Want to write Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will help you on your merry way to accomplishing just that. Specifically, this lesson will demonstrate how to work with event handlers when coding in Java. For more information, including detailed, step-by-step instructions, watch this programmer's guide.
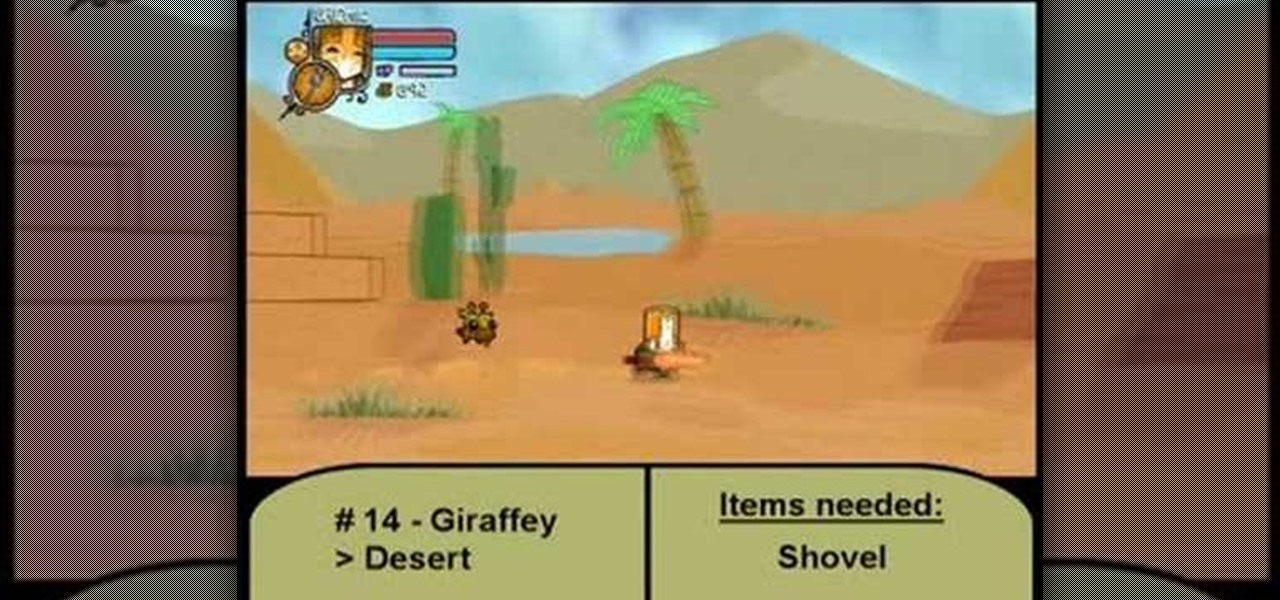
For all you achievement hunters, getting absolutely everything is key, and some of the pets in Castle Crashers are hard to find if you don't know where you're going. Let this video show you the way! It'll give the locations, and items needed, of all 26 animals that you will need to get the "Animal Handler" achievement and a cool 20G!

Ultra violet lights can easily be installed in your air handler to reduce the airborne bacteria and molds in your home. Check out this instructional appliance video that shows how easy it is to install one. Just follow the step by step instructions and you'll be able to install ultra violet lights in your air handler.
In this video tutorial, Chris Pels will show how to create event handlers for ASP.NET web pages and web server controls. First, learn how to create page level events for the standard page events provided by the .NET Framework. See how to automatically bind the events to a page using the AutoEventWireup attribute as well as programmatically bind the events. Next, learn how to create and bind event handlers for the standard web server control events. Also learn how to connect multiple events fo...

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.
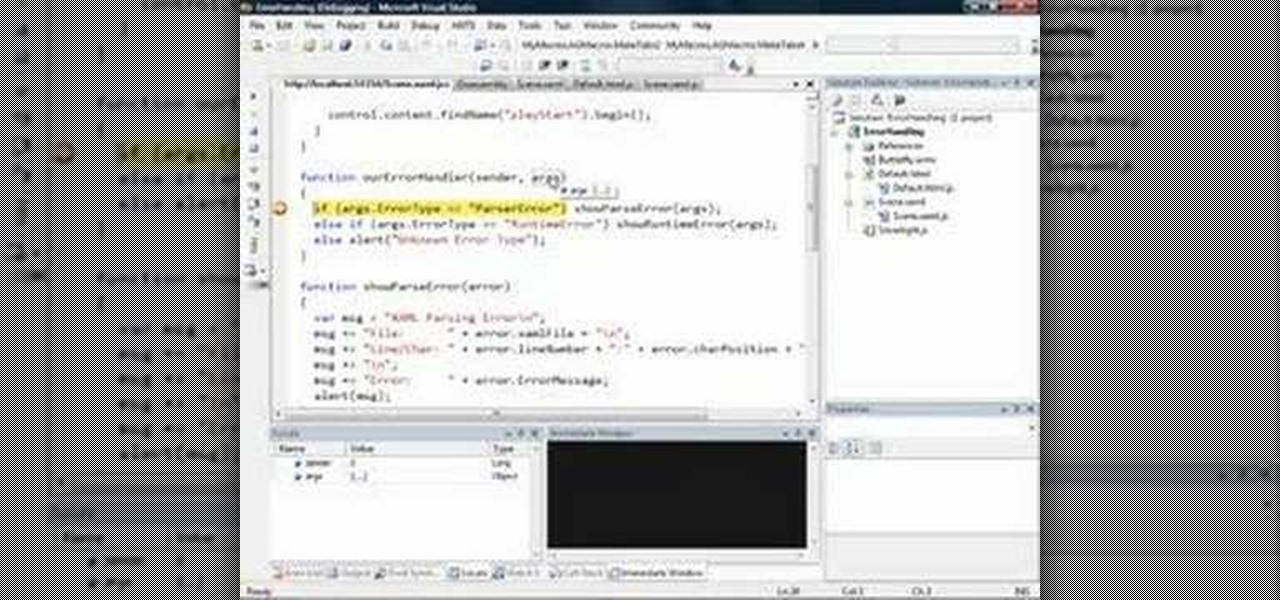
In this web application tutorial you will learn how to set up error handling using Microsoft's Silverlight developers tool plug-in. This tutorial will be helpful if you want to create your own error handler instead of using the default handler set up by Silverlight.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...

Reddit user craigyboy2601 knows a thing or two about airline baggage handlers. After all, he is one. So, when he offers some tips on how to protect your luggage from loss or damage, you should probably pay attention! Here are the highlights from his post.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Here's a fast lesson in hosting video on your own Drupal website using the FileField and jQuery Media modules. The Filefield and jQuery Media modules are a one-two knock out combination for allowing users to upload media files to fields in your custom content types and then playing back the media files in their matching player or handler. It represents a positive direction for treating fields containing files and is a great starting point for researching your own implementation of this recipe.

In this video tutorial, Chris Pels will show how to create an Application Class File (Global.asax) that contains application level event handlers such as Application_Start and Application_BeginRequest. Then the sequence of application level events in the application lifecycle will be discussed as a basis for determining where certain types of operations would be best performed during the application lifecycle.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Chrome's Incognito Mode is a great feature for folks that don't want their browsing history tracked. When it's enabled, Incognito Mode makes sure that all cookies and cache that are saved while you're browsing are deleted as soon as you leave a webpage.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Horses don't kick their owners and handlers unless they think it is okay, or unless they think there won't be any repercussions for their actions. The gentleman in this video shows you that being gentle with your horse can go a long way!

In this video tutorial, Chris Pels will show how events are handled in master and individual content pages. Even though the end result of a master and individual content page is a single ASP.NET page rendered in the user's browser the event handling in each type of page is handled separately. If a control is located in the master page the corresponding event handler is located in the master page by default. The same is true for controls in the content page. See two approaches to having the ev...

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

The video shows a unique method of solving a Rubik's cube. The method is called F2LL or 'winter variation'. There is very little information about this method on the internet. It deals with Corner Orientation. The person in the video is a skilled cube handler. There are 27 algorithms and their mirrors in the F2LL method. While you form an F2LL pair, you need to orient the corners at the same time. This method makes cube solving all the more easy.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

When on-screen buttons were introduced alongside Android 4.0, it didn't take long before Google added a gesture to these virtual navigation keys. Since then, an upward swipe originating from the home button has always been a shortcut to Google Now on Nexus devices.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

One of Android's strengths when compared to other mobile operating systems is its ability to set third-party apps as the default handler of certain file types. Instead of being stuck with pre-installed system apps when it comes to opening files and links, you're free to choose a better-fitting alternative.

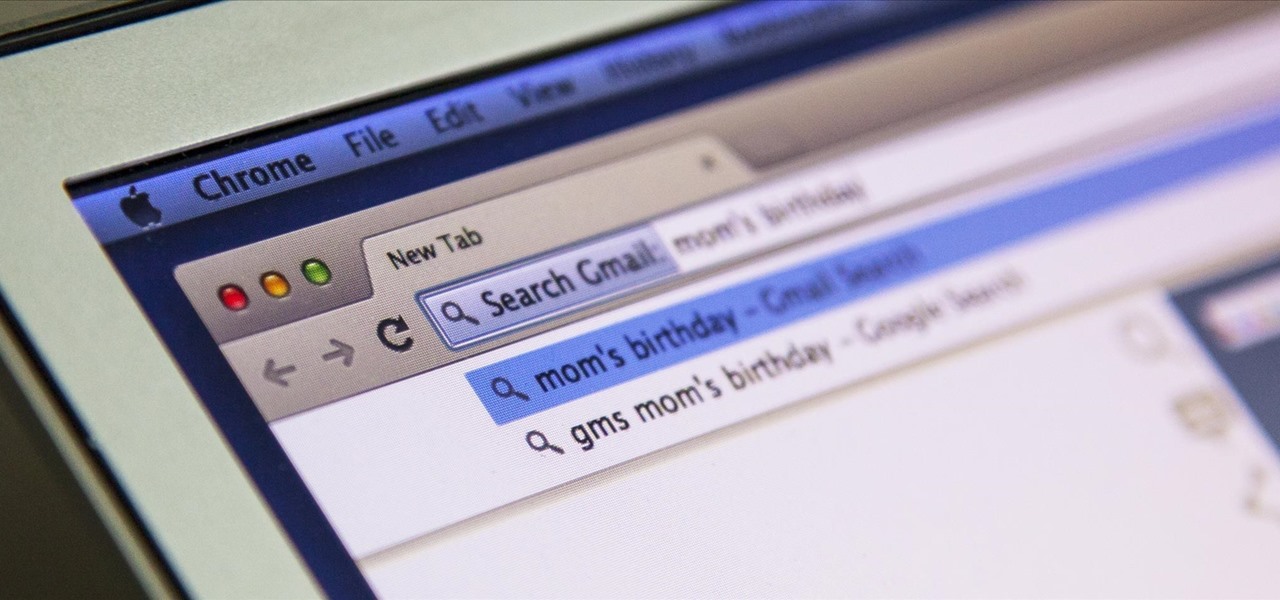
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Almost all modern Android devices have a gesture that will take you directly to Google Now. For most phones and tablets, it's a simple swipe up from the home button. With a Samsung or an older Android device, it's only a matter pressing and holding the home button.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Figure out the 17th puzzle, entitled "The Bunker", in Assassin's Creed 2. Code wheel puzzle: Here’s a tricky one; your clues are “<” and “2,” and the only advice you’ll get from your handlers is that maybe there’s “something we can count” on the strange symbols. In this case that “something” is the number of times each symbol bends sharply. Don’t expect consistency across the wheel on this one; just take a look at what symbols flank the blank spaces and pick a shape with the number of bends t...

Cacti have spines that prick the handler's skin. So how do people in the cactus business handle spiny cactus all day long? They use nitro gloves! Watch this instructional video for a demonstration on how these special gloves prevent gardeners and cactus growers from getting pricked.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

Norovirus outbreaks occur all year long, but peak in the winter months, which means we are in the middle of norovirus season. But there's still time to protect yourself from the highly infectious bug.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

Apple's keyboard has a set of media controls to navigate the music playing on iTunes, allowing you to play, pause, skip, and replay songs and videos. Unfortunately, these controls are exclusive to iTunes; if you're playing music from Spotify, Pandora, or the myriad of other online web-based services (Amazon, Rdio, SoundCloud, etc.), you're out of luck.

First of all you have to check the breast collar which is attached and hanged to the saddle. You have to maintain safety by not ducking under the horse neck. It is better for you to go around and do your job. Keep your head away from the horse head while attaching a collar. Ask your handler to hold the horse for you. Now pick your breast collar up and reach around the horse. Don’t duck under the horse head, but bring the collar belt to your side and then attach it to the ring on the saddle. N...

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.