The Crayola washable supertip markers are an ideal tool for any artist, young or old, who wants to bring sharply defined, bright color to their drawings. This video demonstrates how to color simple line drawings using these basic markers.

The granddaddy of all knots... the square knot. Watch this ViewDo video tutorial to learn how to tie a square knot. This is a very useful knot. It's strong, sturdy, and ideal for joining ends of rope together.

This crunchy, creamy, frosty recipe is ideal for kids. And since it's low in sugar and low-calorie, it works with a diabetic meal plan. This dish is a crowd pleaser and perfect for your holiday menu. Makes a great dessert for Christmas dinner.

Take a look at this instructional video of a three part series in how to joint and butcher a roe deer. This tutorial covers the basics and is ideal for home venison and choice cuts.

As requested by a few of you guys, here is a video you can follow to learn how to play the batman theme on your guitar. Hopefully, this will cover all that is needed. This is ideal for beginners, provided you can play power chords and have a little bit of musical and batman knowledge. Enjoy!

Sometimes, smokey eyes just aren't appropriate to wear. This is a tutorial on how to create a natural glowing makeup look ideal for formal daytime events, such as weddings.

In this how to video, learn to put together the right hand and the left hand when playing the blues on the piano or keyboard. This piano tutorial is ideal for beginner pianists.

Learn how to play the blues scale in the key of C on the piano or keyboard. This blues lesson is ideal for beginner pianists.

This lesson covers six unique sixteenth note accent beats. These are ideal for intermediate to advanced drummers that are looking for new ways to spice up their grooves. The patterns are somewhat similar to the two-handed sixteenth note beats, but they incorporate accents on certain hi-hat strokes.

Brandon goes into the wilderness to shoot video in the snow. He demonstrates which situations to avoid and which provide ideal opportunities for great looking winter videos.

Chopping up downed trees and sending them to the landfill isn't ideal. It's better to use them as firewood or have them chipped up and use them as mulch material or for a walkway. Never combine woodchips with the soil because they rob the soil of nitrogen, phosphorus and potassium but they're great walkway material and will gradually break down providing nutrients for the soil.

Guest designer Jasmine Burgess shows Kristy Clark how to make gorgeously vibrant butterflies, ideal for use as table decorations, novelty gift tags or embellishments on a whole range of different projects. With clever hints and handy tips, you'll see how to create a professional finish.

Store your cards or ATC's in style with these fab paper card wallets. Corinne Bradd demonstrates how to combine clever folding techniques and fabulous papers for a fantastic project that would make an ideal gift for any keen crafter. Easy to embellish, it can be made in several different sizes, including one so small it can be hidden amongst the boughs of the Christmas tree.

I have made this stunning Photo Card project and it is gorgeous, ideal for any kind of photos, simple and yet so pretty. In this project I show you how I have put it all together to create a great keepsake. Step 1: Now Watch the Tutorial

In this cardmaking tutorial I make a glorious card from the DCWV Hello Darling cardstock stack. It is a easy to make card but it looks so impressive, ideal for anyone that likes a little bit of fussy cutting and decoupage, all from the stack.. Step 1: Now Watch the Tutorial

This card tutorial make a very modern style of card that is out of the ordinary for me.. However this is an easy and quick card, ideal for Valentines Day or a Love card or even a Wedding Card Step 1: Items Used

A great technique for tempering chocolate on one you can do in the same bag you use for piping. Ideal to be used with a Water bath or Circulator but there are plenty of ways you can replicate this without those items.

This card is ideal for anyone that is getting married or has to make a card for the Big Day, easy to make but yet it looks so complicated. Step 1: Items Need to Make the Card

This is ideal for anyone wanting to save a few pennies or for any papercrafters, easy to make and can be filled with your own choices. Items You Will Need to Make the Crackers

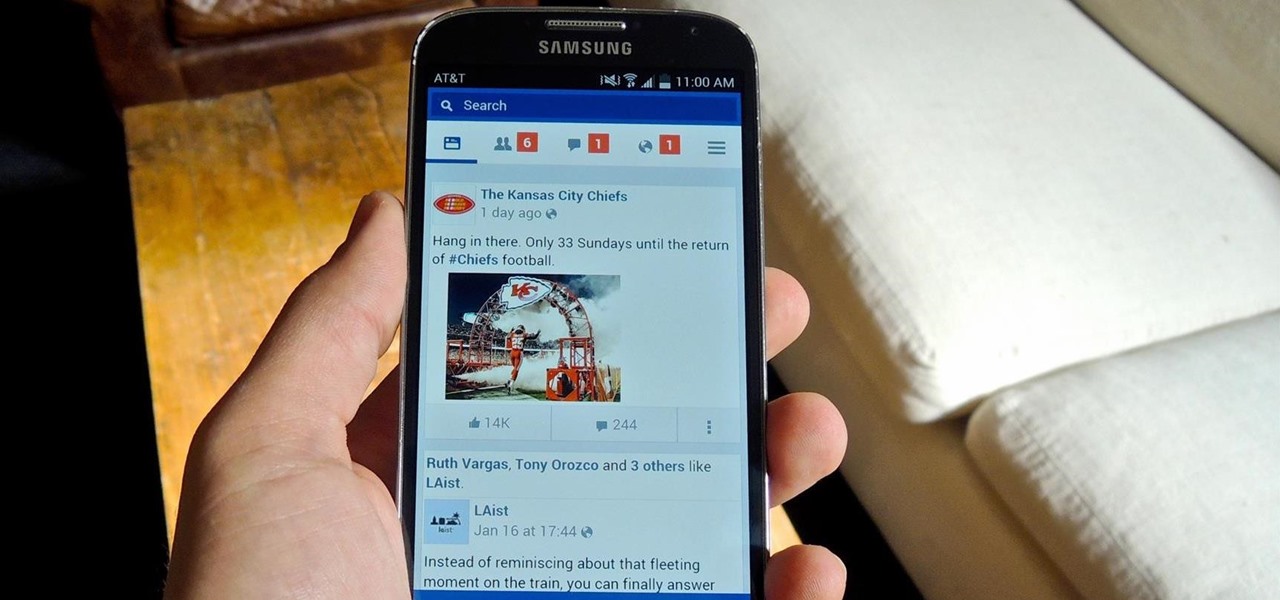
As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.

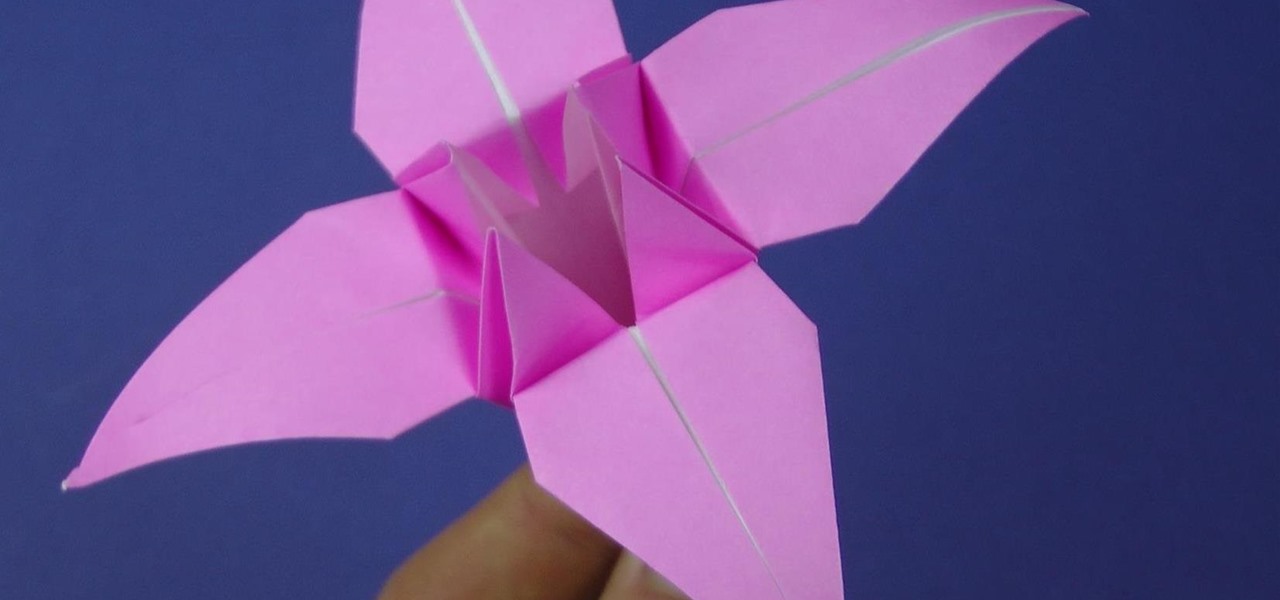
this tutorial explains how to make a traditional origami lily from one sheet of paper. No cuts, no glue needed. You'll Need

The Niknon D7000 is a hot new camera, and figuring out how to use it fast after you get it is key to getting the most out of it. This two-part series will show you how all of the buttons, menus, and other functions come together and how to set up the camera for ideal shooting.

Whether you call it a survival backpack, bug out bag, get home bag, or 72-hour kit, having a backpack full of survival gear is a must for anyone concerned about disaster survival. This video series will show you how to pack an ideal survival backpack that contains everything you need to survive for 72 hours or more in an emergency in a package you can carry on your back.

Learn how to use the BIG-IP Edge Client and its Smart Connect, Location Awareness, Customization, Deployment features. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Live View wit the EOS 7D camera from Canon, lets you compose and view your subjects with the LCD monitor as your viewfinder. This is great for a multiple of reasons. See how to use live view on this digital SLR camera.

Check out this video tutorial to show you how to use the Sony DSR-PD170 MiniDV camcorder. This video was made by the equipment room at CUNY Journalism School in New York.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

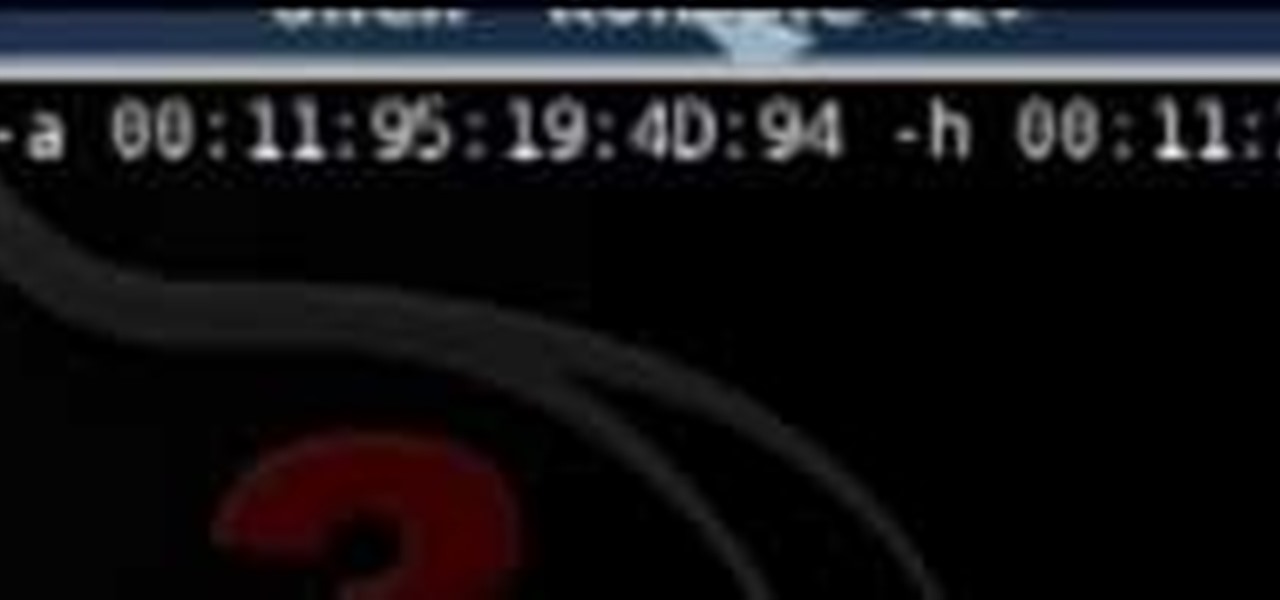
A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

Stumped on what frame to use for your favorite piece of artwork or photo? The perfect frame will make your painting, photograph, or piece of artwork stand out on your wall. Here's how to find an ideal match.

We next try some staking, because this garden has tall plants. Tall plants add verticality to the garden, but they only stay tall until a thunderstorm hits. They need staking if for no other reason to keep them out of the mud. Dahlias definitely need staking because their flowers are enormous and bend easily. Plan for this ahead of time. For staking there are lots of possibilities. You can use bamboo and string or you could use multi-purpose stakes. This metal stake is ideal for a single stem...

Pressure washers are a great way to clean a brick patio - if you do it right! The pressure washer can harm the surface you are cleaning or even yourself. The basic operation of the pressure washer is to take the low pressure from you garden hose and increase the pressure with a special pump. The pump uses either a gas powered engine or an electric motor to boost the pressure.

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

Watch how the F5 Networks BIG-IP Edge Client solution gets you connected automatically when you boot/start up your computer along with seeing the browser based version of the F5 BIG-IP Edge Gateway. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

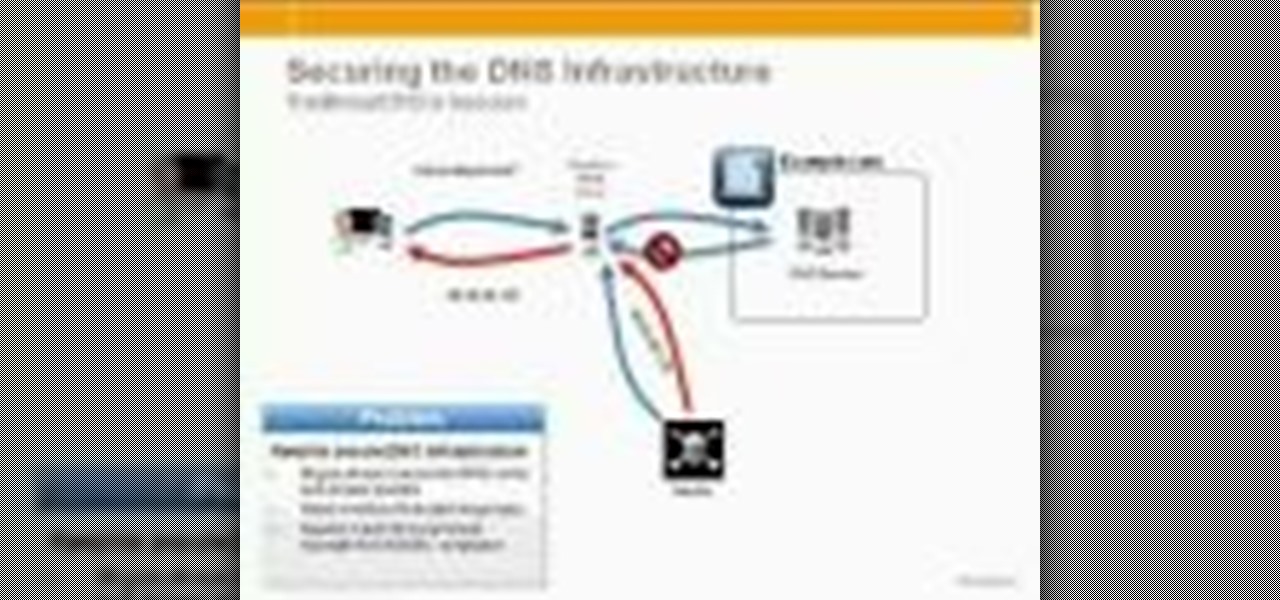
In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to use the PCI compliance reporting functionality within BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

See how to enable Layer 7 DoS and brute-force protection within DoS within BIG-IP ASM. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.