As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.
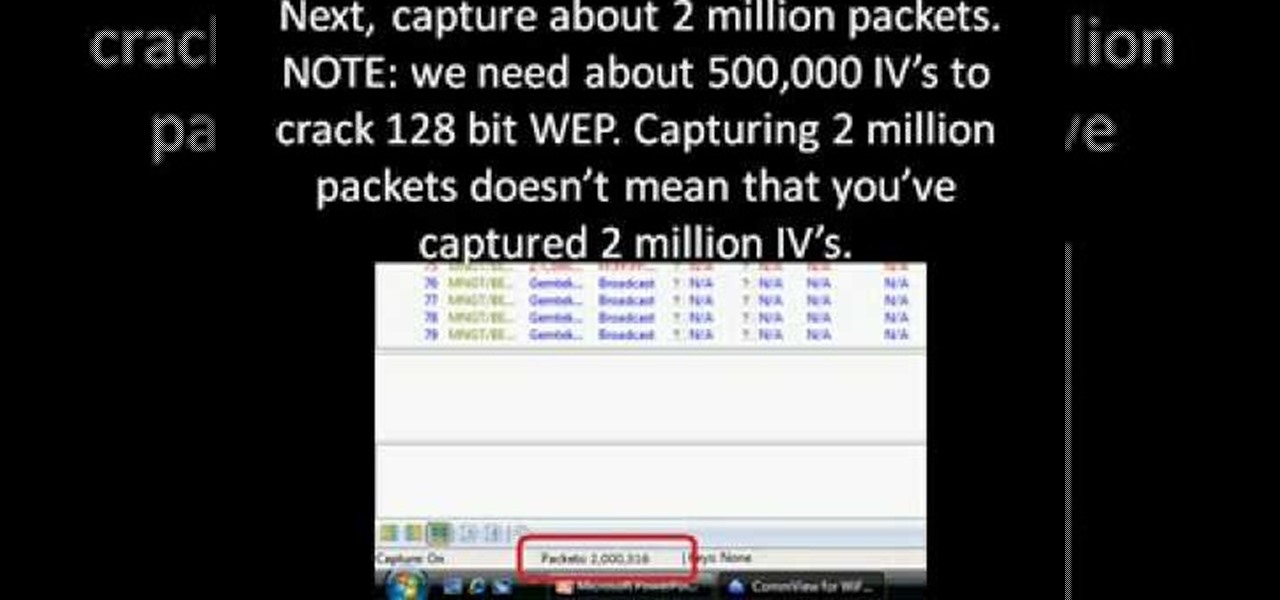
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

In this video Dr. Carlson demonstrates the properties of light. Light is like a wave and it is also like a particle, which means that it comes in small packets. To demonstrate how we know that light behaves like packets of energy, he uses LED’s in different colors and a sheet of phosphorescent paper. When light with a high enough energy shines on the paper it will cause the paper to glow.

Kat teaches us how to make a sugar free strawberry pie in this tutorial. First, purchase fresh strawberries and wash them, then pull the stems off. Next, use a butter knife to remove the top middle of the strawberries. After this, use an egg slicer to slice up your strawberries until you have four cups. Next, purchase a graham cracker crust from the store, then place all the strawberries into it. After this, even them out and pack them into the crust. Set this aside, then take 1.5 c water, su...

In this video tutorial, viewers learn how to do the swing false cut card trick. This cut makes it seem like the magician actually shuffled the deck. Hold the deck with one hand and cut a portion of it. Then lock the packet with your other hand's thumb and cut another portion of the decking, forming 3 packets. Put the top pack at the bottom as you pull out the center pack. Then swivel the packet on top to the other hand and drop the final pack on top. This video will benefit those viewers who ...

Have a hot party going on this weekend? Learn how to make these cool Jell-O shots in oranges with this easy to follow instructional video. All you will need is packets of instant Jell-O, vodka, oranges and snob. All you need to do is follow the instruction on the back of the Jell-O box and substitute a couple of things with liquor. Then, the cool part is where you halve the orange and put the Jell-O in to create orange Jell-O shot wedges!!!

This video will show you how to make an easy and quick envelope for holding cards and seed packets. This is a great idea and super-cute. Your family and friends will absolutely love receiving this wonderful envelope that you made.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

In this video, we learn how to make a molded tomato aspic salad with crab and couscous. You will first take 2 c tomato juice and pour into a saucepan over medium heat. Next, take 1 c of tomato juice, and add in 2 packets of unflavored gelatin inside. Sprinkle this over your tomato juice so it softens, then pour this mixture into the hot tomato juice and stir until it's dissolved. Next, add finely chopped carrots, green peppers, and cucumbers to the mix. Stir this, then place into small molds ...

In this video, we learn how to dye yarn with Kool-Aid. First, take two chairs and wrap yarn around them as tight as possible to keep them from getting tangled up. Then, place in a bath of lukewarm water for ten minutes. After this, grab packets of Kool Aid the color you want your yarn to be. Now, take the yarn out of the water and squeeze out any excess water. After this, mix up the Kool Aid and place it into individual jars for each color. Next, place the jars in a large pot of water and the...

You know those sugary sweet jelly fruit slices you can get in little packets at every grocery and convenience store? Well, we've found a way for you to enjoy them without busting out of your belt.

When making Coconut Kefir you should use young ty coconut from a whole foods store because it will be sweet. You will also need a product called Kefir starter. Open your coconut and strain out the water and remember to save the meat from the coconut. Heat the water from the coconut to about body temp. Once heated pour the water into a large jar and add a packet of kefir. The Kefir packets should be measured one packet to one quart of water. You will need to store your kefir in an airtight con...

The video describes how to make a fake blood quickly by using kool-aid which takes atleast 2 to 3 minutes.For that we need at least five packets of kool-aid,sunsilk hair conditioner(any relevant conditioner),bowl and spoon.firstly,mix the kool-aid with hair conditioner in the bowl with spoon.Now the mixture is in the form of paste.But to make more fluid type add some more hair conditioner.Mix well to avoid the crystal forming of the kool-aid.It will really appear like blood and there is no st...

This video is a demonstration of how to make the perfect ramen noodles. The requirements for the recipe are 2 packets of ramen noodles, milk and vegetable oil. Using butter instead of oil enhances the taste of this recipe. Water is heated in a pan and the noddles are added to hot water. Let the water boil and cook the noodles till they turn soft. Drain the water from the noodles using a strainer and put it back in the pan. Add half a cap of vegetable oil to the strained noodles and mix thorou...

This video shows the method to use a puggmill in pottery throwing. Take the two packets of clay and take the clay out on the table. Take a thread and cut the two pieces of clay in the middle to form four bricks. Put the bricks in the puggmill one by one and wait for it to come out. The pugged clay comes out from the bottom in a cylindrical shape. Take out the four cylinders from the four bricks of clay. After this, put the cylinders in the pugmill again so that they are pugged thoroughly. Put...

This video shows you how easy it is to make Mexican (Spanish) rice. You start with a pan on medium heat.1 tablespoon of oil, 2 cups of long grain rice. Long grain rice because it’s good for this type of meal. You can get the rice in packets that you won't have to wash the rice. You want a to cook the rice until it gets a little color. Then add 1/2 cup of chopped large onions for 1 minute, 1 can of kidney beans washed and drained, 1 medium bell pepper chopped, and 1/2 teaspoon garlic powder, 1...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

Watch this instructional magic card trick tutorial to learn how to perform the binary routine. This is an original series of user-created moves. There are 9 phases of the Binary Routine, 6 of which are false, and the other 3 are closers that involve a color card change at the end. This video provides instruction on 2 false cuts and 1 closer, along with some possible variations. Just keep in mind, there is room for adjustment with these phases. If you find a better way to do a certain move, th...

En papillote may sound like a difficult French cooking method you'd never use at home, but don't be fooled by its fancy name—it's actually a really easy way to cook food that is moist and flavorful, and all you need is some parchment paper and your oven.

Next time you organize a cookout, throw a few spuds on the grill, too. Watch this video to learn how to make grilled potatoes.

Here is a cake type of chocolate cake, it uses biscuit cookies. You will probably have to fight the kids off just because you want it all to yourself. The best part is that there is no baking required and it is very simple to make. The only thing you need is patience - just enough to make it and allow it to chill before you dig into it. Watch this how to video to learn a quick recipe for a chocolate biscuit cake recipe.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

You're in your car. You've got a bag of piping-hot French fries with you. You want those fries in your mouth ASAP, but you also want to dip them in ketchup. So what do you do?