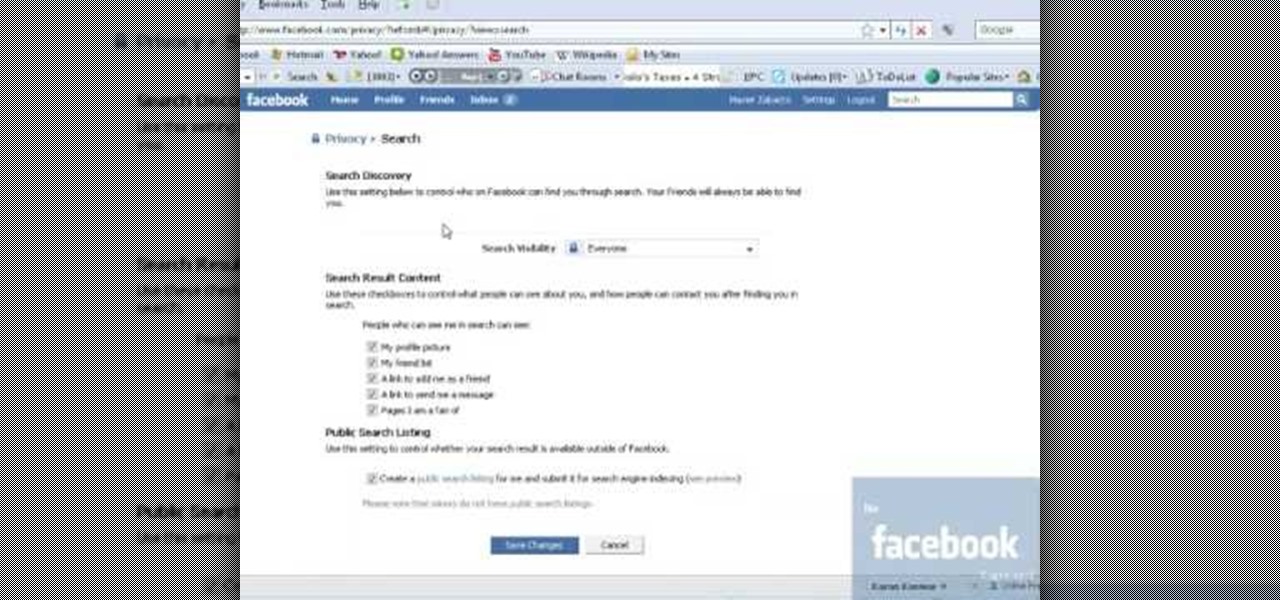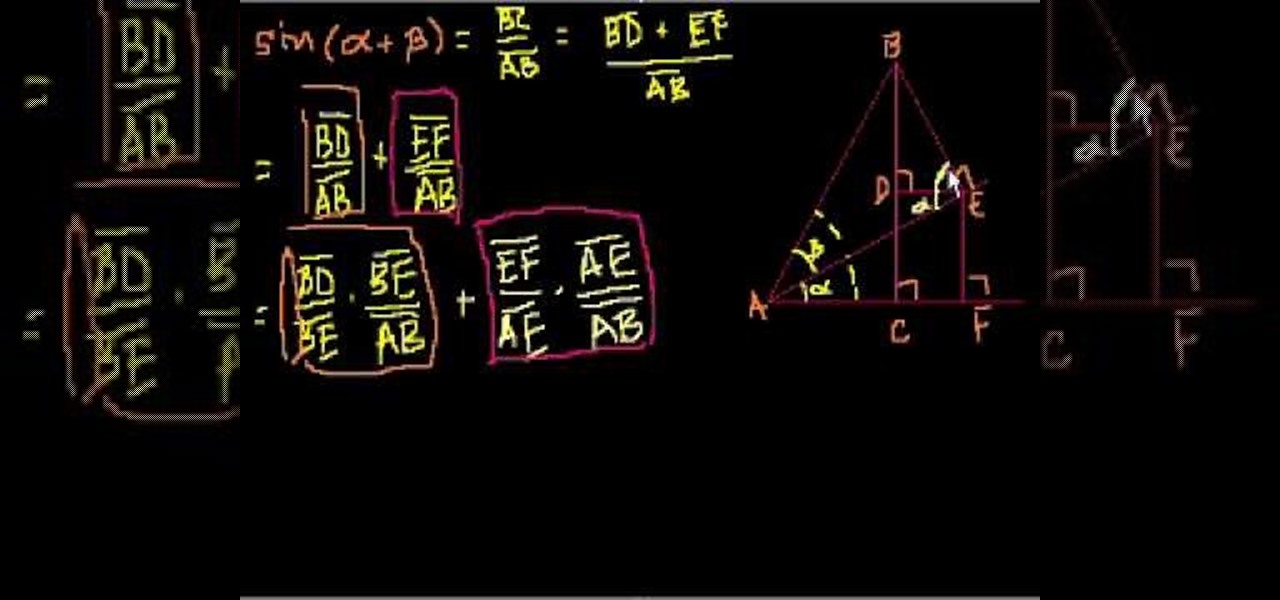
Need help proving the sin(a+b)=(cos a)(sin b)+(sin a)(cos b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of...
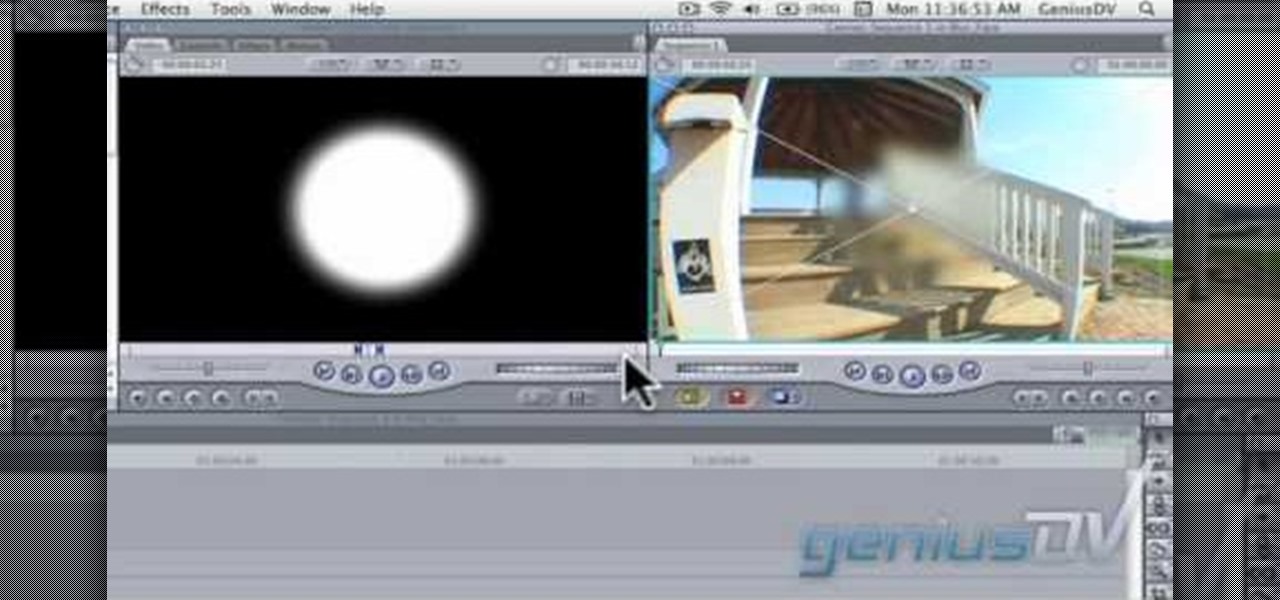
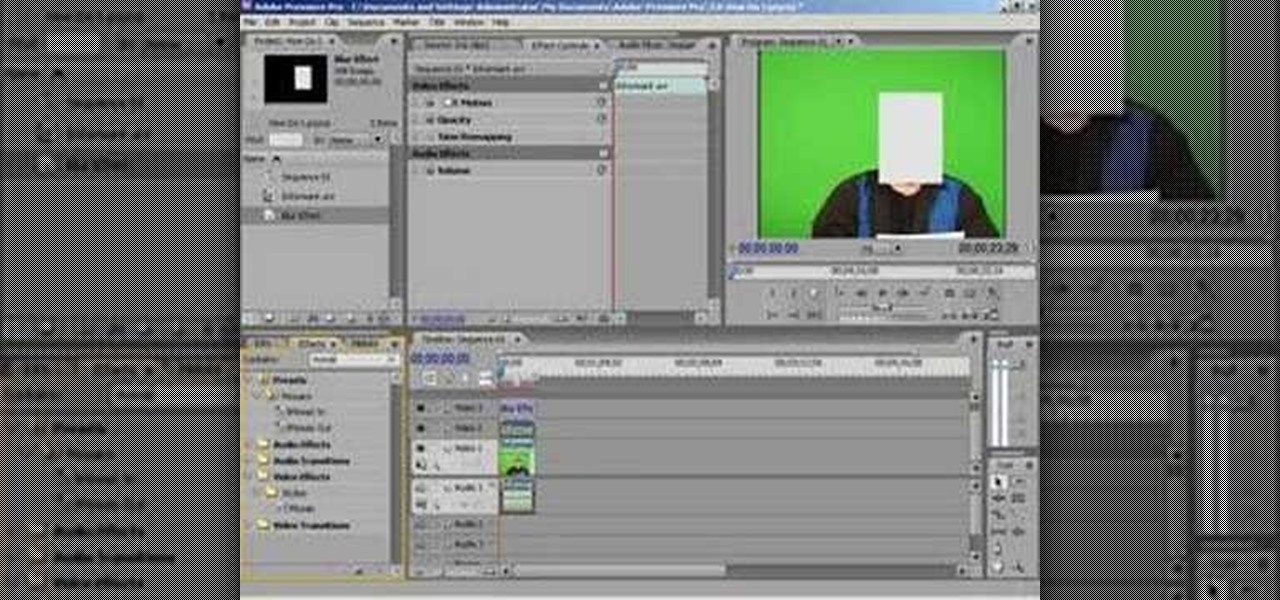
In this clip, you'll learn how to blur out a person's identity with matte tracking in Final Cut Pro or Express. Whether you're new to Apple's Final Cut Pro non-linear video editor or just want to better acquaint yourself with the popular video editing program, you're sure to benefit from this video tutorial. For more information, including detailed, step-by-step instructions, watch this tutorial.
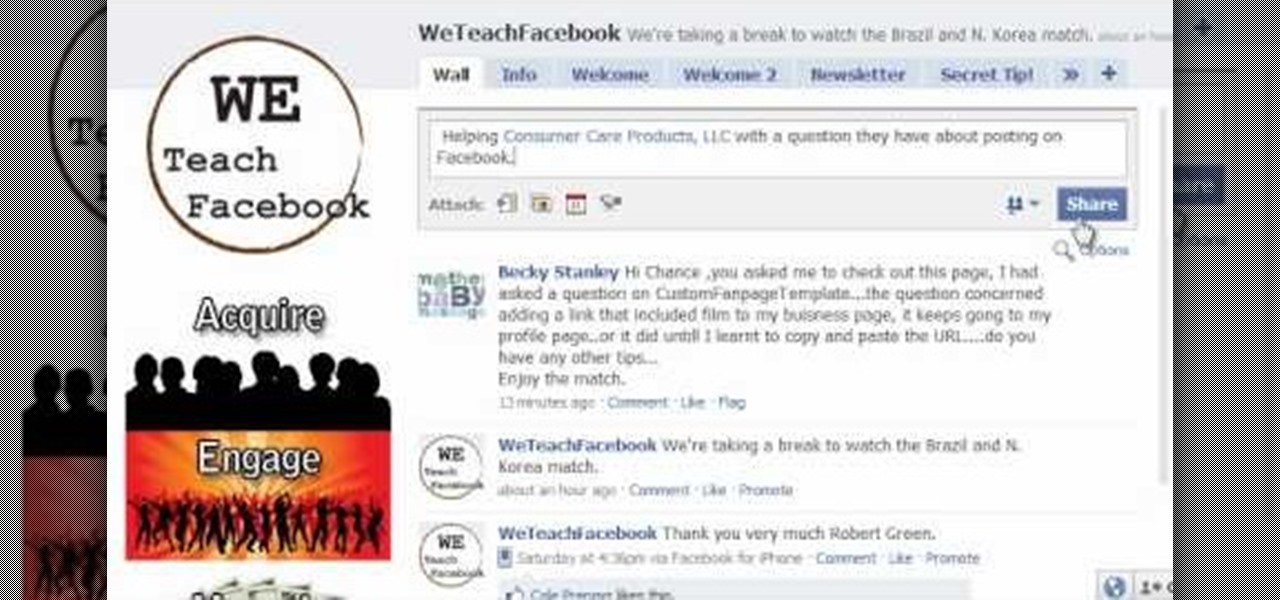
In this tutorial, learn how to use your Facebook Fan Page to comment and write on other people's walls like you would a personal account. Your fan page is linked to your personal page, and sometimes you don't want to use your real identity to write messages. Check out this clip and get the hang of a FB glitch that will allow you to "tag" your friends so you can write on their walls.

If you've ever participated in a Anonymous protest against scientology or celebrated Guy Fawkes day, you probably know that drinking through a Guy Fawkes mask is tough, especially if you're keeping your identity a secret. Watch this video to hear an Anonymous member explain how to drink water without compromising your anonymity.
Looking for an easy way to make certain that your sensitive personal information is secure? With Identity Finder, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

FAST is an expedited travel program for commercial truck drivers that travel between the US and Canada. FAST cards are available to citizens or permanent residents of Canada or the US. The FAST program is viewed as a privilege by both Canada and the US. You can be denied for the FAST program if you do not have a clean driving record and a clean record with the Canadian Border Services and The US Customs and Border Protection. Things such as being caught with undeclared items and having a crim...

Need to change your IP address? In this how-to, you'll find instructions for changing your IP address from the Windows command prompt with the ipconfig console application. For step-by-step instructions, take a look. NB: Changing your IP will not protect your identity; it's merely a simple expedient for getting around certain problems ones might encounter while using the Internet.

Today's word is "incognito". This is a noun, adjective and adverb. As an adverb it means without revealing one's identity.

Steal someone else's fingerprints, use identity thief powders, & photograph the prints. Print the 3d prints & adhere to your fingers!

Sometimes--no matter how much you may want to avoid any trouble--you just have to swallow it up and do it the smart way. Notarizing your documents helps you avoid fraud.

In this video, we learn how to bring your Cuban spouse to Canada. First, you need to have the correct documents which prove your identity and marriage status. You will also need marriage certificates from previous marriages stating that they are dissolved. After this, you will need to have them notarized, then travel to Cuba to obtain new documents for you and your future spouse. The authorities will direct you to the appropriate offices, then you will need to pay the fee for filing these pap...

In this video, we learn how to make your Facebook profile less public. First, log onto your Facebook account, then go to your privacy settings. Through there, go to search and choose who you want to allow to search for you on your site. After this, save your settings and move on to the other sections to change more privacy settings. If you do not want people that aren't your friends to see your information or to be able to search for you on Google, this is a great way to go. Making your infor...

This video from TechFusionVids presents how to install Microsoft Office 2008 on Macbook Pro.All installation process takes about 5 minutes. Insert Microsoft Office 2008 installation disk, double click on the installer icon when Office installation window opens.Click Continue two times, agree to software license agreement, type your name and name of your computer, click Continue again.Window opens saying you should close all running applications before starting further installation.Once it's d...

In this video, Dan and Jennifer will teach you how to be safe while trying to meet girls or date online. Learn tips and tricks to avoid common scams such as identity theft and fraud, as well as things to look out for and early warning signs that your potential lover may not be all she says she is. Dan and Jennifer will also show you how to watch out for one of the most common scams online: "cam girls". Don't fall for that fake girl that acts like she's totally into you but really just wants y...

This video shows the method to prove some trigonometric identities. This involves the use of algebra and knowledge of basic trigonometric identities. The video demonstrates three examples to illustrate this problem and its solution. The first problem shows a relatively simple problem involving sines and cosines. The video shows some basic algebra steps to simplify the problem and prove the identities. The second example involves a slightly complicated problem involving square of combination o...

A PDF Portfolio is a bundled collection of content compressed into one PDF file. Watch this 5 minute overview and learn how you can bundle documents, e-mail, drawings, flash presentations and even video into one sleek package that can be used for presentations or project management for your organization. Your portfolio can include introductory text and sets of data that can be sorted geographically by being linked to clickable maps. Not only can the entire portfolio be branded with your logo ...

First you want to find X using the identities given for a 45-45-90 triangle. When comparing the triangles in the video, we find that X must be 6. Next, use the identity to solve for the measurements of the sides of the triangle. In the video example, 6 is the length of the two sides and 6 times the square root of 2 is the length of the hypotenuse. The video is very short and does not explain a lot of things in detail, but that is because the examples are easy to figure out.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Recycling your garbage is noble and, in many places, mandatory. But it also can be very confusing. This guide will clear up the rules.

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Need to hide the identity of an informant in your video? Maybe doing a spot for COPS or the Discovery Channel? Well, this tutorial shows you how to create a mosaic blur effect to cover someone's face in Premiere.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.

Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Channel art can be used to brand your channel's identity and give your channel page a unique look and feel. Your channel art will be used on all platforms where viewers can see your channel (TV, mobile, tablets, etc.) Please watch the video below for clear understanding

Birds don't generally wear collars, but to give a bird an identity tag, leg bands can be used. This video demonstrates the way to put leg bands on baby pigeons. This is usually done between 5-7 days of age. When pulling the back toe through, make sure not to force it if the little claw gets caught on the inside of the band. Watch this video pet care tutorial and learn how to band the leg of a baby pigeon with an ID tag.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.