In this video, we learn how to write a winning resume and cover letter. First, you want to remember that your resume online needs to be keyword rich, so you will have greater chances of getting an interview. To find keywords for your resume, look up different job descriptions to change your resume to fit that specific job. List your specific qualities that make you the best candidate for that job. For your cover letter, make sure you always send it along with your resume. You want to capture ...

Focus groups strike fear into the hearts of even the most season marketer, and with good reason. In a world where everything is subject to change based on public opinion, from movie endings, to popcorn flavors, to logo colors, focus groups can make or break a new idea, but it doesn't have to be that way. A focus group is just a way to gather opinions in a vigorous way and can be very useful. Watch this video tutorial to use a focus group to develop and test a new brand name or corporate ident...

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

This video gives a clear view of how well one has to answer in an interview. This is a good answer given by a woman interviewing for an environmental scientist position. This video is provided by denham resources. The first question asked by the interviewer is, "How do you stay current?" The candidate gives a wonderful answer for that. She told the interviewer that she is a member of a relevant discipline, and through that she is attending events; that itself shows a relevant passion for grow...

See how to change your logon background with Tweaks in Windows 7. This is a quick tip for the new Windows 7 operating system. You'll need a piece of software called Tweaks.com Logon Changer. It allows you to have your own background for Windows 7 to make it a bit more personal.
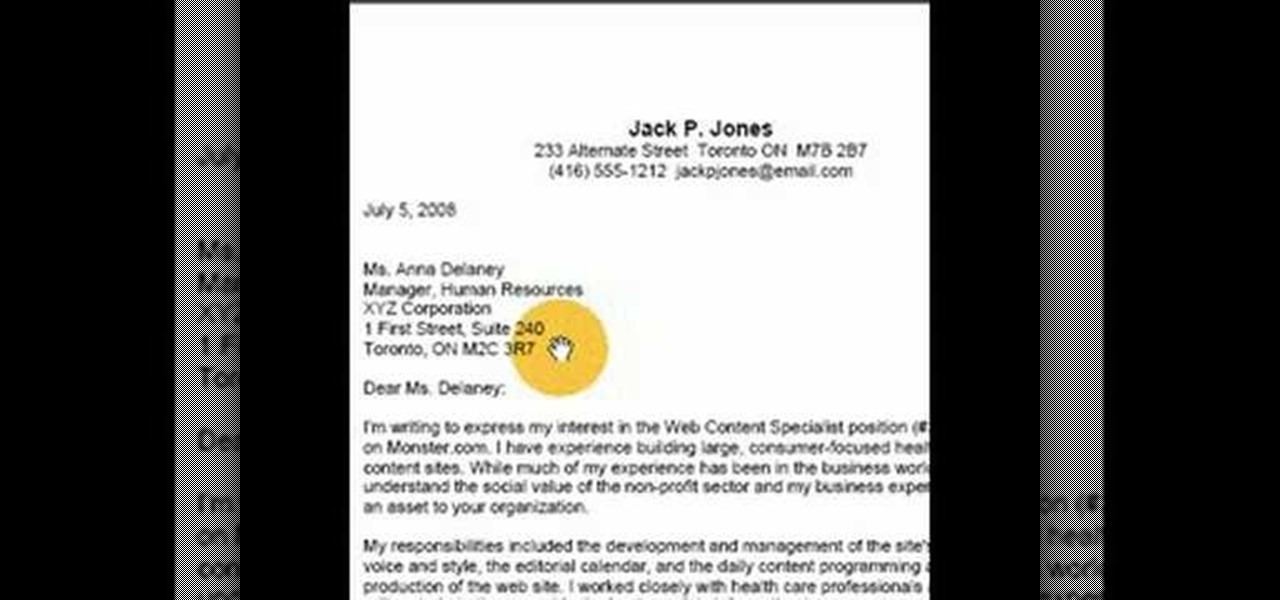
This video goes over cover letter formats, specifically in Full Block Style. Cover Letters accompany resumes in job applications. They should be sent ahead of the resume. They go over your experience, desires and objectives. The cover letter is important to both employers and employees. A human resources or HR department often receives thousands of letters that it must review before granting a job candidate a job interview or even reading their resume. This is a LIAD Production for World of W...

Learn how to use the English past tense passive voice in this how to video. The passive voice is the form of a transitive verb, that requires both a subject and one or more objects. To make the past tense passive, use "was" or "were," depending on the subject, and then add the past participle.

This ESL how to video teaches you the use of the passive voice in the passive tense in English. The passive voice is the form of a transitive verb, that requires both a subject and one or more objects. In the present tense, the subject changes the verb "be" and then you use the past participle of the main verb. Watch this tutorial and you will be speaking English in no time.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

This ESL tutorial shows how to make yes-no questions in the passive voice in the present perfect tense. The passive voice un the present perfect tense uses have or has + subject + been + past participle. Watch this how to video and you'll be speaking English in no time.

Modal verbs in the passive voice follow this pattern: Modal + be + past participle. There are many possibilities with modal verbs. This ESL tutorial gives a basic description of how to use modal verbs in the passive voice. Watch this how to video and you will be speaking English properly in no time.

Learn how you can use the passive voice in the future tense in this ESL tutorial. To make the future tense passive in English, use "will be" and then the past participle. "Will" is a modal verb, so this formula applies to other modals such as can, may, must, might, etc. Watch this how to video and you will be speaking English in no time.

Learn how to use the English passive voice in the continuous tense in this tutorial. When the present continuous tense is in the passive voice it looks like this:

There is a wide rage of variables to consider when considering getting breast implants. This includes everything from if you are a good candidate, the type of implants, the size of the implants, the type of surgery, the size and the possible side-effects.

I hate being cold. That's why I live in Los Angeles. But, there are plenty of folks who are experiencing some pretty chilly temperatures this year, despite global warming, and one of the worst places affected is the garage. C'mon, who has a freakin' heater in their garage?

In this ESL tutorial you will learn how to use the passive voice in the past continuous tense in Englishi. The passive voice is the form of a transitive verb, that requires both a subject and one or more objects. To put the past continuous tense into the passive voice, use "was" or "were" depending on the subject, then "being" and then the past participle. Watch this grammar how to video and you will be speaking English in no time.

The last presidential debate of 2012 is over between President Barack Obama and Republican nominee Governor Mitt Romney. Now it's up to you to choose your candidate by election day on November 6th, 2012, and more importantly—VOTE!

Play the Sad Mummy as your champion! This video goes into strategies and tips when you play the League of Legends character Amumu the Sad Mummy. Watch Amumu in play and see the best way to use his unique and passive abilities to ensure victory for your team!

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

In this language tutorial, you will learn to use the present passive indicative in biblical Greek (Koine). This is a perfect lesson for those who wish to study this ancient language. Listen and repeat the words in this language tutorial and you will be speaking biblical Greek in no time.

Mr. Blake is showing us how he uses various features of Screenflow and iMovie 09 for making YouTube videos. He takes us through features of Screenflow which not only includes recording a video but also lets us customize the video wherein you can edit giving various effects to the video with the size or the scale, make changes in the audio, give click effect, change passive things, covered action, add text or other things which also includes media. He also mentions and shows us how to use the ...

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway

You can’t change the size of your pores, but you can make them look a lot smaller. You Will Need

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Have an opinion and want the whole world to know it? You're not alone! There are many online outlets for you to type up your review, whether it be for a restaurant, play, movie, book or anything else you have recently experienced. Check out this video for tips on how and where to post your exciting review.

Answer “Why should we hire you?” in a job interview John Heaney from The Job Shopper discusses how to handle one of the toughest questions you will face in a job interview: “Why should we hire you?”

In a recent poll taken by an online recruiting company revealed that 37 percent of all hiring managers do not hire someone based just on the way they dress, more than half said they'd hold it against a candidate if they hadn't worn a jacket and seventy percent said that they wouldn't hire anyone wearing jeans, a leather jacket or a polo shirt to the interview. The rules for office dress code have changed, more and more companies offer their employees a business-casual dress code which makes i...

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

Kings Dominion, an amusement park located in Doswell, Virginia, just announced a mobile augmented reality game for park visitors. Gameplay in The Battle for Kings Dominion — available on May 19 for iOS and Android devices — follows the playbook designed by Niantic through Ingress and Pokémon GO.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Make your underwater dreams come true by turning yourself into a bona fide swimming mermaid. If mermaids did exist, you would be the perfect candidate to transform into the mythical creature. So check out this video tutorial form Little Orca to learn how to make your own mermaid tail costume.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

Just like a rapper engaged in tweet feud, Elon Musk was working overtime on Twitter this morning, dropping information about the upcoming Tesla Model 3. He even gave a sneak peek of the "release candidate" version of the car, sharing a brief clip of the car driving, which, let's be real, doesn't really tell us anything. Aside from the video, Musk also revealed the fun fact that the car gots its name after Ford sued Tesla for trying to name it the Model E, which would make the abbreviation of ...

Earlier today, Alphabet announced that the Self-Driving Car Project has officially graduated from their innovation factory (X) and will now operate as an independent company called Waymo.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

The Unicode Consortium just unveiled 72 new emojis that will be included in the upcoming Unicode 9.0 release, but we're not here to talk about the winners. Instead, let's take a look at the five poor emojis that will have to wait until at least next year to join the Unicode roster.