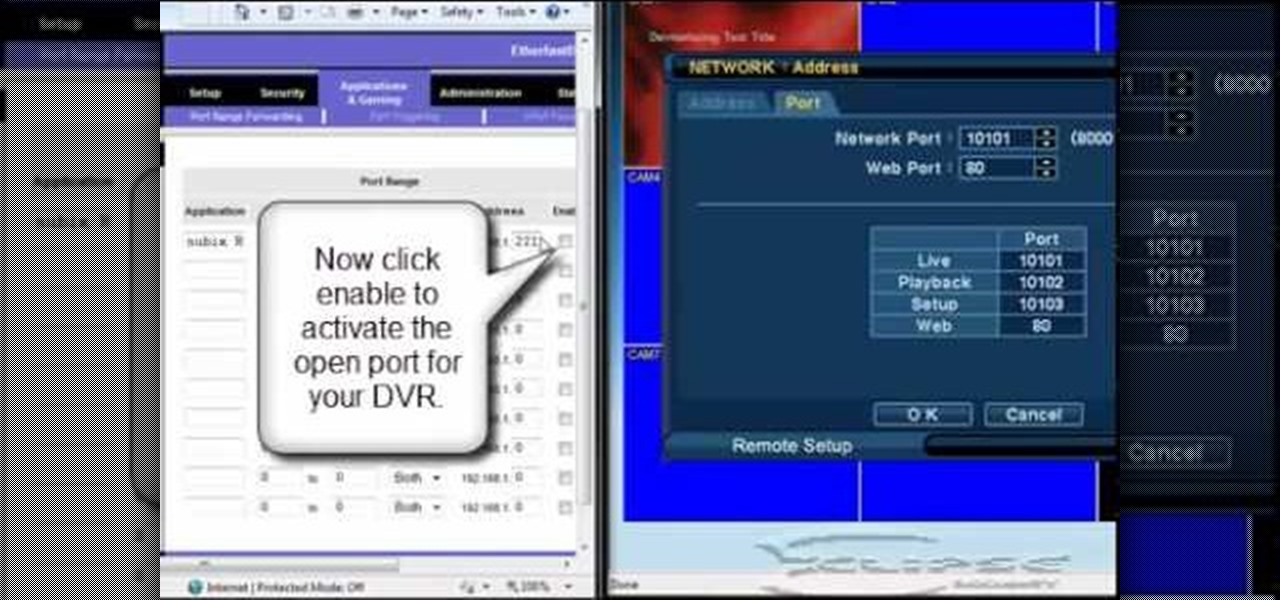
In this tutorial, we learn how to open ports on a Linksys router for your DVR. First, make sure your internet is connected and your DVR is connected to Linksys. Next, log into your Linksys router online and set up your DVR to the "DHCP" section. When you have the information from this, enter this information on your DVR so it has the correct server name. Make sure the IP and other information displayed on your Linksys page is the same as the setup on the DVR page. When finished, change your p...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.
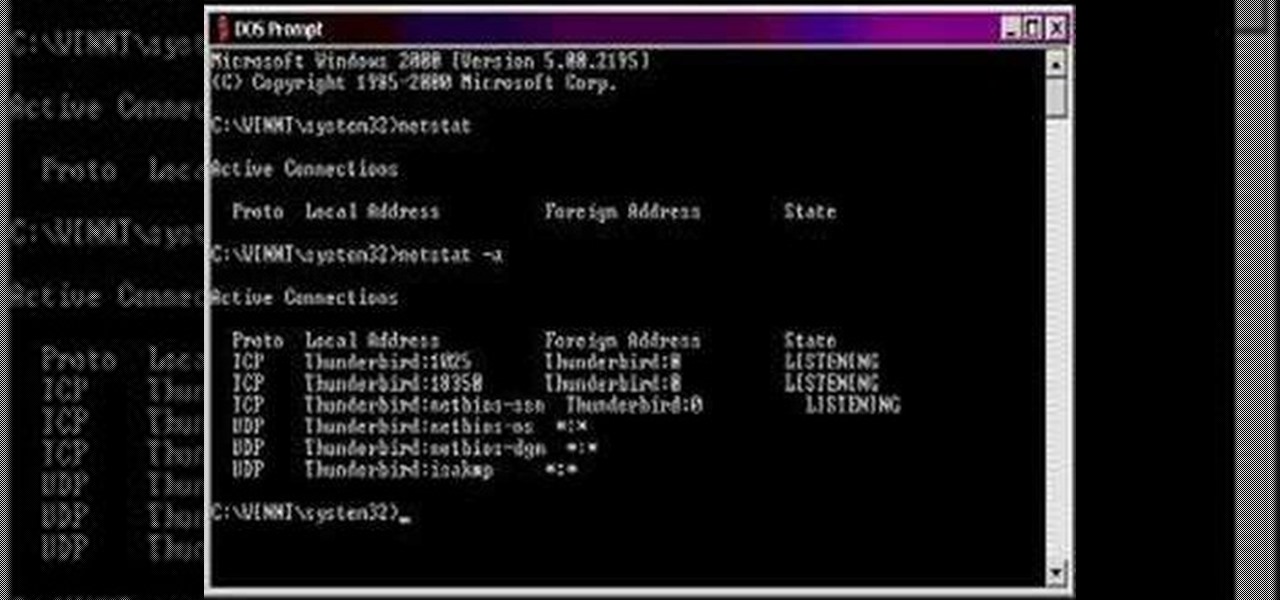
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Each Toyota 2010 4Runner has a mini plug auxiliary audio input port in the center console. When you want to play your personal playback devices, e.g. iPods or other MP3 players, on your car's sound system, simply plug it in the mini plug socket and press the aux button of the sound system. Depending on the model you drive there may also be a USB port in the glove box for selected models. Connecting your iPod to it will play the device as well as charge it when you drive. Playing sounds in you...

A tutorial on how to change the remote desktop port number in Windows.
This video explains how to make your bittorent client download faster. To increase torrent downloads increase your upload capacity to max, enable port forwarding if you have a router hub or firewall that blocks ports, and download torrents with a lot of seeds.

This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer and put in the IP address and open the port you found. Now right click after you enter the computer's IP address and the open port. Select full control or view only and there you go. The computer has been successfully hack...

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

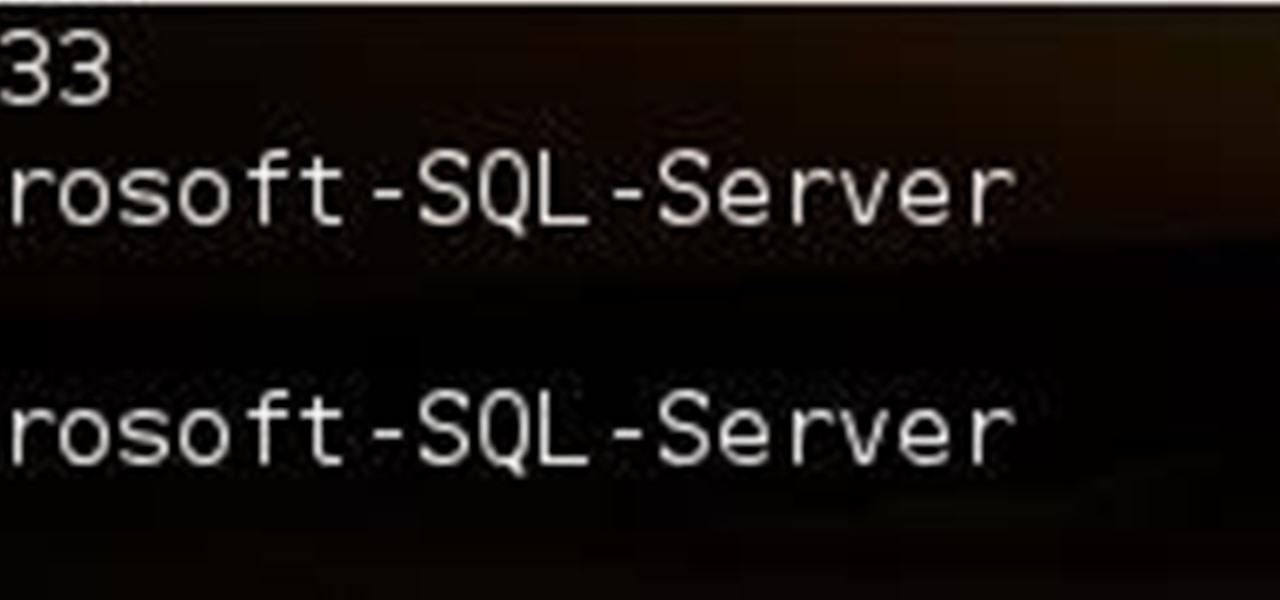
Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Celebrate America's birthday the way the Founding Fathers might have, by whipping up a batch of Plantation Punch. Howcast presents this video recipe guide to mixing the alcoholic drink: The Founding Father's Plantation Punch. Perfect for the 4th of July.

Oh Christmas tree, oh Christmas tree...how beautiful would a Christmas tree be, though, without any ornaments? If you've finally hit the tree lot and picked out the perfect grand fir, make sure it shines bright by decorating it with several of these intricate lacy snowflake decorations.

In Halo: Reach for the Xbox 360, there is so much to do! The campaign, the multiplayer, the achievements! But One tough one to get is all 19 hidden data pads. Luckily for you, the first nine can be acquired on any difficulty, and in this video you will learn the locations of all nine of the initial data pads on levels such as Winter Contingency and Pillar of Autumn!

TextNow is a great App for the iPhone that allows you to, for a $1 initial fee, send unlimited text messages to any other TextNow user without using any of the precious limited texts on your AT&T plan. The App is very easy to use, requires only a modest amount of additional money to keep using it forever, and will probably wind up saving you money in the long run by cutting down your monthly billed texts.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

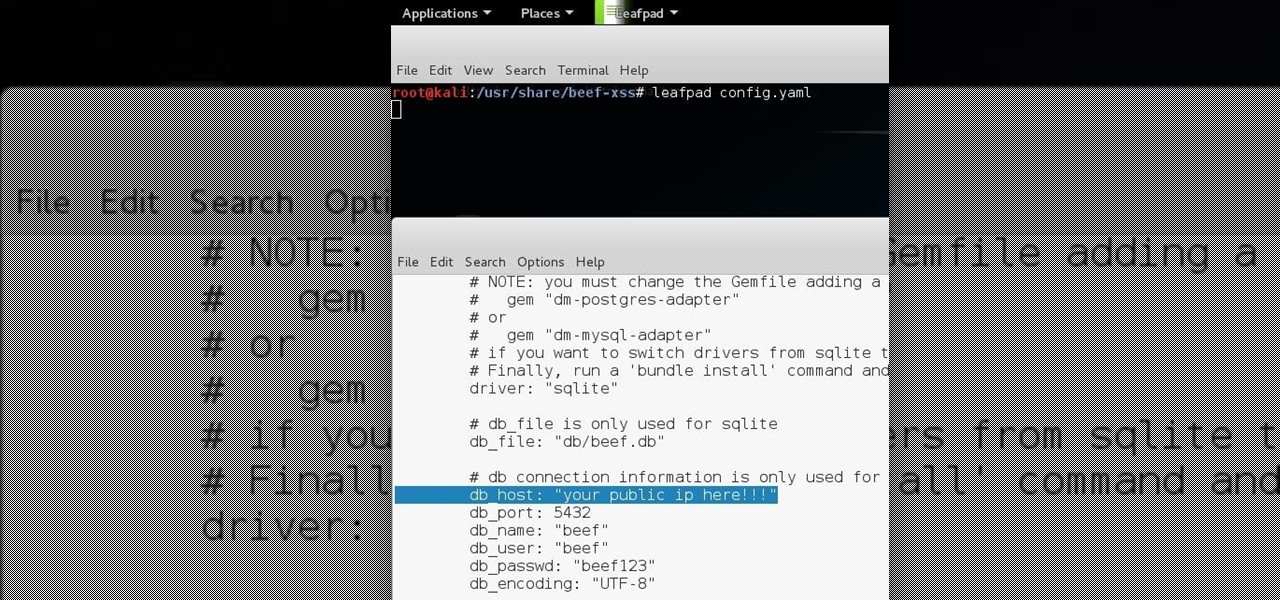
Hello all Just thought id share how ive managed to get beef working over the internet.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

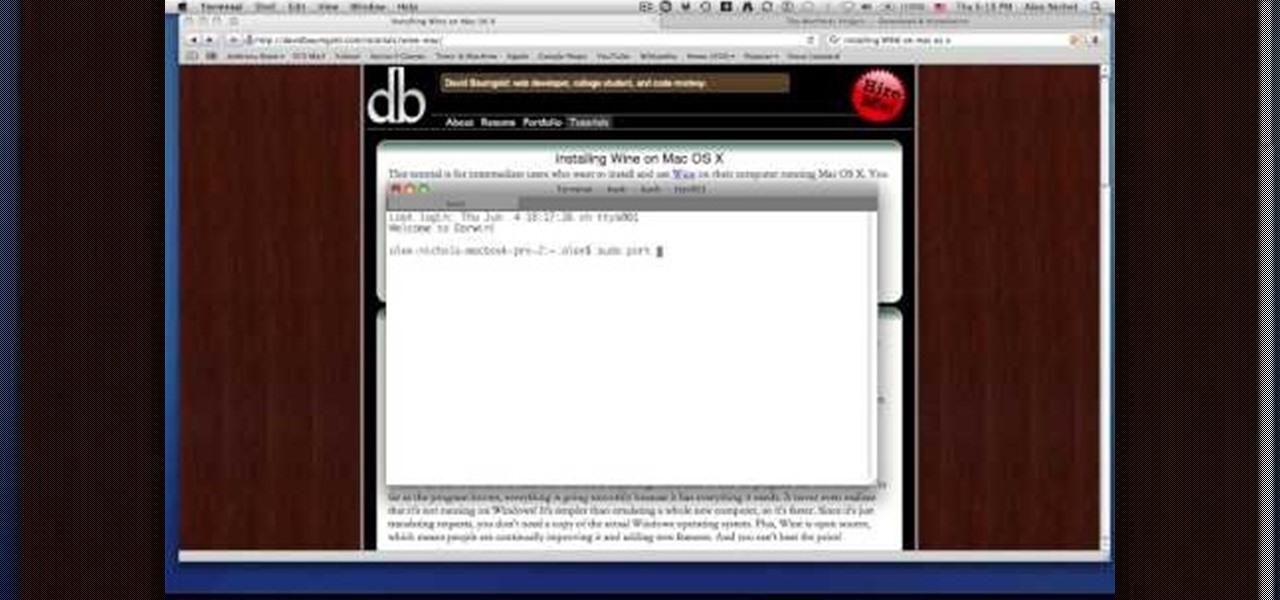
Macheads demonstrates how to install wine on mac. What is wine? Wine allows you to run and install windows program on Intel based machine. This program will work only on Intel and wont work on power PCs,unfortunately. First, we have to install macports which is something similar to installing unix programs on mac. The following are a bunch of requirements in order to install wine - an intel mac, admin account, X code installed, X11 (which comes mostly with intel macs). First of all we have to...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Create a three-dimensional logo in Cinema 4D and Photoshop with realistic lighting, reflection and shadows. The render is created in 3D inside Cinema 4D using Mograph Text and a bend deformer, textured and lit for initial reflections, and polished in Photoshop with blending modes, blurs and curves. Greyscale Gorilla demonstrates in this informative hour-long video.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

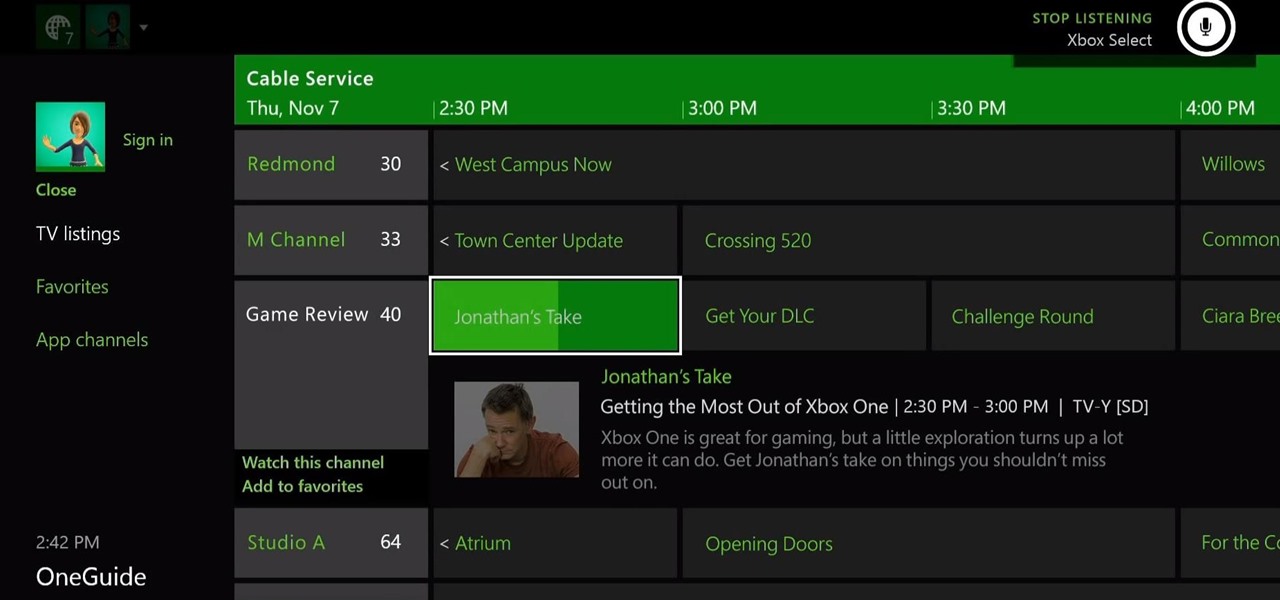
The Xbox One is the quintessential jack of all trades. It can be your browser, music player, gaming system, and cable box, but in order to benefit from all of these goodies, you're going to have to set it all up.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

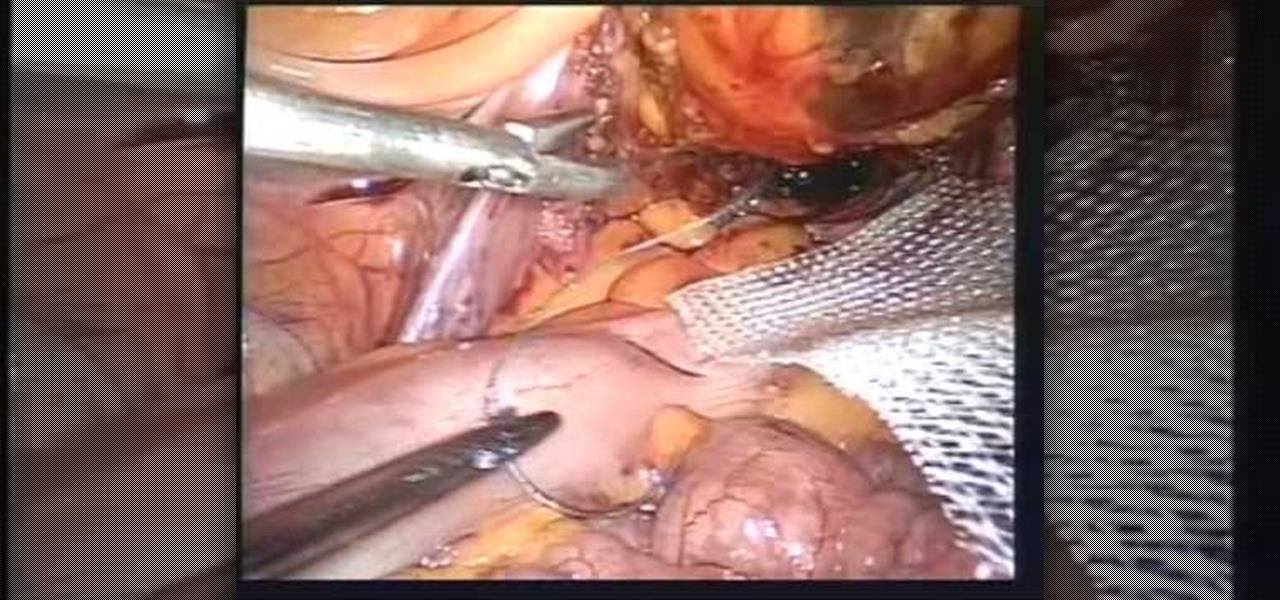
This video is about Laparoscopic Suturing Techniques.The video begins with the narrator saying that the technique is widely used in major abdominal surgeries and mastering of the techniques would give great confidence in the surgical procedures.There are various types of laproscopic needle drivers are available which can be selected according to preference.Different types of 10 millimeter laproscopic ports are available,however the valves used in the ports are important for performing extra c...

Hook up your TiVo, Xbox and other television-based electronics to a single HDMI port. All you need is a switcher, which you can buy easily for around fourteen dollars. Then hook it up, and have multiple input devices attached to your TV!

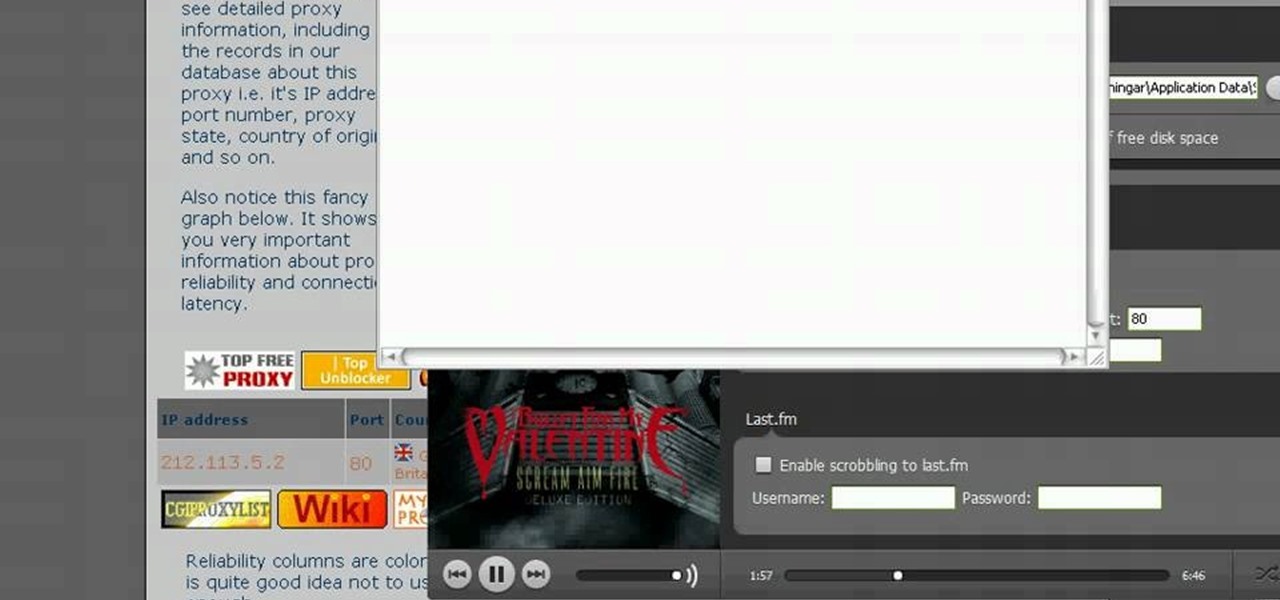
In this tutorial, we learn how to remove the ads from Spotify. First, you will need a proxy, which you can get from the website: Proxylist. Just simply click on a free proxy once you get to the site, then write down the proxy and port. Next, go to edit, then preferences. After this, change the auto-detect to https, then put the proxy next to the box that says "host". Next, type in the port next to where it says "port", then click on the "apply" button listed at the bottom of this window. Now ...

Want to set up your own multiplayer server so you can play MineCraft with your friends? From the initial download to your first logon, this tutorial shows you how you can build and set up your own server for multiplayer Minecraft!

Finding oil on your land is no easy task. Usually experts do this sort of thing, but why shell out money when you can do it yourself? We'll be the first to tell you that finding oil in your yard is not easy, though.

This how-to video demonstrates the right skills for stamping with a watercolor technique. You will need non-running inks to stamp the initial image, a specialty brush pen, and watercolor paper. This watercolor effect is pretty, and can add some different texture to your stamped images. Watch this video tutorial and learn how to make a watercolor look with stamps.

In this tutorial you will learn to wrap a logo around a photographed object in Photoshop. Learn to work with smart objects and label grid to do the job. However, some of the initial steps are not shown in this video, so you might want to listen closely to the narration about the preparation work.

Here is a supernatural how-to for all you spirit lovers. This is a step-by-step guide to create a fake ghost video with free software. The initial technique is simple, but with a few more tweaks, you can get video that can fake at least your grandmother. Use this as inspiration for one of your April Fools Day pranks!

2019 has been a great year for smartphone batteries. Several phones have topped the 5,000 mAh threshold, and Apple finally went all in on 18 W USB PD charging, which means millions of new users are finally taking advantage of fast charging. All of this gets even better when you have the right charger.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

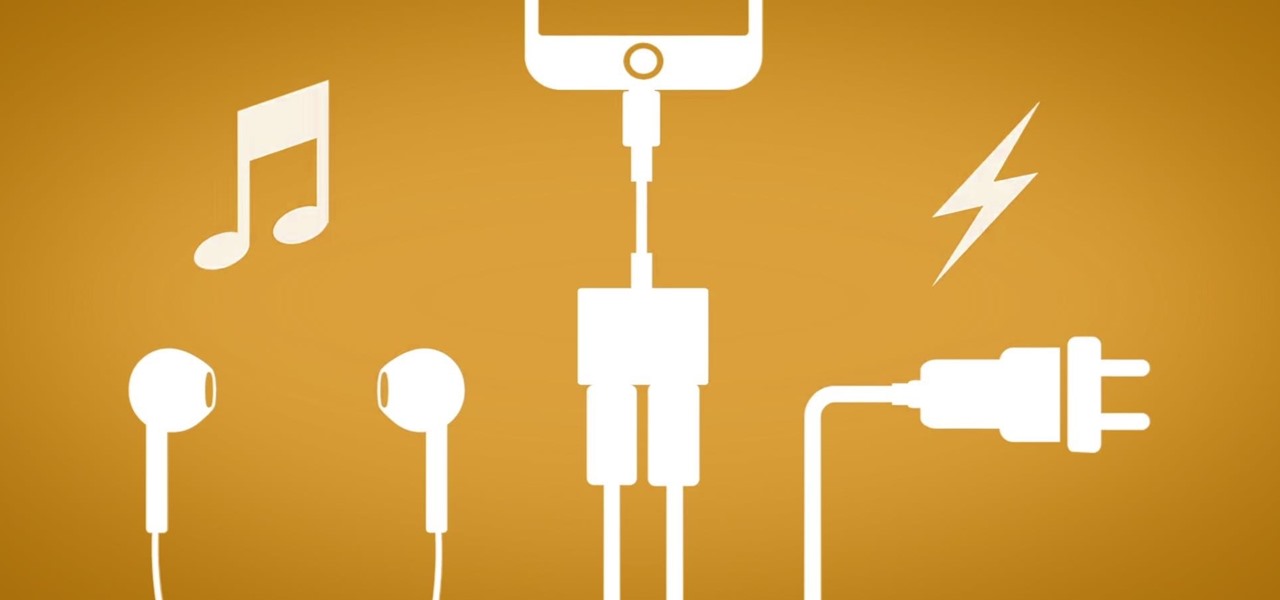
The fact that this guide even exists is a downright shame, but that's neither here nor there. The truth of the matter is the iPhone 7 and 7 Plus don't have 3.5 mm headphone jacks, and since they use the Lightning connector to output audio, it's hard to charge your phone while your headphones are plugged in.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.

A FGPA is chip that is programmable with the computer to create circuit. It is a totally different type of programmable board compared to an Arduino for example. The Arduino will follow lines of codes to generate the necessary outputs. A FPGA won't however read lines of code, but it is a circuit itself. When the chip is programmed, a series of AND-ports, OR-ports and many others ports are linked together. The FGPA will increase the speed and the possibilities of your designs! I assume that by...