I'm a long-time and loyal Android user, but one iOS feature that I'm truly envious of is their keyboard shortcuts, which lets you assign a short macro that inputs a longer phrase. For example, typing "home" can input your home address.

Some apps have a nasty habit of ignoring your Android's auto-rotation settings and locking the display into either portrait or landscape orientation.
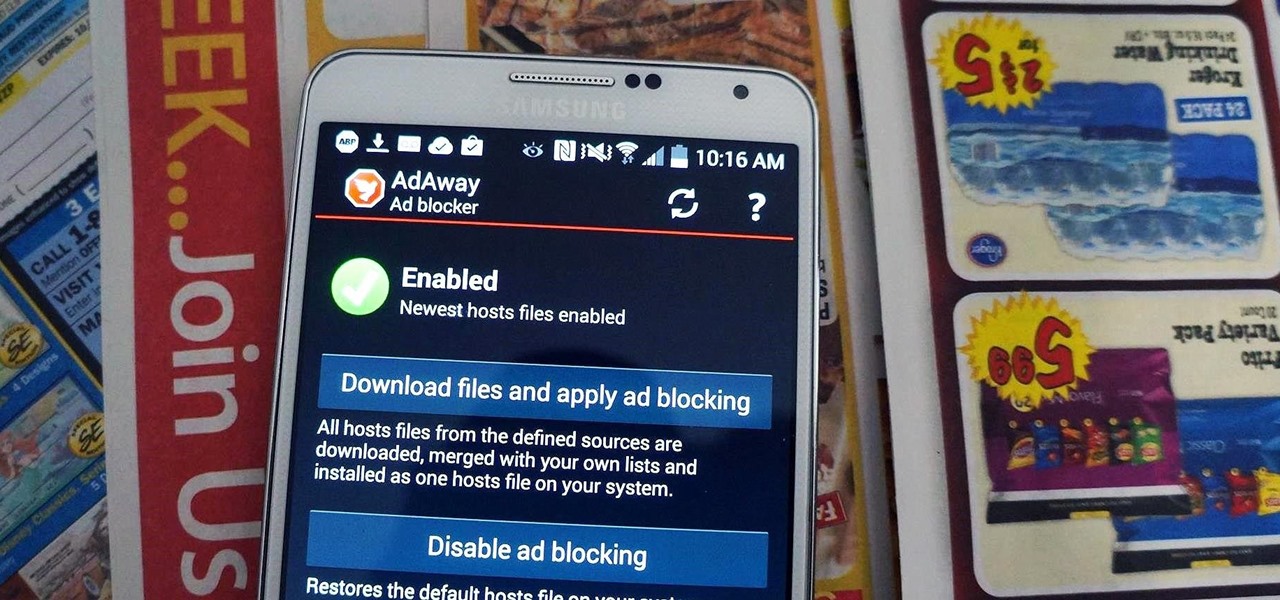
The Play Store is loaded with just about any app you can imagine. While many are free or have a "lite" version of a paid app for download, often enough, these freebies have intrusive ads cluttering up your screen.
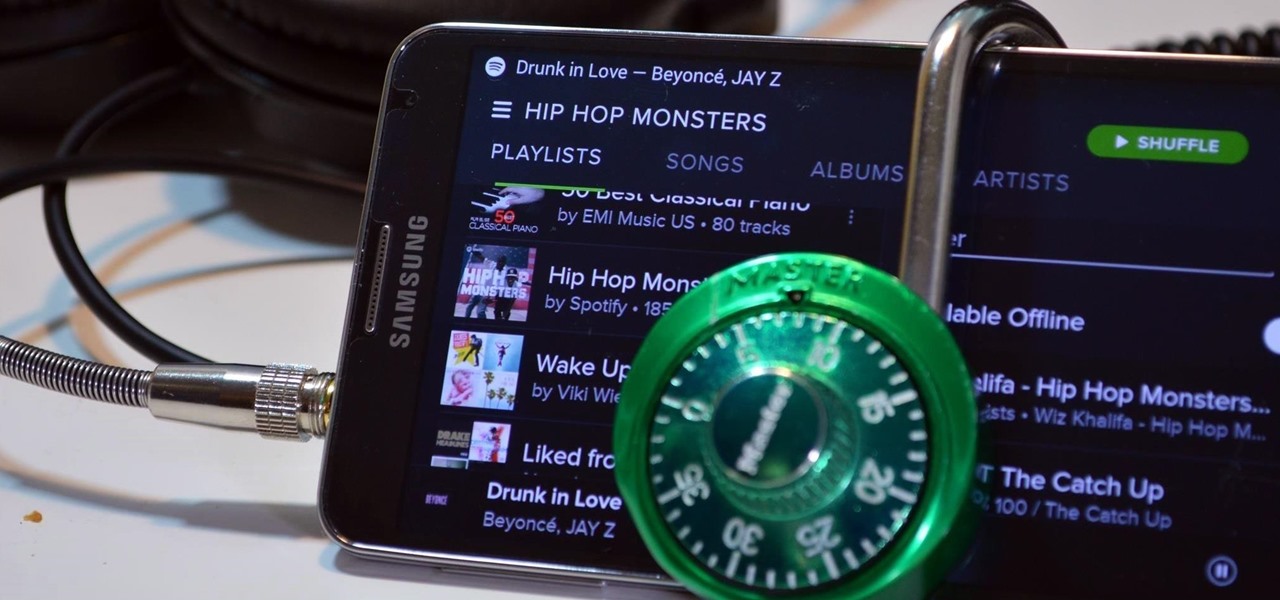
With over 20 million songs, Spotify has become my go-to source for music. I can stream tunes to my desktop or phone, without ever having to worry about storage space being eaten up.

Normally, it's good to automatically update your apps to the latest version, but sometimes those updates take away features that you've grown to love.

There's a lot you can access from the Notification tray on your Galaxy S4. Quick settings toggles, brightness controls, and of course, notifications. However, despite the power this simple pull-down gives you, you're still left with a boring, black background for the shade.

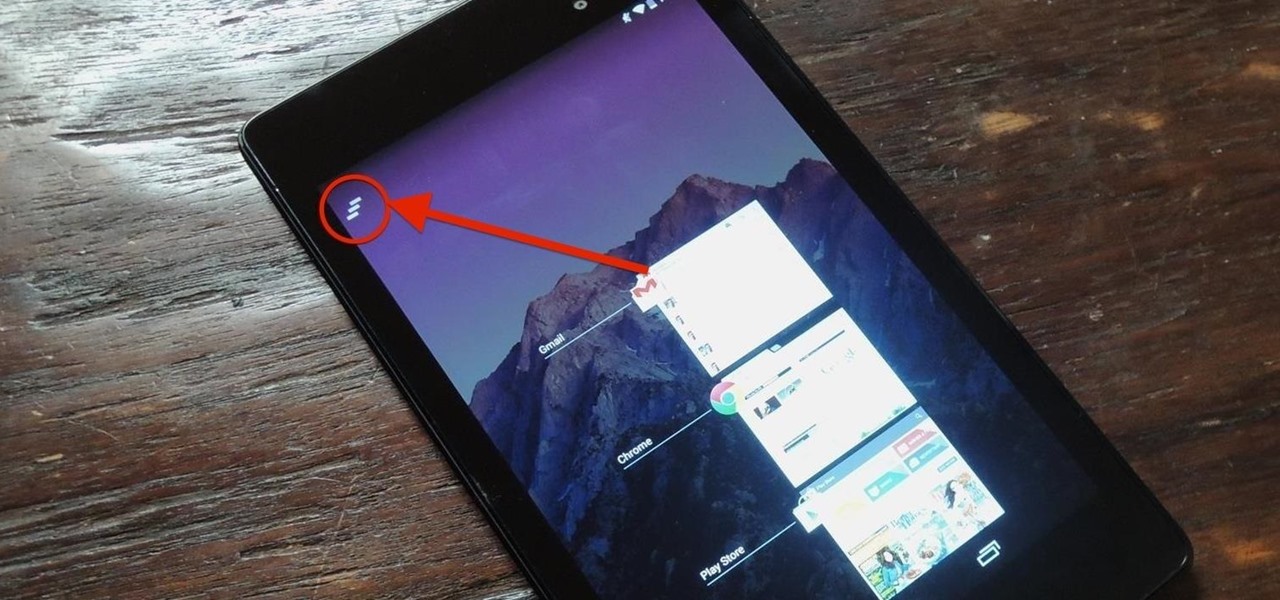
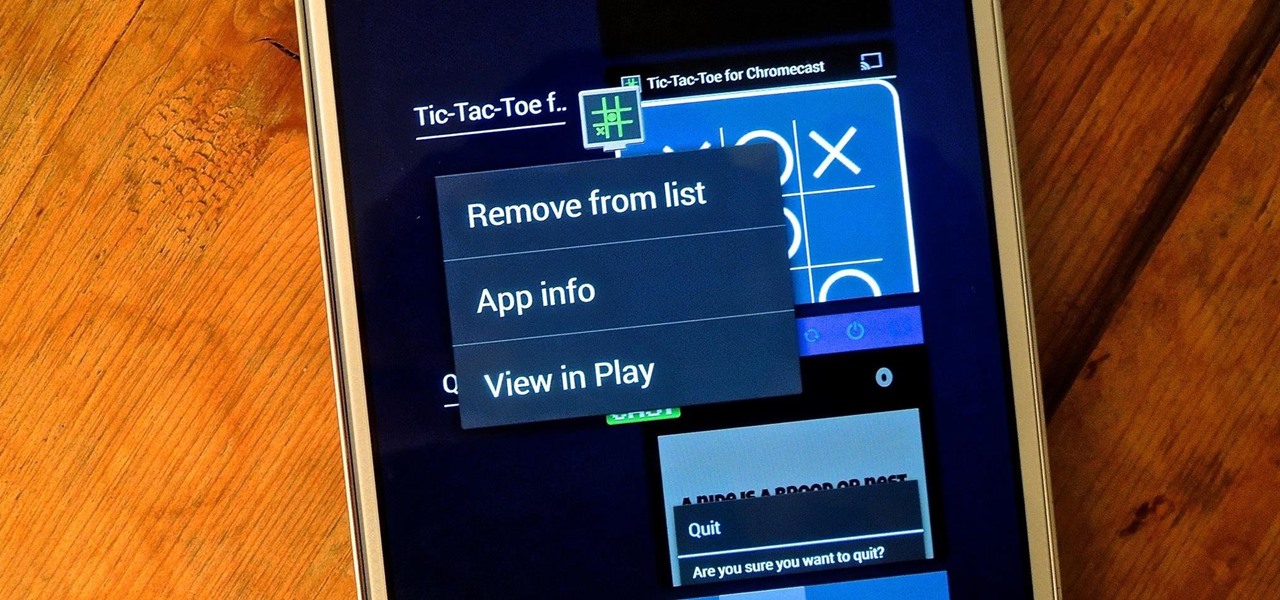
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its non-obvious setup and lack of features.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

I love my status bar. Not only does it tell what time it is and how much battery juice is left, but it gives me cellular connection info, text alerts, and app update notifications. However, one thing is does not give me is customization. Since you're looking at it all the damn time, why not personalize it?

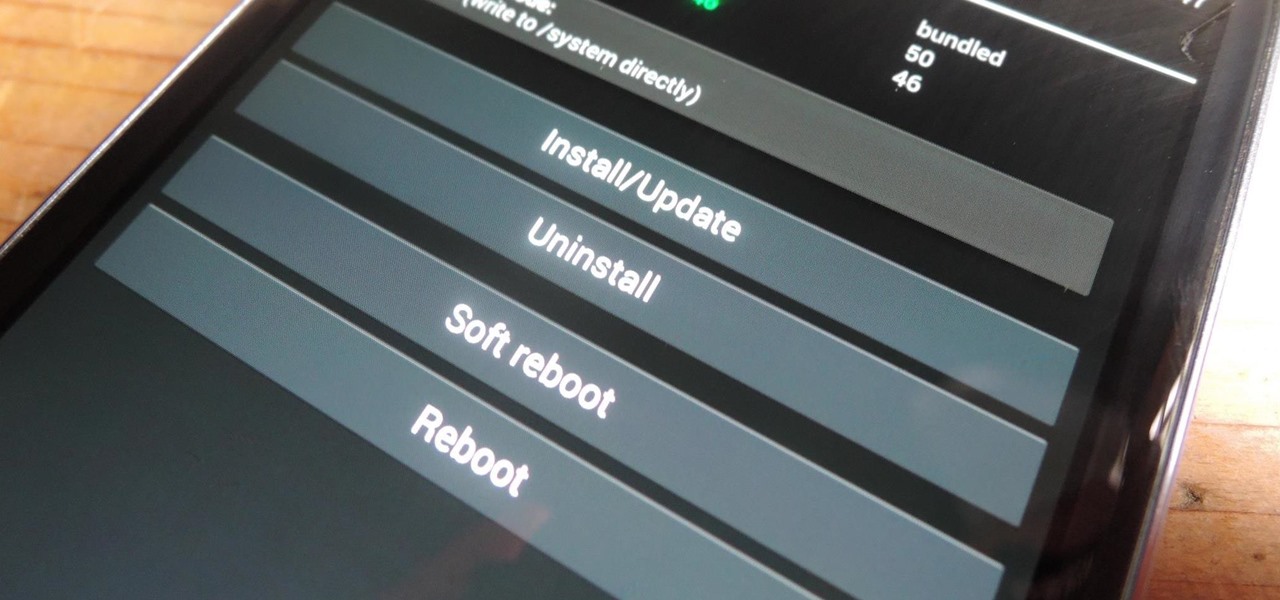
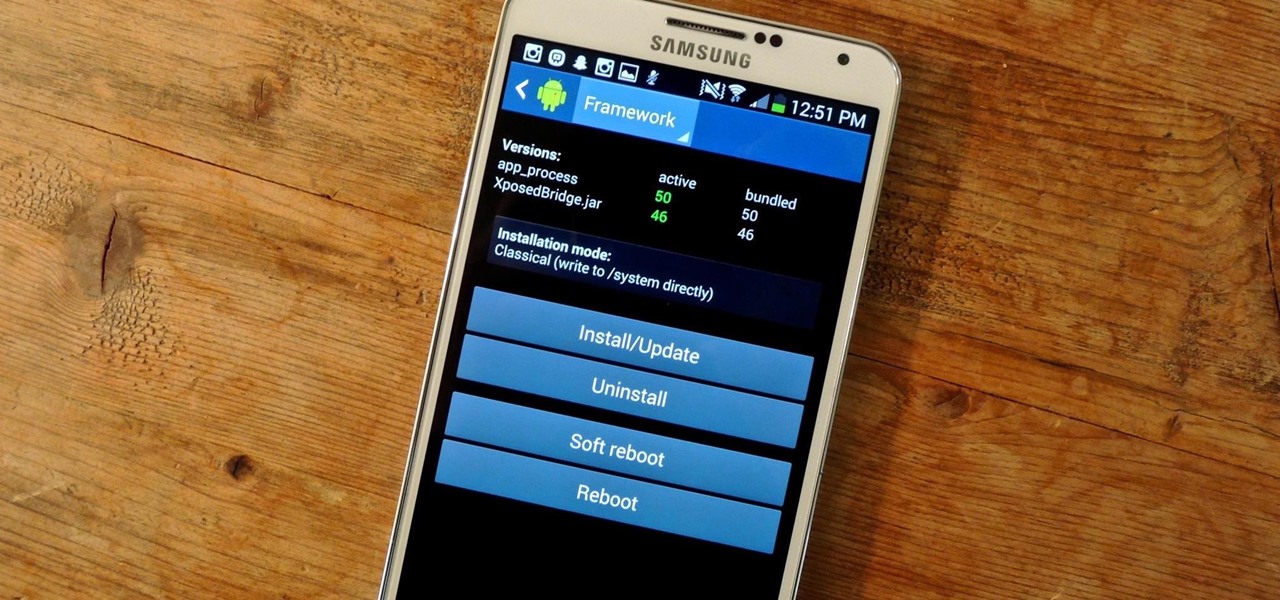
Created by by XDA developer rovo89, the Xposed Framework allows you to quickly search for, download, and install new modules that allow various forms of customization for your Android device.

Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.

Android is all about the fine details. You can make a little tweak here and a little tweak there and completely customize your experience to be exactly how you want it to be. Sure, you don't need to customize LED colors or screen record, but it's nice to know you can.

On more than one occasion, I've wanted to check out the Google Play page for an app I was currently using, whether it was to get contact information or read recent reviews to see if others were experiencing issues that I was.

When you're scrolling through your iPhone's home screens, you'll inevitably reach the end and have to either swipe backwards or hit the Home button to return to the first page. Why Apple didn't instill an endless scrolling feature, or at the very least an option for it, is anyone's guess, but just because you can't do it out of the box doesn't mean you can't do it.

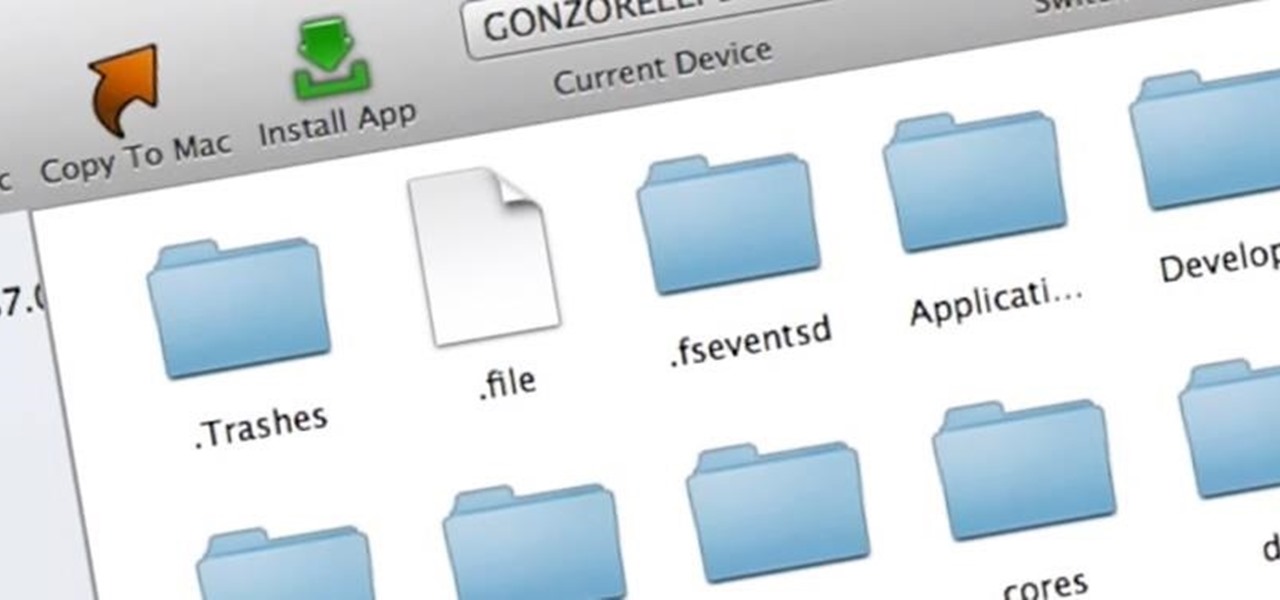
There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly onto your device and installing it with iFile.

While browsing the internet on your Samsung Galaxy S4, you've probably scrolled to the bottom of a very long webpage, Twitter feed, or down into the abyss of some other app. Depending just how far down you've scrolled, it can be a test of your patience (and fingertips) scrolling back up to the top.

While Siri may be the cream of the crop when it comes to smartphone personal assistants, there is always room to grow bigger and better (that's what she said). Siri, although recently expanded, is still lacking in the amount of commands and actions she can currently perform. While looking up directions and restaurants is fairly easy for Siri, asking her to gain access to third-party programs or browsers is a little more difficult.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Software issues occur more frequently on jailbroken iPhones, though, they're usually minor bugs that can be fixed easily with a respring. But if your device freezes up, restarting is the only way to get back to normal, which also means having to re-enable your jailbreak. There is one way, however, to respring without interacting with the touchscreen and having to re-jailbreak.

The "Albums" tab in Photos is great for sorting through the images and videos on your iPhone since you can narrow things down by your recent pics and recordings, apps used, media types, people, places, and so on. If you never look at all of those folders, however, it could feel like an overwhelming cluttered mess. Plus, there may be some collections you don't want others to see.

The iPhone's home screen gets its signature aesthetic from a grid of icons that seamlessly blend in to almost any background. It's a somewhat minimalistic look, but that's interrupted by cluttery text labels for apps and folders. Fortunately, there's a way to remove these labels, but you'll have to be jailbroken to pull it off.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

Tapping on your iPhone's display to pick up an incoming call can be annoying when your hands are wet or dirty. It might even fail to register and cause you to miss your call. If you have a jailbroken iPhone, however, you can get rid of this problem entirely, thanks to a free tweak that lets you instantly pick up calls without having to interact with your phone's screen.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

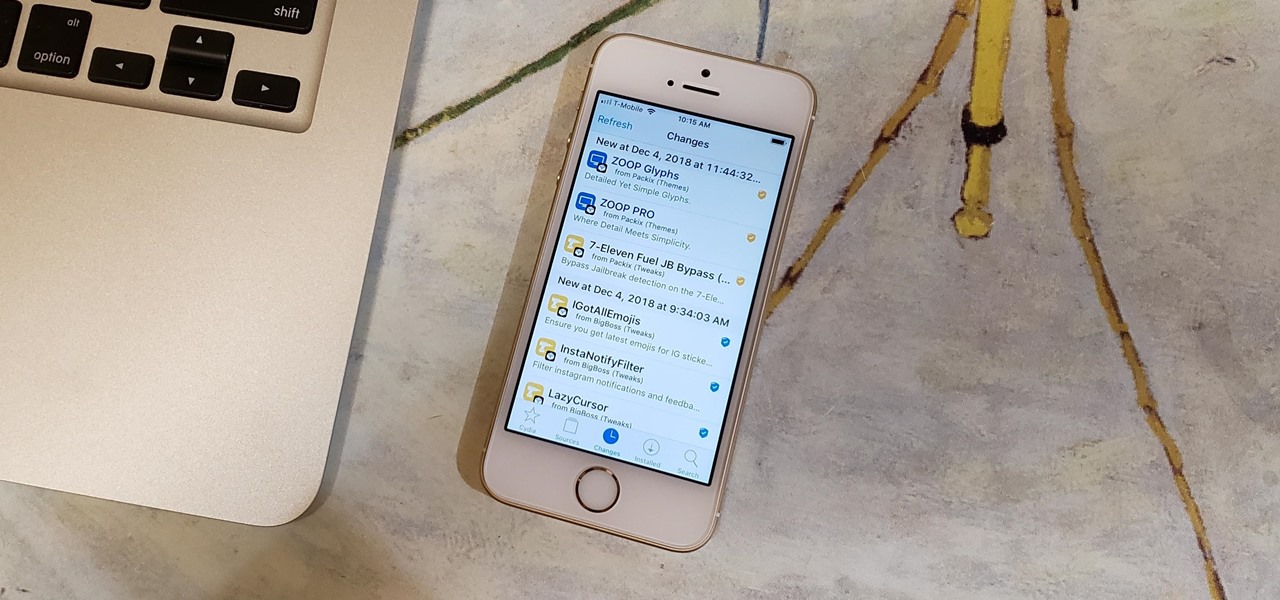
Apple has done a fantastic job of instantly patching iOS exploits through constant firmware updates to keep hackers at bay. Because of this, jailbreaking has largely been pushed to the fringes, resulting in a myriad of tweaks being abandoned by developers which, in turn, have been rendered incompatible with later jailbroken versions of iOS.

Using the ARKit 2.0 announcement as its springboard, software maker Adobe is looking leap up to the level of Unity Technologies and Epic Games, the companies making the go-to tools for creating augmented reality experiences.

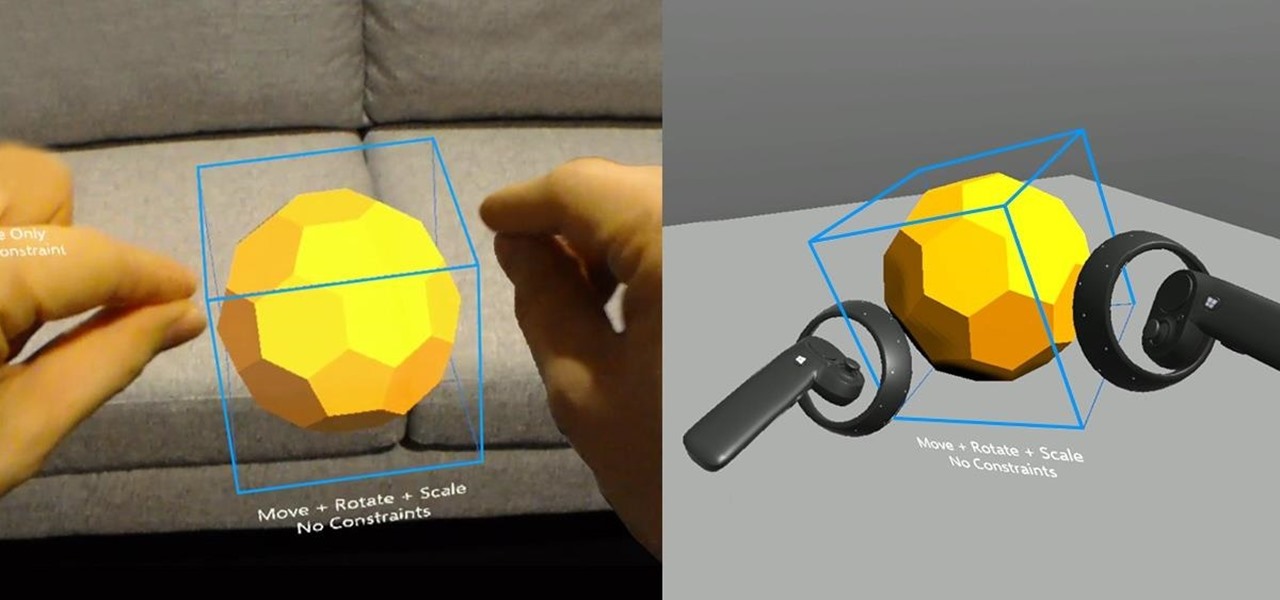
It is finally happening. After not having a major update since August of 2016, HoloLens owners everywhere will soon get a number of new features added to their devices. At least if they are members of the Windows Insider program.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.