This tutorial describes how to make a Hershey Kiss holder. This is a quick and easy project that you can make to use as little gifts in your kids' lunches, for co-workers, party favors, place-holders at holiday meals and more.

This video is a production of midget makeup. The person in the video shows us how to get wavy hair using a clampless curling iron. The first step she says is to brush your hair to get rid of any knots. Then she explains that the next step is to wet your hair a little and then apply mousse, she uses a 'got2b glued' which is a stiff mousse. She then asks you to again brush your hair nicely to get rid of any knots. She then puts on a black glove and takes a small cluster of hair. She then puts t...

Vah-Chef Sanjay Thumma shows how to cook fish fry (small fish stuffed) the Indian way. Use small kind of fish when cooking this dish such as maral fish which is a freshwater fish also called Snakehead. Marinate the fish by adding chili powder, salt, a little bit of ginger garlic base, oil and lime juice. Mix all the said ingredients and apply on the fish. After marinating the fish, keep it aside for at least half an hour. Meanwhile, make Masala preparation with rich hot oil by adding chopped ...

How many stitches does your crochet art have? How can you tell? Why would you even want to know how many stitches are in your crocheted sweater or crocheted hat? Knowing how to count your stitches is a fundamental step in learning to crochet – assuming you want your finished product to be the right size and shape.

First of all you need to have a piece of silver wire which is about three inches long and twenty-two to twenty-four gauge. Now take pliers and bend the wire into a right angle. Now take round nose pliers and wrap the wire around the tip. At the half way reposition the wire and then complete the loop. Now look at the loop which should be nicely stemmed in the middle. No insert the bead into the wire and grab the bead with thin nose pliers. Bend the wire at the right angle. Now take round nose ...

Beryl Stokes shows how to make ‘Smothered Potatoes’ in this video. She begins by peeling the skin of 8 medium white potatoes. Next, she cuts a potato in half and thinly slices it. The same is done for the remaining potatoes. The potato slices are soaked in water to prevent them from turning red. Next, 3 tablespoons of softened butter is taken in a pan. Now 3 tablespoons of flour is added to the melted butter, a little at a time and the mixture is whisked well. Next, 2 cups of milk is added gr...

Learn how to bake salmon in the oven with mayonnaise and onions in simple steps. You will need: a large onion, salmon, mayonnaise1. First peel out the outer layer of the onion, then cut it out and separate each of its layers. 2. Now slice the separated layers of the onion nicely and keep it aside. 3. Now take a suitable tray, place a piece of aluminum foil over it and spray it with butter. 4. Place the cleanly rinsed salmon on the tray and season it. 5. Add some oil to a pan, then add the sli...

Patti the Garden Girl uses her own free range chickens and home grown vegetables to make her Classic Traditional Baked Stuffed chicken

This video is a demonstration of how to cook a perfect steak. She explains how to sear a steak in a cast iron skillet. She turns the burner on pretty high. She explains that a non-stick pan doesn't work well for this recipe, because a cast iron skillet is better for high heat. She uses a rib eye steak and takes it out of the fridge 20 minutes before cooking so it won't be cold when it goes into the pan. She sprinkles the steak with salt, and freshly ground pepper. She puts unsalted butter int...

Building a frame for your paintings can save you money and provide one more creation of which to be proud. Normally recommended for abstract paintings, basic float frames offer a professional feel to your art. This video demonstrates how to build a very simple float frame, which compliments a modern, contemporary, abstract painting rather nicely.

Maria teaches the secrets of making French onion soup. An excellent summary is given below. First peel some onions and slice them nicely. Now heat about 10 table spoons of butter in a soup broth and add the sliced onions to it. Cook them on very low heat by stirring occasionally until they turn golden brown(1 hour approximately). Now add some white wine, turn the heat up high and add a bay leaf and handful of flat leaf parsley to it. Cook it till the wine evaporates, add 3 cups of beef stock ...

Want to solve the Rubik's Cube? Well, watch this how to video to know all about solving the troublesome Rubik's Cube. This three-part tutorial will go through seven steps to mastering the Cube. You'll need to lubricate the Cube first, with silicon spray, so it's lubed up nicely, for maximum speed. Then, start the steps.

Prepare this wonderful easy vegan meal for six. It only requires a 10 minute prep time and it cooks in 35-40 minutes.

Well I've converted one of these rc bikes into a snarling (ha ha) nitro powered machine. I'm now going to convert my other stock model into a brushless monster. This particular bike had a rather bumpy crossing from the USA when I bought it from ebay. It got damaged in it's box and was returned to the sender. He, very nicely, found a new set of front forks, fitted them and posted it back to me, for no extra charge! Top Man! It's a bit sluggish, stock, so I think sticking a MAMBA MAX 7700kv mot...

We've all been there. You wake up early, hungry for breakfast, but not just any breakfast will do. You want bacon and eggs. So, you blindly stumble into your kitchen, underwear-clad, and begin fumbling about with pots and pans. After a few minutes, you fill your pan with delicious and smokey rashers and turn the heat on. Everything seems okay... until the bacon actually starts to cook. With a splat, burning hot grease flies out of the pan and bombards your skin, causing intense pain and great...
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

Tater tots have a bad rap as a soggy cafeteria staple, but bake them at home and they crisp up nicely in the oven. Drain any unwanted oil from them on paper towels and they become perfectly crunchy on the outside and fluffy on the inside.

In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.

Chef Francois Payard shows some innovative cake decorating tips in this video. He says that all you need to make a beautiful cake topping is just a little chocolate, some practice and a lot of imagination. A cold slab of marble,approximately an inch thick and which is kept in the fridge for 3-4 hours, is required for shaping the decorations. Chocolate should be melted and it should be hot, not boiling. A large spoonful of chocolate should be poured on the marble and spread nicely and evenly. ...

You don't need a fancy panini press to make a good panini! Check out this video for tips on how to make yummy grilled sandwiches using items you already have in your kitchen. Save time and money with this method!

Take a pumpkin that is round and not oblong, to make the arrangement look its best. Cut the pumpkin strait across at the top, below the stem but far enough down so you have a wide opening. Clean all the seeds out and guts in pumpkin so that the pumpkin will not decompose. Cut your floral foam piece to fit snugly inside the pumpkin so it won't move. Take it out, and soak it for a few minutes in water so it will absorb lots of water. Choose fresh flowers that would look nicely in pumpkin arrang...

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

In just a few days, all the Galaxy S9 and S9+ leaks will come to an end, as Samsung will officially unveil its latest top-tier smartphone. But before that happens, we're all getting another leaked image of the handset thanks to a bit of snooping and the magic of augmented reality.

While it might be a little past its prime now, the running gag about Nokia phones never breaking was one of the internet's favorite jokes. "If you buy one," they would say, "you'll never need another phone again." I think if those users could see into the future, they'd change their tune, as the Nokia 6 is now available to preorder — and I'm guessing it would give any of Nokia's old bricks a run for their money.

Update 6/20/17: Olixar, a smartphone case manufacturer, has released images of an iPhone 8 case design. While at first glance this might seem to confirm the iPhone 8's final design, 9to5 Mac reports that Olixar admits they produced these renders based on "information and schematics they've acquired through their factories and contacts in the far east."

Snapchat accidentally—and then intentionally—announced their digital eyeglasses, known as Spectacles, over the weekend. While we'd hoped their augmented reality-heavy platform would result in related hardware, Spectacles unfortunately seek to "reinvent" little more than a video camera.

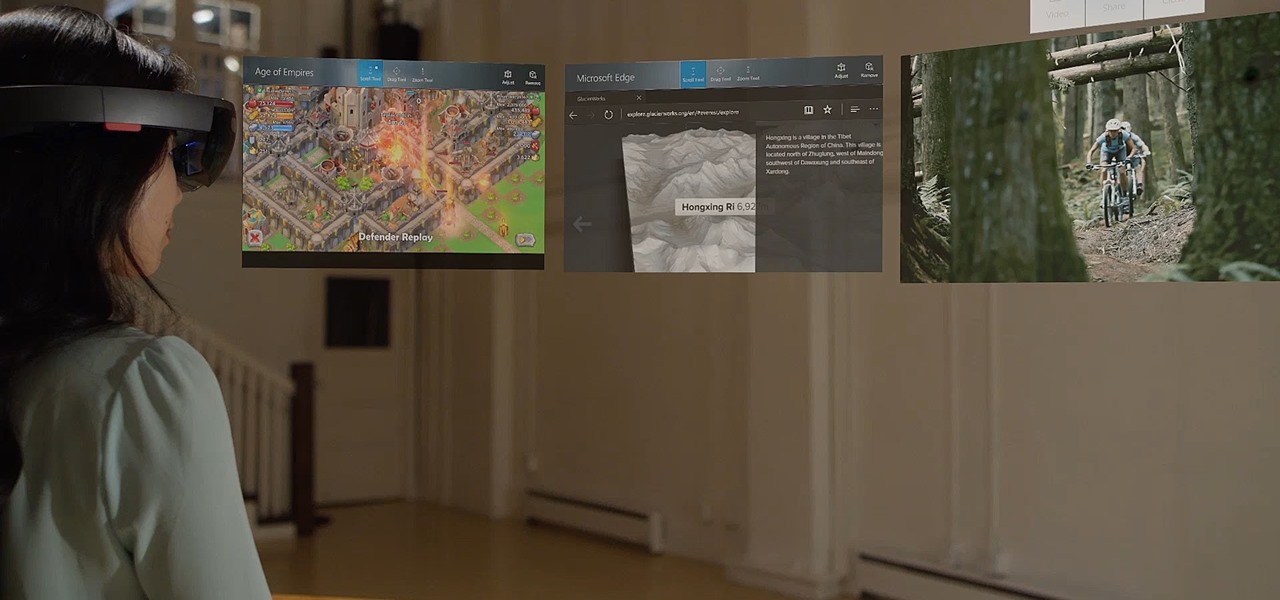
Microsoft released a robust version of the HoloLens when shipping the developer kits, but there's still lots of room left to grow. Today, they've released the first update to Windows Holographic, the operating system of the HoloLens, with a whole bunch of cool new features like voice commands and app multitasking.

More proof is emerging that the iPhone 7 won't include a 3.5 mm headphone jack, and damn—it is not pretty. These third-party Lightning-to-3.5 mm dongles were spotted on Chinese site Tama, and they give us a glimpse into a horrifying future in which we have to attach one of these clunky monstrosities to an iPhone just to connect a set of standard headphones.

I'm a PlayStation 4 owner, but also enjoy gaming on my Mac. Though it may not be as synonymous with computer gaming as a Windows system, it's still a great experience. But what makes it even better is ditching the keyboard and mouse for my PS4's DualShock controller.

Baking thinly sliced salami in the oven changes it to an awesome and savory crispy snack. They're dippable, crowd-pleasing, and healthier than your average slice of salami —the amount of oil that drains from each slice is a little scary!

Ordering delivery or takeout is an event. Most of the effort is put into actually choosing a joint to order from and figuring out what you want, so when you finally get the food, you don't want to have to worry about anything else—including dishes.

Pringles are just as well known for their cylindrical packaging as for their suspiciously addictive fried crisps. Yes, that's crisps—not chips.

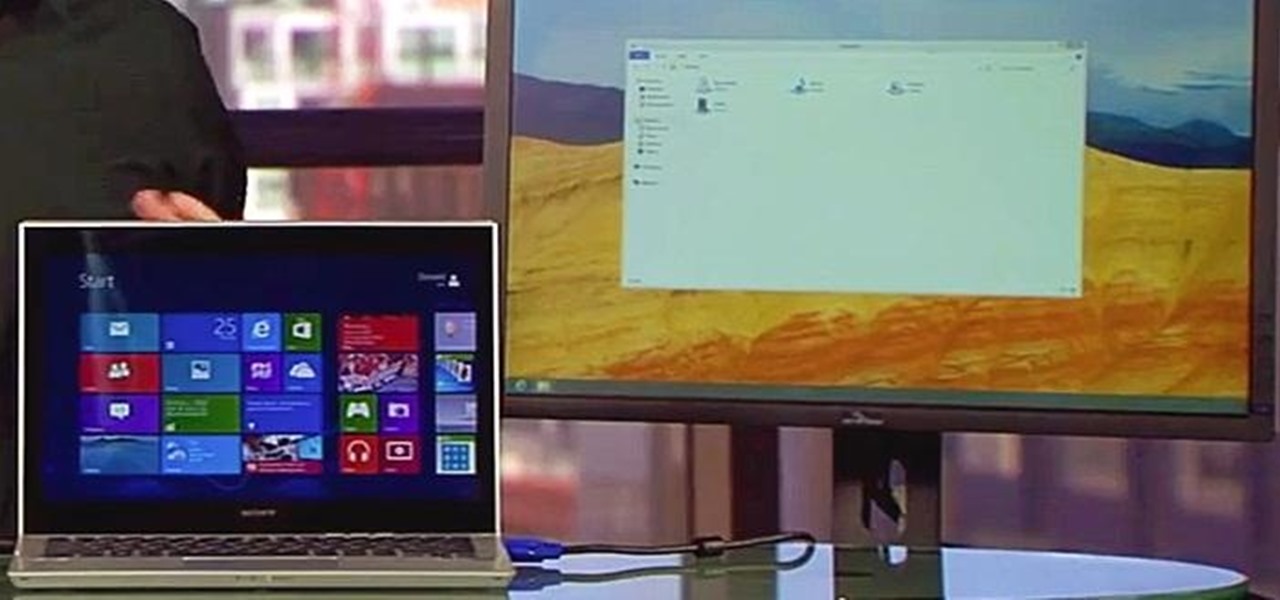
The new Windows 8 operating system pushes the Metro interface hard, but not all of your apps will play nicely in Metro, which means you'll need to resort to the traditional desktop environment for some of your favorite programs. As a result, it has left many users picking between the two—Metro or traditional? Fortunately, there's a way to run them both simultaneously with the use of second monitor. In the video below, Donald Bell of CNET explains how you can run both interfaces simultaneously...

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

With all those cables coming from your computer, printer and fax machine there is hardly any room to do your work. This how to video demonstrates how to install a cable tidy device to keep all those cords nicely organized.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?