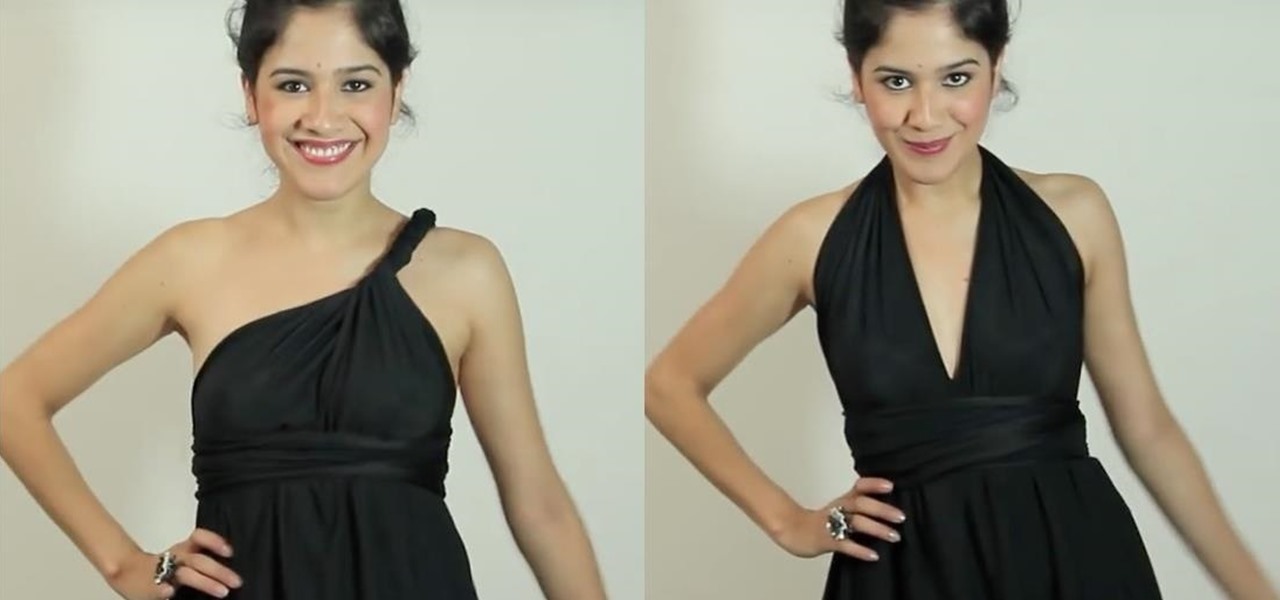Thanks to Stephanie Meyer, the greater part of the English-reading world thinks that vampires are gorgeous. And casting talented and beautiful actors like Robert Pattinson, Ashley Greene, and Nikki Reed probably didn't help to dispel notions of their beauty.

Sewing is an expensive enough hobby without having to factor in repair costs, as well. You can save money (and have more cash to spend on fabric and notions!) by fixing your own machine at home. This video shows you how to clean and fix the bobbin case area, which can often get cluttered with lint and fuzz.

This is a fun project that doesn't take much in terms of time or resources. You can even make it out of your scrap fabric! Use whatever notions or embellishments you want to create a lovely, Victorian inspired pillow at home.
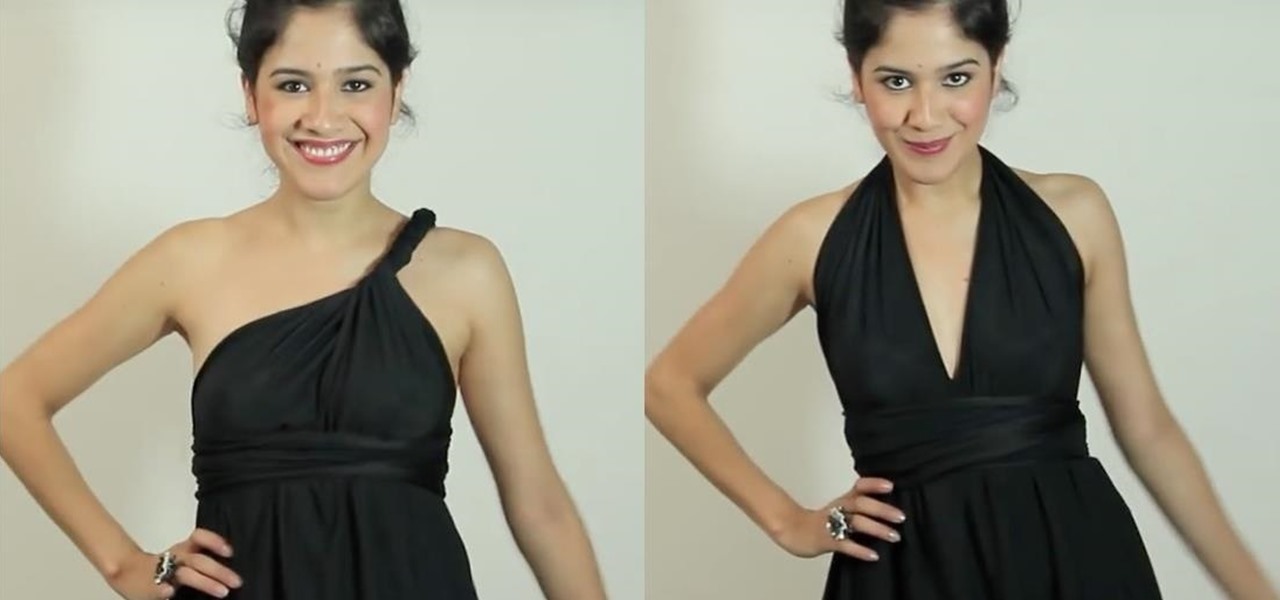
This dress can be wrapped, draped, or tied any way that suits you, depending on where you're going. Choose a lightweight fabric, like silk or satin, when you're sewing this dress. All you need is a few yards of fabric and your usual sewing notions.

Perfect for the holidays! Make a quick and easy red hoilday dress, with white fur trim! Dress it up with a Santa hat, and you have the perfect dress for holiday festivities! You don't need anything special, just a few notions and a sewing machine.

A welted pocket (also called a jetted pocket or piped pocket) is a pocket where it appears just to be a thin slit in the fabric of the garment. Ideal for when you are making something you want to have pockets, but don't want to necessarily draw much attention to them - such as tailored suit jackets or streamlined dresses. All you need to learn this technique are some basic sewing notions (scissors, pins, etc) and either bias tape or the ability to cut your own bias tape from your fashion fabric.

Despite all the glitz and glamour of the '20s, flappers were more than anything else dressing the scandalous way they were in order to look like men. They flouted traditional notions of female beauty by binding their breasts, wearing sheaths that disguised their feminine curves, and wearing hemlines up to there.

Don't be intimidated by this couture technique - it's actually quite easy! Sew a silk ribbon binding to your project as a way to stabilize it. All you need is the ribbon, your fabric and a few extra sewing notions.

We've always thought that supersized everyday items were cool, like a 4 ft. tall pencil or scissors so large they could cut a posterboard in half in one snip. But few of these supersized notions are practical.

These ornaments make a great embellishment to any Christmas gift or present, and are easy to make out of scrap fabric. You can also use them as a tree decoration! All you need, besides a few sewing notions, is some heavy cardstock.

A quillow is a blanket that, when folded, can serve double duty as a pillow. You will need fabric for the front and back as well as some batting and regualr sewing notions. This is a great Christmas or holiday gift even a beginner can make!

This is very easy to follow project you can use to sew a cute, stylish pillbox style hat. All you need is some stiff fabric, a few sewing notions and then whatever embellishments (like ribbons, flowers or applique) you want to attach to the sides.

Crafting and sewing is lots of fun, but it calls for many accessories and notions that can clutter your craft area. This tutorial shows you how to create your own craft supply organizer out of some upcycled or recycled materials.

Upcycle your old T-shirts into a classy and fashionable corset top! All you need are some basic sewing notions, in addition to eyelets and eyelet pliers. Embellish your corset top with ribbon, appliques, rhinestones or any other accessory you fancy.

This tutorial shows you two different techniques for creating a boning channel when you're making a corset. You will need the corset boning and a pressing bar, along with some bias tape (or the ability to make your own) and a few other sewing notions.

This is a great and attractive shirt - a corset tank top. You don't need a pattern to make this, just some fabric, lining and ribbon. You'll also need some basic sewing notions and access to a sewing machine to sew this very basic item.

This is a great project to make a fun and feminine shirt. All you need is one piece of fabric cut in a circle, a few basic notions and a sewing machine. No pattern required, just make sure you have your measurements at hand!

Make your own pyjama knickers! This is a great tutorial that a beginning sewer can use to hone their skills. You don't need very much fabric - just some elastic and a few basic sewing notions as well as your sewing machine.

Love the look of vintage? You don't have continuously prowl vintage stores - make your own inspired skirt! All you need is your favorite fabric and a few sewing notions (matching thread, scissors, pins, and of course, a sewing machine).

If your jeans have worn out from wearing them all winter, don't throw them out! You can easily recycle them into a cute pair of summer sandals! All you will need, apart from the jeans, are a few basic sewing notions.

Start with an old pair of jeans and some scrap fabric. Then, using a few small sewing notions (scissors, thread and a decorative button) and the pattern given in this video, transform this old fabric into a super cute and useful lined handbag.

It's Christmas season, and that means it's time for holiday parties! This tutorial shows you how you can make a fun and festive dress for your upcoming holiday celebrations. You will need approximately two and a half yards of fabric, in addition to a sewing machine and the regular notions.

Oh, consider those veggies… consider young Percy! How he craves his dessert, please P.B., show him some mercy! Save the child, P.B.! Get the solution to the "Citizen Clone" puzzle in The Misadventures of PB Winterbottom.

Please permit us, dear player, to expand your dim view. See how Bakersburg suffered thanks to P.B. (and you)! Get the solution to the "Busted Cretin" puzzle in The Misadventures of PB Winterbottom.

In this tutorial, we learn how to write a literature review for thesis writers. The three elements are: discuss the most relevant theory, introduce and define key terms, and discuss recent research in the field. You will need to include the most important literature, quote directly only if you discuss at some length, and use indirect quotes as well. Focus on notions you will use in your empirical study. It should be ten pages or less and sources of all quotes must appear in your works cited p...

Is your BFF getting married? Looks like you have a bridal shower to plan! Organize a bridal bash that people will actually want to attend using these innovative ideas.

You don't need to be an expert designer to make your own clothes, only the patience to work step by step. This video will show you how to follow a sewing pattern.

This year, as part of the Next Reality 30, in partnership with Snap, we're spotlighting an up-and-coming innovator in augmented reality. Specifically, we were searching for an independent developer or creator who embodies the bleeding edge spirit of AR and its ability to leverage machine learning. This year's honoree is Aidan Wolf.

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

It's common knowledge that certain foods foster brain development, health, and memory. Fish almost always makes the list, as do any foods that are loaded with antioxidants like blueberries, nuts, whole grains, green tea, and dark chocolate. Spices like turmeric are being studied for their ability to prevent Alzheimer's, among other things.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

This is a quick and easy tutorial, great for anyone interested in learning how to make their own designer handbag. Add in a zippered pocket to the inside lining of your handbag. You will need a window stencil and a craft knife as well as your notions. Add a zippered pocket to the lining of your designer handbag.

Carly Waito's beautifully rendered oil paintings of minerals totally inspire me to pick up a brush and start painting.

Kevin Van Aelst creates witty visual "one-liners" by recontextualizing everyday, ordinary objects. With a few simple tweaks, the viewer recognizes a roll of tape as the ocean or reads gummi worms as chromosomes or understands mitosis through the use of sweet, sugary donuts.