Despite the relatively small size of Magic Leap's first annual L.E.A.P. conference, there was a lot to see and experience. Apparently missed by many was one of the best experiences I had at the event: Wingnut AR's unreleased Pest Control game.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

A lot of people have problems with their cats urinating inside the house, leaving behind the retched odor of cat pee. Others get frustrated when feral or stray cats pee on their porch, patio, or anywhere else outside of their house, as it's not the most welcoming odor when guests arrive.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.

Unity 5.6 was just released on March 31, and it will be the last entry in the Unity 5 cycle. With all of the new features, it looks like Unity 5 is going out with a bang.

Apple's just released a new beta of iOS 7.1 for developers, Beta 5, which fixes some small bugs and adds some minor feature enhancements. With previous reports stating that the final version of 7.1 was slated for a public release in March, these early leaks are indications that the final will be released in the following weeks, shortly after the Golden Master version hits developers.

For being an inexpensive tablet, the Nexus 7 packs a 1,280 x 800 pixel resolution into a relatively small display, offering a very sharp-looking 216 pixels per inch. What does that mean? It's one of the best e-readers on the market.

Check out this supernatural tutorial video that offers 7 tips on getting started in becoming a paranormal investigator. Just follow these simple steps:

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Is your blog booming or just plain boring? IMaybe it's not boring, but you probably aren't getting much traffic, at least, not the amount you want. If you want to learn how to increase your traffic to your blog or website, this video has information pertaining to quick traffic.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, making it a truly hands-free experience.

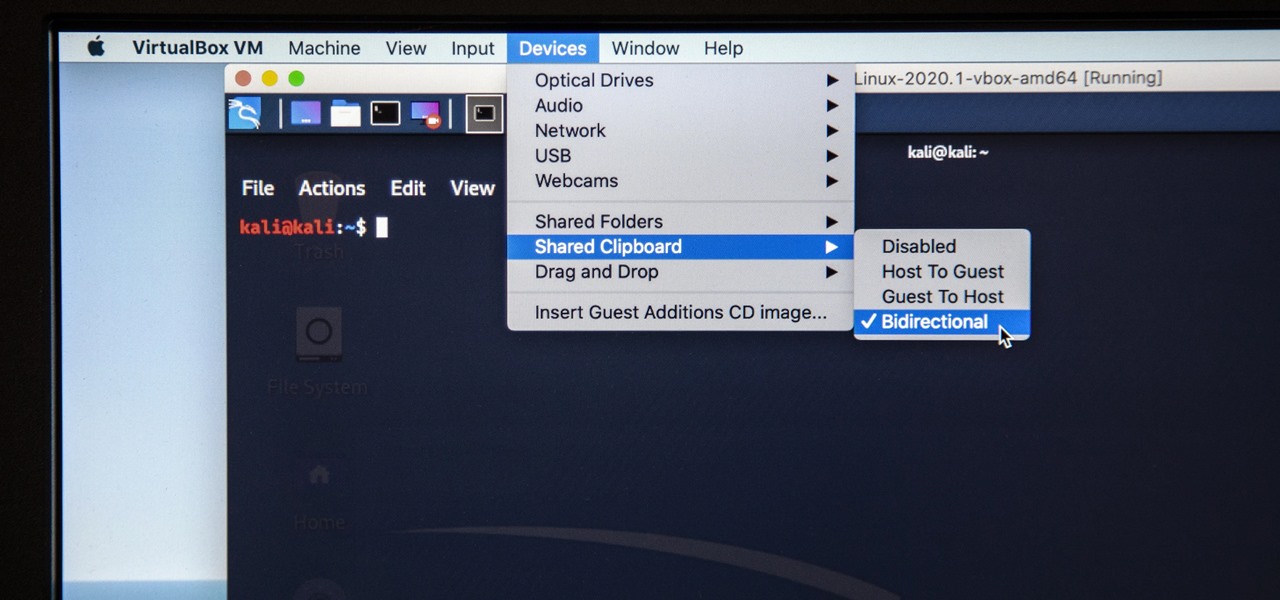
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

The latest official update for iPhone, iOS 13.2, introduced 22 new features and changes to the iOS 13 era, building off the improvements brought by iOS 13.1 and iOS 13 proper before it. It's time to take our first peek into what's next for iPhone and iOS, as Apple releases iOS 13.3 developer beta 1 today, Tuesday, Nov. 5.

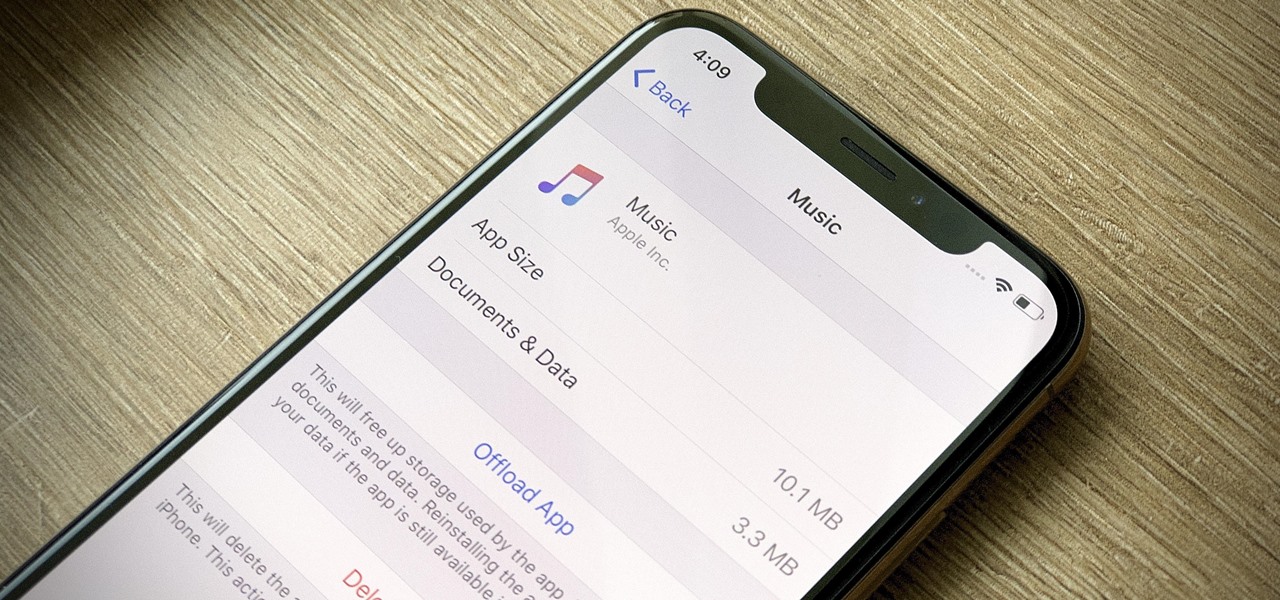
While smartphones are increasing their built-in storage every year, they're also giving you more features that consume all that extra space quickly, like when you shoot 4K videos. So while you may have a load of gigabytes for all your music, it may get eaten up quickly by apps, photos, and videos. Luckily, Apple Music has an auto-delete feature, so you don't have to manage anything manually.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

By default, the Galaxy S9 and S9+ only have 15 media volume steps — in other words, there are only 15 increments between silent and full volume. That's usually fine if you're using your phone's speakers, but if you're wearing headphones, more fine-tuned controls would be helpful.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Apple just pushed out iOS 11.2.5 beta 7 today for iPad, iPhone, and iPod touch to both developers and public beta testers. On Wednesday, Jan. 17, beta 6 was released, and there were two betas the previous week. With Apple promising a patch for "ChaiOS" next week for everyone, it's like iOS 11.2.5 will be that update.

Snapchat announced today that you can now design geofilters in-app, making it easier than ever to customize your snaps. This new feature incorporates a mobile creative studio, so you no longer have to use your computer to create your custom masterpiece.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Google's Pixel and Pixel XL flagship phones are a rousing success, with consumers praising the fluid user experience and overall performance as two of the devices' biggest strengths. But even though Google may have knocked it out of the park with a set of Apple-like smartphones that "just work," there's still room for improvement in a few areas.

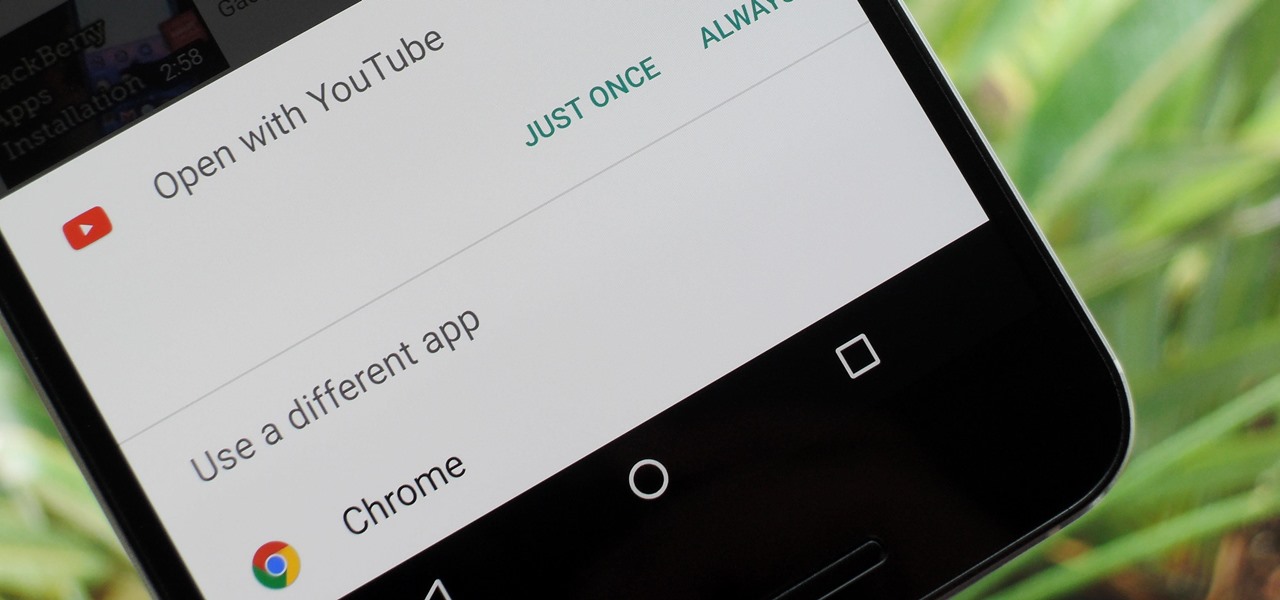
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

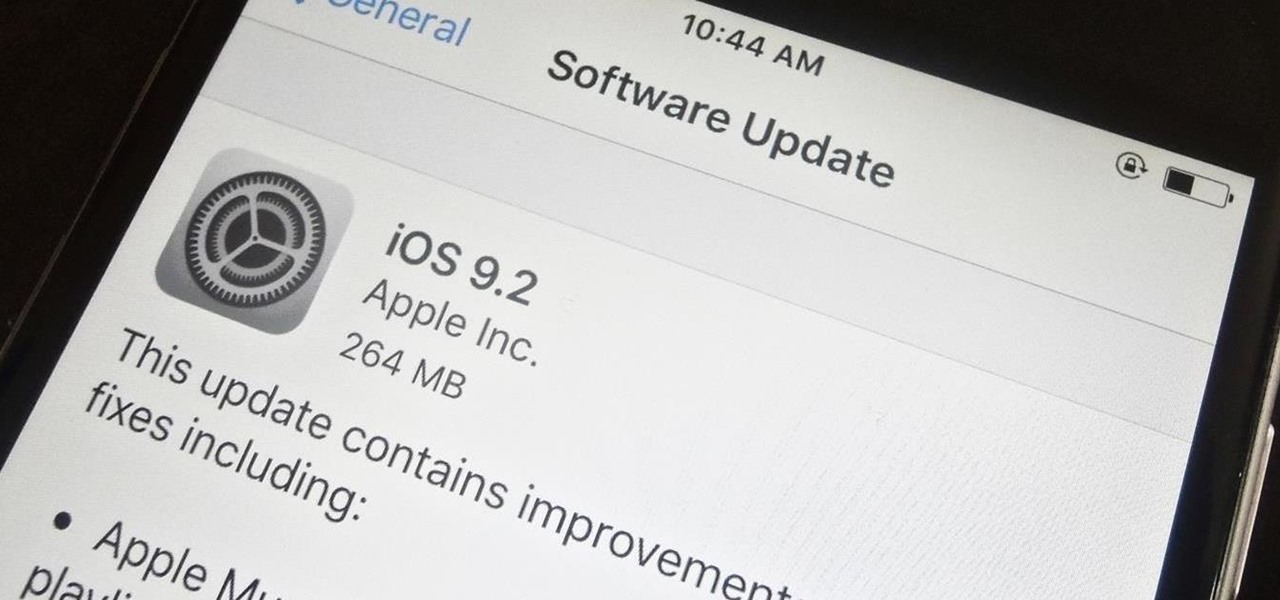
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.