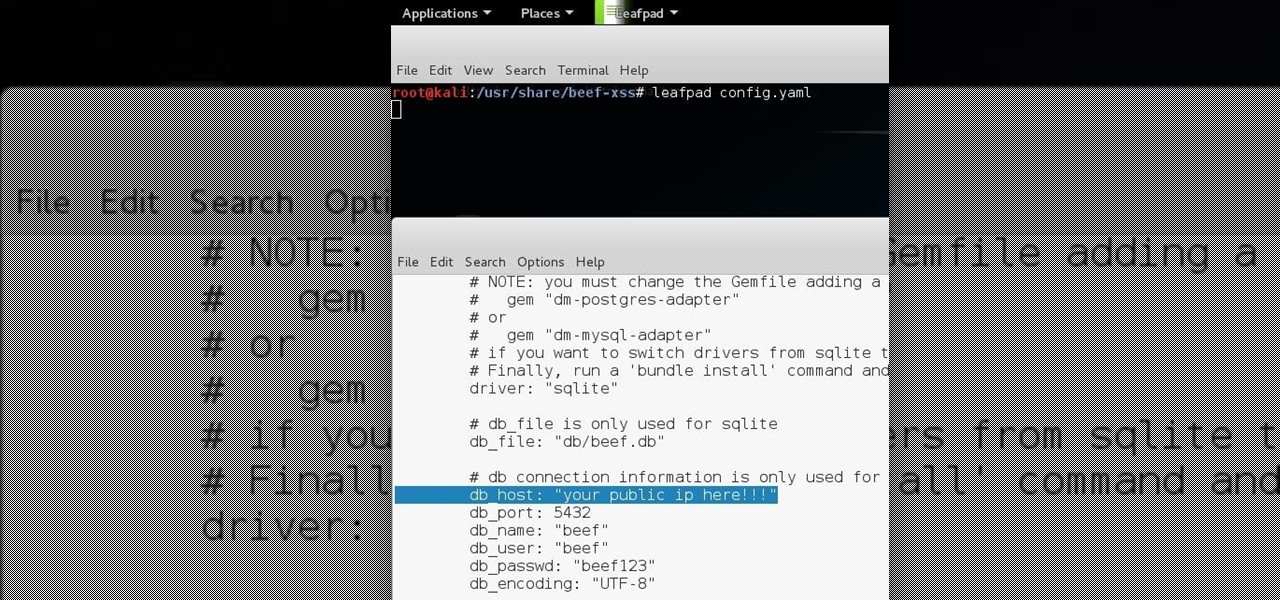
Hello all Just thought id share how ive managed to get beef working over the internet.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.
Macheads demonstrates how to install wine on mac. What is wine? Wine allows you to run and install windows program on Intel based machine. This program will work only on Intel and wont work on power PCs,unfortunately. First, we have to install macports which is something similar to installing unix programs on mac. The following are a bunch of requirements in order to install wine - an intel mac, admin account, X code installed, X11 (which comes mostly with intel macs). First of all we have to...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Hook up your TiVo, Xbox and other television-based electronics to a single HDMI port. All you need is a switcher, which you can buy easily for around fourteen dollars. Then hook it up, and have multiple input devices attached to your TV!

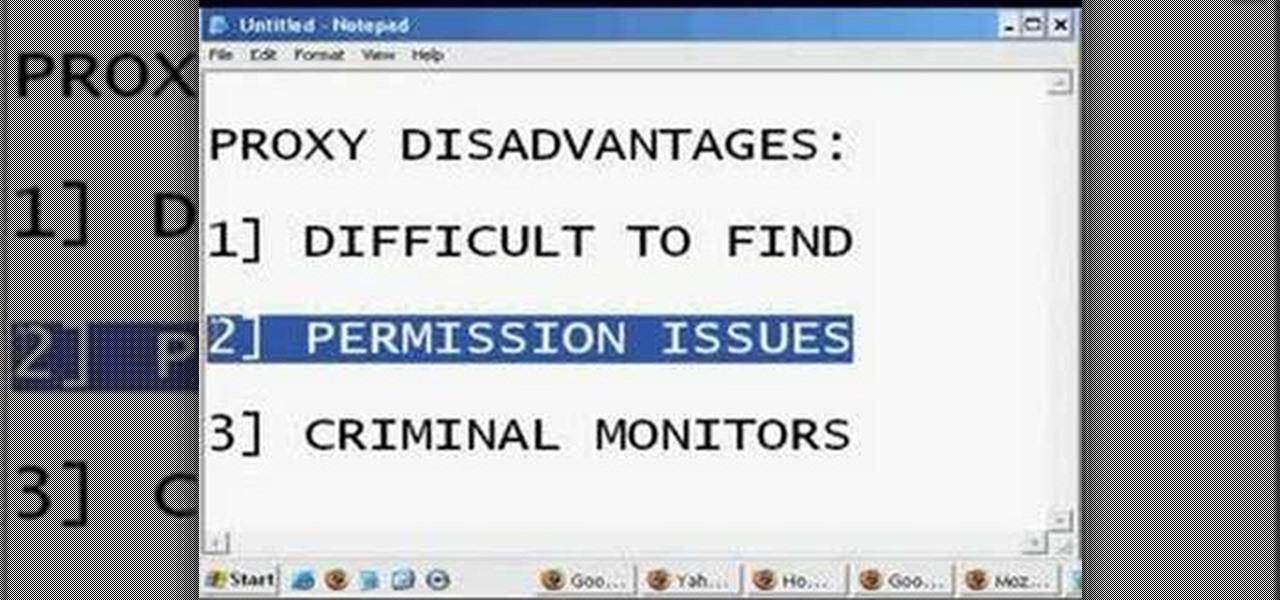
In this tutorial, we learn how to remove the ads from Spotify. First, you will need a proxy, which you can get from the website: Proxylist. Just simply click on a free proxy once you get to the site, then write down the proxy and port. Next, go to edit, then preferences. After this, change the auto-detect to https, then put the proxy next to the box that says "host". Next, type in the port next to where it says "port", then click on the "apply" button listed at the bottom of this window. Now ...

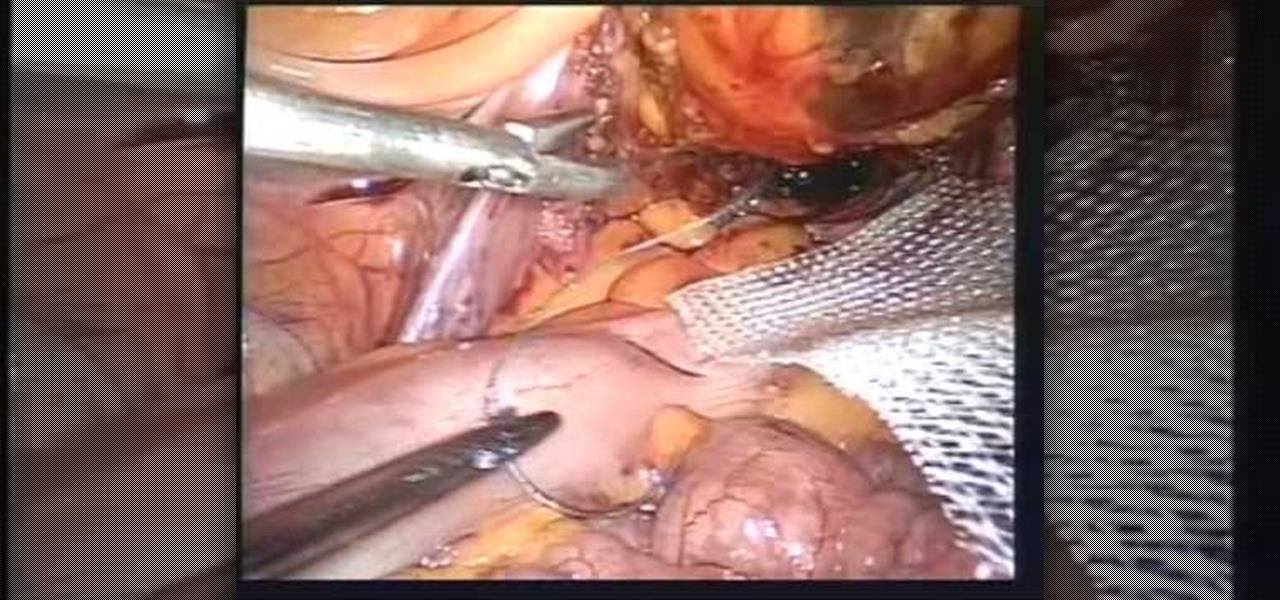
This video is about Laparoscopic Suturing Techniques.The video begins with the narrator saying that the technique is widely used in major abdominal surgeries and mastering of the techniques would give great confidence in the surgical procedures.There are various types of laproscopic needle drivers are available which can be selected according to preference.Different types of 10 millimeter laproscopic ports are available,however the valves used in the ports are important for performing extra c...

2019 has been a great year for smartphone batteries. Several phones have topped the 5,000 mAh threshold, and Apple finally went all in on 18 W USB PD charging, which means millions of new users are finally taking advantage of fast charging. All of this gets even better when you have the right charger.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

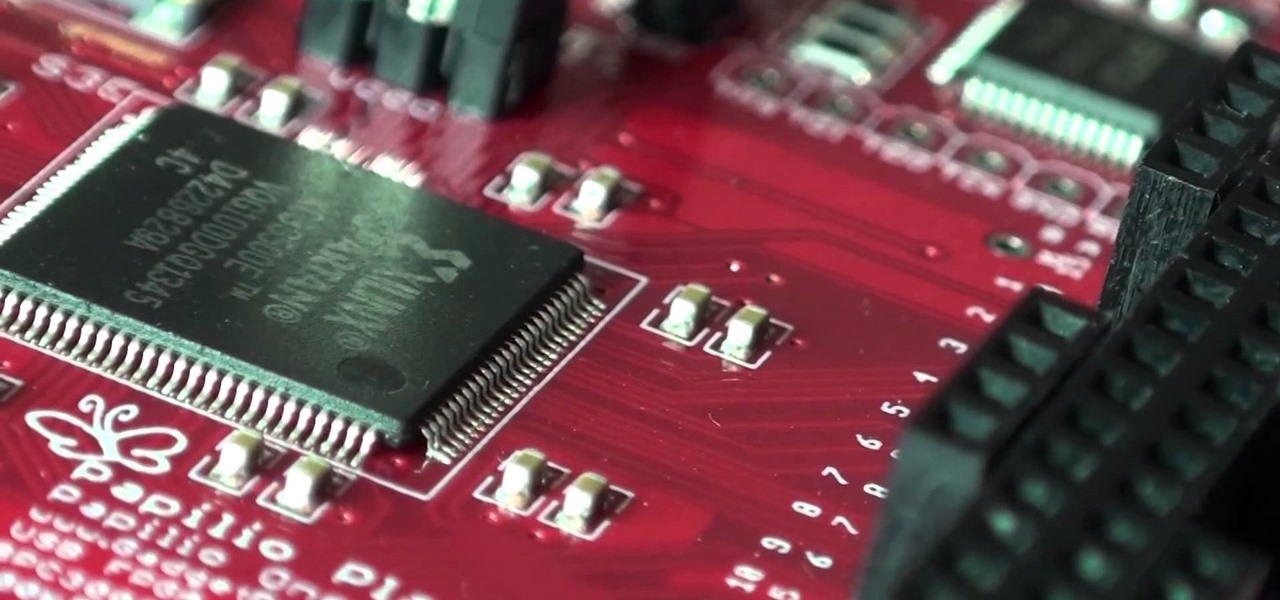
A FGPA is chip that is programmable with the computer to create circuit. It is a totally different type of programmable board compared to an Arduino for example. The Arduino will follow lines of codes to generate the necessary outputs. A FPGA won't however read lines of code, but it is a circuit itself. When the chip is programmed, a series of AND-ports, OR-ports and many others ports are linked together. The FGPA will increase the speed and the possibilities of your designs! I assume that by...

If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not always the problem.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

As if there weren't already enough problems with the iPhone 5, now the new Lightning USB cable is reportedly getting stuck in USB power adapters and computer ports. The newer Lightning cables have deeper divots and a slightly thinner mouth on the USB plug than the old 30-pin cables did, so the cable can get stuck inside your USB port.

Cranberry sauce is one of the most important side dishes to any Thanksgiving dinner—even Christmas dinner! And if you're like me, you usually buy a can of cranberry sauce for the holidays because you don't have the extra time to go homemade with the turkey stealing the show.

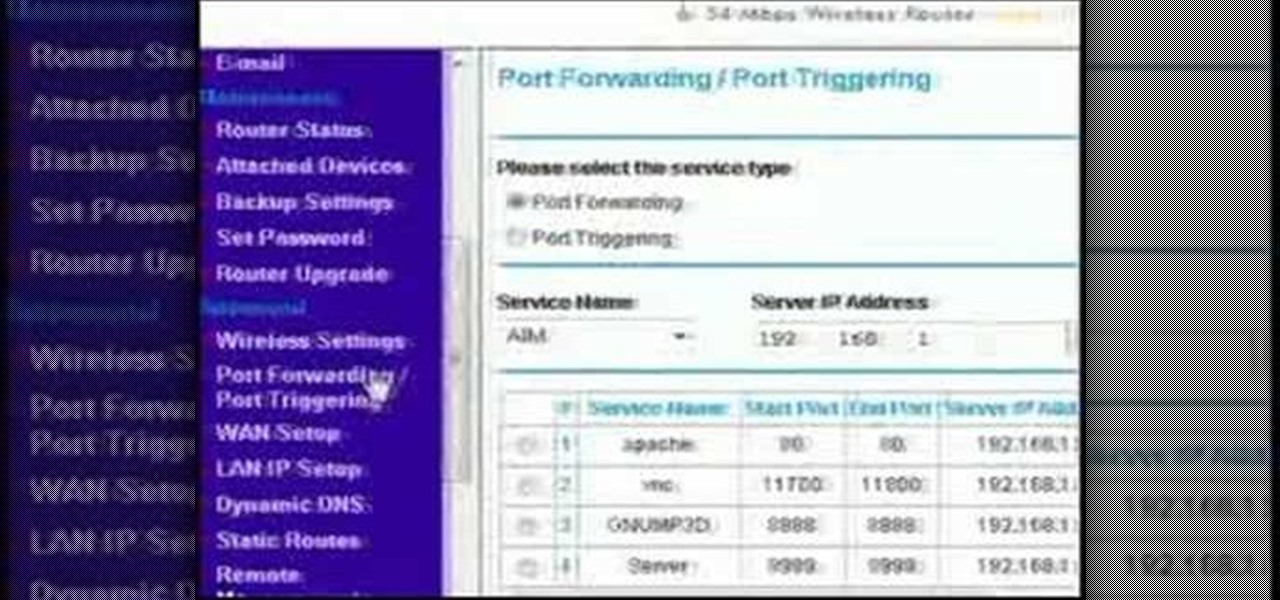
Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The fact that this guide even exists is a downright shame, but that's neither here nor there. The truth of the matter is the iPhone 7 and 7 Plus don't have 3.5 mm headphone jacks, and since they use the Lightning connector to output audio, it's hard to charge your phone while your headphones are plugged in.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

This video tutorial is in the Computers & Programming category where you will learn how to set up an FTP connection using Firezilla. Open up your filezilla program. On the top left, click on the file menu button, and select 'site manager'. In the window that opens up, select 'new folder' and give it a name. Now create a site to store in this new folder. Click on 'new site' and name it. Now on the right hand side, enter the host and the port. The default port is 21. Under server type, select F...

1.First take 1 cup of All purpose flour in a plate and 2 cups of same flour in another plate. And then take a stuffer can be anything like sweet coconut, chocolate flavor to put inside the puff.2.First add one tablespoon of vegetable oil to each plate and slowly make it out by hand and add some water and make flour mix. Now separate the 2 cups flour mix into 4 to 5 big pieces and separate the 1 cup flour mix into 4 to 5 small pieces.3.cover the small pieces with big pieces of each. Now just r...

In this video from lunawebs we learn how to use an external monitor with a camcorder. The best way is to use an HDTV and use your HDMI output on the TV. The sound can also come through the monitor if you have a headphone port on the monitor. If you want to go outdoors, it will be more of a challenge. If you do not have an HDMI out on your camera, there is a component you can use. Composite AV outs are cheaper when it comes to monitors and camcorders. If you have a composite monitor, assign th...

In this video, Caroline, host of 10MinuteCook, demonstrates how to create a traditional chestnut stuffing. The ingredients used in this recipe are: 500g ground sausage, 1 onion and 1 garlic clove - finely chopped, 75g dried cranberries - soaked in 50mL of port wine for an hour, 3 slices of bacon - chopped, 2 1/2 cups of bread crumbs, 1 can of chestnuts - finely chopped or pureed, 1 tsp thyme, 1 large egg. She begins by frying the bacon and onion and garlic mixture together, first. Once the on...

This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.