Interested in setting up WiFi in your home or office? This tutorial will show you precisely how to set up your own wireless network. Before you begin, make sure you have the following: (1) a wireless-enabled computer, (2) a wireless router, and (3) a modem.
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Mike Biggly shows us how to set up our home internet and networks. Part 1 of 20 - How to Set up your home internet and network.

In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

TheUMLabs shows how to setup a wireless network with Ubuntu. The first thing the user does in this task is open Hardware Drives. After the searching for drives box finish scanning it list available drives to install. This s then selects a driver that is available to the computer they are working on. The next thing that the user do is edit the Wireless connection. If you follow all of the steps in the video, you should be able to connect to a wireless network in Ubuntu.

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

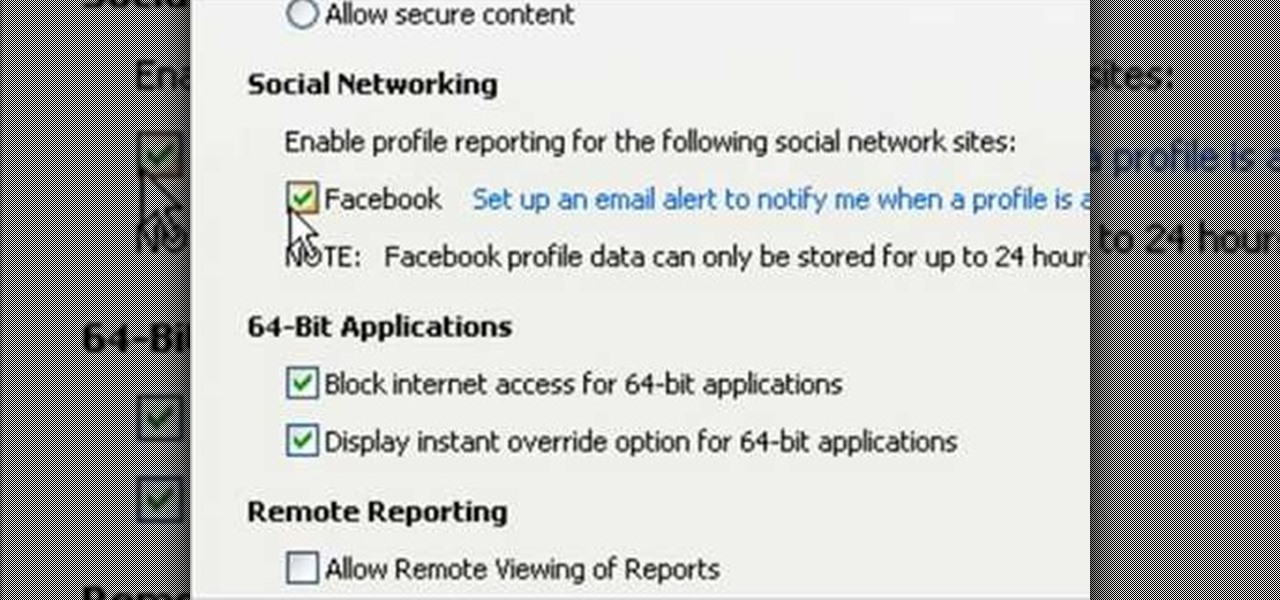
Danny with Top Ten Reviews will show you how to monitor social network activity with the Net Natty program. This will be helpful for monitoring social networking accounts on websites such as Facebook and MySpace. First, open Net Nanny. Go to the dashboard and select Additional Settings under Filtering. With this section, social networking sites that have been used on the computer will be listed. You can check whichever account you want to monitor. Under the dashboard, go to Reports and select...

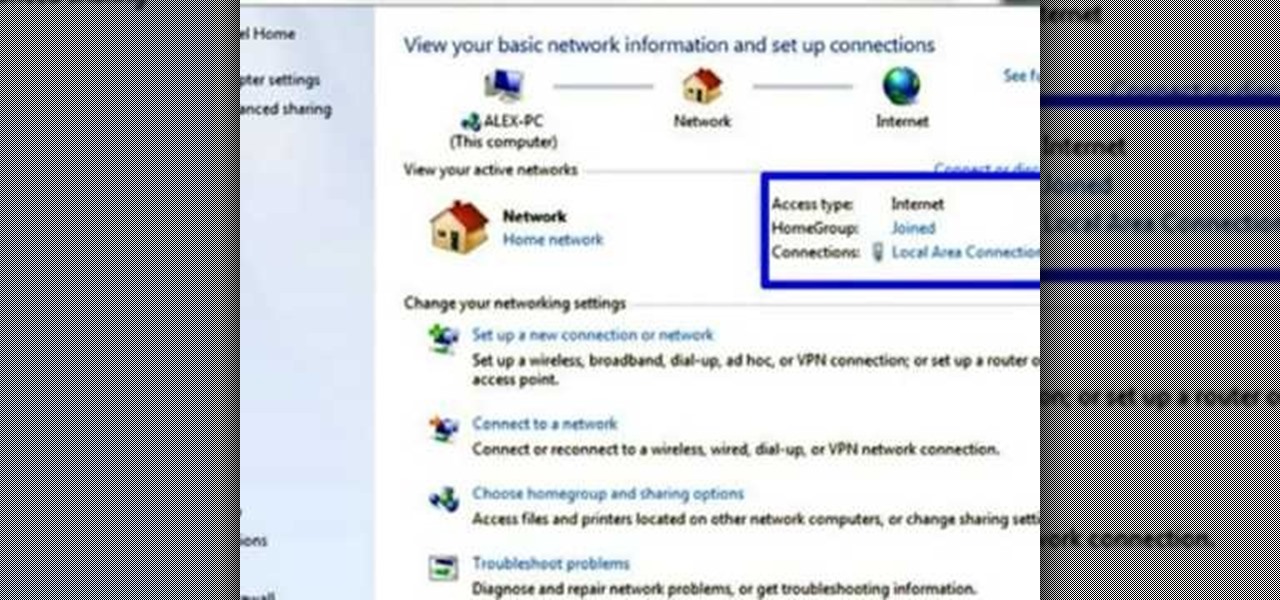
This video tutorial will teach you how to troubleshoot a HomeGroup network in Windows 7. In order to do this follow these steps: Go to the Start Menu and then go into Control Panel. Now go to Network and Internet and then in Network and Sharing Center. Now click the Troubleshoot Problems link located on the bottom of the window. Here you can select which part of networking you want to troubleshoot, in this case select HomeGroup. A process will start and you will have to answer the questions t...

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

Set up your network storage system with the help from a kind of creepy blonde woman. Great tutorial though. Easy to follow. Set up a nas200 network storage system.

Most of you are familiar with using Ettercap for attacking systems, but what about using it to find attackers? This tutorial will cover using Ettercap to find people sniffing on your network. The plug-ins we will be using are search_promisc, arp_cop and scan_poisoner. Have fun detecting network sniffers. Detect hackers on your network with Ettercap.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

Want to access files from multiple computers at work or home? An expert from PC Remedies explains how to set up a Home Group network on Windows 7 systems. Includes a how-to of setting up your location, and managing the set-up wizard. Finally maximize your current resources by networking your work and entertainment files, as well as hardware such as printers. The excellent video gives you an exact snapshot of what you can expect to see on your own Windows 7 system. Includes advice on setting u...

How to send pop-up messages to friends on a local Windows NT network. Send pop-up messages to friends on a Windows network.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

A tutorial showing how to send messages in a Windows-based network without any programs. Send messages on a Windows network with the cmd prompt.

Wireless can be a pain sometimes with video games on the Internet, with disconnections and signal losses, but why not revert back to a wired connection? This video will explain how to connect your Nintendo Wii to a wired network using Actiontec Powerline Networking technology. This will enable your Nintendo Wii to connect to the Internet to download games, console updates, and other information.

How to use Cain & Abel software to intercept passwords from an unsecured network. Intercept network passwords with Cain & Abel.

InfoWorld has some expertise advice for the new Windows 7 operating system from Microsoft. Now that Microsoft has made the Windows 7 beta available for public download, many people are trying to figure out what's new and different. And many others not willing to risk their PCs by installing a beta OS are curious, too.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

You may not know him by name, but Eric Leebow is the man we can all thank for inventing social networking. At least, that's what he thinks.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

In this video tutorial, viewers learn how to make a crossover cable from scratch. Users will need an Ethernet cable. Begin by removing one side of the connector and strip off the outside casing. Then separate the wires. Change the sequence order of the cables to: white green, green, white orange, blue, white blue, orange, white brown and brown. Make the cables straight and close together. Then cut off about half of the wires and carefully put back on the connector. Use pliers to squeeze the c...

People are very opinionated about what version of Microsoft they like. Some people love the easy-to-use nature of classic Windows 2000 and stick with that, whereas others love the upgraded, super sleek Windows Vista version which has its faults but at least looks amazing.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Sometimes shit goes down on your home computer and you're just not able to be home to fix it. After all, most of us have commitments such as school, work, and volunteer activities that keep us away from our home computers for most of the day.

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.

A custom application directory partition is a method of dividing your DNS servers for replication, and allows replication to occur between domain controllers. This video shows you the process of setting up your own using Windows Server 2008, though it will also work for the 2003 version as well.

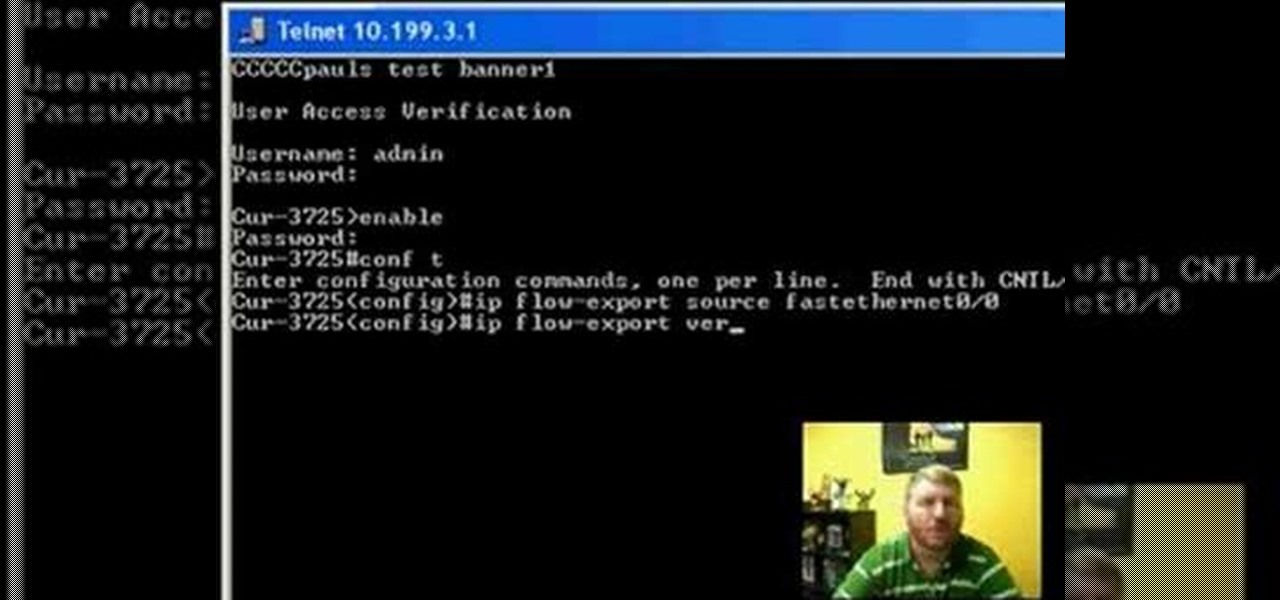
Netflow technology allows you to monitor web traffic to your website - find out who comes to your site, where they're coming from and where they go afterwards. You can configure a Cisco router manually to monitor netflow going through the router.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...