
News: A Protein Found in Ticks Can Help Kill MRSA Infections
As researchers from Yale searched our environment for compounds to aid in the battle against drug-resistant bacteria, they got an unlikely assist from ticks.


As researchers from Yale searched our environment for compounds to aid in the battle against drug-resistant bacteria, they got an unlikely assist from ticks.

When just floating peacefully in the water with their brood mates, the Culex mosquito larvae in the image above does not look very frightening. But in their adult form, they are the prime vector for spreading West Nile virus — a sometimes mild, sometimes fatal disease.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

Warning: If you are eating and for some reason still decided to click on this article, turn around now. Maui, Hawaii health officials have reported finding at least six cases of angiostrongyliasis, a parasitic lungworm that infects humans. Colloquially, it's known as rat lungworm disease. And if you think that name is awful, just wait until you hear what it does to the human body.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

Exposed to hormones, pharmaceuticals, and other chemicals, the beautiful wild fish in Canada's Grand River have taken on some pretty odd characteristics—they're turning into females. A long-term study suggests using bacteria to manage polluted water could turn the tide for feminized fish.

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

The origins of vodka are shrouded in mystery, with both Russia and Poland laying claim to its invention. Some say Genovese merchants brought vodka (then known as aqua vitae, or the water of life) in the late fourteenth century to Russia. For many years, vodka wasn't just an alcoholic beverage: it was also consumed as medicine.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

Whether you want to give a gift that your loved one has wanted all year or one that they never even knew existed, there's something awesome for everyone in these gifts. Just as exciting as their innovative features is their price.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.
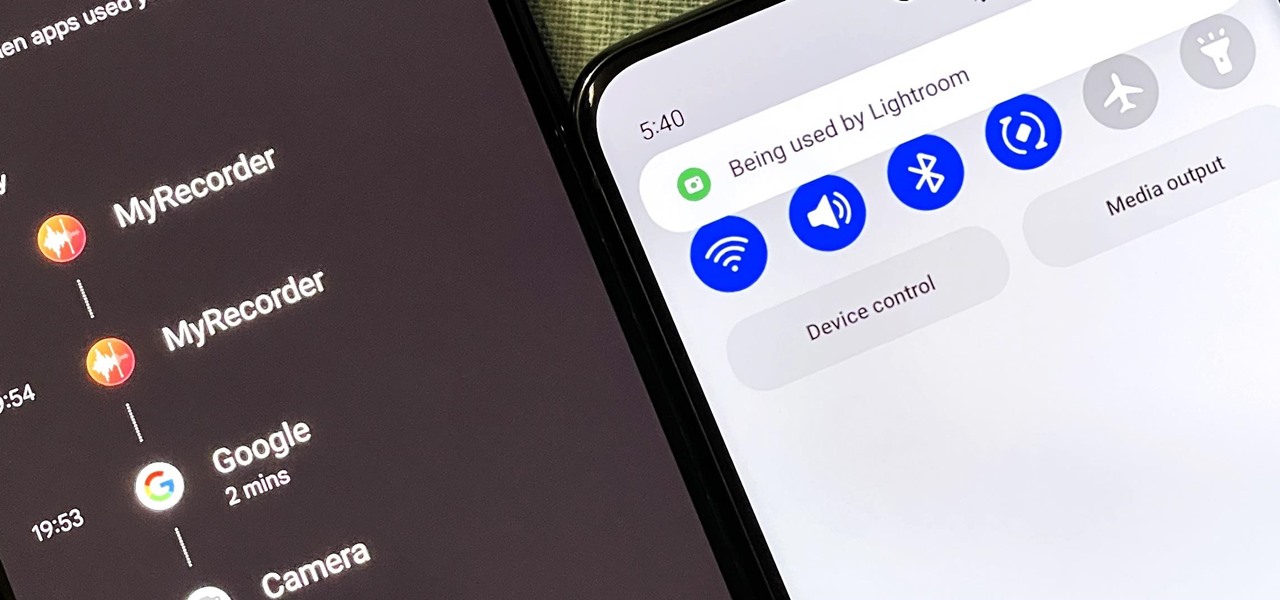
Is your smartphone eavesdropping on you? It's a question that will never go away because it's easy to envision hackers or malicious apps taking over your device to spy on conversations, snap photos, or even record video. But fewer people will be asking it, thanks to Android 12, which has a new privacy feature that visually warns you of possible invasive surveillance.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding your stuff.

Researchers at Kentucky State University are introducing Kentucky "tuna." Still in development stages, the tasty treat offers one useful benefit of an otherwise invasive fish, the Asian carp.

The In-Line vasectomy is a minimally invasive, procedure. In an In-Line vasectomy the vas deferens is cauterized but not removed. The ILV instruments were standardized by measurement and design to perform specific functions within a 4mm space. This video is a step by step explanation on how to perform this rapid and reliable procedure.

Most bamboo in the United States is running bamboo, because nearly all cold hardy bamboo is the running or invasive type. The tropical bamboos are mostly "clumpers" and stay in a nice, tight clump. Running bamboos spread far and wide and can be very invasive. I grow many kinds of running bamboos and over the past 20 years I've had to learn how to control it's spread.

Are your sinus problems getting in the way of your life? Dr. Oz of Real Age Videos provides an informative, animated video that unravels the mysteries of infected sinuses. He explains the physiology of the sinuses, and details the possible causes of sinusitis and its common symptoms, including colds and allergies. This video offers a few suggestions about current methods of medical treatments to alleviate this troublesome malady. It explains how the Balloon Sinuplasty procedure can provide ef...

Boats look great in the water, but take them out and you’ll often find build-ups of algae and other invasive aquatic species. A pressure washer can help keep your boat looking its best – in and out of the water. Watch this how-to video to learn how to clean your boat with a pressure washer. Clean a boat with a pressure washer.

This video is here to demonstrate that the TSA's insistence that the nude body scanner program is effective and necessary is nothing but a fraud, just like their claims that the program is safe and non-invasive .

This is personally one of my favorite mods, it adds a whole new aspect to the game with realistic and diverse biomes. I wish some of these biomes would be introduced in the official minecraft version as it out does some of the current ones in creativity and uniqueness.

When I tried to send a free gift back to my friend, I got this popup I clicked skip the first time, and it came up twice more. So I logged in, it imported my contacts...

If you're into entomology, then you probably recognize the name E.L. Trouvelot. After all, he was the person responsible for the outbreak of invasive gypsy moths in North America, which are now one of the most destructive foliage-eating pests in the United States.