Focus groups strike fear into the hearts of even the most season marketer, and with good reason. In a world where everything is subject to change based on public opinion, from movie endings, to popcorn flavors, to logo colors, focus groups can make or break a new idea, but it doesn't have to be that way. A focus group is just a way to gather opinions in a vigorous way and can be very useful. Watch this video tutorial to use a focus group to develop and test a new brand name or corporate ident...

Prevent indoor lighting problems with these great tips. -When a window is behind the object, bring lights closer to object or use a reflector using the light from the window to create a 3 point lighting effect.

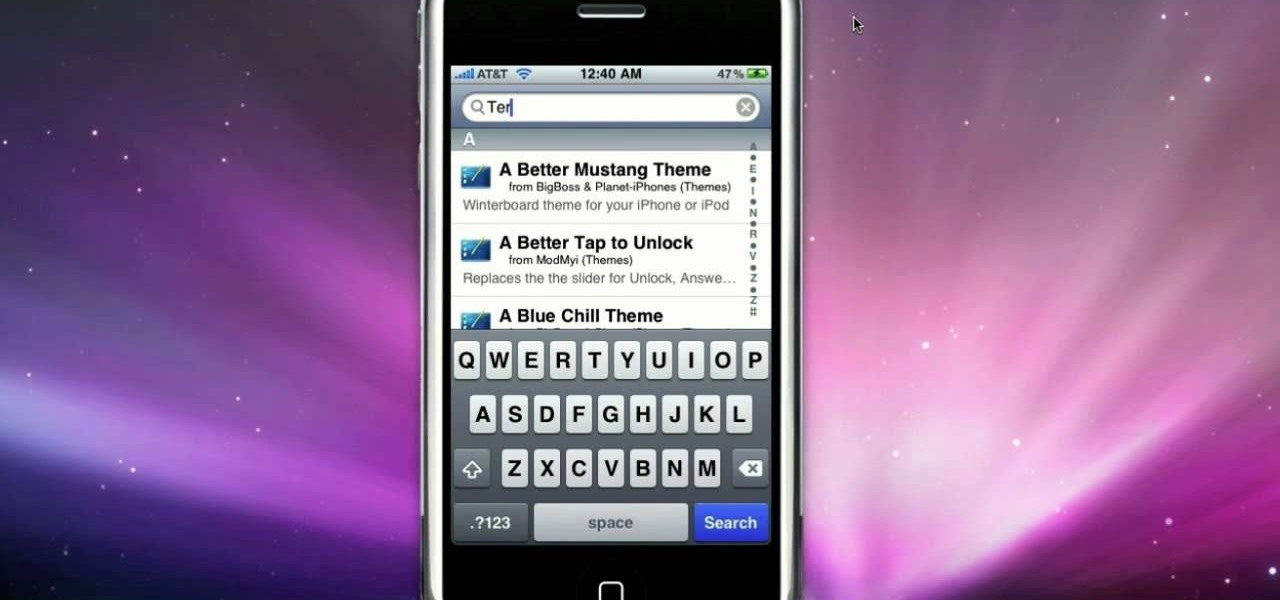
This software tutorial takes a look at how to design an icon set in both Photoshop and Illustrator. An icon set is a set of icons that you can integrate into a number of different projects, like a website or a company letterhead, logo and identity set up. Having an icon set readily available for all your project needs will make your workflow faster and simpler. So watch and see how to make an icon set first in Photoshop and then in Illustrator.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

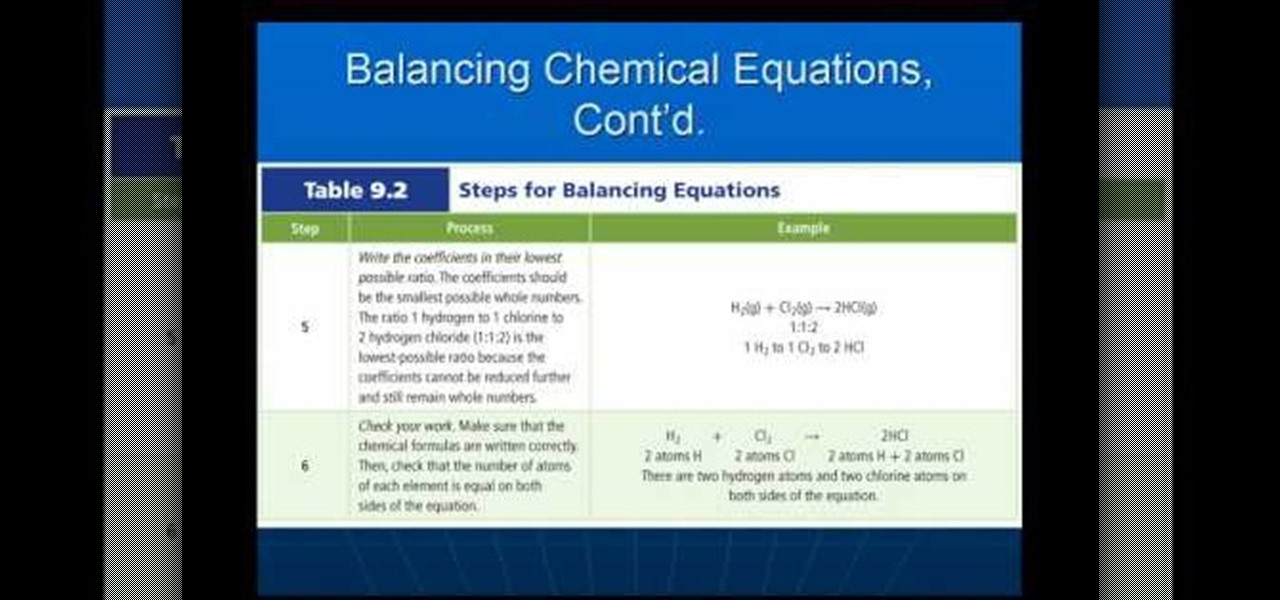
In this video we learn how to balance chemical equations properly. What is a chemical equation? It's a statement that uses a chemical formula to show identities and relative amounts of the substances involved in a chemical reaction. To balance an equation out you must have the same number of atoms on both sides of the chemical equation. Or, you must have the same amount of mass or matter on both of the sides. Once you have these balanced out so they are the same then you will have it complete...

Sometimes--no matter how much you may want to avoid any trouble--you just have to swallow it up and do it the smart way. Notarizing your documents helps you avoid fraud.

In this video, we learn how to bring your Cuban spouse to Canada. First, you need to have the correct documents which prove your identity and marriage status. You will also need marriage certificates from previous marriages stating that they are dissolved. After this, you will need to have them notarized, then travel to Cuba to obtain new documents for you and your future spouse. The authorities will direct you to the appropriate offices, then you will need to pay the fee for filing these pap...

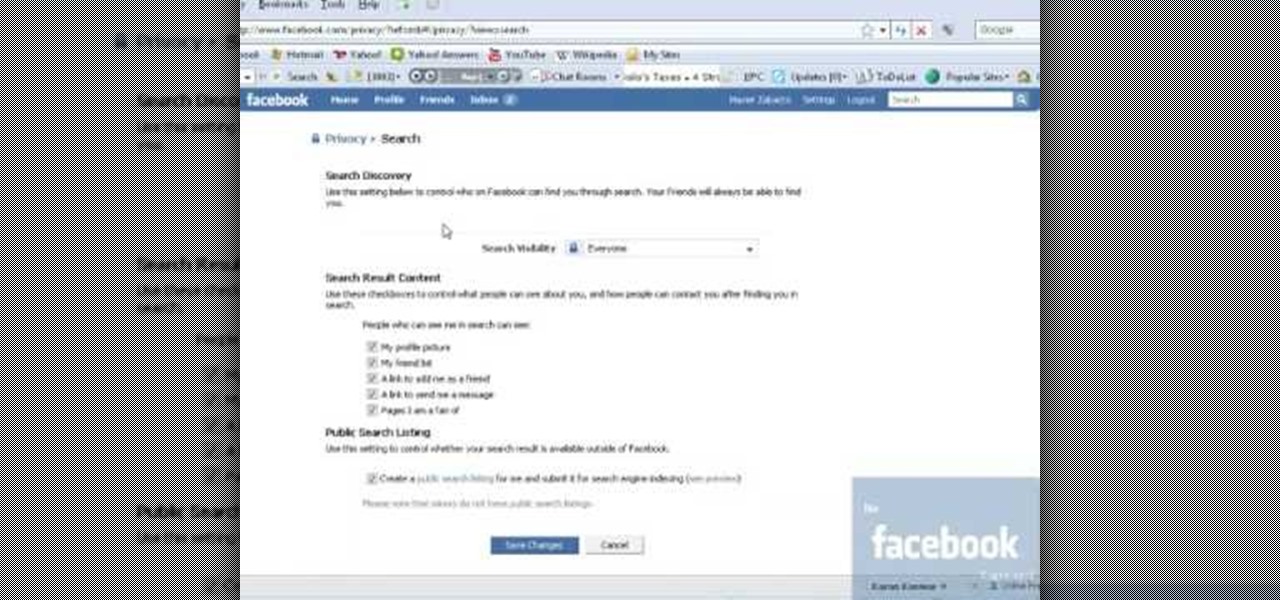
In this video, we learn how to make your Facebook profile less public. First, log onto your Facebook account, then go to your privacy settings. Through there, go to search and choose who you want to allow to search for you on your site. After this, save your settings and move on to the other sections to change more privacy settings. If you do not want people that aren't your friends to see your information or to be able to search for you on Google, this is a great way to go. Making your infor...

This video from TechFusionVids presents how to install Microsoft Office 2008 on Macbook Pro.All installation process takes about 5 minutes. Insert Microsoft Office 2008 installation disk, double click on the installer icon when Office installation window opens.Click Continue two times, agree to software license agreement, type your name and name of your computer, click Continue again.Window opens saying you should close all running applications before starting further installation.Once it's d...

In this video, Dan and Jennifer will teach you how to be safe while trying to meet girls or date online. Learn tips and tricks to avoid common scams such as identity theft and fraud, as well as things to look out for and early warning signs that your potential lover may not be all she says she is. Dan and Jennifer will also show you how to watch out for one of the most common scams online: "cam girls". Don't fall for that fake girl that acts like she's totally into you but really just wants y...

A PDF Portfolio is a bundled collection of content compressed into one PDF file. Watch this 5 minute overview and learn how you can bundle documents, e-mail, drawings, flash presentations and even video into one sleek package that can be used for presentations or project management for your organization. Your portfolio can include introductory text and sets of data that can be sorted geographically by being linked to clickable maps. Not only can the entire portfolio be branded with your logo ...

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

HTC is one of the few OEMs that make it easy to unlock the bootloader on their devices. And while they do warn you that doing so voids your warranty, they don't tell you that it also prevents you from collecting promotions that come with their devices.

Birds don't generally wear collars, but to give a bird an identity tag, leg bands can be used. This video demonstrates the way to put leg bands on baby pigeons. This is usually done between 5-7 days of age. When pulling the back toe through, make sure not to force it if the little claw gets caught on the inside of the band. Watch this video pet care tutorial and learn how to band the leg of a baby pigeon with an ID tag.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

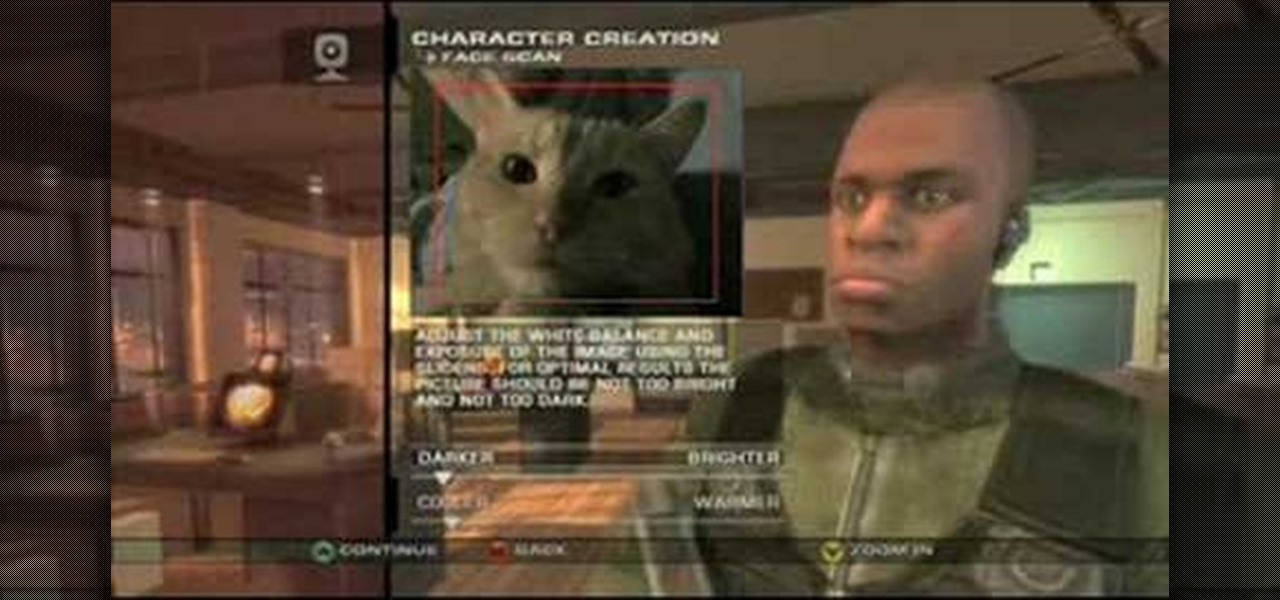
This process requires XBox2 live with vision camera. We are going to create a character. First, you go to multiplayer mode, options and then choose character creation. If you haven't created a character, you will start from scratch here. If you have created a character previously, you will make some adjustments to the character for this presentation. Now, go to player information and then service record. As the program already has a character, we are going to change the appearance of the char...

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

Meez is the social entertainment leader combining avatars, web games and virtual worlds. Get help with all of your Meez avatar needs with these Meez tips and tricks! Watch this video tutorial to learn how to remove the head off your Meez avatar.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

This video will show you how to translate webpages using Google Toolbar. To quickly translate a web page using Google Toolbar, simply do the following: Click on the 'Translate' button in the toolbar. Select the language into which you wish to translate the page, and it will be translated within seconds. If you want to go back to viewing the page in its original language, simply click on 'Show Original'.

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.