A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.
Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.
This clip discusses how authorization roles work and their role in the security of the latest release of the F5 Networks Management Pack suite. It also touches on the creation and use of user roles within Operations Manager console and how to apply the authorization tasks to those roles. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with F5 Networks Management Pack suite, you're sure to benefit fro...
In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
See how to use the PCI compliance reporting functionality within BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

This video tutorial shows you how to create a pink and teal eye look. 1. Apply primer over entire lid (use concealer if you do not have primer)

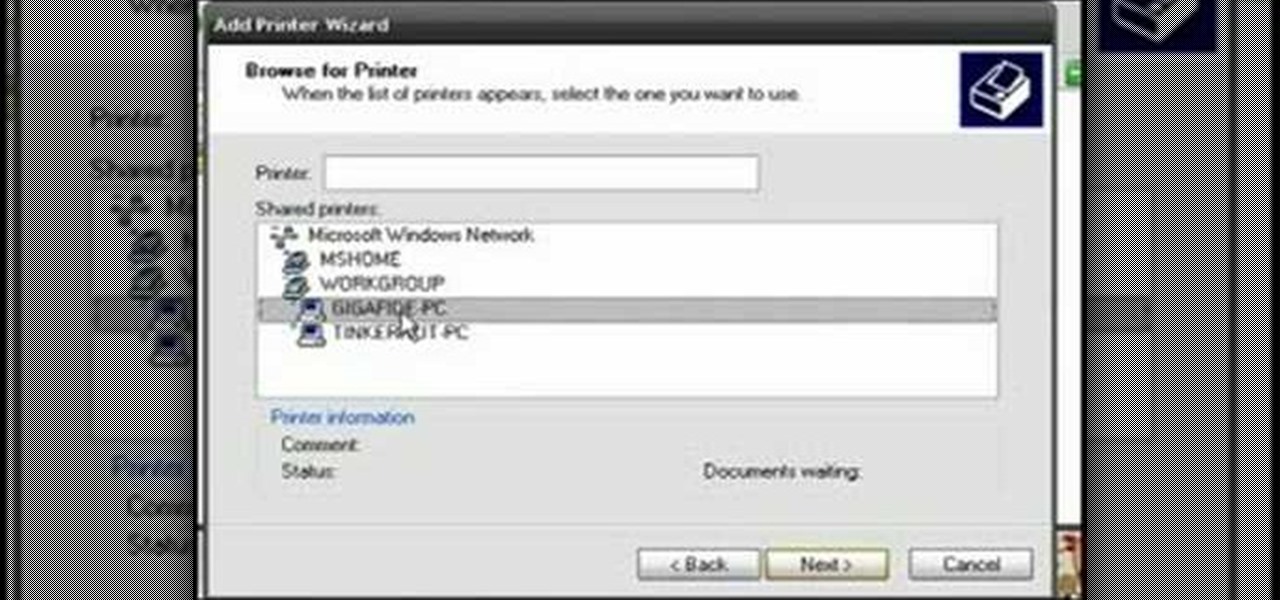
Odds are you have more computers on your network than printers. This video lays out the steps for sharing a printer over a network. This tutorial assumes that the printer is installed on another computer and not connected directly to the network. Take a look!

No wireless router? There is a way to network your computers by using your existing power-line. This CNET video will show you how to set up a power-line network - it's not as sexy as a wireless network, but it's easy and reliable!

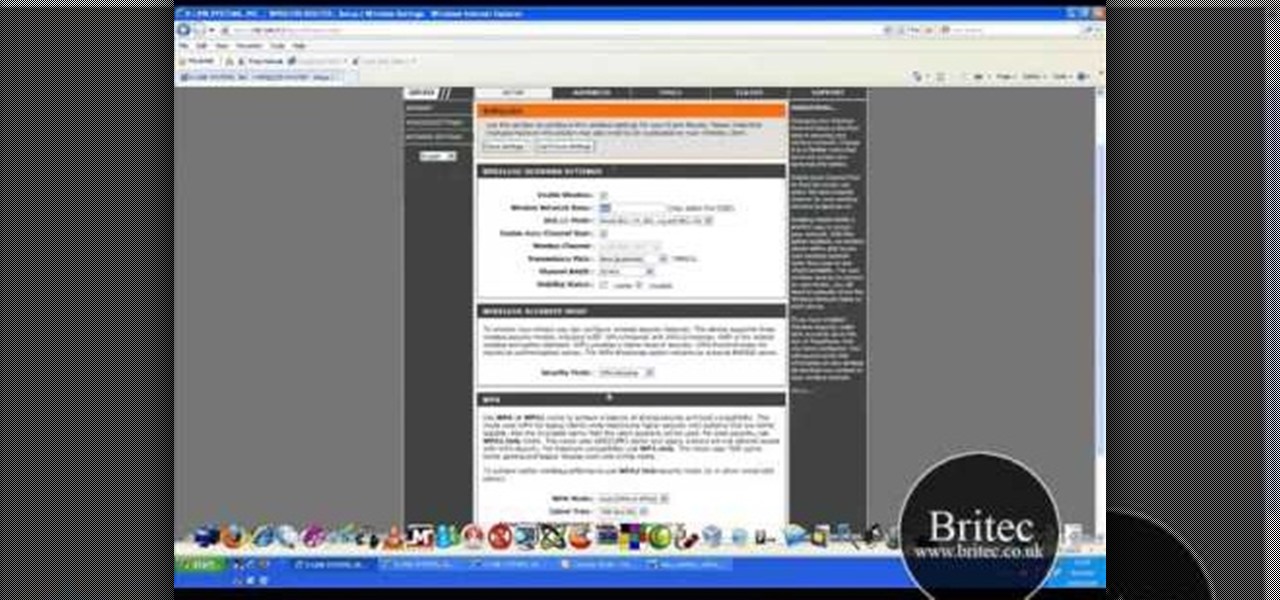
This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

The wait is finally over. Apple just released iOS 13.2 for iPhone, the latest update to this year's iOS 13 release. The update contains a slew of exciting new features, such as Deep Fusion for 2019 iPhones, a suite of new emojis, the long-awaited Announce Messages with Siri, among many, many others.

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now that you know this, you should upgrade to WPA! It is much harder and takes much longer to crack.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

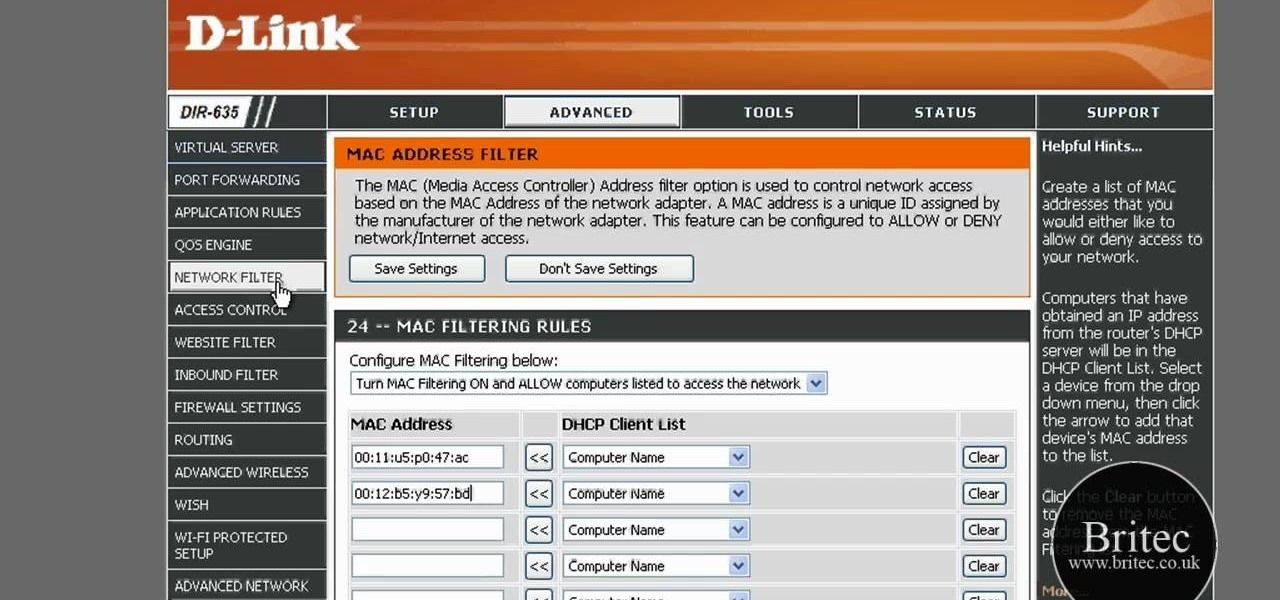
The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in setting up a WiFi network in your home or office? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started configuring your own wireless network, take a look.

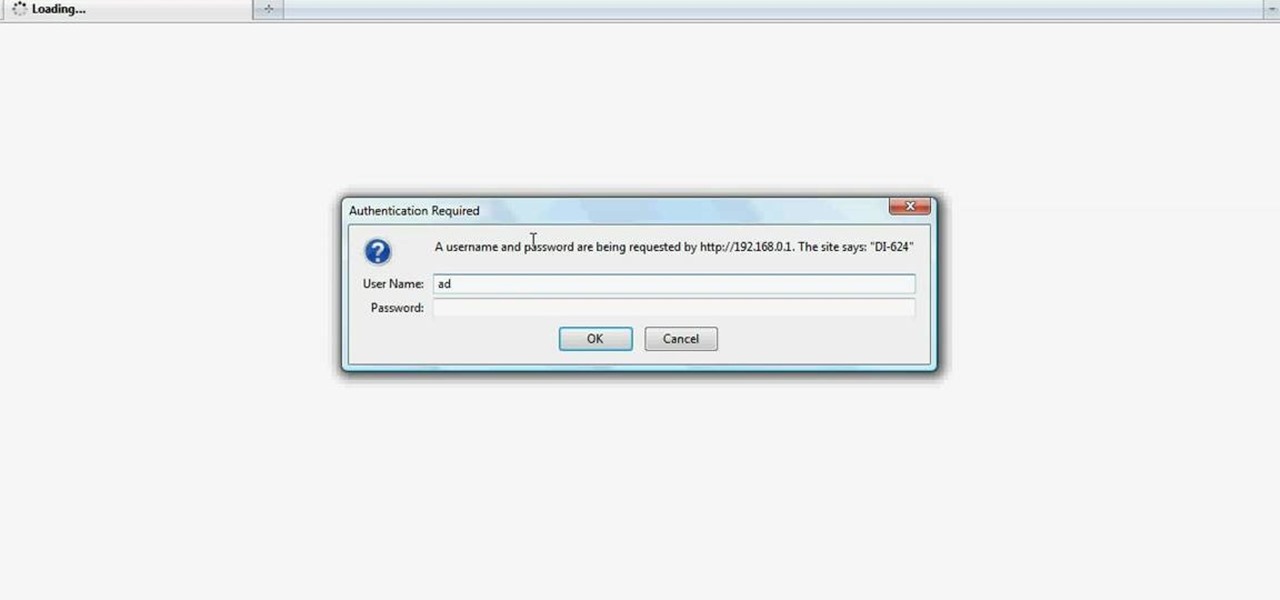
In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Want to set up a wireless network in your home or office? It's simple. So simple, in fact, that this free networking how-to presents a complete overview of the process in just over four minutes. Set up a WiFi network with this video guide.

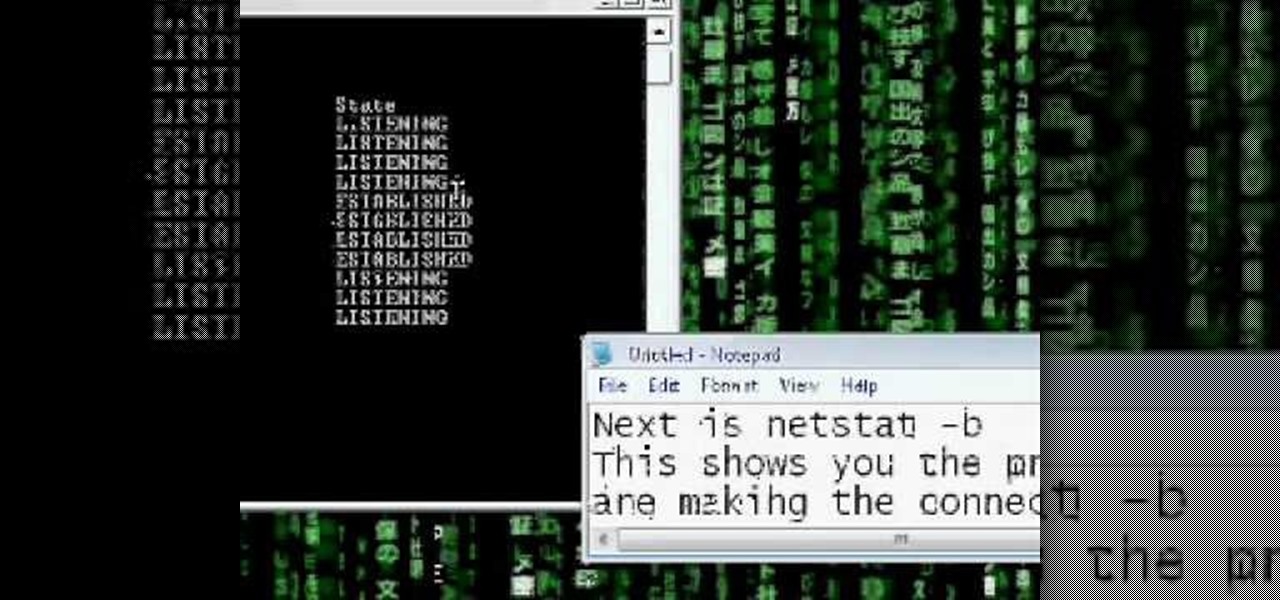
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

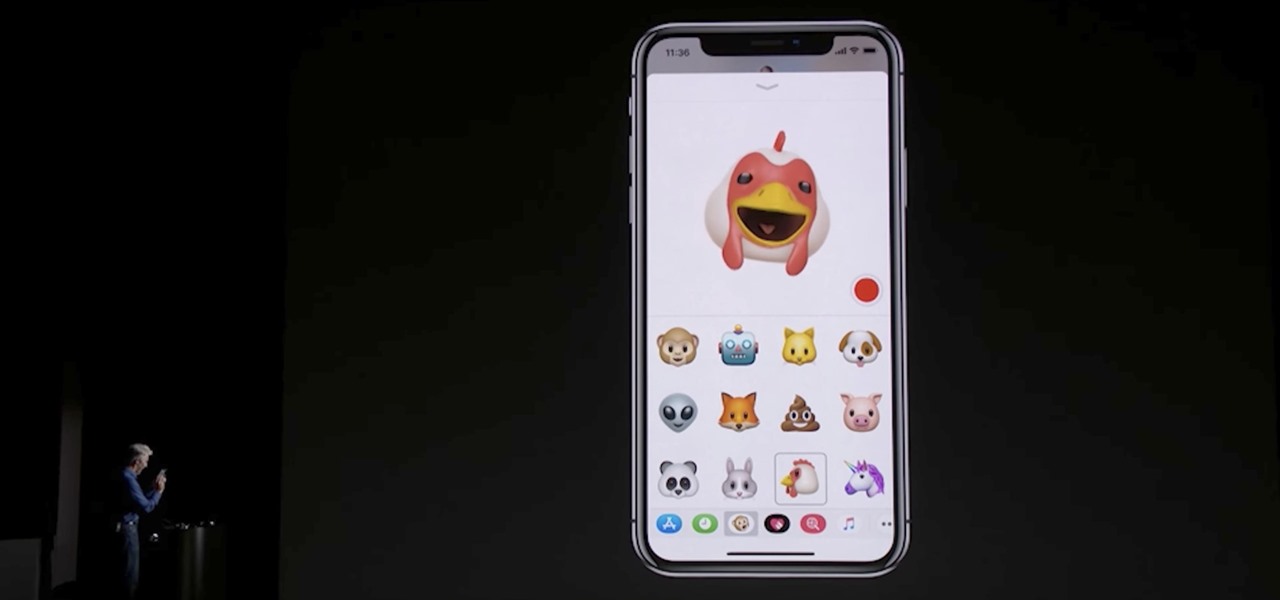
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Many wonder how driverless cars will ever be able to navigate through any driving condition imaginable — but the point is self-taught machines, in theory, have the innate ability to adapt to chaotic and extreme driving conditions in ways far superior to what humans are capable of.

A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

While the technology continues to mature, businesses from various industries continue to adopt augmented reality to improve the efficiency of business processes. In this edition of Brief Reality, as conference season continues, we see examples of augmented reality applied to logistics processes and marketing of industrial supplies, as well as the topic of discussion at another trade show.

It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.

After Apple unveiled ARKit 3 at WWDC on Monday, Unity Technologies wasted little time on ensuring its developers can take advantage of it.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.