If you have your own domain, odds are you do things from FTP from time to time. In this tutorial, you'll learn a technique for making FTP shortcuts with the Windows HOSTS file, which will allow you to simplify the process. The time you save will be your own.
How to solve some of SC's common hosting problem, this clip is using LINKSYS but it can work with all routers in about the same way.

Ever wonder who's host in Halo 3? Well now there is a way to find out with this Halo tricks video.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

The fine folks at ITS Tactical made this detailed tutorial on how to make a two-piece lock pick set out of only a few paper clips and using only a multi-tool in the construction. The host begins by demonstrating how to construct the pick, then how to use it on a real lock. It is not as easy as using a real lock pick, but will still work. As the host emphasizes at the beginning of the video, these picks are only to be used in emergency situations, and NOT to break into other people's homes wil...

To make quick and easy cornbread in a truck, the host only needs jiffy corn muffin mix, egg beaters instead of whole eggs, and a little bit of milk. The ingredients are combined in a bowl, then poured into a disposable baking tin. A Crockpot is used in place of a traditional oven for baking by removing the glass interior. Place the tin with the mix directly inside, and cover until baked fully. The host usually uses a small tin that will fit easily inside the Crockpot, but if only a larger one...

When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

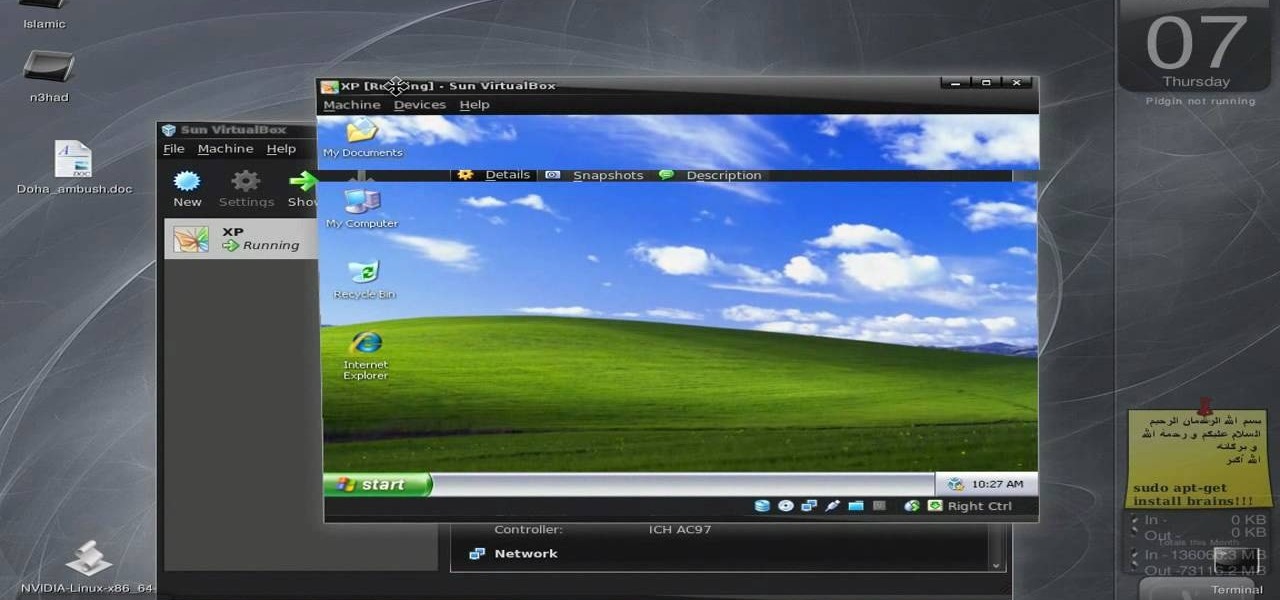
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to share files between Ubuntu (Host) & XP (Guest).

Check out this informative video tutorial from Apple on how to add a blog to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a movie to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

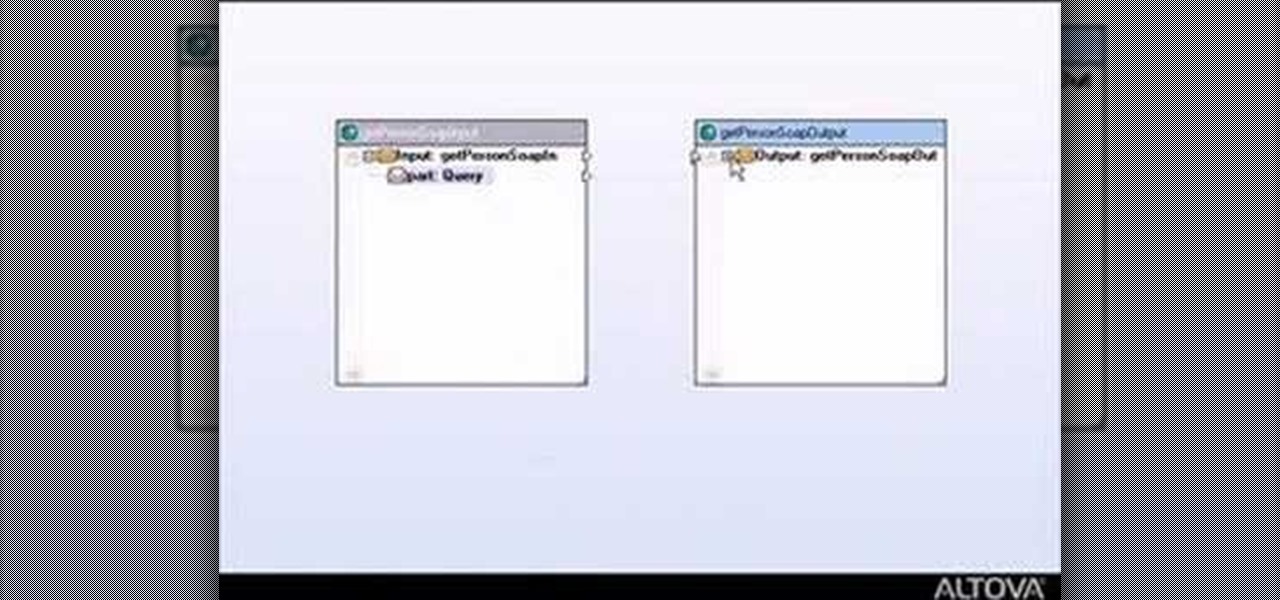
This tutorial shows you how to build web services with MapForce. Load an existing WSDL file and build a complete web service by retrieving data from databases or XML files and using a visual function builder. It's easy to build web services in MapForce as this tutorial shows.

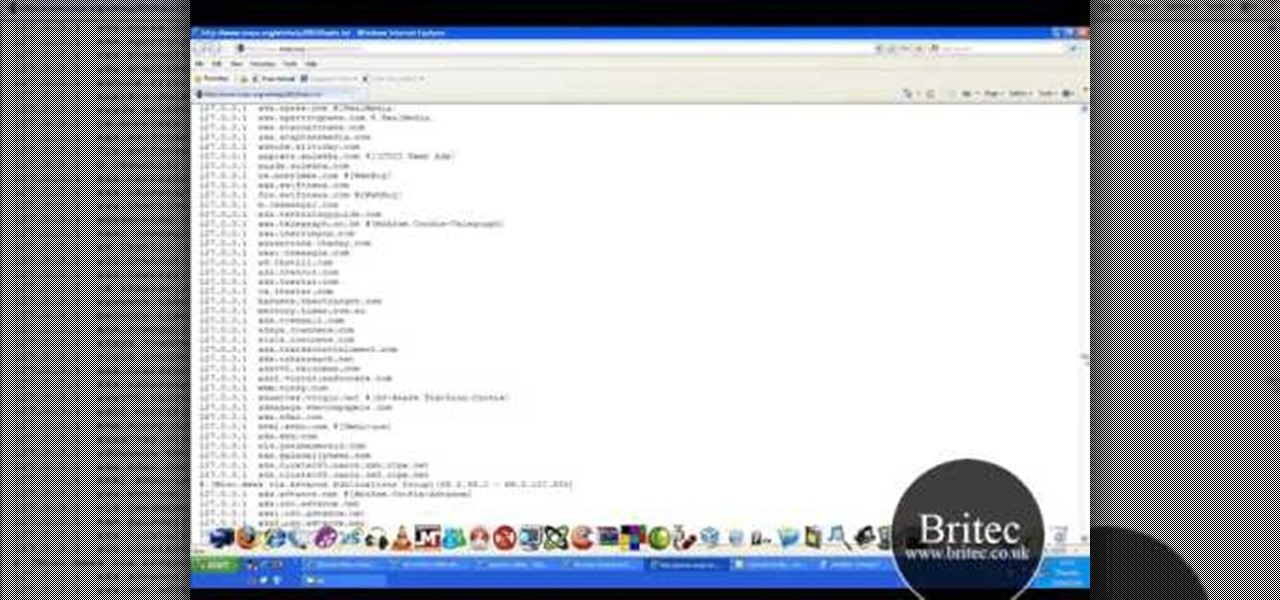
Want to know how to block websites on a Windows XP PC by editing the HOSTS files? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

In this Computers & Programming video tutorial you will learn how to use the Remote Desktop feature within Windows XP. This application will enable you to access your home computer from office using the internet. This application is really very easy and simple to use. You have to ensure 3 things for this to work. Ensure that the computer on which your files reside that you want to access has all the components of XP installed. This is the host. The computer that you want to use to access the ...

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

LX.com's Shira Lazar visits Grace Restaurant to receive expert tips on tasting, serving, and picking out the perfect wine for your wine party. Wine tasting can be an elegant gathering, or a fun party with friends. Wines should be selected with the food serving in mind. Learn how to host a wine tasting party by watching this video tutorial.

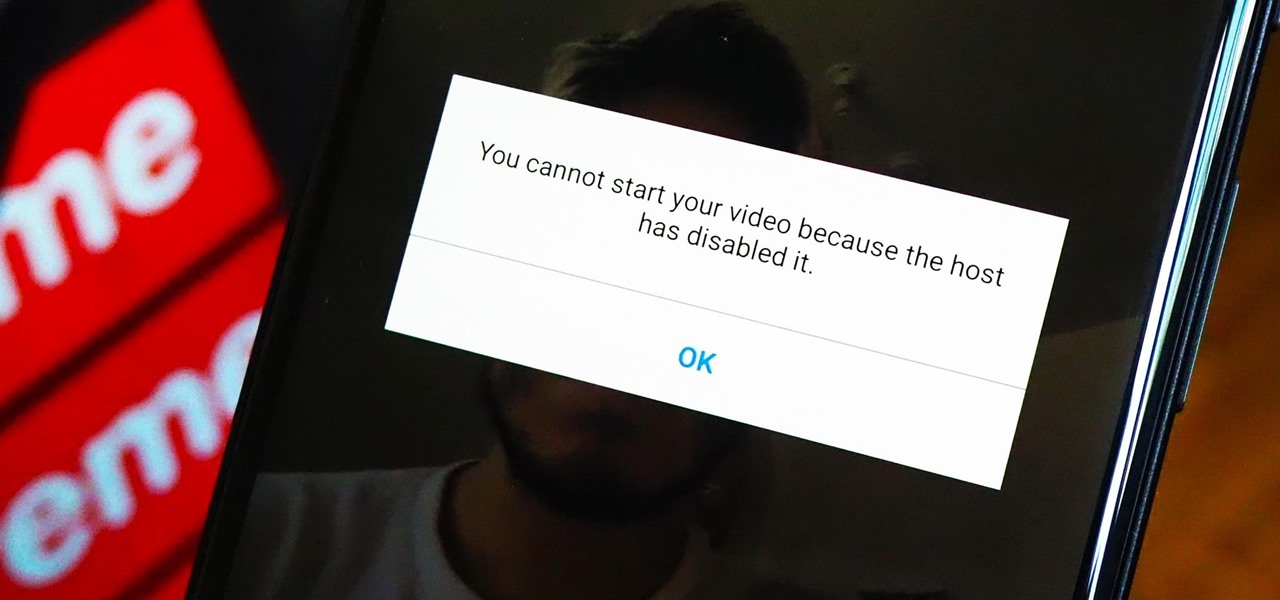
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

According to domestic goddess supreme Martha Stewart, you should always eat fresh, and even grow your own vegetables and herbs in your backyard if you can. But for those of us who are urbanites and don't have as much as a square foot of balcony space, it's not always possible to eat as fresh as we want.

Just hearing "brie" and "baguette" were enough to get us interested in this delicious summertime recipe, but Food Network host Sandra Lee amps up the classic baguette topped with brie recipe by adding raspberry jam.

Who doesn't want to enjoy a nice big bowl of freshly fried crab cakes on a warm summer's day? These bite-sized shellfish goodies are delicious, sure, but they definitely not as charming on your waistline. If you still want to fit into your bikini without giving up crab cakes entirely, then this is the perfect crab cake recipe for you to make.

When entertaining, it's great to have fun, colorful ideas to make drinks feel special. By adding a simple slice of fruit or vegetable to a glass of water can impress your friends and make you feel like you're at the spa. It is very important to drink water, and flavoring it with lemon makes it easier if you're not a water drinker. The host cuts slices of lemon and lays them on top of the water or the side of the glass to garnish, and squeezes the rest of the juice into the water. It can be ma...

In this video the host of "Tying It All Together" demonstrates how to create a "Eternity Knot". This type of knot is an attractive way to decorate a rope or string. Strung along one after another on a rope or string, it creates elongated bead-like knots at intervals of your choosing. The Eternity Knot is named for it's resemblance to the symbol of Buddha's all-knowing wisdom and the uncommon quality of his realizations. In this video the host will lead you through the entire process of creati...

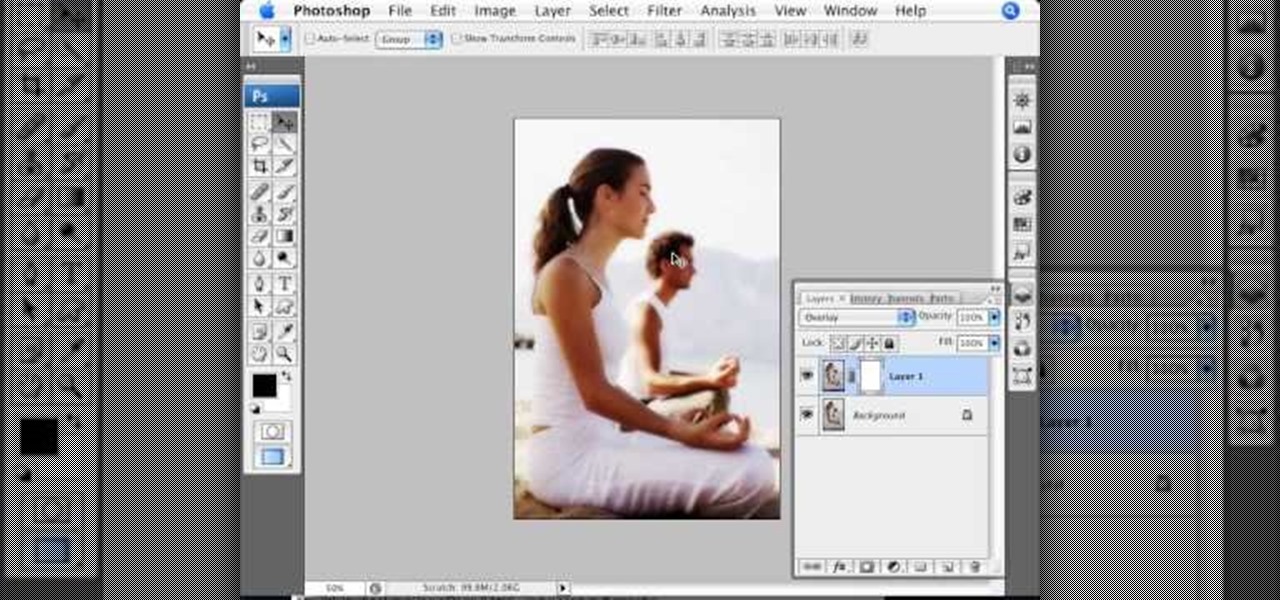
In this Photoshop video tutorial, hosted by photoshopuniverse, from Free Photoshop Video Tutorials, you will learn how to create a romantic touch effect to photos using Photoshop. The host will teach you how to use the soft overlay diffusion effect to achieve this. Guiding you, step by step, through the process of navigating Photoshop to find and use the tools you will need achieve this kind of effect. He also explains in detail what the tools are, as well as what they do, as you follow along.

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Get a sexy rock 'n' roll look that would be seen on the likes of such stylish celebs as Katy Perry and Gwen Stefani. In this makeup tutorial hosted by the experts at Smashbox Cosmetics, get tips, tricks and secrets to achieving this look without paying for a stylist. With dark, deep lips and a black pussy cat eye applied to your lids, you'll be ready to take center stage!

Looking to emulate the vixens of the 20's and 30's? In this makeup tutorial hosted by Smashbox Cosmetics, embrace your inner vixen with these tips and tricks on how to steal this look with your makeup. With a clean face, a natural matted eye with nude shades, and a dark winged out liner, you'll be channeling Betty Page in no time!

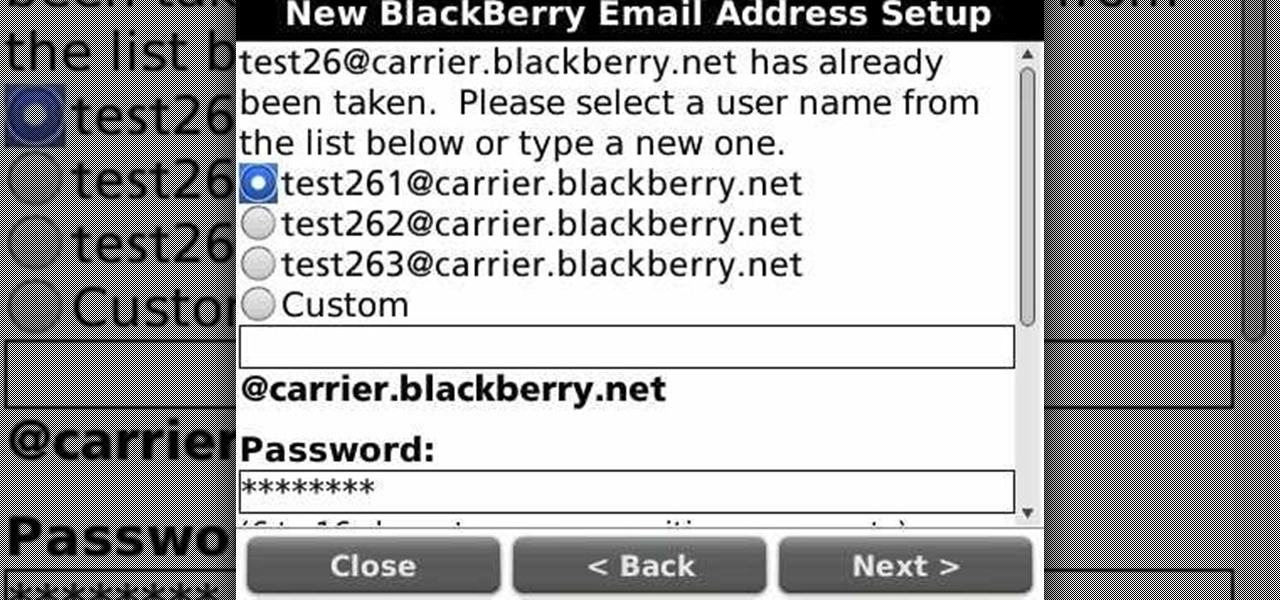
Learn how to create a new BlackBerry Internet service email account on a BlackBerry device running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The iPhone has always been hamstrung by its alignment with AT&T, the worst of the big 4 US cell service providers. If you have an iPhone and are planning on unlocking it for use with another provider, or just want to use it without being connected to AT&T's network, this video is here to help. It will show you how to activate an iPhone instantly without a service plan using any AT&T SIM card.