
How To: Change the hold music on the company phone system
Changing the hold music piped into your company phone is a prank some callers will appreciate—depending on what you replace it with.


Changing the hold music piped into your company phone is a prank some callers will appreciate—depending on what you replace it with.

Have you been noticing a small stench trailing throughout your home? Is you teen going through "changes" and you don't know how to approach them? Follow these tips to keep your home and teen smelling like roses.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.
Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.
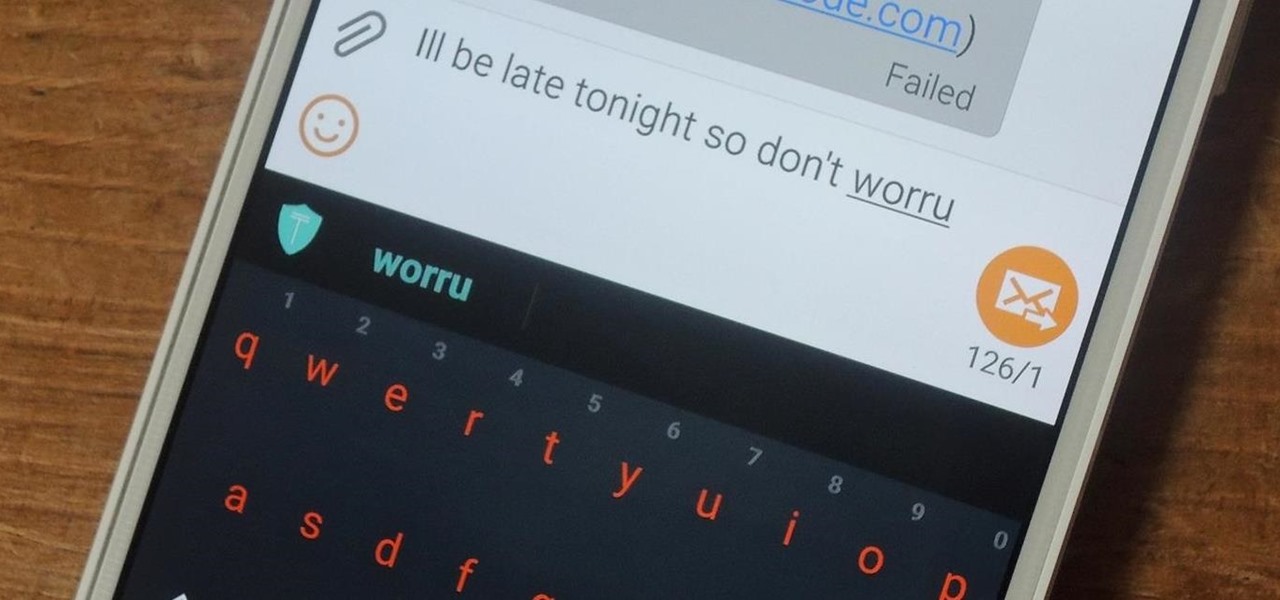
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.
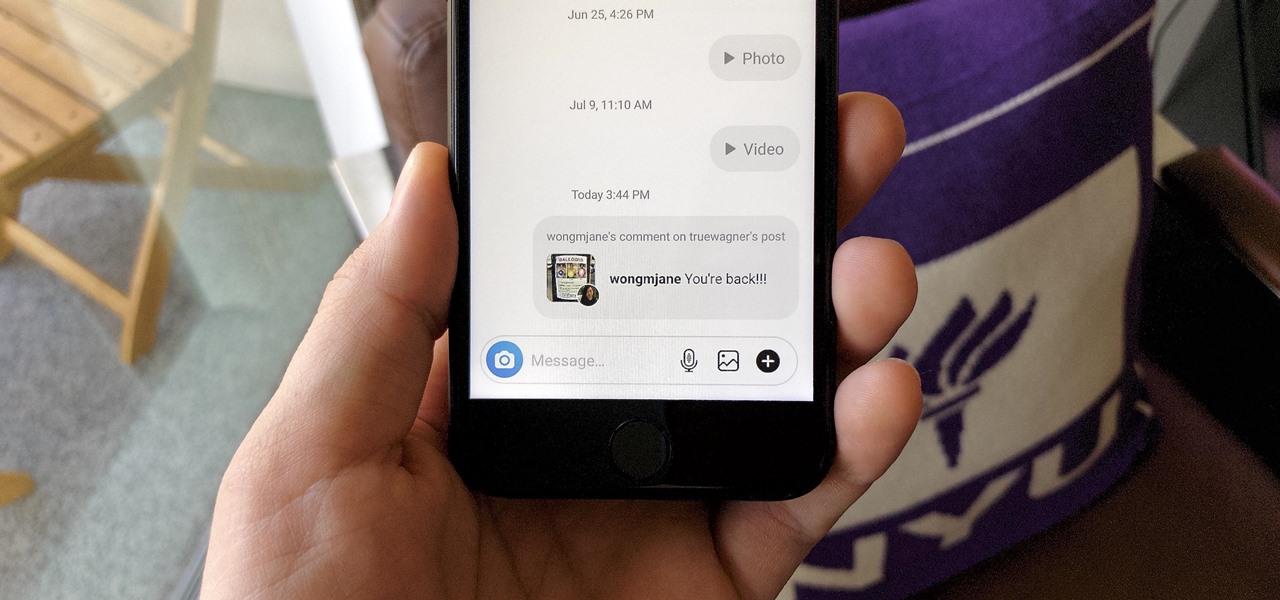
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.
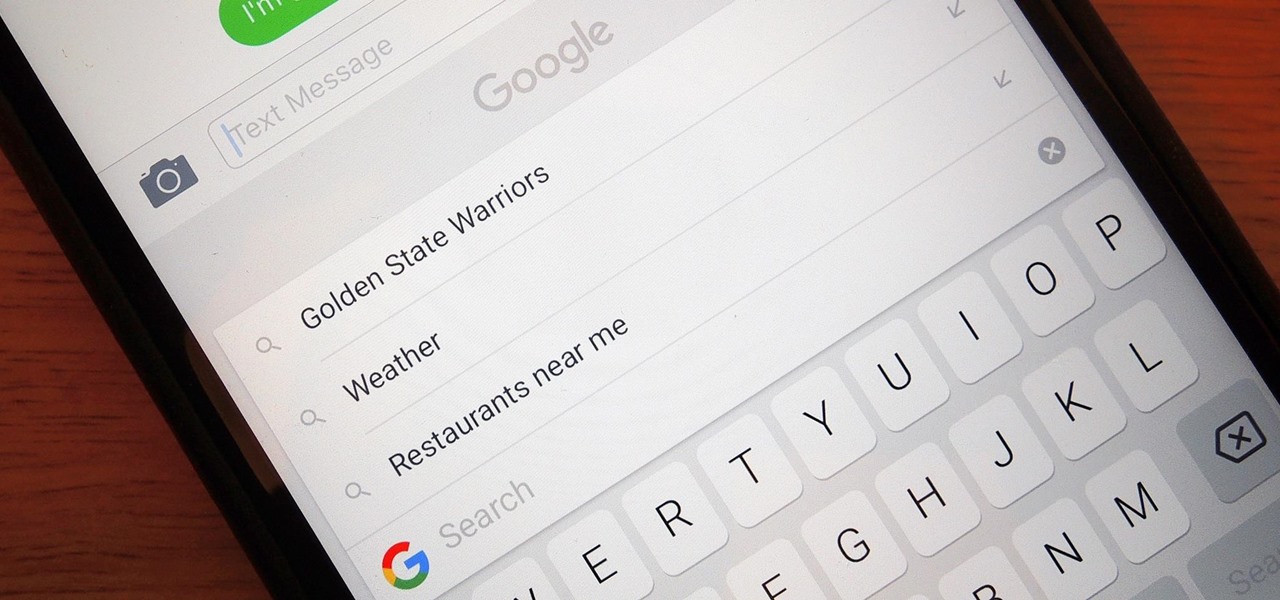
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

Love him or hate him, we all know President Trump has a strong presence on Twitter. Whether it's 3 pm or 3 am, the president is probably tweeting. His frequent Twitter habits are often discussed by the media, and they've especially caught the attention of lawyers at Columbia University ... but not in a good way.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!
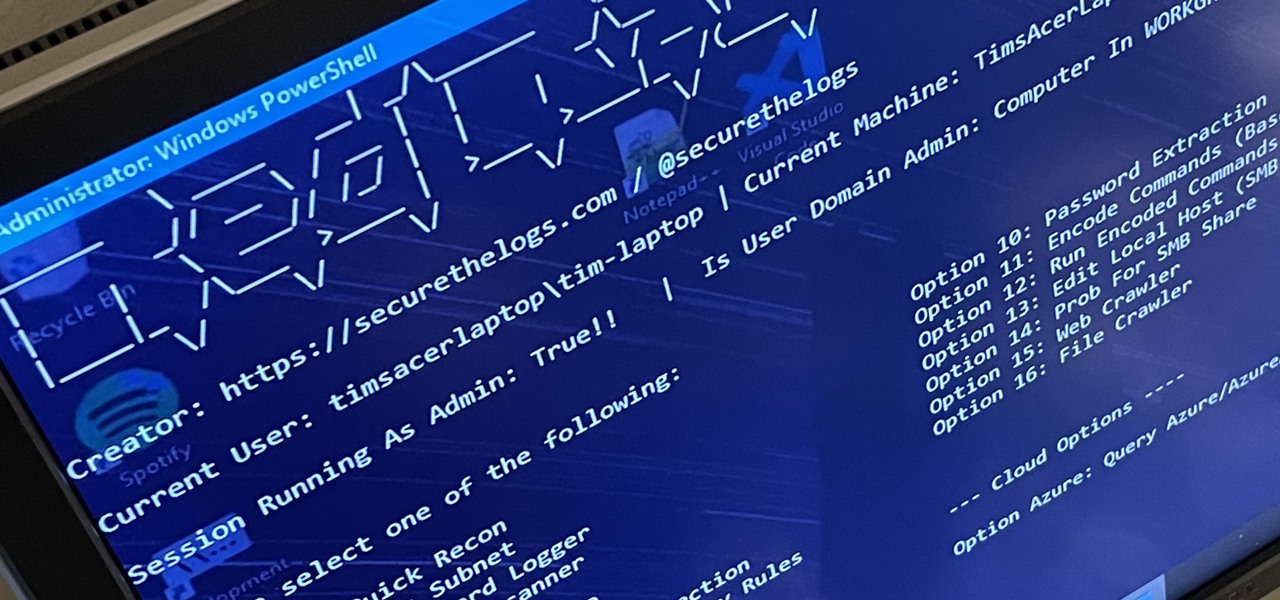
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

The iPhone's autocorrect feature is wonderful and convenient, but it doesn't always work with informal language like profanity. If you've ever used the F-word, there's a good chance you've had your curse words "corrected" to other words that don't ducking make sense. And with the release of iOS 13, swearing in your messages and on social media could get a little harder.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.
We're all guilty of a little social media stalking now and again. Or ... every day. Who's keeping track? Everyone secretly wants to know what their ex/arch nemesis is doing for the weekend via Snapchat or Instagram Stories.

Fans of Titanfall now have a great alternative to play on their iPhones whenever they're out and about. Titanfall: Assault has arrived as a soft launch for iOS devices. A hybrid between card-based and real-time strategy genres, the game will pit you against other players with some mech-on-mech action to dominate the battlefield. Taking some cues from Clash Royale, each unit that's deployed in Titanfall: Assault will automatically fight its way through opposing forces to accomplish its objecti...

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

One of the best things about cold weather is soup, and there's nothing more comforting than a great chicken noodle soup. But I've often grabbed a can from the grocery store and found the chicken dried out and over-processed... and the noodles soggy and tasteless. What's worse: there's never enough of the stuff you like (such as the vegetables) and too much of what you don't (the nasty stuff I mentioned above).

When I was younger, my family would go to fancy restaurants and I would invariably order a Shirley Temple. (Ironically, the real Shirley Temple actually didn't like it much.) But it's hard to really find anything offensive in this kiddie cocktail: It's ginger ale with a splash of grenadine. There's also the less famous Roy Rogers, which is Coca-Cola with grenadine. The grenadine, red and sumptuous, always made its drinks look and taste much cooler.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.