Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

The company augmented reality that Rony Abovitz was trying to build at Magic Leap apparently wasn't working out the way he hoped it would. That company, built on dreams, music, and future-looking entertainment, rather than truly new technology, came with a $2,300 price tag for a device using dynamics most mainstream consumers have never even tried.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

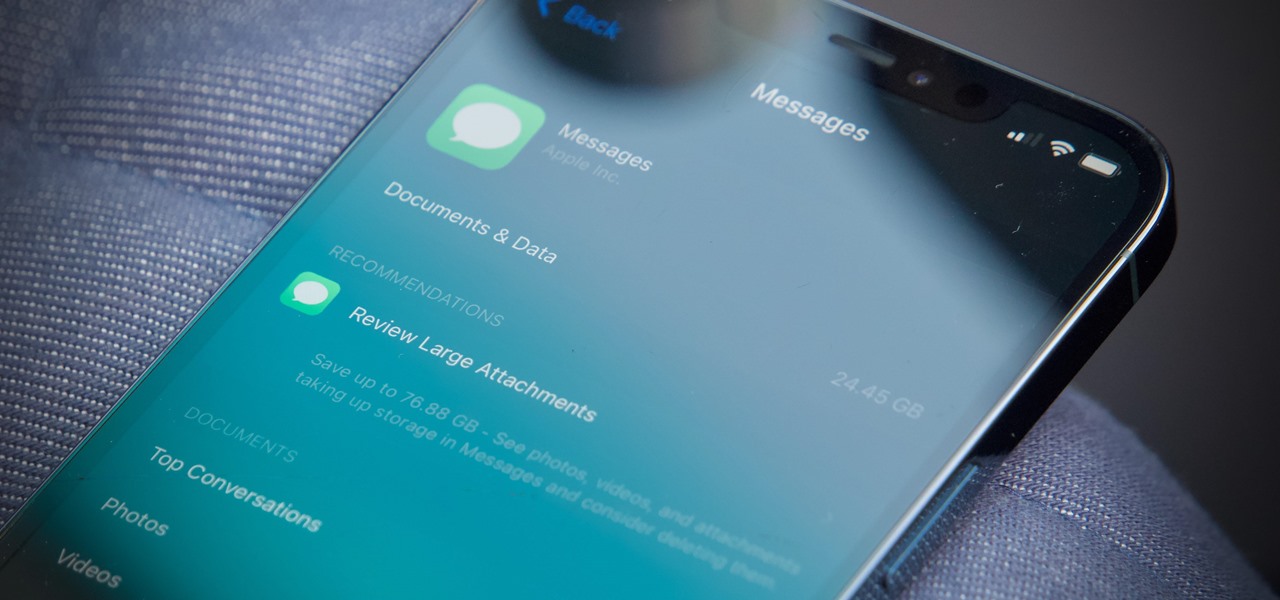
When iOS starts barking at you that you've run out of iCloud or iPhone storage, a quick trip to your settings to see what the culprit is may show that Messages is one of the worst offenders. But if deleting message after message doesn't free up your storage much, it's likely because "Messages" doesn't really mean messages.

In a tradition dating back to the Nexus days, Google has always used fish-themed codenames when communicating internally about their phones. Their laptops and tablets are usually named after video game characters. These names often give us the first evidence of an upcoming device when they're used in software commits in Android's open source code.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

From time to time, you may need to locate the version and build number for a particular app on your iPhone or iPad, but it's not at all obvious where you can find the information. Well, there's more than one place to look on iOS 15 and iPadOS 15, but none are perfect solutions. Knowing each method will ensure you can always find any app's real version number.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

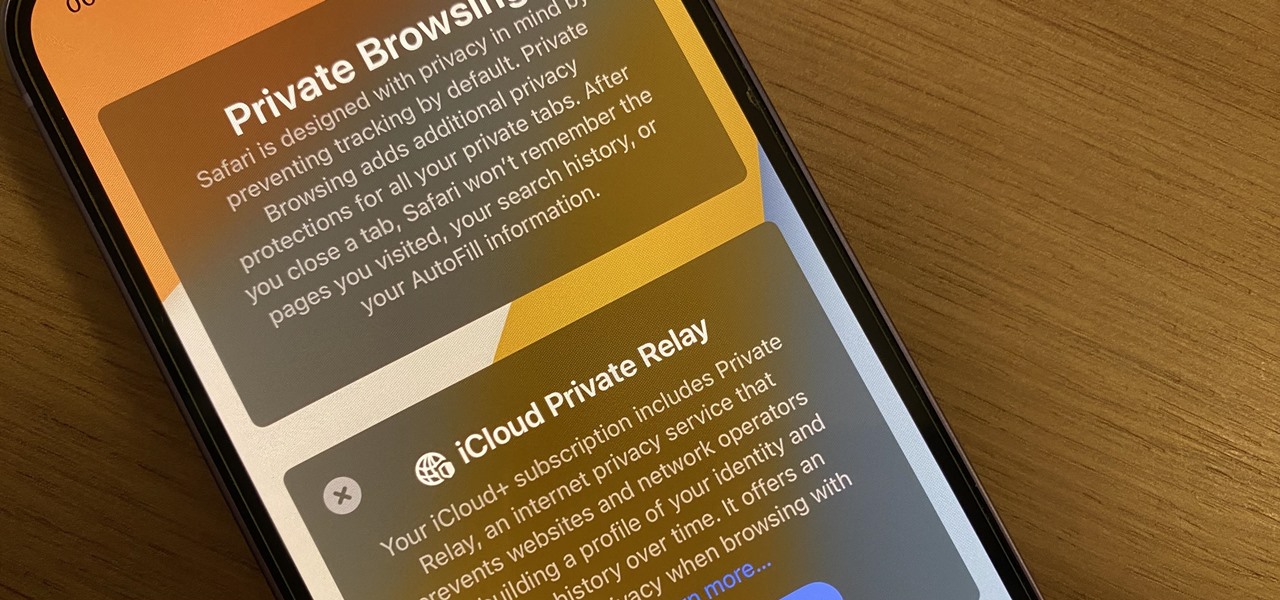
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Dr. Aris Latham suggests setting standard plans for breaking a fast for most of people that he interacts with because the animal body has been programmed to eat in a certain way. This is necessary to train your body well so as to survive and be healthy. Divide your day into 3 equal parts of 8 hours. Take the sleep part of the day where you deal with the waste in your body and create energy within the body. The next period when you get up is basically when you break your fast when your were sl...

Always wanted to try skinny dipping but not sure quite how to get the ball rolling? There's not much to it but with a little bit of forward thinking you can make sure to get your friends on board while avoiding cops and an unwanted audience.

Ingredients ½ teaspoon active dry yeast

This device is a refined version of the vernier caliper. What seperates this from the other is that is has a circular dial that is measured thanks to a small gear rack. The device can still be used to measure things externally and internally as well as sometimes depth. The side of the caliper can be locked in order to keep it in place and is quick to use. So find out how to read this dial caliper following some easy steps. Enjoy! Read a dial caliper.

External shoulder rotation exercises are done to work the rotator cuff. The rotator cuff consists of four muscles. They include the supraspinatus, infraspinatus, subscapularis, and teres minor. Each muscle works to rotate the arm externally (laterally) and internally (medially). The following are instructions for the cable external rotation shoulder exercise:

We were dumbfounded at first, too. But this jumping bean is momentum based, not larva powered. The erratic movement of these DIY foil toys is actually simple physics. Hint: there is a marble inside the aluminum foil. When the marble rolls internally to the foil's end, the foil-bean flips with the momentum. All this commotion mixed with some well coached hands makes for a magic jumping effect.

Electronic Arts is the biggest game publisher in the world, and have been for years. And yet, their only successful internally developed games nowadays are the EA Sports mega-franchises like Madden. Most of their success has stemmed from their ability to buy other companies on their way up, squeeze the creativity out of them, and then sell them to someone else or just let them go. This week they made their largest acquisition ever when they purchased PopCap Games for $750 million upfront—as m...

There is a difference between what is possible, what should be done and what an owner manager may want to do. Decide how you want to handle payroll then determine if your desires and best practices are in agreement. Before I point out the decisions that need to be made, let me make two points. First, all personnel for your business do not have to be employees. Some entities can be run with all non-employee personnel or a combination of both. This is one of the reasons why doing a business pla...

Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in space!

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

Thanks to the advent of smartphones and mobile apps, Scrabble has spread like wildfire across the globe, whether it be Scrabble or one of its many popular word game spinoffs, such as Words with Friends, WordWise and Kalimat.